Académique Documents
Professionnel Documents
Culture Documents
How To Use FarBar Scanner To Remove Malware
Transféré par
ramanathansesha0 évaluation0% ont trouvé ce document utile (0 vote)
72 vues3 pagesREMOVE MALWARE
Titre original
How to Use FarBar Scanner to Remove Malware
Copyright
© © All Rights Reserved
Formats disponibles
PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentREMOVE MALWARE
Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
72 vues3 pagesHow To Use FarBar Scanner To Remove Malware
Transféré par
ramanathanseshaREMOVE MALWARE
Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 3
How to Use FarBar Scanner to Remove Malware
Two versions, 32bit and 64bit
Works with XP, 7vISTA and 8
Free Tool
Available at BleepingComputer.com
You want to run this in a recovery environment for Vista7 from a flash drive.
Open a command prompt from safe mode, a repair CD dos box or a PE environment
Two programs are - FRST.exe and FRST64.exe programs
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Procedure
1> At the command prompt find your flash drive and location of FRST.exe
2> Run FRST.exe
3> Leave all the ticks selected on the bottom for the Whitelist
4> Press Scan
5> When completed, FRST.txt log file was stored on flash drive where FRST.exe was located.
Also a another copy FRST.txt is stored on the root of the partition you scanned.
6> Click OK and minimize FarBar window for now.
7> Navigate to your windows partition
8> cd to c:\windows\system32
9> Type in notepad.exe
10> Goto file - open and located FRST.txt on your flash drive. Open it
11> Amongst all the data are the sections that show Modified files as you scan down.
12> As you scan down you might see this for a zero access infection and all the files infected.
13> Scanning further you will see example like this. Services.exe file is infected.
14> Sometimes Zero Access creates small hidden partitions and you can remove them with this tool as well.
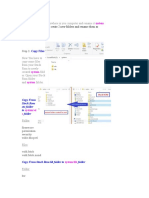
15> Open another notepad window notepad.exe
16> Tile the two notepad windows side by side. One is the FRST.txt and the other the new notepad window.
17> Now, if you notice in the above example for zero access the folder c:\windows\installer\{df5b1d7b-.}
All the files are located in this same folder, so copy that first line for the parent folder
18> In the new notepad window enter on the first line the word Start
19> Beneath that paste the folder you copied from the FRST.txt file
That should delete all the files listed in the parent dir and all sub dir.
20> From the example above you see another infected folder for the user
c:\users\Britec\AppData\Local\{df5b1d7b
21> Copy the parent folder ( first line) here as well and paste into the new notepad window under the previous line.
22> From the example above you see that last line for c:\windows\assembly\GAC\Desktop.ini
Copy and paste this line as well.
23> Now for the services we need to handle that differently. So minimize the new notepad window for now
24> Go back to you minimized Farbar window and run it again, but this time with the word services.exe
in the search line
25> Now scan again.
26> It will generate another log file called search.txt in the last location as the frst.txt file location.
27> Now open up another notepad window (I know lol) and open up the search.txt log file.
28> Here are the results
29> Copy that top line I highlighted and paste that into the file we were creating with all the infected foldersfiles
30> Now at the bottom of this created file we need to type the following:
replace: paste in the line we copied from the search.txt file, enter a space, then c:\windows\system32\services.exe
31> Now on the very last line type the word end and press enter. Below is what you should have.
32> Now save this file as fixlist.txt in the same location as the other .txt files we've been working with.
33> Now go back to your flash drive and run frst.exe again
34> This time you click the fix button which will scan for the fixlist.txt button and repair those items.
35> As you can see it then fixes the issues and generates another log file called FixLog.txt in the same location.
You can open that file with notepad to see what was done.
36> Notice that the files were moved into a folder for quarantine, which can be deleted later.
37> At this point you should be clean but it is wise to do another scan to be sure.
38> Notice below now that services.exe is good
And there you have it. Not for the everyday user. A lot must be inferred from this guide but I am sure you can figure out it use
from this sample scan.
