Académique Documents
Professionnel Documents
Culture Documents
Study of Routing Protocols in Mobile Ad Hoc Networks
Transféré par
seventhsensegroup0 évaluation0% ont trouvé ce document utile (0 vote)
20 vues4 pagesMobile ad hoc networks (MANETs) are rapidly
evolving as an important area of mobility. MANETs are
infrastructure less autonomous collection of mobile users that
communicate over relatively bandwidth constrained wireless
links. Due to mobile nature of nodes, the network topology may
change rapidly and unpredictably time to time. The network is
decentralized, where all network activity including discovering
the topology and delivering messages must be executed by the
nodes themselves, i.e., routing functionality will be incorporated
into mobile nodes. Many routing algorithms have been
proposed and developed for accomplishing this task.
Therefore, it is difficult to determine which protocol performs
best under different situations. Hence, this paper presents
review of routing protocols.
Titre original
Study of Routing Protocols in Mobile Ad Hoc
Networks
Copyright
© © All Rights Reserved
Formats disponibles
PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentMobile ad hoc networks (MANETs) are rapidly
evolving as an important area of mobility. MANETs are
infrastructure less autonomous collection of mobile users that
communicate over relatively bandwidth constrained wireless
links. Due to mobile nature of nodes, the network topology may
change rapidly and unpredictably time to time. The network is
decentralized, where all network activity including discovering
the topology and delivering messages must be executed by the
nodes themselves, i.e., routing functionality will be incorporated
into mobile nodes. Many routing algorithms have been
proposed and developed for accomplishing this task.
Therefore, it is difficult to determine which protocol performs
best under different situations. Hence, this paper presents
review of routing protocols.
Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
20 vues4 pagesStudy of Routing Protocols in Mobile Ad Hoc Networks
Transféré par
seventhsensegroupMobile ad hoc networks (MANETs) are rapidly
evolving as an important area of mobility. MANETs are
infrastructure less autonomous collection of mobile users that
communicate over relatively bandwidth constrained wireless
links. Due to mobile nature of nodes, the network topology may
change rapidly and unpredictably time to time. The network is
decentralized, where all network activity including discovering
the topology and delivering messages must be executed by the
nodes themselves, i.e., routing functionality will be incorporated
into mobile nodes. Many routing algorithms have been
proposed and developed for accomplishing this task.
Therefore, it is difficult to determine which protocol performs
best under different situations. Hence, this paper presents
review of routing protocols.
Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 4
International Journal of Computer Trends and Technology (IJCTT) volume 9 number 2 Mar 2014
ISSN: 2231-2803 http://www.ijcttjournal.org Page 82
Study of Routing Protocols in Mobile Ad Hoc
Networks
Nitin Goyat
#1
, Mr. Anshul Anand
+2
#
M.Tech Student, Department of CSE, Shri Baba Mastnath Engineering College, Rohtak (INDIA)
+
Assistant Professor, Department of CSE, Shri Baba Mastnath Engineering College, Rohtak (INDIA)
Abstract : Mobile ad hoc networks (MANETs) are rapidly
evolving as an important area of mobility. MANETs are
infrastructure less autonomous collection of mobile users that
communicate over relatively bandwidth constrained wireless
links. Due to mobile nature of nodes, the network topology may
change rapidly and unpredictably time to time. The network is
decentralized, where all network activity including discovering
the topology and delivering messages must be executed by the
nodes themselves, i.e., routing functionality will be incorporated
into mobile nodes. Many routing algorithms have been
proposed and developed for accomplishing this task.
Therefore, it is difficult to determine which protocol performs
best under different situations. Hence, this paper presents
review of routing protocols.
Keywords: MANET, ad hoc, AODV, DSR, TORA.
I. INTRODUCTION
A mobile ad hoc network ( MANET) is a kind of
wireless network without centralized administration or
fixed network infrastructure in which nodes communicate
over relatively bandwidth constrained wireless links and
performrouting discovery and routing maintenance in a self-
organized way. Due to mobile nature of nodes, the network
topology may change rapidly and unpredictably time to time.
The network is decentralized, where all network activity
including discovering the topology and delivering messages
must be executed by the nodes themselves, i.e. routing
functionality will be incorporated into mobile nodes. Due to
these reasons routing in MANETs is a challenging task.
Multicast plays an important role in MANET.
