Académique Documents
Professionnel Documents
Culture Documents
Ijret - Transmission of Cryptic Text Using Rotational Visual Cryptography
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Ijret - Transmission of Cryptic Text Using Rotational Visual Cryptography
Droits d'auteur :
Formats disponibles
IJRET: International Journal of Research in Engineering and Technology
eISSN: 2319-1163 | pISSN: 2321-7308
TRANSMISSION OF CRYPTIC TEXT USING ROTATIONAL VISUAL CRYPTOGRAPHY
P. R. Sushma Priya1, P. Vijaya Bharati2
1
student, 2Asst.Prof.,Department of CSE, Vignans Institute of Engineering for Women, Visakhapatnam, Andhra Pradesh, India, sushmapriya_pr3135@yahoo.co.in, pvijayabharati@gmail.com
Abstract
Today security is an important thing when we need to transmit data from one location to another safely. In this paper we are proposing an empirical model of secure data transmission technique with a hybrid approach of Cryptography, Stegnography and rotational analysis. In the initial phase, data is encrypted with DES algorithm with the help of Session key which is generated by the Diffie-Hellman Key exchange Algorithm. In the second phase Cipher Data is hidden into the cover images LSB to form the stego image, by considering security as the optimal security parameter. In the third phase, the Stego image is rotated with specific angle. At the receiver end, the image is de-rotated and the cipher information from the LSB is retrieved and the cipher information is decrypted with session key. This scheme achieves lossless recovery and is difficult to decrypt by the attackers.
Keywords: Cryptography, Stegnography, Visual Cryptography, DES, Diffie-Hellman Algorithm, Session Key ---------------------------------------------------------------------***------------------------------------------------------------------------1. INTRODUCTION
Cryptography is the method that allows information to be sent in a secure form in such a way that the only receiver is able to retrieve the information. Now-a-days, cryptography has many commercial applications. It provides high level of privacy for individuals and groups. However, the main purpose of the cryptography is not only to provide confidentiality but also provide solutions for other problems like: data integrity, authentication, non-repudiation. Presently continuous researches on the new cryptographic algorithms are going on. However, it is very difficult to find out the specific algorithm they must consider various factors like: security, the features of algorithm, the time complexity and space complexity. Visual Cryptography (VC) is a new technique of cryptographic scheme, which can decrypt encrypted images without any mathematical computations but with the help of Human Visual System (HVS). Visual cryptography scheme has many applications like secret sharing scheme, Copyright protection, Halftoning process and Watermarking. There are various schemes of Visual Cryptography. Visual Cryptography scheme can also be used for authentication and identification process (visual authentication and identification)[11]. Steganography is the art and science of invisible communication. This is accomplished through hiding information in other information, thus hiding the existence of the communicated information. The word steganography is derived from the Greek words stegos meaning cover and grafia meaning writing , defining it as covered writing. In image steganography the information is hidden exclusively in images [8]. The main feature of the encryption/decryption process implementation is the generation of the encryption key. Our hybrid approach achieves the optimal security during the transmission of data over the network. Due to three levels of security, cipher text cannot be decrypted and the time required to break the cipher to plain is more. Our approach follows the conversion of plain text to cipher text, hiding the cipher information in the image pixels and rotating the image with the required or specific angle to prevent the unauthorized access over the network [5]. The main difference between Cryptography and stegnography is, Cryptography is a process of converting a plain text to cipher text where as Stegnography is a process of hiding the data into the cover medias [3]. Image rotation enhances our security feature by integrating with our previous stegnography because of the noise factors we regularized our approach to few specific angles of rotation of pixels in the image.
2. RELATED WORK
As our initial research starts with the different types of attacks, mainly classified as Active attacks (Interruption, modification, fabrication) and passive attacks(Interception) during the transmission of data, Cryptography introduced to convert the formatted text to unformatted text through the various cryptographic algorithms[1][2].