Enjoy
GEGeek
Source - You can watch a video fot his same procedure here.
http:www.youtube.comwatch?v=D1iS1Vdxeeo&feature=em-uploademail
Vous aimerez peut-être aussi
- Subramanya Bhujangam in TamilDocument5 pagesSubramanya Bhujangam in Tamilramanathansesha100% (3)
- Computer Forensics Tools ComparisonDocument13 pagesComputer Forensics Tools ComparisonSundeel Bin HaleemPas encore d'évaluation
- Command Prompt HackingDocument4 pagesCommand Prompt Hackingapi-2687048493% (14)
- Ultimate Hacking Challenge: Hacking the Planet, #3D'EverandUltimate Hacking Challenge: Hacking the Planet, #3Évaluation : 5 sur 5 étoiles5/5 (2)
- Rent Agreement SummaryDocument10 pagesRent Agreement SummaryramanathanseshaPas encore d'évaluation
- Ansys How To InstalDocument5 pagesAnsys How To InstalMzahr SahabPas encore d'évaluation
- 1) Disabling Display of Drives in My Computer:: 2) Pop A Banner Each Time Windows BootsDocument8 pages1) Disabling Display of Drives in My Computer:: 2) Pop A Banner Each Time Windows Bootsoo7return4uPas encore d'évaluation
- FAT16 The FAT16 File System Was IntroducedDocument25 pagesFAT16 The FAT16 File System Was Introducedamittyagi23Pas encore d'évaluation
- Best Hacking Site: XP Tricks LL Some Call It HackDocument13 pagesBest Hacking Site: XP Tricks LL Some Call It HackkarthithebossPas encore d'évaluation
- XP Tricks LL Some Call It HackDocument96 pagesXP Tricks LL Some Call It HackRaaj KeshavPas encore d'évaluation
- Ebook by Nishant Srivastava For Computer Trcks and HacksDocument135 pagesEbook by Nishant Srivastava For Computer Trcks and HacksRimjhim BhagatPas encore d'évaluation
- Hack Your Friends Account PasswordDocument12 pagesHack Your Friends Account Passwordnelsondarla12100% (1)
- Virus Kill by Run CMDDocument4 pagesVirus Kill by Run CMDvampiremynPas encore d'évaluation
- How to install EMUBOX CCcam on WindowsDocument11 pagesHow to install EMUBOX CCcam on WindowsexxytecPas encore d'évaluation
- Removing Angry Birds Vbe Auto RunDocument2 pagesRemoving Angry Birds Vbe Auto RunOdd DetsPas encore d'évaluation
- Easy Hack To Windows XPDocument28 pagesEasy Hack To Windows XPmanit_parikh87Pas encore d'évaluation
- Linux FinalDocument90 pagesLinux FinalnithamolPas encore d'évaluation
- ZFX-Constructor 4.4 Making Your Own Portable App LZMA2 CompressedDocument8 pagesZFX-Constructor 4.4 Making Your Own Portable App LZMA2 CompressedSalvatore BonaffinoPas encore d'évaluation
- Lab-Proj3 Static TechniquesDocument10 pagesLab-Proj3 Static Techniquesv0dk4Pas encore d'évaluation
- SRIM Installation in Win-XP and Win-7 Systems: For 32-Bit Windows SystemsDocument1 pageSRIM Installation in Win-XP and Win-7 Systems: For 32-Bit Windows SystemsHyun Deog YooPas encore d'évaluation
- Dynamic Malware Analysis Lab ProjectDocument10 pagesDynamic Malware Analysis Lab Projectv0dk4Pas encore d'évaluation
- Install NX on Windows XP in 5 stepsDocument3 pagesInstall NX on Windows XP in 5 stepsTaha ZiaPas encore d'évaluation
- Linux System Administrator Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesD'EverandLinux System Administrator Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesPas encore d'évaluation
- Disable Windows File ProtectionDocument3 pagesDisable Windows File ProtectionCRQ1974Pas encore d'évaluation
- SRIM Setup MessageDocument3 pagesSRIM Setup MessageRicardo Bim100% (1)
- Install CadenceDocument4 pagesInstall Cadencenguyenbinh12xPas encore d'évaluation
- 17 Windows tricks to impress and optimize your PCDocument8 pages17 Windows tricks to impress and optimize your PCManthan SolankiPas encore d'évaluation
- CST Studio Suite 2010 Installation GuideDocument6 pagesCST Studio Suite 2010 Installation GuideKrishna Yadav100% (2)