Nowadays the MANET enables many applications in
the areas of emergency operations, disaster relief efforts. The
Mobile Ad hoc network is one of most commonly used
wireless network. As the number of user increases MANET
suffer from most common network problems like congestion,
packet loss, intrusion etc.
II. ROUTING PROTOCOLS in MANET
Protocol Classifications
Depending on how protocols handle data packets from
source to destination, MANET routing protocols are broadly
classified into three categories (Fig 1): Proactive, Reactive
and Hybrid protocols.
Fig 1 : Routing protocols in MANET
A. Proactive Protocols
Proactive protocols table driven protocols in which every
node maintains one or more tables representing the entire
topology of the network. These tables are updated regularly in
order to maintain up-to-date routing information fromeach
node to every other node. Data Packets are transferred over
the predefined route specified in the routing table. For
maintenance of up to date routing information, information
needs to be exchanges in-between nodes in topology on
regular basis, leading to high overhead on network.
Example protocols: DSDV, WRP, OLSR (Optimized Link
State Routing)
B. Reactive Protocols
These types of protocols are also called as On Demand
Routing Protocols where the routes are not predefined for
routing table. This type of routing creates routes only when
desired by source node. When a node requires a route to a
destination, it initiates a route discovery process within the
network. This route discovery mechanism is based on
algorithmwhich employs on the technique that a node just
broadcasts the packet to all of its neighbours and intermediate
nodes just forward that packet to their neighbours. This is a
repetitive technique until it reaches the destination. Reactive
techniques have smaller routing overheads but higher latency.
Example Protocols: DSR, AODV
International Journal of Computer Trends and Technology (IJCTT) volume 9 number 2 Mar 2014
ISSN: 2231-2803 http://www.ijcttjournal.org Page 83
C. Hybrid Protocols
Hybrid protocols are the combinations both On Demand
and Table driven routing protocols. Hybrid protocol has
advantages of both reactive and proactive protocols and as a
result, routes are found quickly in the routing zone.
Example Protocol: ZRP (Zone Routing Protocol)
III. AODV (The Ad hoc On Demand Distance Vector)
The Ad hoc On Demand Distance Vector (AODV) routing
algorithmis a routing protocol designed for ad hoc mobile
networks. AODV is the most efficient on demand protocol
used in MANET. AODV is capable of both unicast and
multicast routing. AODV is an on demand algorithm, which
means that it builds routes between nodes only as desired by
source nodes and maintains these routes as long as they are
needed by the source. Additionally, AODV forms trees which
connect multicast group members. The trees are composed of
the group members and the nodes, needed to connect the
members. AODV uses sequence numbers to ensure the
freshness of routes.
An important feature of AODV is the maintenance of time-
based states in each node: a routing entry not recently used is
expired. If a route is broken the neighbours can be notified.
Route discovery is based on query and reply cycles, and route
information is stored in all intermediate nodes along the
route in the form of route table entries. Control packets
are used to accomplish above task are as follows : routing
request message (RREQ) is broadcasted by a node
requiring a route to another node, routing reply message
(RREP) is unicast back to the source of RREQ, and route error
message (RERR) is sent to notify other nodes of the loss of
the link. HELLO messages are used for detecting and
monitoring links to neighbours.
Characteristics of AODV
On- demand routing with small delay.
Link breakages in active routes efficiently repaired.
Sequence numbers are used to make all the routes loop-
free.
Use of Sequence numbers to track accuracy of
information.
Instead of the entire route it only keeps track of next
hop for a route.
HELLO messages are used periodically to track
neighbours.
IV. DSR (The Dynamic Source Routing protocol )
The Dynamic Source Routing protocol (DSR) is a simple
and efficient routing protocol developed at CMU in 1996,
specifically for use in multi-hop wireless ad hoc networks of
mobile nodes. DSR allows the network to be completely self-
organizing and self-configuring, without the need for any
existing network infrastructure. DSR, a reactive unicast
protocol is based on source routing algorithm. In source
routing, when a source node wants to send a packet, it first
searches for an entry in its route cache. If the route is
available, the source node includes the routing information
inside the data packet before sending it. If entry is not
available, the source node initiates a route discovery operation
using route request (RREQ) packets. Each RREQ packet is
uniquely identified by source address and unique no known as
request id. On receipt of RREQ packet, an intermediary node
checks its route cache. If the node doesnt have routing
information for the requested destination, it appends its own
address to the route record field of the route request packet.