__________________________________________________________________________________________
Volume: 02 Issue: 10 | Oct-2013, Available @ http://www.ijret.org 345
IJRET: International Journal of Research in Engineering and Technology
Now-a-days hackers and attackers are also very familiar with cryptanalysis(cracking of ciphers or unformatted texts),so cryptography may not resolve the problem of security, later stegnography is introduced for hiding the data into the image, which is a simple implementation issue and human eye undetectable changes are seen. In this process we consider these two parameters i.e., cover image and the message are embedded and form the stego image. Even though various cryptography and stegnographic approaches are developed, security is still an importantant research issue in the field of network security [6][7]. Here we are introducing a new approach that uses image rotational analysis along with the cryptographic and Stegongraphic techniques. In the traditional process of visual cryptography, data can be added to the Cover image to convert it into stego image and the stego image can be divided into number of shares, to retrieve the data, we need to combine the shares, there is a noise issue during the data retrieval. In our approach there is no issue of noise during the stego image conversion or during image rotation.
eISSN: 2319-1163 | pISSN: 2321-7308
3. PROPOSED MODEL
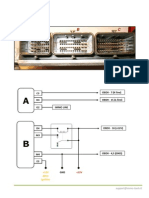
We are proposing a hybrid approach with both cryptography and rotational visual cryptography for secure data transmission over the network. In our approach, initially the sender converts the plain text to cipher text with Data Encryption Standard (DES) algorithm. The reason to choose DES and DiffieHellman algorithms in our paper is, DES is most certified algorithm than the many traditional cryptographic algorithms. Implementation of DES is not complex and it is fast in hardware and relatively fast in software. But the DES requires a 56-bit session key for the process of encryption and decryption, which can be achieved by the Diffie-Hellman key exchange protocol. After the session key generation, the sender converts the plain text to cipher text by DES algorithm with the key generated by the key exchange protocol (DiffieHellman)[10]. It is one of the most efficient Symmetric key approach. No individual user can create the session key, without using the other half part of the receiver or sender. Diffie-Hellman ephemeral key exchange provides perfect forward secrecy. Computational complexity is low during the key calculations and not much expensive. The cover image is selected and is converted into binary format and the cipher text is embedded into the LSB of the binary format of the image which forms the stego image. The stego image is rotated by some specific angle and is sent to receiver. The reverse process is done at the receiver end. The receiver receives the rotated image and the encrypted angle with the same session key exchanged by Diffie-Hellman key exchange protocol. The entire process is shown in architectural Fig-1. Fig-1: Architecture
4. LSB APPROACH
LSB (Least Significant Bit) substitution is the process of adjusting the least significant bit pixels of the carrier image. It is a simple approach for embedding message and the image. The Least Significant Bit insertion varies according to number of bits in an image. For an 8 bit image, the least significant bit i.e., the 8th bit of each byte of the image is changed with the bit of cipher text. For a 24 bit image, the colors of each component like RGB (red, green and blue) are changed. LSB is effective in using BMP images since the compression in BMP is lossless [4].
5. ROTATIONAL ANALYSIS
Rotational Analysis is a new approach where the image is rotated with an angle instead of sending it directly. In our approach, after hiding the data in the image, it is rotated with a specific angle by the sender and is sent to the receiver. The angle is transmitted in encrypted format using the session key generated by Diffie-Hellman Key Exchange Algorithm. In the reverse process, receiver decrypts the angle and than of 900,1800,2700, de-rotates the image with the same angle, extracts the cipher information from the stego image (i.e., least significant bits of the pixels of image) then converts the cipher information to plain text with the DES algorithm followed by the key generated with Diffie- Hellman Key Exchange.
__________________________________________________________________________________________
Volume: 02 Issue: 10 | Oct-2013, Available @ http://www.ijret.org 346
IJRET: International Journal of Research in Engineering and Technology
cryptography, cryptography.
eISSN: 2319-1163 | pISSN: 2321-7308
stegnogrpahy and rotational visual
6. EXPERIMENTAL RESULT
Fig-2 shows the plain text , Fig-3 shows the cipher text, Fig-4 shows the binary text, Fig-5 shows the cover image before embedding data into it, Fig-6 shows the stego image (i.e., after data embedding) and Fig-7 shows the rotated image as follows
FUTURE SCOPE
We can enhance our approach by using the advanced cryptographic algorithms like AES, but Computational complexity is the major issue with the advanced algorithms. We designed our architecture with some specific static angles, we can enhance our system by providing the flexibility of rotation of image with any angle. We can also enhance our approach with elliptic curve key exchange Algorithm for more secure session key generation.