- Hacking Windows Password-Lab1Document11 pagesHacking Windows Password-Lab1Joel JohnPas encore d'évaluation
- Basic Shortcut KeysDocument52 pagesBasic Shortcut KeysSreenivas SunkaraPas encore d'évaluation
- Kali 5Document10 pagesKali 5michal hanaPas encore d'évaluation
- Lab Proj 04 - UnpackingDocument6 pagesLab Proj 04 - Unpackingv0dk4Pas encore d'évaluation
- Blaster RemovalDocument3 pagesBlaster RemovalflorincrPas encore d'évaluation
- Lab-Proj.06 RegeditDocument4 pagesLab-Proj.06 RegeditHiệp ĐàoPas encore d'évaluation
- 25+ Notepad Virus Script (Just Copy & Paste) 2020: ResponsesDocument29 pages25+ Notepad Virus Script (Just Copy & Paste) 2020: Responsesmuna cliff100% (1)
- Tukar Nama DriveDocument16 pagesTukar Nama DriveRusli NorizanPas encore d'évaluation
- Linux FinalDocument79 pagesLinux FinalShalu sajuPas encore d'évaluation
- XP Tricks & Tips-IIDocument29 pagesXP Tricks & Tips-IIMd Raisul Islam100% (1)
- Lab 03 Informational File, and Directory CommandsDocument11 pagesLab 03 Informational File, and Directory CommandsQuyên PhươngPas encore d'évaluation
- 14 Notepad Tricks for Fun and PrankDocument10 pages14 Notepad Tricks for Fun and PrankJohn HeilPas encore d'évaluation
- Wmic Trick O HackerDocument12 pagesWmic Trick O HackerjoseanPas encore d'évaluation
- Installation For UnixDocument5 pagesInstallation For UnixUkat HidayatPas encore d'évaluation
- Add8 (Just A Name) in The Main Directory RT. Create A New Directory in E Drive in Your Name, Say RTDocument6 pagesAdd8 (Just A Name) in The Main Directory RT. Create A New Directory in E Drive in Your Name, Say RTSingam SridharPas encore d'évaluation
- Fixing "Task Manager Is Disabled by Your Administrator"Document9 pagesFixing "Task Manager Is Disabled by Your Administrator"julius1015Pas encore d'évaluation
- WInHelp On Windows 10Document14 pagesWInHelp On Windows 10Jeremy DudleyPas encore d'évaluation
- Trick-1: Create Shortcut For Removing PendriveDocument230 pagesTrick-1: Create Shortcut For Removing Pendriveprince4458Pas encore d'évaluation
- Inside The System Folder Create 2 New Folders and Rename Them AsDocument3 pagesInside The System Folder Create 2 New Folders and Rename Them AsVcj Reza Donotneedtoalways-Exaggerated RememberintheskythereismoreskyPas encore d'évaluation
- A Short Linux Tutorial For This Course Getting Access To LinuxDocument6 pagesA Short Linux Tutorial For This Course Getting Access To LinuxNashrif KarimPas encore d'évaluation
- Xset 1Document6 pagesXset 1Lukas ButkusPas encore d'évaluation
- Installing Pynomo On A Windows Machine: Ron Doerfler (21 December 2011)Document3 pagesInstalling Pynomo On A Windows Machine: Ron Doerfler (21 December 2011)DacianMPas encore d'évaluation
- 50 Tips and Tricks ApprovalDocument20 pages50 Tips and Tricks ApprovalArvind YadavPas encore d'évaluation
- Increase Your RAM There by Increase System SpeedDocument6 pagesIncrease Your RAM There by Increase System Speedkaushik240Pas encore d'évaluation
- Windows XP TweaksDocument11 pagesWindows XP TweakswaynePas encore d'évaluation
- Starting WinLASI 7v02Document24 pagesStarting WinLASI 7v02Ernest TiongPas encore d'évaluation
- 50 Tricks and Hacks for Your PC You Don't Know AboutDocument83 pages50 Tricks and Hacks for Your PC You Don't Know AboutA KA SH TickuPas encore d'évaluation
- LAB A COMMAND PROMPT & INSTALLING WIN 7Document27 pagesLAB A COMMAND PROMPT & INSTALLING WIN 7njvroom100% (1)
- Ns2 Install GuideDocument21 pagesNs2 Install GuideSuganyadevi SubramaniamPas encore d'évaluation
- Pro e PatchDocument2 pagesPro e PatchjayanthklraoPas encore d'évaluation
