Académique Documents
Professionnel Documents
Culture Documents
E - Comm
Transféré par
Moygaon RockersTitre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
E - Comm
Transféré par
Moygaon RockersDroits d'auteur :
Formats disponibles
A web browser is a software application for retrieving, presenting and traversing information resources on the World Wide Web.
An information resource is identified by a Uniform Resource Identifier (URI) and [1] may be a web page, image, video or other piece of content. Hyperlinks present in resources enable users easily to navigate their browsers to related resources. A web browser can also be defined as an application software or program designed to enable users to access, retrieve and view documents and other resources on the Internet. Although browsers are primarily intended to use the World Wide Web, they can also be used to access information provided by web servers in private networks or files in file systems. The major web browsers are Chrome, Firefox, Internet Explorer, Opera, and Safari
Function
The primary purpose of a web browser is to bring information resources to the user ("retrieval" or "fetching"), allow them to view the information ("display", "rendering"), and then access other information
Features
For more details on this topic, see Comparison of web browsers. Available web browsers range in features from minimal, text-based user interfaces with bare-bones support for HTML to rich user interfaces supporting a wide variety of file formats and protocols. Browsers which include additional components to support e-mail,Usenet news, and Internet Relay Chat (IRC), are [11][12][13] sometimes referred to as "Internet suites" rather than merely "web browsers". All major web browsers allow the user to open multiple information resources at the same time, either in different browser windows or in different tabs of the same window. Major browsers also include pop-up blockers to prevent unwanted windows from "popping up" without the user's consent
Computer crime
From Wikipedia, the free encyclopedia
Computer crime refers to any crime that involves a computer and a network.[1] The computer may have been used in the commission of a crime, or it may be the target.[2] Netcrime refers to criminal exploitation of the Internet.[3] Cybercrimes are defined as: "Offences that are committed against individuals or groups of individuals with a criminal motive to intentionally harm the reputation of the victim or cause physical or mental harm to the victim directly or indirectly, using modern telecommunication networks such as Internet (Chat rooms, emails, notice boards and groups) and mobile phones (SMS/MMS)".[4] Such crimes may threaten a nations security and financial health.[5] Issues surrounding this type of crime have become high-profile, particularly those surrounding cracking, copyright infringement, child pornography, and child grooming. There are also problems of privacy when confidential information is lost or intercepted, lawfully or otherwise.
Internationally, both governmental and non-state actors engage in cybercrimes, including espionage, financial theft, and other cross-border crimes. Activity crossing international borders and involving the interests of at least one nation state is sometimes referred to ascyber warfare. The international legal system is attempting to hold actors accountable for their actions through the International Criminal Court.[6]
Spam
Spam, or the unsolicited sending of bulk email for commercial purposes, is unlawful in some jurisdictions. While anti-spam laws are relatively new, limits on unsolicited electronic communications have existed for [7] some time. [edit]Fraud Main article: Computer fraud Computer fraud is any dishonest misrepresentation of fact intended to let another to do or refrain from doing something which causes loss
Obscene or offensive content
The content of websites and other electronic communications may be distasteful, obscene or offensive for a variety of reasons. In some instances these communications may be illegal.
Harassment
Whereas content may be offensive in a non-specific way, harassment directs obscenities and derogatory comments at specific individuals focusing for example on gender, race, religion, nationality, sexual orientation. This often occurs in chat rooms, through newsgroups, and by sending hate e-mail to interested parties
Cyber terrorism
Main article: Cyber terrorism Government officials and Information Technology security specialists have documented a significant increase in Internet problems and server scans since early 2001. But there is a growing concern among [who?] federal officials that such intrusions are part of an organized effort by cyberterrorists
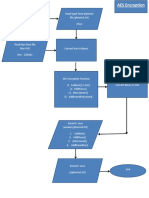
Cryptography (or cryptology; from Greek , "hidden, secret"; and, graphein,
"writing", or -, -logia, "study", respectively) is the practice and study of techniques for secure [2] communication in the presence of third parties (called adversaries). More generally, it is about [3] constructing and analyzing protocols that overcome the influence of adversaries and which are related to various aspects in information security such as data confidentiality,data integrity, authentication, [4] and non-repudiation. Modern cryptography intersects the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce. A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender such that they cannot deny sending it (authentication and non-repudiation) and that the message was not altered in transit (integrity). Digital
[1]
signatures are commonly used for software distribution, financial transactions, and in other cases where it is important to detect forgery or tampering. Digital signatures are often used to implement electronic signatures, a broader term that refers to any [1] electronic data that carries the intent of a signature, but not all electronic signatures use digital [2][3] [4] signatures. In some countries, including the United States, India, and members of the European Union, electronic signatures have legal significance.