REFERENCES
[1] A. Forouzan.,: " Cryptography and Network Security ", First Edition. McGraw-Hill, (2007), USA. [2] R Hamamreh., M Farajallah., " Design of a Robust Cryptosystem Algorithm for Non-Invertible Matrices Based on Hill Cipher ". International Journal of Computer Science and Network Security, (2009): Vol (9), pp: 12-21. [3] J Hoffstein., et al, "An Introduction to Mathematical Cryptography ", First Edition. Springer Science & Business Media, (2008):, Germany. [4] H.Kenneth, Elementary Number Theory and Its Applications " Third Edition. Addison-Wesley, (1992): Germany. [5] M.Lucas, Thomas Jefferson wheel cipher ", Monticello Research Department, Thomas Jefferson Foundation, Charlottesville, (1995):, VA. [6] Steganography and steganalysis-Robert Krenn, Internet Publication, March 2004 [7] Steganographic Techniques and their use in an OpenSystems Environment- Bret Dunbar, The Information Security Reading Room, SANS Institute 2002 [8] Steganography Primer - Ruid, Computer Academic underground,2004 [9] Image Compression and Discrete Cosine Transform - Ken Cabeen and Peter Gent,Math 45 College of the Redwoods,1998 [10] Practical Data Hiding in TCP/IP - Kamran Ahsan and Deepa Kundur Multimedia and Security Workshop at ACM Multimedia, Juan-les-Pins, France, Friday, Dec 6th, 2002 [11] "Rotation Visual Cryptography Using Basic (2, 2) Scheme", International Journal of Computing Science and Communication Technologies, VOL. 3, NO. 2, Jan. 2011. (ISSN 0974-3375) ,1B. Dinesh Reddy, 2V. Valli Kumari, 3KVSVN Raju, 4Y.H. Prassanna Raju 1Vignan Institute of Information Technology.
While in the reverse process, we derotate the image with the specific angle and retrieve the cipher information from the LSBs of the stego image to retrieve the final cover image and plain text.
CONCLUSIONS
We are concluding our research issue with empirical approach of data hiding through rotational visual cryptography. Our experimental result shows an efficient performance results than the traditional approach with hybrid mechanism of
__________________________________________________________________________________________
Volume: 02 Issue: 10 | Oct-2013, Available @ http://www.ijret.org 347
IJRET: International Journal of Research in Engineering and Technology
eISSN: 2319-1163 | pISSN: 2321-7308
BIOGRAPHIES
P. R. Sushma Priya received the M.C.A degree from JNTU, Hyderabad in 2007. She is pursuing the M. Tech( Computer Science Engineering ) degree from JNTU, Kakinada. She worked as an assistant professor in Vignans Institute of Engineering, Visakhapatnam, Andhra Pradesh, India. P. Vijaya Bharati received the M.Sc degree in Computer Science from Gitam University in 2004, Visakhapatnam and the M.Tech degree in Computer Science from Vignan University in 2009. She is pursuing her Ph.D from Gitam University, Visakhapatnam. Presently, she is working as an Assistant Professor in Vignans Institute of Engineering for Women. Her research interests in areas of Computer Networks, Mobile Computing, DSP, MATLAB, Data Mining, Sensor Networks. She attends so many Workshops and National & International Conferences.
