Académique Documents
Professionnel Documents
Culture Documents
Ccnp-Access List
Transféré par
Ti NguyenTitre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Ccnp-Access List
Transféré par
Ti NguyenDroits d'auteur :
Formats disponibles
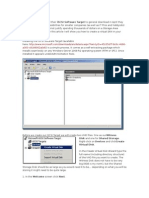
1. The network of a company is shown as in the figure 1. In a company we have network of two PCs located in on 201.205.84.0 network.
The network connects to a router 2 located on 192.168.1.0 network. In present setup we have no ACL configured, and information can travel unrestricted between PCs. a. Configure the network, routers so that PC1, PC2 can ping Router 2. Next, configure the router 2 so PC1, PC2 can telnet to it with Username: telnet, Password: Troy. b. Configure the ACL on the router 1 so that PC1 can ping router 2, while allowing only PC2 to telnet to Joker. We will achieve this by creating three ACLs. First one would allow PC1 to ping router 2,by allowing ICMP packets to pass from FE1 to FE0. Second one would allow PC2 to telnet to router 2, by allowing TCP telnet packets from FE1 to FE0. Finally, third one would deny any traffic that comes from FE1 to FE0. You make get confused by thinking howwould other two operate if third ACL denies all traffic. Well, it is pretty simple, the thing to know is that when packet is being filtered through ACL, router checks ACL in order they were created, one by one, and if match is found, checking process is stopped, and packet can go through. In this way, all traffic denied ACL would comein play, only if two other ACL were not matched beforehand. c. Configure the ACL on the router 1 so that PC1, PC2 can ping the web server, but only PC1 can access the webpage of the server.
2. The test-bed is built as shown in the figure 2. Complete the following tasks
Asignment 6 Page 1
a. Configure a hostname of Sw1 on your lab switch, and the hostname R1 on the router as illustrated in the topology. b. Create VLAN 10 on switch Sw1 and assign port FastEthernet0/2 to this VLAN as an access port. c. Configure IP address 10.0.0.1/30 on router R1's FastEthernet0/0 interface, and IP address 10.0.0.2/30 in switch Sw2's VLAN 10 interface. Verify that R1 can ping Sw1 and vice versa. d. Configure port security on port FastEthernet0/2 on switch Sw1 so that only 1 MAC address is allowed to be learned on thatinterface. In the event of port security configuration violations, where more than 1 MAC address is observed on that interface, the switch should shut the interface down. Verifyyour configuration with port security commands in Cisco IOS.
Bi 1 a. Cu hnh mng Router 1
Router1> enable Router1# configure terminal Router1(config)# interface FastEthernet0/0 Router1(config-if)# ip address 201.205.84.1 255.255.255.0 Router1(config-if)# no shutdown Router1(config-if)# exit Router1(config)# interface FastEthernet0/1 Router1(config-if)# ip address 192.168.1.1 255.255.255.0 Router1(config-if)# no shutdown Router1(config)# exit Asignment 6 Page 2
Router1(config)# router rip Router1(config-router)# version 2 Router1(config-router)# network 192.168.1.0 Router1(config-router)# network 201.205.84.0 Router1(config-router)# no auto-summary Router1(config-router)# exit
Router 2
Router2> enable Router2# configure terminal Router2(config)# interface FastEthernet0/0 Router2(config-if)# ip address 192.168.1.3 255.255.255.0 Router2(config-if)# no shutdown Router2(config-if)# exit Router2(config)# router rip Router2(config-router)# version 2 Router2(config-router)# network 192.168.1.0 Router2(config-router)# no auto-summary Router2(config-router)# exit Sau khi cu hnh, ping t PC1 v PC2 n router2 thnh cng
Asignment 6
Page 3
Asignment 6
Page 4
Cu hnh trn Router 2 c th telnet vo vi username telnet v pasword Troy Router2(config)#username telnet password troy Router2(config)#line vty 0 4 Router2(config)#login local Router2(config)#exit
b. Access list
Cu hnh ACLs trn R1 : PC1 ping R2 nhng khng th telnet c PC2 telnet R2 nhng khng th ping R2 c
Cu hnh R1 Router1(config)#ip access-list extended 1b Router1(config-ext-nacl)#permit icmp 201.205.84.15 0.0.0.0 192.168.1.3 0.0.0.0 Router1(config-ext-nacl)#permit icmp 201.205.84.15 0.0.0.0 192.168.1.3 0.0.0.0 Router1(config-ext-nacl)# deny ip 201.205.84.0 0.0.0.255 192.168.1.3 0.0.0.0 Router1(config-ext-nacl)#exit Router1(config)#interface fastEthernet0/1 Asignment 6 Page 5
Router1(config-if)#ip access-group 1b in Router1(config-if)#int fa0/0 Router1(config-if)#ip access-group 1b out
Kt qu i vi [PC1]( [PC2] tng ng).