Definition
Main article: Public-key cryptography A digital signature scheme typically consists of three algorithms: A key generation algorithm that selects a private key uniformly at random from a set of possible private keys. The algorithm outputs the private key and a corresponding public key. A signing algorithm that, given a message and a private key, produces a signature. A signature verifying algorithm that, given a message, public key and a signature, either accepts or rejects the message's claim to authenticity.
Two main properties are required. First, a signature generated from a fixed message and fixed private key should verify the authenticity of that message by using the corresponding public key. Secondly, it should be computationally infeasible to generate a valid signature for a party who does not possess the private key. Public-key cryptography refers to a cryptographic system requiring two separatekeys, one of which is secret and one of which is public. Although different, the two parts of the key pair are mathematically linked. One key locks or encrypts the plaintext, and the other unlocks or decrypts the ciphertext. Neither key can perform both functions by itself. The public key may be published without compromising security, while the private key must not be revealed to anyone not authorized to read the messages. Symmetric encryption (also called private-key encryption or secret-key encryption) involves using the same key for encryption and decryption.
Encryption involves applying an operation (an algorithm) to the data to be encrypted using the private key to make them unintelligible. The slightest algorithm (such as an exclusive OR) can make the system nearly tamper proof (there being so such thing as absolute security).
An e-commerce payment system facilitates the acceptance of electronic payment for online transactions. Also known as a sample ofElectronic Data Interchange (EDI), e-commerce payment systems have become increasingly popular due to the widespread use of the internet-based shopping and banking.
Methods of Online Payment
Although credit cards are most popular in the US and some other countries, there are a few alternative systems. [edit]Net
Banking
This is a system, well known in India that does not involve any sort of physical card. It is used by customers who have accounts enabled with Internet Banking. Instead of entering card details on the purchaser's site, in this system the payment gateway allows one to specify which bank they wish to pay from. Then the user is redirected to the bank's website, where one can authenticate oneself and then approve the payment. Typically there will also be some form of Two-factor Authentication. It is typically seen as being safer than using credit cards, with the result that nearly all merchant accounts in India offer it as an option These include debit cards, credit cards, electronic funds transfers, direct credits, direct debits, internet banking and e-commerce payment systems. Some payment systems include credit mechanisms, but that is essentially a different aspect of payment. Payment systems are used in lieu of tendering cash in domestic and international transactions and consist of a major service provided by banks and other financial institutions. Real time gross settlement systems (RTGS) are funds transfer systems where transfer of money or [1] securities takes place from one bank to another on a "real time" and on "gross" basis. Settlement in "real time" means payment transaction is not subjected to any waiting period. The transactions are settled as soon as they are processed. "Gross settlement" means the transaction is settled on one to one basis without bunching or netting with any other transaction. Once processed, payments are final and irrevocable.
The protection of email from unauthorized access and inspection is known as electronic
privacy. In countries with a constitutional guarantee of the secrecy of correspondence, email is equated with letters and thus legally protected from all forms of eavesdropping. The Internet is an expansive network of computers, much of which is unprotected against malicious attacks. From the time it is composed to the time it is read, email travels along this unprotected Internet, perpetually exposed to electronic dangers. Many users believe that email privacy is inherent and guaranteed, psychologically equating it with postal mail. While email is indeed conventionally secured by a password system, the one layer of protection is not secure, and generally insufficient to guarantee appreciable security. Businesses are increasingly relying on electronic mail to correspond with clients and colleagues. As more sensitive information is transferred online, the need for email privacy becomes more pressing.