Then, the request packet is forwarded to its neighbors. A node
processes route request packets only if it has not seen the
packet before and its address is not presented in the route
record field. If the route request packet reaches intermediate
node has routing information to the destination or the
destination node, a route reply packet is generated. Route
reply packet is generated by the destination node, then it
comprises addresses of nodes that have been traversed by the
route request packet. Otherwise, if the route reply packet is
generated by intermediate node it comprises the addresses of
nodes the route request packet has traversed the route in the
intermediate nodes route cache.
A. Advantages
Guaranteed loop free routing.
Operation in networks containing unidirectional links.
Reduction of route discovery overheads with the use of
route cache.
Supports multi path routing.
Does not require any periodic messages.
B. Limitations
DSR is not very effective in large networks, it performs
well in static and low-mobility environments and the
performance degrades rapidly with increasing mobility.
Routing overhead is involved due to the source-routing.
Packet size keeps on increasing with route length,
because of source routing.
DSR suffers fromhigh route discovery latency.
V. TORA (Temporally ordered routing protocols)
The Temporally-Ordered Routing Algorithm (TORA) is
an on demand highly adaptive, efficient and scalable routing
protocol. TORA is proposed for highly dynamic mobile,
multi-hop wireless network that possesses the following
attributes.
Distributed execution,
Loop-free routing,
Multipath routing,
Reactive or proactive route establishment and
maintenance,
Minimization of communication overhead via
localization of algorithmic reaction to topological
changes.
International Journal of Computer Trends and Technology (IJCTT) volume 9 number 2 Mar 2014
ISSN: 2231-2803 http://www.ijcttjournal.org Page 84
TORA belong to a class of algorithms called link reversal
algorithms. TORA is distributed execution, in that routers
need only maintain information about adjacent routers (i.e.,
one-hop knowledge). Like a distance-vector routing approach,
TORA maintains state on a per- destination basis. The
destination-oriented nature of the routing structure in TORA
supports a mix of reactive and proactive routing on a per-
destination basis. During reactive operation, sources initiate
the establishment of routes to a given destination on- demand.
This may be advantageous in dynamic networks. At the same
time, selected destinations can initiate proactive operation,
matching traditional table driven routing. This allows routes
to be proactively maintained to destinations for which
routing is repeatedly required.
A. Advantages
Multiple route support, i.e. failure or removal of any of
the nodes is quickly resolved without source
intervention by switching to an alternate route.
Its on demand routing nature creates DAG only when
necessary.
Good in network with large no of nodes.
B. Limitations
TORA protocol algorithmmay also produce temporary
invalid routes as in LMR.
It depends on synchronized clocks among nodes in the
ad hoc network. The dependence of this protocol on
intermediate lower layers for certain type of
functionality presumes that the link status sensing,
neighbour discovery, in order packet delivery and
address resolution are all readily available
Table : Comparison between ad hoc routing protocols.
References
[1] Michael Gerhar z, Link Stability in Mobile Wireless Ad Hoc
Networks, Proc. of the 27th I EEE Conference on Local Computer
Networks (LCN), pp. 30-39, 2002
[2] Udayachandran Ramasamy, Classification of Self -Or ganizing
Hierarchical Mobile Adhoc Network Routing Protocols - A
Summary, (IJ ACSA) International J ournal of Advanced Computer
Science and Applications, . Vol. 1, No.4 October, 2010. 86
[3] J yoti J ain, OVERVIEW AND CHALLENGES OF ROUTI NG
PROTOCOL AND MAC LAYER IN MOBILE AD-HOC
NETWORK, journal of Theoretical and Applied Information
Technology. 2005 - 2009 J ATIT.
[4] Sima, SIMULATION STUDY OF AODV&DSR, International
J ournal of Computing and Business Research ISSN (Online) : 2229-
6166 Volume 2 Issue 3 September 2011.
[5] Perkins, C.; Royer, E.B.; Das, .S; :Ad hoc On-Demand Distance Vector
(AODV) Routing - Internet Draft, RFC 3561, IETF Network Working
Group, J uly 2003.