a. Cu hnh ACLs trn R1 [PC1] ping c webserver v truy cp webpage t server ny [PC2] ping c webserver nhng khng truy cp webpage t server ny c. Cc ACLs cn to ra : permit icmp host 201.205.84.15 host 192.168.1.4 (16 match(es)) permit icmp host 201.205.84.12 host 192.168.1.4 (8 match(es)) permit tcp host 201.205.84.15 host 192.168.1.4 (12 match(es)) deny ip 201.205.84.0 0.0.0.255 host 192.168.1.4 (12 match(es)) Cu hnh R1 Router1(config)#interface FastEthernet0/0 Router1(config-if)#no ip access-group 1b out Router1(config-if)#interface fastEthernet0/1 Router1(config-if)#no ip access-group 1b in Router1(config)#ip access-list extended 1c Router1(config-ext-nacl)#permit icmp 201.205.84.15 0.0.0.0 192.168.1.4 0.0.0.0 Router1(config-ext-nacl)#permit icmp 201.205.84.12 0.0.0.0 192.168.1.4 0.0.0.0
Asignment 6 Page 6
Router1(config-ext-nacl)#permit tcp 201.205.84.15 0.0.0.0 192.168.1.4 0.0.0.0 Router1(config-ext-nacl)#permit tcp 201.205.84.0 0.0.0.0 192.168.1.4 0.0.0.0 Router1(config-ext-nacl)#exit Kt qu [PC1]
Asignment 6
Page 7
[PC2]
Asignment 6
Page 8
a. i tn switch thnh SW1, router thnh R1. Router1>enable Router1#configure terminal Router1(config)#hostname R1 R1(config)# Switch1>enable Switch11#configure terminal Switch1(config)#hostname SW1 SW1(config)# b. To vlan10 trn SW1 c port-access l FastEthernet0/2. SW1(config)#vlan 10 SW1(config)#hostname Sales SW1(config)#interface fa0/2 SW1(config-if)#switchport mode access SW1(config-if)#switchport access vlan 10
Asignment 6 Page 9
SW1(config-if)# no shutdown SW1(config-if)#exit Kt qu kim tra vi SW1# show vlan brief Kim tra cc vlan trn SW1
c. nh a ch 10.0.0.1/30 trn Fa0/0 ca R1 v vlan interface 10.0.0.2/30 R1(config)#interface fa0/0 R1(config-if)#no shutdown R1(config-if)#ip address 10.0.0.1 255.255.255.248 R1(config-if)#exit SW1(config)#inteface vlan 10 SW1(config-if)#ip address 10.0.0.2 255.255.255.248 SW1(config-if)#no shutdown SW1(config-if)#exit
Asignment 6 Page 10
Kim tra rng R1 ping ti VLAN 10 v ngc li. R1>ping 10.0.0.3 Kt qu
d. Thc hin cu hnh port-security trn Fa0/2 i vi SW1.Ch cho php duy nht mt a ch MAC bt k c php trn Fa0/2, nu nh c MAC khc lp tc shutdown port ny. SW1(config)#int fa0/2 SW1(config-if)# switchport portsecurity SW1(config-if)# switchport portsecurity violation shutdown SW1(config-if)# switchport portsecurity maximum 1 SW1(config-if)# switchport portsecurity mac-address sticky SW1(config-if)#exit Kim tra
Asignment 6 Page 11
Ngt dy ni gia R1 v SW1, kt ni mt PC vo port Fa0/2 ca SW1 .
Khi ping t [PC] ti vlan 10 , cng lp tc b shutdown
Mun khi phc li ch cn vo interface Fa0/2 thc hin shutdown v no shutdown l cng li up li nhng cu hnh port-security vn lu gi ngha l SW1 chp nhn MAC ca [PC1] l MAC hp
Asignment 6
Page 12
Vous aimerez peut-être aussi
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5794)
- Joint ProbabilityDocument13 pagesJoint ProbabilityTi NguyenPas encore d'évaluation
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (399)
- Wallchart Cisco Ccap 2013Document2 pagesWallchart Cisco Ccap 2013Ti NguyenPas encore d'évaluation
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- DOCSIS 3.0 - CM-SP-MULPIv3.0-I15-110210Document750 pagesDOCSIS 3.0 - CM-SP-MULPIv3.0-I15-110210Ti Nguyen100% (1)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (894)
- Gummalla 1 0701Document19 pagesGummalla 1 0701Ti NguyenPas encore d'évaluation
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- Casa Systems C10G CMTSDocument5 pagesCasa Systems C10G CMTSmutckataPas encore d'évaluation
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- Cable Modem Hacking: Gaining Anonymous Internet Access and Maximizing SpeedsDocument42 pagesCable Modem Hacking: Gaining Anonymous Internet Access and Maximizing SpeedsTi NguyenPas encore d'évaluation
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- Video On DemandDocument13 pagesVideo On DemandTi NguyenPas encore d'évaluation
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- GregWhite ChannelBondingDocument32 pagesGregWhite ChannelBondingHumberto ZambranoPas encore d'évaluation
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (587)
- 80211Document64 pages80211Ti NguyenPas encore d'évaluation
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (265)
- DOCSIS 3.0 - CM-SP-MULPIv3.0-I15-110210Document750 pagesDOCSIS 3.0 - CM-SP-MULPIv3.0-I15-110210Ti Nguyen100% (1)