__________________________________________________________________________________________
Volume: 02 Issue: 10 | Oct-2013, Available @ http://www.ijret.org 348
Vous aimerez peut-être aussi
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- Wind Damage To Buildings, Infrastrucuture and Landscape Elements Along The Beach Road at VisakhapatnamDocument10 pagesWind Damage To Buildings, Infrastrucuture and Landscape Elements Along The Beach Road at VisakhapatnamInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- Wind Damage To Trees in The Gitam University Campus at Visakhapatnam by Cyclone HudhudDocument11 pagesWind Damage To Trees in The Gitam University Campus at Visakhapatnam by Cyclone HudhudInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5794)
- Enhancing Post Disaster Recovery by Optimal Infrastructure Capacity BuildingDocument8 pagesEnhancing Post Disaster Recovery by Optimal Infrastructure Capacity BuildingInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- Flood Related Disasters Concerned To Urban Flooding in Bangalore, IndiaDocument8 pagesFlood Related Disasters Concerned To Urban Flooding in Bangalore, IndiaInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (894)
- Impact of Flood Disaster in A Drought Prone Area - Case Study of Alampur Village of Mahabub Nagar DistrictDocument5 pagesImpact of Flood Disaster in A Drought Prone Area - Case Study of Alampur Village of Mahabub Nagar DistrictInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (399)
- Role of Voluntary Teams of Professional Engineers in Dissater Management - Experiences From Gujarat EarthquakeDocument6 pagesRole of Voluntary Teams of Professional Engineers in Dissater Management - Experiences From Gujarat EarthquakeInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Shear Strength of RC Deep Beam Panels - A ReviewDocument15 pagesShear Strength of RC Deep Beam Panels - A ReviewInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- Effect of Lintel and Lintel Band On The Global Performance of Reinforced Concrete Masonry In-Filled FramesDocument9 pagesEffect of Lintel and Lintel Band On The Global Performance of Reinforced Concrete Masonry In-Filled FramesInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- Groundwater Investigation Using Geophysical Methods - A Case Study of Pydibhimavaram Industrial AreaDocument5 pagesGroundwater Investigation Using Geophysical Methods - A Case Study of Pydibhimavaram Industrial AreaInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (587)
- Cyclone Disaster On Housing and Coastal AreaDocument7 pagesCyclone Disaster On Housing and Coastal AreaInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (265)
- Low Cost Wireless Sensor Networks and Smartphone Applications For Disaster Management and Improving Quality of LifeDocument5 pagesLow Cost Wireless Sensor Networks and Smartphone Applications For Disaster Management and Improving Quality of LifeInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Likely Impacts of Hudhud On The Environment of VisakhapatnamDocument3 pagesLikely Impacts of Hudhud On The Environment of VisakhapatnamInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (73)
- Monitoring and Assessment of Air Quality With Reference To Dust Particles (Pm10 and Pm2.5) in Urban EnvironmentDocument3 pagesMonitoring and Assessment of Air Quality With Reference To Dust Particles (Pm10 and Pm2.5) in Urban EnvironmentInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- Hudhud Cyclone - A Severe Disaster in VisakhapatnamDocument8 pagesHudhud Cyclone - A Severe Disaster in VisakhapatnamInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (344)
- Review Study On Performance of Seismically Tested Repaired Shear WallsDocument7 pagesReview Study On Performance of Seismically Tested Repaired Shear WallsInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- A Geophysical Insight of Earthquake Occurred On 21st May 2014 Off Paradip, Bay of BengalDocument5 pagesA Geophysical Insight of Earthquake Occurred On 21st May 2014 Off Paradip, Bay of BengalInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- Cpw-Fed Uwb Antenna With Wimax Band-Notched CharacteristicsDocument5 pagesCpw-Fed Uwb Antenna With Wimax Band-Notched CharacteristicsInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2219)