[6] V. Bharathi, A Performance Enhancement of an Optimized Power
Reactive Routing based on AODV Protocol for Mobile AD-HOC
Network, gopalax - International J ournal of Technology And
Engineering System(IJ TES) J an March 2011- Vol2 .No1.
[7] Sridhar K N, Stability and Hop-Count based Approach for Route
Computation in MANET, ICCCN, October 2005
[8] Harminder S. Bindra, Performance Evaluation of Two Reactive
Routing Protocols of MANET using Group Mobility Model,
International J ournal of Computer Science 2010; 7(3): 3843, 2010
[9] Udayachandran Ramasamy, Classification of Self -Organizing
Hierarchical Mobile Adhoc Network Routing Protocols - A
Summary, journal of Advanced Computer Science and
Applications,. Vol. 1, No.4 October, 2010.
[10] Yu-Chee Tseng, On Route Lifetime in Multihop Mobile Ad Hoc
Networks, IEEE TRANSACTIONS ON MOBILE COMPUTI NG
1536-1233/03@ 2003 IEEE
[11] Pushpa, WEIGHTAGE FACTOR BASED SCHEME FOR
PERFORMANCE IMPROVEMENT IN AD HOC NETWORKS,
(IJ CSE) International J ournal on Computer Science and Engineering.
Vol. 02, No. 02, 2010, 146-148
[12] Changling Liu, A Survey of Mobile Ad Hoc network Routing
Protocols, K.E. Kannammal et. al. International J ournal of
Engineering Science and Technology Vol. 2(5), 2010, 1298-1303.
[13] http://moment.cs.ucsb.edu/AODV/aodv
[14] V. Park, S. Corson, Temporally-Ordered Routing Algorithm(TORA)
Version 1 Functional Specification, 20 J uly 2001,
http://tools.ietf.org/html/draft-ietf-manet-tora-spec-04
[15] http://www.cs.ucr.edu/~krish/lec7
[16] http://ijecs.in/ijecsissue/wp-content/uploads/2013/03/707-718ijecs
[17] Arash Dana, A Reliable routing algorithm for Mobile Adhoc
Networks based on fuzzy logic, International J ournal of Computer
Science Issues Year: 2011 Vol:8 Issue:3 , 128-133
[18] C. Venkatesh, DYNAMIC SOURCE ROUTING PROTOCOL
USING FUZZY LOGIC CONCEPTS FOR AD HOC
NETWORKS, In. Transactions of Academic Open Internet
J ournal, Vol.15,pp 1- 14. 2008
[19] Panagiotis, Path Set Selection in Mobile Ad Hoc Networks, ACM
Mobihoc 2002, Lausanne, Switzerland, J une 2002.
[20] Navid Nikaein, DDR-Distributed Dynamic Routing Algorithm for
Mobile Ad hoc Networks, Proceedings of ACM MobiHoc, pp. 19
27, 2000
[21] Kwan-Wu Chin, Implementation Experience with MANET Routing
Protocols, J CST VOL II ISSUE IV, 2002
[22] Uma Nagaraj, Study of Various Routing Protocols in VANET,
IJ CST ISSN 09788491(Online) | ISSN : 2229-4333(Print).
[23] Thomas D. Dyer, A Comparison of TCP Performance over Three
Routing Protocols for Mobile Ad Hoc Networks, MobiHoc '01
Proceedings of the 2nd ACM international symposiumon Mobile
ad hoc networking & computing Pages 56 66 ACM New York, NY,
USA 2001 ISBN:1-58113-428-2
[24] Ashwani Kush; Phalguni Gupta ; Ram Kumar ; :Performance
Comparison of Wireless Routing Protocols, J ournal of the CSI , Vol.
AODV DSR TORA
Multiple routes No Yes Yes
Loop free Yes Yes No
Reactive Yes Yes Yes
Unidirectional Link
Support
No Yes No
Distributed Yes Yes Yes
QoS Support No No No
Methood Unicast Unicast Broadcast
Security No No No
Requires reliable or
Sequenced data
No No Yes
Topology Full Full Reduced
International Journal of Computer Trends and Technology (IJCTT) volume 9 number 2 Mar 2014
ISSN: 2231-2803 http://www.ijcttjournal.org Page 85
35 No.2, April-J une 2005
[25] AnneAaron; J ieWeng;: Performance Comparison of Ad-hoc
Routing Protocols for Networks with Node Energy Constraints ,
available at http://ivms.stanford.edu
[26] Charles Perkins; Elizabeth Royer; Samir Das; Mahesh Marina;:
Performance of two on-demand Routing Protocols for Adhoc
Networks, IEEE Personal Communications, February 2001, pp. 16-28.