Risks to user
The pathway of email. Terminology used in this image is explained in the electronic mail article.
Email is vulnerable to both passive and active attacks. Passive threats includeRelease of message contents, and Traffic analysis while active threats includeModification of message contents, Masquerade, Replay, and Denial of Service (DoS). Actually, all the mentioned threats are [3] applicable to the traditional email protocols: Disclosure of Information Modification of messages: Replay of previous messages Spoofing: False messages may be inserted into mail system of another user. It can be accomplished from within a LAN, or from an external environment using Trojan horses. Denial of Service: It can put a mail system out of order by overloading it with mail shots. It can be carried out using Trojan horses or viruses sent to users within the contents of emails. It is also possible to block the user accounts by repeatedly entering wrong passwords in the login.
[edit]Remedies To provide a reasonable level of privacy, all routers in the email pathway, and all connections between them, must be secured. This is done through data encryption, which translates the email's contents into incomprehensible text that, if designed correctly, can be decrypted only by the recipient. An industry-wide push toward regular encryption of email correspondence is slow in the making. However, there are certain standards that are already in place which some services have begun to employ. There are two basic techniques for providing such secure connections. The electronic envelope technique involves encrypting the message directly using a secure encryption standard such as OpenPGP (Public key infrastructure), S/MIME. These encryption methods are often a user-level responsibility, even though Enterprise versions of OpenPGP exist. The usage of OpenPGP requires the exchange of encryption keys. Even if an encrypted email is intercepted and accessed, its contents are meaningless without the decryption key. There are also examples of secure messaging solutions available built on purely symmetric keys for encryption. These methods are also sometimes tied with authorization in the form of authentication. Authentication just means that each user must prove who he is by using either a password, biometric (such as a fingerprint), or other standard authentication means. The second approach is to send an open message to the recipient which does not have to contain any sensitive content but which announces a message waiting for the recipient on the sender's secure mail facility. The recipient then follows a link to the sender's secure website where the recipient must log in with a username and password before being allowed to view the message. Some solutions combine the approaches, and allow for offline reading.
Both approaches, and their related techniques, come with advantages and disadvantages and it is today generally considered that the setup of choice varies depending on the target market and application. PKI based encryption methodologies have limits in efficiency in how to engage secure messaging between two parties, as creation and delegation of certificates are needed prior to communication. Methods of utilizing non-PKI based encryption bring in challenges in a successful and secure key-exchange. Having the sensitive content shipped with the email delimits the senders possibilities to make the content unavailable, or control when in time the content should be available for consumption. If on the other hand, the sensitive information is not shipped with the MIME stream and the sender is hosting the information on a web-server, it requires the recipient to be online to be able to read it. At the ISP level, a further level of protection can be implemented by encrypting the communication between servers themselves, usually employing an encryption standard called Transport Layer Security (TLS). It is coupled with Simple Authentication and Security Layer(SASL), which confirms the target router's identity. This ensures that unintended servers don't end up with a copy of the email, which happens frequently in the course of normal correspondence. This method is the only method that is completely transparent to end-users and does not require the creation of individual certificates for each user. Gmail adopted TLS on outgoing mail in October 2011. Other major webmail providers such as [8] Yahoo! and Hotmail have yet to announce any plan to adopt TLS on outgoing mail. Although some ISPs have implemented secure sending methods, users have been slow to adopt the habit, citing the esoteric nature of the encryption process. Without user participation, email is only protected intermittently from intrusion. A non-technical approach employed by some users is to make tapping and analysis of their email impractical via email jamming.