- Detection of Hazard Prone Areas in The Upper Himalayan Region in Gis EnvironmentDocument9 pagesDetection of Hazard Prone Areas in The Upper Himalayan Region in Gis EnvironmentInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Comparative Study of The Forces in G+5 and G+10 Multi Storied Buildings Subjected To Different Wind SpeedsDocument10 pagesComparative Study of The Forces in G+5 and G+10 Multi Storied Buildings Subjected To Different Wind SpeedsInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Can Fracture Mechanics Predict Damage Due Disaster of StructuresDocument6 pagesCan Fracture Mechanics Predict Damage Due Disaster of StructuresInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Assessment of Seismic Susceptibility of RC BuildingsDocument4 pagesAssessment of Seismic Susceptibility of RC BuildingsInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Coastal Zones - Seismic Vulnerability An Analysis From East Coast of IndiaDocument4 pagesCoastal Zones - Seismic Vulnerability An Analysis From East Coast of IndiaInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Effect of Hudhud Cyclone On The Development of Visakhapatnam As Smart and Green City - A Case StudyDocument4 pagesEffect of Hudhud Cyclone On The Development of Visakhapatnam As Smart and Green City - A Case StudyInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- Challenges in Oil and Gas Industry For Major Fire and Gas Leaks - Risk Reduction MethodsDocument4 pagesChallenges in Oil and Gas Industry For Major Fire and Gas Leaks - Risk Reduction MethodsInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Developing of Decision Support System For Budget Allocation of An R&D OrganizationDocument6 pagesDeveloping of Decision Support System For Budget Allocation of An R&D OrganizationInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Disaster Recovery Sustainable HousingDocument4 pagesDisaster Recovery Sustainable HousingInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Brain Tumor Segmentation Using Asymmetry Based Histogram Thresholding and K-Means ClusteringDocument4 pagesBrain Tumor Segmentation Using Asymmetry Based Histogram Thresholding and K-Means ClusteringInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Analytical Solutions For Square Shape PressureDocument4 pagesAnalytical Solutions For Square Shape PressureInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (119)
- Rate Adaptive Resource Allocation in Ofdma Using Bees AlgorithmDocument5 pagesRate Adaptive Resource Allocation in Ofdma Using Bees AlgorithmInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- IT Policy Ensures Data ProtectionDocument16 pagesIT Policy Ensures Data ProtectionHesham Elsayed100% (1)
- 3DS Information Security Overview ExternalDocument15 pages3DS Information Security Overview ExternalRaut AbhimanPas encore d'évaluation
- Time StampDocument1 pageTime StampRobert KeyPas encore d'évaluation
- Penetration Testing Services and Solutions: This Is One Test You MayDocument4 pagesPenetration Testing Services and Solutions: This Is One Test You MayIR AwakenedPas encore d'évaluation
- A Survey On Cyber Security Threats and Their SolutionsDocument8 pagesA Survey On Cyber Security Threats and Their SolutionsIJRASETPublicationsPas encore d'évaluation
- Cyber Security Goals: 1. ConfidentialityDocument12 pagesCyber Security Goals: 1. Confidentialitydoctorbabu01430 949043101111Pas encore d'évaluation
- Update KONAMI ID InformationDocument1 pageUpdate KONAMI ID InformationPetros ZafiroulisPas encore d'évaluation
- Computer, Network & Internet SecurityDocument325 pagesComputer, Network & Internet Securityapi-3850169100% (3)
- Defense in Depth PDFDocument9 pagesDefense in Depth PDFYasir MushtaqPas encore d'évaluation
- 15: Security and Cyber LawsDocument49 pages15: Security and Cyber LawsPixelPas encore d'évaluation
- Inmo ToolsDocument15 pagesInmo ToolsEugenio BenitezPas encore d'évaluation
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)
- CSCUv2 Module 00 Introduction v3Document14 pagesCSCUv2 Module 00 Introduction v3Fina LestariPas encore d'évaluation