[27] Sridhar K N, Stability and Hop-Count based Approach for Route
Computation in MANET, Computer Communications and Networks,
2005. ICCCN, 17-19 Oct. 2005.
[28] Aditya Kumar Mishra, Power -Aware Routing in Mobile Ad Hoc
Networks, Proceedings of the 4th annual ACM/IEEE international
conference on Mobile Computing and Networking, October 1998.
[29] Anuradha Banerjee, Fuzzy-Controlled Adaptive and Intelligent Route
(FAIR) Selection in Ad Hoc Networks, European J ournal of
Scientific Research. ISSN 1450-216X Vol.45 No.3 (2010), pp.367-
382.
[30] Hasnaa Moustafa, Source Routing-based Multicast Protocol for
Mobile Ad hoc Networks, 10
th
International Conference on
Telecommunication Systems Modeling and Analysis (ICTSM-10),
October 2002.
[31] Anuj K. Gupta, Member, IACSIT, Dr. Harsh Sadawarti, Dr. Anil K.
Verma Performance analysis of AODV, DSR & TORA Routing
Protocols.
Vous aimerez peut-être aussi
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (121)
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (588)
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (400)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (266)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5794)
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2259)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (345)
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (895)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (74)
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- Design and Implementation of Multiple Output Switch Mode Power SupplyDocument6 pagesDesign and Implementation of Multiple Output Switch Mode Power SupplyseventhsensegroupPas encore d'évaluation
- Azure Migration Readiness WhitepaperDocument17 pagesAzure Migration Readiness Whitepapersanchetanparmar100% (2)
- Linux Basic Sysadmin PDFDocument283 pagesLinux Basic Sysadmin PDFKaushal ShakyaPas encore d'évaluation
- Non-Linear Static Analysis of Multi-Storied BuildingDocument5 pagesNon-Linear Static Analysis of Multi-Storied Buildingseventhsensegroup100% (1)
- Double Smith Chart - Z & YDocument1 pageDouble Smith Chart - Z & YkgrhoadsPas encore d'évaluation
- FSLB ReadmeDocument7 pagesFSLB ReadmeJoseIgnacioContreras100% (1)
- Fabrication of High Speed Indication and Automatic Pneumatic Braking SystemDocument7 pagesFabrication of High Speed Indication and Automatic Pneumatic Braking Systemseventhsensegroup0% (1)
- Design, Development and Performance Evaluation of Solar Dryer With Mirror Booster For Red Chilli (Capsicum Annum)Document7 pagesDesign, Development and Performance Evaluation of Solar Dryer With Mirror Booster For Red Chilli (Capsicum Annum)seventhsensegroupPas encore d'évaluation
- Implementation of Single Stage Three Level Power Factor Correction AC-DC Converter With Phase Shift ModulationDocument6 pagesImplementation of Single Stage Three Level Power Factor Correction AC-DC Converter With Phase Shift ModulationseventhsensegroupPas encore d'évaluation
- FPGA Based Design and Implementation of Image Edge Detection Using Xilinx System GeneratorDocument4 pagesFPGA Based Design and Implementation of Image Edge Detection Using Xilinx System GeneratorseventhsensegroupPas encore d'évaluation
- Ijett V5N1P103Document4 pagesIjett V5N1P103Yosy NanaPas encore d'évaluation
- An Efficient and Empirical Model of Distributed ClusteringDocument5 pagesAn Efficient and Empirical Model of Distributed ClusteringseventhsensegroupPas encore d'évaluation
- Ijett V4i10p158Document6 pagesIjett V4i10p158pradeepjoshi007Pas encore d'évaluation
