Académique Documents
Professionnel Documents
Culture Documents
Keamanan - Internet Security
Transféré par
IeMa HalimCopyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Keamanan - Internet Security
Transféré par
IeMa HalimDroits d'auteur :
Formats disponibles
10/25/2010
1
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Chapter 29
I nternet
Security
cr aw- i l l he cr aw- i l l ompani es, nc. ,
CONTENTS
INTRODUCTION
PRIVACY
DIGITAL SIGNATURE
SECURITY IN THE INTERNET
APPLICATION LAYER SECURITY
TRANSPORT LAYER SECURITY: TLS
SECURITY AT THE IP LAYER: IPSEC
FIREWALLS
10/25/2010
2
cr aw- i l l he cr aw- i l l ompani es, nc. ,
INTRODUCTION
29.1
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-1
Aspects of security
10/25/2010
3
cr aw- i l l he cr aw- i l l ompani es, nc. ,
PRIVACY
29.2
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-2
Secret-key encryption
10/25/2010
4
cr aw- i l l he cr aw- i l l ompani es, nc. ,
In secret-key encryption,
the same key is used by the sender
(for encryption)
and the receiver
(for decryption).
The key is shared.
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Secret-key encryption is often called
symmetric encryption because
the same key can
be used in both directions.
10/25/2010
5
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Secret-key encryption is
often used for long messages.
cr aw- i l l he cr aw- i l l ompani es, nc. ,
We discuss one secret-key
algorithm in Appendix E.
10/25/2010
6
cr aw- i l l he cr aw- i l l ompani es, nc. ,
KDC
can solve the problem
of secret-key distribution.
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-3
Public-key encryption
10/25/2010
7
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Public-key algorithms are more
efficient for short messages.
cr aw- i l l he cr aw- i l l ompani es, nc. ,
A
CA
can certify the binding between
a public key and the owner.
10/25/2010
8
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-4
Combination
cr aw- i l l he cr aw- i l l ompani es, nc. ,
To have the advantages of both
secret-key and public-key
encryption, we can encrypt the secret key
using the public key and encrypt
the message using the secret key.
10/25/2010
9
cr aw- i l l he cr aw- i l l ompani es, nc. ,
DIGITAL SIGNATURE
29.3
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-5
Signing the whole document
10/25/2010
10
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Digital signature cannot be
achieved using only secret keys.
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Digital signature does not
provide privacy.
If there is a need for privacy,
another layer of
encryption/decryption
must be applied.
10/25/2010
11
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-6
Signing the digest
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-7
Sender site
10/25/2010
12
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-8
Receiver site
cr aw- i l l he cr aw- i l l ompani es, nc. ,
SECURITY IN THE
INTERNET
29.4
10/25/2010
13
cr aw- i l l he cr aw- i l l ompani es, nc. ,
APPLICTION LAYER
SECURITY
29.5
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-9
PGP at the sender site
10/25/2010
14
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-10
PGP at the receiver site
cr aw- i l l he cr aw- i l l ompani es, nc. ,
TRANSPORT LAYER
SECURITY
(TLS)
29.6
10/25/2010
15
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-11
Position of TLS
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-12
Handshake protocol
10/25/2010
16
cr aw- i l l he cr aw- i l l ompani es, nc. ,
SECURITY AT THE
IP LAYER
(IPSec)
29.7
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-13
Authentication
10/25/2010
17
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-14
Header format
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-15
ESP
10/25/2010
18
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-16
ESP format
cr aw- i l l he cr aw- i l l ompani es, nc. ,
FIREWALLS
29.8
10/25/2010
19
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-17
Firewall
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-18
Packet-filter firewall
10/25/2010
20
cr aw- i l l he cr aw- i l l ompani es, nc. ,
A packet-filter firewall filters
at the network or transport layer.
cr aw- i l l he cr aw- i l l ompani es, nc. ,
Figure 29-19
Proxy firewall
10/25/2010
21
cr aw- i l l he cr aw- i l l ompani es, nc. ,
A proxy firewall
filters at the application layer.