- Cryptography and Network Security Course LecturesDocument4 pagesCryptography and Network Security Course LecturesMadan GopalPas encore d'évaluation
- CISSP Cheat Sheet SeriesDocument8 pagesCISSP Cheat Sheet Seriesmayurigupta00793% (30)
- Digital Investigation: Myungseo Park, Giyoon Kim, Younjai Park, Insoo Lee, Jongsung KimDocument7 pagesDigital Investigation: Myungseo Park, Giyoon Kim, Younjai Park, Insoo Lee, Jongsung KimRendyPas encore d'évaluation
- Nginx Hardening ChecklistDocument1 pageNginx Hardening Checklistoverdigo100% (1)
- Meritas Cybersecurity Standards: January 2020Document1 pageMeritas Cybersecurity Standards: January 2020Roy Adig Menacho CespedesPas encore d'évaluation
- Info Security Assi.Document2 pagesInfo Security Assi.Emmanuel Appiah100% (1)
- Social EngineeringDocument4 pagesSocial EngineeringkhonelloPas encore d'évaluation
- Enterprise Information Security Guide 2023Document10 pagesEnterprise Information Security Guide 2023Guillermo ValdèsPas encore d'évaluation
- C725 Review QuestionsDocument5 pagesC725 Review QuestionsJoshua FarrowPas encore d'évaluation
- Grammarly CookiesDocument4 pagesGrammarly CookiesGene Rose TeraniaPas encore d'évaluation
- CEH Master BrochureDocument14 pagesCEH Master Brochureahfuoahrf0384100% (2)
- Cyber Security BasicsDocument36 pagesCyber Security BasicsTausif RazaPas encore d'évaluation
- Course Syllabus Penetration Testing and Ethical Hacking: Brought To You byDocument7 pagesCourse Syllabus Penetration Testing and Ethical Hacking: Brought To You bymedtrachiPas encore d'évaluation
- Content of The Torrent E-BooksDocument5 pagesContent of The Torrent E-BooksShrikar TarePas encore d'évaluation
- Ebook - A Comprehensive Guide To Preventing Supply Chain AttacksDocument13 pagesEbook - A Comprehensive Guide To Preventing Supply Chain AttacksEduardo ManchegoPas encore d'évaluation
- KPMDocument10 pagesKPMjgvivasPas encore d'évaluation
- The Guide To Cyber Investigations-Second EditionDocument227 pagesThe Guide To Cyber Investigations-Second EditionMeir ZushnovPas encore d'évaluation
- Public-Key Cryptography: Data and Network Security 1Document15 pagesPublic-Key Cryptography: Data and Network Security 1asadPas encore d'évaluation
- AI and Machine Learning for Coders: A Programmer's Guide to Artificial IntelligenceD'EverandAI and Machine Learning for Coders: A Programmer's Guide to Artificial IntelligenceÉvaluation : 4 sur 5 étoiles4/5 (2)
- Scary Smart: The Future of Artificial Intelligence and How You Can Save Our WorldD'EverandScary Smart: The Future of Artificial Intelligence and How You Can Save Our WorldÉvaluation : 4.5 sur 5 étoiles4.5/5 (54)
- ChatGPT Millionaire 2024 - Bot-Driven Side Hustles, Prompt Engineering Shortcut Secrets, and Automated Income Streams that Print Money While You Sleep. The Ultimate Beginner’s Guide for AI BusinessD'EverandChatGPT Millionaire 2024 - Bot-Driven Side Hustles, Prompt Engineering Shortcut Secrets, and Automated Income Streams that Print Money While You Sleep. The Ultimate Beginner’s Guide for AI BusinessPas encore d'évaluation
- ChatGPT Side Hustles 2024 - Unlock the Digital Goldmine and Get AI Working for You Fast with More Than 85 Side Hustle Ideas to Boost Passive Income, Create New Cash Flow, and Get Ahead of the CurveD'EverandChatGPT Side Hustles 2024 - Unlock the Digital Goldmine and Get AI Working for You Fast with More Than 85 Side Hustle Ideas to Boost Passive Income, Create New Cash Flow, and Get Ahead of the CurvePas encore d'évaluation
- Generative AI: The Insights You Need from Harvard Business ReviewD'EverandGenerative AI: The Insights You Need from Harvard Business ReviewÉvaluation : 4.5 sur 5 étoiles4.5/5 (2)
- Mastering Large Language Models: Advanced techniques, applications, cutting-edge methods, and top LLMs (English Edition)D'EverandMastering Large Language Models: Advanced techniques, applications, cutting-edge methods, and top LLMs (English Edition)Pas encore d'évaluation
- Who's Afraid of AI?: Fear and Promise in the Age of Thinking MachinesD'EverandWho's Afraid of AI?: Fear and Promise in the Age of Thinking MachinesÉvaluation : 4.5 sur 5 étoiles4.5/5 (12)