- Experimental Analysis of Tobacco Seed Oil Blends With Diesel in Single Cylinder Ci-EngineDocument5 pagesExperimental Analysis of Tobacco Seed Oil Blends With Diesel in Single Cylinder Ci-EngineseventhsensegroupPas encore d'évaluation
- Analysis of The Fixed Window Functions in The Fractional Fourier DomainDocument7 pagesAnalysis of The Fixed Window Functions in The Fractional Fourier DomainseventhsensegroupPas encore d'évaluation
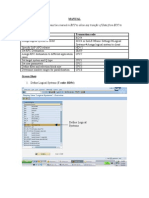
- Latitude 3480 3488 3580 16852-1 2-7 Taos - Kbl-U - A00 - 1223 - 1Document105 pagesLatitude 3480 3488 3580 16852-1 2-7 Taos - Kbl-U - A00 - 1223 - 1cuncho lennonPas encore d'évaluation
- Important QuestionsDocument2 pagesImportant QuestionsMahi SahuPas encore d'évaluation
- CE0510 4.0v1 Sophos Central Protection OverviewDocument32 pagesCE0510 4.0v1 Sophos Central Protection Overviewing.victorm.bastidassPas encore d'évaluation
- ARM7 Based Smart ATM Access SystemDocument3 pagesARM7 Based Smart ATM Access SystemEditor IJRITCCPas encore d'évaluation
- CS59201 DDocument4 pagesCS59201 DJose M PeresPas encore d'évaluation
- Goodmans High Power Bass Party Speaker - ImDocument11 pagesGoodmans High Power Bass Party Speaker - ImArron McgoniglePas encore d'évaluation
- Overview of PIC 16F877Document20 pagesOverview of PIC 16F877Santhanu Surendran100% (1)
- Middle-East Software V2Document226 pagesMiddle-East Software V2Arnold Cabading50% (2)
- Training Quizz Ciena - Elcom.mobifoneDocument3 pagesTraining Quizz Ciena - Elcom.mobifonephuongnt1710100% (2)
- Lesson: Counters Paper: Digital Electronics Lesson Developer: Ms. Chanchal Yadav College: Rajdhani College, University of DelhiDocument47 pagesLesson: Counters Paper: Digital Electronics Lesson Developer: Ms. Chanchal Yadav College: Rajdhani College, University of DelhiLeonardo CastilloPas encore d'évaluation
- Power Spark MAX User ManualDocument3 pagesPower Spark MAX User ManualZaita FregaPas encore d'évaluation
- User Manual Apo Rs6 Connection ConfigDocument29 pagesUser Manual Apo Rs6 Connection ConfigDipak BanerjeePas encore d'évaluation
- Debug 1214Document3 pagesDebug 1214123sudhirPas encore d'évaluation
- Complete Final Sem Report PDFDocument79 pagesComplete Final Sem Report PDFbhanu pratap mishraPas encore d'évaluation
- BE Major Project Format FinalDocument40 pagesBE Major Project Format Finalshilpi rajakPas encore d'évaluation
- LTA400HM21 SamsungDocument27 pagesLTA400HM21 SamsungJAMES SMITH VALDERRAMAPas encore d'évaluation
- BDSCP Module 08 MindmapDocument1 pageBDSCP Module 08 MindmappietropesPas encore d'évaluation
- Base Converter Application: R.Lakshmi K.Chandra MouliDocument16 pagesBase Converter Application: R.Lakshmi K.Chandra MouliAjit KumarPas encore d'évaluation
- Architectural Components - PreQuiz - Attempt ReviewDocument4 pagesArchitectural Components - PreQuiz - Attempt Reviewvinay MurakambattuPas encore d'évaluation
- ECE 545-Digital System Design With VHDL: Memories (RAM/ROM) 11/11/08Document68 pagesECE 545-Digital System Design With VHDL: Memories (RAM/ROM) 11/11/08Animesh SharmaPas encore d'évaluation
- DS3003 Standard EU EN BWDocument6 pagesDS3003 Standard EU EN BWKrisPas encore d'évaluation
- Connessioni Airbag PDFDocument6 pagesConnessioni Airbag PDFJesús GutiérrezPas encore d'évaluation
- (Pax-I3d) TSM (h022) New - EngDocument4 pages(Pax-I3d) TSM (h022) New - Engdekson alvesPas encore d'évaluation
- User Guide enDocument32 pagesUser Guide enAlberto Suazo BasaezPas encore d'évaluation
- Das, Nas and SanDocument5 pagesDas, Nas and SanAtthulaiPas encore d'évaluation
- Mode of ExamDocument6 pagesMode of ExamJaspreetPas encore d'évaluation