Vous aimerez peut-être aussi
- Paper 14-Study of Indian Banks Websites For Cyber Crime Safety MechanismDocument4 pagesPaper 14-Study of Indian Banks Websites For Cyber Crime Safety MechanismEditor IJACSAPas encore d'évaluation
- MArketing MAnagementDocument4 pagesMArketing MAnagementAjaySon678Pas encore d'évaluation
- Technical Management Issues For Resolving The Cyber CrimeDocument6 pagesTechnical Management Issues For Resolving The Cyber CrimeMehneen KaurPas encore d'évaluation
- Glossary of TermsDocument9 pagesGlossary of TermsRentonPas encore d'évaluation
- Exposing Ways and Means of Carrying Out Phishing Attacks Towards Ensuring Confidence in The Use of University PortalsDocument6 pagesExposing Ways and Means of Carrying Out Phishing Attacks Towards Ensuring Confidence in The Use of University PortalstheijesPas encore d'évaluation
- Negative Impacts of Technology in Banking SectorDocument5 pagesNegative Impacts of Technology in Banking Sectorapaman100% (1)
- Cyber Laws and Ethics, Digital Signature and E-RecordsDocument29 pagesCyber Laws and Ethics, Digital Signature and E-RecordsAnkush Kumar YedePas encore d'évaluation
- Data AlterationDocument13 pagesData AlterationVicky SharmaPas encore d'évaluation
- 2 Types of SecurityDocument17 pages2 Types of SecurityUmesh KanadePas encore d'évaluation
- Cyber Crimes and Steps To Prevent and ControlDocument4 pagesCyber Crimes and Steps To Prevent and ControlJanani ShreePas encore d'évaluation
- Cyber Crimes and SecurityDocument3 pagesCyber Crimes and SecuritySunil PandeyPas encore d'évaluation
- Practical 1 AIM: Study Practical On Cyber Crime and Generation of Hash Values On File System. Theory: 1) Cyber CrimeDocument4 pagesPractical 1 AIM: Study Practical On Cyber Crime and Generation of Hash Values On File System. Theory: 1) Cyber CrimeSneha DasPas encore d'évaluation
- Understanding Cybercrime: Phenomena, Challenges and Legal ResponseDocument29 pagesUnderstanding Cybercrime: Phenomena, Challenges and Legal ResponseVipul Khullar100% (1)
- Module-1: Introduction of E-CommerceDocument286 pagesModule-1: Introduction of E-Commercenidhi goelPas encore d'évaluation
- Module-1: Introduction of E-CommerceDocument82 pagesModule-1: Introduction of E-Commercenidhi goelPas encore d'évaluation
- Basics of Encryption andDocument4 pagesBasics of Encryption andShruti JainPas encore d'évaluation
- 1.digital SecurityDocument25 pages1.digital Securitymarjana bharaliPas encore d'évaluation
- Cyber LawDocument21 pagesCyber LawradhakrishnaPas encore d'évaluation
- E&clDocument10 pagesE&clSBAPas encore d'évaluation
- Types of Data Transferred On Web Top Secret (TS) : National SecurityDocument5 pagesTypes of Data Transferred On Web Top Secret (TS) : National SecurityAman MalooPas encore d'évaluation
- Topic1 Lesson1to9 IAaS1Document62 pagesTopic1 Lesson1to9 IAaS1Kervi Sanares BacuelPas encore d'évaluation
- Information Systems Assignment Answers June 2022Document8 pagesInformation Systems Assignment Answers June 2022sanhitaPas encore d'évaluation
- Cyber LawDocument53 pagesCyber LawMuzammil Deshmukh0% (1)
- CEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021D'EverandCEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021Pas encore d'évaluation
- Cyber Threats and SecurityDocument17 pagesCyber Threats and Securityno OnePas encore d'évaluation
- Sem - 6 Cyber SecurityDocument9 pagesSem - 6 Cyber Securitykalida6408Pas encore d'évaluation
- Web SecurityDocument8 pagesWeb SecurityAniket ShetyePas encore d'évaluation