- Docsis 2.0 Standard CM SP Rfiv2.0 I07 041210Document530 pagesDocsis 2.0 Standard CM SP Rfiv2.0 I07 041210Ti NguyenPas encore d'évaluation
- Peter Bernholz - Monetary Regimes and Inflation: History, Economic and Political Relationships (2003)Document225 pagesPeter Bernholz - Monetary Regimes and Inflation: History, Economic and Political Relationships (2003)1236howard100% (1)
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- Etherchannel SwitchDocument9 pagesEtherchannel SwitchTi NguyenPas encore d'évaluation
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (73)
- BPO Management System SoftwareDocument15 pagesBPO Management System SoftwaremuthazhaganPas encore d'évaluation
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (344)
- Semantic. TagDocument10 pagesSemantic. TagNdayishimye OnesmePas encore d'évaluation
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- 2013 Siemon Full CatalogDocument248 pages2013 Siemon Full Catalogmc69aPas encore d'évaluation
- Forensic Analysis of the Windows 7 RegistryDocument18 pagesForensic Analysis of the Windows 7 RegistryNeetish JayantPas encore d'évaluation
- Activity 2 Purposive CommunicationDocument4 pagesActivity 2 Purposive CommunicationAnya ForgerPas encore d'évaluation
- Oracle OAF Introduction - by Dinesh Kumar SDocument163 pagesOracle OAF Introduction - by Dinesh Kumar Sdineshcse86gmailcomPas encore d'évaluation
- Java Script Create QuizDocument11 pagesJava Script Create QuizMahfud SidikPas encore d'évaluation
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- Checkpoint 1180 ConfigDocument10 pagesCheckpoint 1180 ConfigganeshPas encore d'évaluation
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2219)
- ISCSI Target 3.3Document5 pagesISCSI Target 3.3Zainuri MuhammadPas encore d'évaluation
- R Programming NotesDocument32 pagesR Programming NotesShanmugasundaram Muthuswamy100% (1)
- Final Fyp Print PDFDocument119 pagesFinal Fyp Print PDFlimPas encore d'évaluation
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- Crypto Currency Tracker PBL ReportDocument13 pagesCrypto Currency Tracker PBL ReportRao AnuragPas encore d'évaluation
- FTP TFTPDocument18 pagesFTP TFTPXXXPas encore d'évaluation
- Sharda dss10 PPT 01Document41 pagesSharda dss10 PPT 01Aniket KaushikPas encore d'évaluation
- Facebook Business ModelDocument32 pagesFacebook Business ModelRon BhuyanPas encore d'évaluation
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (119)
- Airtel Financial Analysis and Ratio StudyDocument32 pagesAirtel Financial Analysis and Ratio StudyMohammad Anwar AliPas encore d'évaluation
- Capstone Project 2 Business Problem Requirement Document: Enterprise Network Security Based On Cisco SolutionsDocument12 pagesCapstone Project 2 Business Problem Requirement Document: Enterprise Network Security Based On Cisco Solutionshoàng huyPas encore d'évaluation
- Case Study 1Document4 pagesCase Study 1Hanshika GuptaPas encore d'évaluation
- TANCET MCA Model Question PaperDocument11 pagesTANCET MCA Model Question PaperKishore KrishPas encore d'évaluation
- Airtel Sales & Insurance ServicesDocument13 pagesAirtel Sales & Insurance ServicesSunil Kumar NagPas encore d'évaluation
- 2G 3G CodecDocument1 page2G 3G CodecBiolandPas encore d'évaluation
- AP Suppliers in R12Document51 pagesAP Suppliers in R12Abhilash KarappankuttyPas encore d'évaluation
- Asterisk ServerDocument6 pagesAsterisk ServerFish BonePas encore d'évaluation
- Finaldis2011 1Document4 pagesFinaldis2011 1syaiful.idzwanPas encore d'évaluation
- Tableau Desktop Windows 9.2Document1 329 pagesTableau Desktop Windows 9.2vikramraju100% (2)
- E-commerce-Evaluation of Marketing EffortsDocument19 pagesE-commerce-Evaluation of Marketing EffortsuniofPas encore d'évaluation
- Social Media: Twitter 101: LAAMA Christmas Luncheon: DEC. 17, 2009Document23 pagesSocial Media: Twitter 101: LAAMA Christmas Luncheon: DEC. 17, 2009saharconsultingPas encore d'évaluation
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)
- Performance Tuning Linux Instances On EC2Document4 pagesPerformance Tuning Linux Instances On EC2Didik HariadiPas encore d'évaluation
- EQ Domestic Biometric Data OperatorDocument4 pagesEQ Domestic Biometric Data OperatorParthibanPas encore d'évaluation
- Deployment With Docker and Rancher and Continuous Integration andDocument47 pagesDeployment With Docker and Rancher and Continuous Integration andManish MalhotraPas encore d'évaluation