Vous aimerez peut-être aussi
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (587)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (265)
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (73)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (119)
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)
- Method Statement of Static Equipment ErectionDocument20 pagesMethod Statement of Static Equipment Erectionsarsan nedumkuzhi mani100% (4)
- FEM IntroductionDocument47 pagesFEM IntroductionShanmuga RamananPas encore d'évaluation
- Financial ManagementDocument21 pagesFinancial ManagementsumanPas encore d'évaluation
- Anthony Flagg's Complaint Against Eddie LongDocument23 pagesAnthony Flagg's Complaint Against Eddie LongRod McCullom100% (1)
- Lirik and Chord LaguDocument5 pagesLirik and Chord LaguRyan D'Stranger UchihaPas encore d'évaluation
- DS 20230629 SG3300UD-MV SG4400UD-MV Datasheet V16 ENDocument2 pagesDS 20230629 SG3300UD-MV SG4400UD-MV Datasheet V16 ENDragana SkipinaPas encore d'évaluation
- Shri Siddheshwar Co-Operative BankDocument11 pagesShri Siddheshwar Co-Operative BankPrabhu Mandewali50% (2)
- HealthFlex Dave BauzonDocument10 pagesHealthFlex Dave BauzonNino Dave Bauzon100% (1)
- Enhancing reliability of CRA piping welds with PAUTDocument10 pagesEnhancing reliability of CRA piping welds with PAUTMohsin IamPas encore d'évaluation
- Critical Values For The Dickey-Fuller Unit Root T-Test StatisticsDocument1 pageCritical Values For The Dickey-Fuller Unit Root T-Test Statisticswjimenez1938Pas encore d'évaluation
- Rasna Project Report FinalDocument31 pagesRasna Project Report FinalReet KanjilalPas encore d'évaluation
- VBScriptDocument120 pagesVBScriptdhanaji jondhalePas encore d'évaluation
- Books 2738 0Document12 pagesBooks 2738 0vinoohmPas encore d'évaluation
- Bid Document PDFDocument125 pagesBid Document PDFAzharudin ZoechnyPas encore d'évaluation
- Curriculum Vitae 2010Document11 pagesCurriculum Vitae 2010ajombilePas encore d'évaluation
- MT R 108 000 0 000000-0 DHHS B eDocument68 pagesMT R 108 000 0 000000-0 DHHS B eRafal WojciechowskiPas encore d'évaluation
- Lenex 3.0 Technical DocumentationDocument31 pagesLenex 3.0 Technical DocumentationGalina DPas encore d'évaluation
- Nexus Undercarriage Cross Reference GuideDocument185 pagesNexus Undercarriage Cross Reference GuideRomanPas encore d'évaluation
- Terminología Sobre Reducción de Riesgo de DesastresDocument43 pagesTerminología Sobre Reducción de Riesgo de DesastresJ. Mario VeraPas encore d'évaluation
- University Assignment Report CT7098Document16 pagesUniversity Assignment Report CT7098Shakeel ShahidPas encore d'évaluation
- High Uric CidDocument3 pagesHigh Uric Cidsarup007Pas encore d'évaluation
- Sierra Wireless AirPrimeDocument2 pagesSierra Wireless AirPrimeAminullah -Pas encore d'évaluation
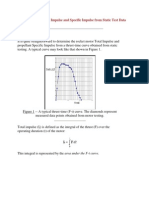
- Determining Total Impulse and Specific Impulse From Static Test DataDocument4 pagesDetermining Total Impulse and Specific Impulse From Static Test Datajai_selvaPas encore d'évaluation
- ETP Research Proposal Group7 NewDocument12 pagesETP Research Proposal Group7 NewlohPas encore d'évaluation
- Fall Protection ANSIDocument5 pagesFall Protection ANSIsejudavisPas encore d'évaluation
- Virgilio S. Delima V. Susan Mercaida Gois GR NO. 178352 - June 17, 2008 FactsDocument6 pagesVirgilio S. Delima V. Susan Mercaida Gois GR NO. 178352 - June 17, 2008 FactsNikki BarenaPas encore d'évaluation
- Organization Structure GuideDocument6 pagesOrganization Structure GuideJobeth BedayoPas encore d'évaluation
- Industry Life Cycle-Plant Based CaseDocument3 pagesIndustry Life Cycle-Plant Based CaseRachelle BrownPas encore d'évaluation
- Amended ComplaintDocument38 pagesAmended ComplaintDeadspinPas encore d'évaluation
- Funded African Tech Startups 2020Document13 pagesFunded African Tech Startups 2020LoPas encore d'évaluation