- Social, Economic, Ethical and Legal Implications of ComputersDocument11 pagesSocial, Economic, Ethical and Legal Implications of ComputersNitro stormPas encore d'évaluation
- Chapter 8 Security and Ethics Computer Science IgcseDocument7 pagesChapter 8 Security and Ethics Computer Science IgcseDesire KandawasvikaPas encore d'évaluation
- Cyber Security All Imprortant QuestionsDocument39 pagesCyber Security All Imprortant Questionsmdatikur.rahman.ds.2022Pas encore d'évaluation
- Cybr CrimeDocument26 pagesCybr CrimeKhushboo JainPas encore d'évaluation
- The Different Types of Threats On The Internet, Which Can Create DamageDocument11 pagesThe Different Types of Threats On The Internet, Which Can Create DamageHariharKaliaPas encore d'évaluation
- Promopedia-2020 CBS-IT C2ODocument72 pagesPromopedia-2020 CBS-IT C2OPrem Prem KumarPas encore d'évaluation
- CyberpdfDocument13 pagesCyberpdfrajput28shwPas encore d'évaluation
- CS Mid Que AnsDocument12 pagesCS Mid Que Ansaashi kareliyaPas encore d'évaluation
- Computer Network SecurityDocument15 pagesComputer Network SecurityRalph Gerahrd LlarinasPas encore d'évaluation
- Information System For ManagersDocument7 pagesInformation System For ManagerselmaPas encore d'évaluation
- Cyber CrimesDocument19 pagesCyber Crimesmalik hadiaPas encore d'évaluation
- Networks Internet E-Commerce Mobile Telephones Wireless Microphones Wireless Intercom Bluetooth Automatic Teller MachinesDocument6 pagesNetworks Internet E-Commerce Mobile Telephones Wireless Microphones Wireless Intercom Bluetooth Automatic Teller MachinessufiyanamujawarPas encore d'évaluation
- Module Ii-Activity IvDocument3 pagesModule Ii-Activity IvGeoffrey Vin GumatayPas encore d'évaluation
- WikcsdsDocument2 pagesWikcsdsrmaniquez415Pas encore d'évaluation
- 202004021910157821anurag Law Cyber CrimeDocument9 pages202004021910157821anurag Law Cyber CrimeUmer BhatPas encore d'évaluation
- Ict Contemporary Trends in Information and Communication TechnologyDocument17 pagesIct Contemporary Trends in Information and Communication TechnologySimonPas encore d'évaluation
- Cyber Crime: Theft of ServicesDocument38 pagesCyber Crime: Theft of ServicesSudeepta VermaPas encore d'évaluation
- Whitfield Diffie Martin Hellman: Key GenerationDocument3 pagesWhitfield Diffie Martin Hellman: Key GenerationSufiyan KhanPas encore d'évaluation
- Persistent Security For Electronic Documents: AbstractDocument9 pagesPersistent Security For Electronic Documents: Abstractnoor sabahPas encore d'évaluation
- Assignment 2Document6 pagesAssignment 2aniket senPas encore d'évaluation
- What Is CybercrimeDocument16 pagesWhat Is Cybercrimehunaiza khanPas encore d'évaluation
- Cyber Crime ClassDocument32 pagesCyber Crime Classlalit sainiPas encore d'évaluation
- Application Area of CryptographyDocument8 pagesApplication Area of CryptographySanjana Jaiswal100% (2)
- Internal Assessment ReportDocument14 pagesInternal Assessment Reportmanmeet chuggaPas encore d'évaluation
- Cyber Security IntroductionDocument44 pagesCyber Security IntroductionShivani100% (1)
- Cyber CrimesDocument7 pagesCyber CrimeslehvbPas encore d'évaluation
- Cyber SecurityDocument3 pagesCyber SecurityNew GeniePas encore d'évaluation
- Security and EthicsDocument6 pagesSecurity and EthicssramsahaPas encore d'évaluation
- Reasons For Cyber CrimeDocument5 pagesReasons For Cyber Crimeganesh_hacksPas encore d'évaluation
- Cyber LawDocument7 pagesCyber LawJyoti BhutiaPas encore d'évaluation
- Mis Assingnment 2Document6 pagesMis Assingnment 2AYESHA BOITAIPas encore d'évaluation
- 5Document6 pages5Arnav GudduPas encore d'évaluation
- Project ProposalDocument35 pagesProject ProposalAyomipo'Holuwasegun Oyesanya OyetugaPas encore d'évaluation
- Privacy Protection Based Access Control Scheme in Cloud-Based Services - 1crore ProjectsDocument5 pagesPrivacy Protection Based Access Control Scheme in Cloud-Based Services - 1crore ProjectsAshok ChelikaPas encore d'évaluation
- Digital SignatureDocument31 pagesDigital SignatureVipin KumarPas encore d'évaluation
- Session 2Document15 pagesSession 2Rumble kingPas encore d'évaluation
- Chapter 13: Digital SignaturesDocument6 pagesChapter 13: Digital Signaturesgraduation projectPas encore d'évaluation
- Information Systems Security LAB: Asymmetric CryptographyDocument11 pagesInformation Systems Security LAB: Asymmetric CryptographyAbdullah Al-HallakPas encore d'évaluation
- Ns Crypto Lab FinalDocument27 pagesNs Crypto Lab FinalNaga KalyanPas encore d'évaluation
- CB3491 NotesDocument192 pagesCB3491 NotesANITHARANI KPas encore d'évaluation
- NIS Slide 4Document28 pagesNIS Slide 4Soumak PoddarPas encore d'évaluation
- ISKLM Planning, and User's Guide PDFDocument180 pagesISKLM Planning, and User's Guide PDFTC Çapulcu Okan BaşarPas encore d'évaluation
- PDFDocument187 pagesPDFKrishnendu RarhiPas encore d'évaluation
- Mobile App Security Checklist 0.9.3Document47 pagesMobile App Security Checklist 0.9.3Ft C PondexterPas encore d'évaluation
- 10 SUBSET-037 v230Document100 pages10 SUBSET-037 v230wranghelPas encore d'évaluation
- Extracting Encryption Keys From RAMDocument10 pagesExtracting Encryption Keys From RAMChris100% (2)
- AES Algorithm Flow ChartDocument3 pagesAES Algorithm Flow Chartchernwei0% (1)
- EMV SWG NH20r2a Issuer Security Guidelines For 1st Gen August2018Document78 pagesEMV SWG NH20r2a Issuer Security Guidelines For 1st Gen August2018This FPas encore d'évaluation
- A Lightweight Data Sharing SchemeDocument15 pagesA Lightweight Data Sharing SchemeAbhishek Basnyat100% (1)
- Pros and Cons of Cryptography, Steganography and Perturbation TechniquesDocument6 pagesPros and Cons of Cryptography, Steganography and Perturbation Techniquesparitosh chandrakapurePas encore d'évaluation
- CSG Case Study - Barclays: Cryptography As A ServiceDocument4 pagesCSG Case Study - Barclays: Cryptography As A ServicerahulPas encore d'évaluation
- Secure Data Sharing in Cloud Computing Using Revocable Storage Identity Based Encryption PDFDocument4 pagesSecure Data Sharing in Cloud Computing Using Revocable Storage Identity Based Encryption PDFPriyanka vadapalliPas encore d'évaluation
- Fortigate Authentication 60Document217 pagesFortigate Authentication 60aykargilPas encore d'évaluation
- Cryptography and Network Security 1Document33 pagesCryptography and Network Security 1Priti PatilPas encore d'évaluation
- Cryptographic Techniques With CrypttoolDocument91 pagesCryptographic Techniques With CrypttoolRobin RohitPas encore d'évaluation
- Moserbaer CompleteDocument54 pagesMoserbaer CompleteRishabh SharmaPas encore d'évaluation
- د. محمد يونسClassical Encryption TechniquesDocument51 pagesد. محمد يونسClassical Encryption TechniquesMohammed Al-RadwanPas encore d'évaluation
- SEC577 Cryptography and Security MechanismsDocument18 pagesSEC577 Cryptography and Security MechanismsLuis MercadoPas encore d'évaluation
- EcommerceDocument12 pagesEcommerceGopal Chatterjee100% (1)
- Legal Issues of Electronic SignatureDocument13 pagesLegal Issues of Electronic SignatureParvathy KarthaPas encore d'évaluation
- S DES ProcedureDocument9 pagesS DES ProcedureRagz RaghavPas encore d'évaluation
- IT - Notes Sir OvaisDocument54 pagesIT - Notes Sir OvaisTauqeer AhmedPas encore d'évaluation