- The Mac Terminal Reference and Scripting PrimerD'EverandThe Mac Terminal Reference and Scripting PrimerÉvaluation : 4.5 sur 5 étoiles4.5/5 (3)
- Preventive VigilanceDocument3 pagesPreventive VigilanceramanathanseshaPas encore d'évaluation
- Compounding Under Companies Act PDFDocument6 pagesCompounding Under Companies Act PDFramanathanseshaPas encore d'évaluation
- Timing MarriageDocument3 pagesTiming Marriageramanathansesha100% (2)
- Compounding Under Companies Act PDFDocument6 pagesCompounding Under Companies Act PDFramanathanseshaPas encore d'évaluation
- Gochar ResultsDocument12 pagesGochar ResultsramanathanseshaPas encore d'évaluation
- Telugu Content: Get FontsDocument2 pagesTelugu Content: Get FontsramanathanseshaPas encore d'évaluation
- Pudhu Periyava Mother Interview JVDocument5 pagesPudhu Periyava Mother Interview JVramanathanseshaPas encore d'évaluation
- "Do-It-Yourself" Water Seepage TestDocument8 pages"Do-It-Yourself" Water Seepage TestramanathanseshaPas encore d'évaluation
- Royapettah Area Map on Google MapsDocument1 pageRoyapettah Area Map on Google MapsramanathanseshaPas encore d'évaluation
- Timing MarriageDocument3 pagesTiming Marriageramanathansesha100% (2)
- 1248905368568 (1)Document8 pages1248905368568 (1)Rodny ThomsonPas encore d'évaluation
- Telugu Content: Get FontsDocument2 pagesTelugu Content: Get FontsramanathanseshaPas encore d'évaluation
- Profession PartIDocument10 pagesProfession PartImedzo77Pas encore d'évaluation
- The Lokpal and Lokayuktas Act, 2013Document26 pagesThe Lokpal and Lokayuktas Act, 2013vivek kumar singh100% (1)
- CholestrolDocument12 pagesCholestrolramanathanseshaPas encore d'évaluation
- C KarakaDocument13 pagesC Karakajaiswal.utkarshPas encore d'évaluation
- Bhikshuka UpanishadDocument2 pagesBhikshuka UpanishadramanathanseshaPas encore d'évaluation
- FRSTDocument2 pagesFRSTramanathanseshaPas encore d'évaluation
- Kanchi Periva Forum - Ebook On Important Daily RitualsDocument26 pagesKanchi Periva Forum - Ebook On Important Daily RitualsMadhu Ganesh100% (6)
- Takeover FaqDocument9 pagesTakeover FaqroutraykhushbooPas encore d'évaluation
- Vishnu TamilDocument15 pagesVishnu TamilramanathanseshaPas encore d'évaluation
- How To Use FarBar Scanner To Remove MalwareDocument3 pagesHow To Use FarBar Scanner To Remove MalwareramanathanseshaPas encore d'évaluation
- 3⁄4¢Õ ̈ÅÌó3⁄4 Å¢ñ1⁄2 ̧ÃõDocument8 pages3⁄4¢Õ ̈ÅÌó3⁄4 Å¢ñ1⁄2 ̧ÃõramanathanseshaPas encore d'évaluation
- Dhan YogaDocument96 pagesDhan Yogaramanathansesha100% (1)
- Sivavakkiyar 2012 5Document13 pagesSivavakkiyar 2012 5MuraliPas encore d'évaluation
- Yes Bank Meet Note Highlights Growth Targets, Asset QualityDocument4 pagesYes Bank Meet Note Highlights Growth Targets, Asset QualityramanathanseshaPas encore d'évaluation
- Visa Reinstatement GuidelinesDocument3 pagesVisa Reinstatement GuidelinesramanathanseshaPas encore d'évaluation
- 14 SparkParallelProcessingDocument51 pages14 SparkParallelProcessingPetter PPas encore d'évaluation
- Predictive Coding IDocument14 pagesPredictive Coding IRakesh InaniPas encore d'évaluation
- SBC-4B03: Single Board ComputerDocument65 pagesSBC-4B03: Single Board ComputerOvi PanteaPas encore d'évaluation
- WCG FAQs 78Document10 pagesWCG FAQs 78list_coursePas encore d'évaluation
- Changes Compared To OData V2 Model Abd4d7cDocument2 pagesChanges Compared To OData V2 Model Abd4d7czzgPas encore d'évaluation
- PX PX5 PX30 InstructionDocument10 pagesPX PX5 PX30 InstructionJake BloomPas encore d'évaluation
- Data Structure Lab ManualDocument77 pagesData Structure Lab ManualkunalPas encore d'évaluation
- PCPDocument126 pagesPCPdipak1986Pas encore d'évaluation
- HL7 Communication Protocol For QuintusDocument7 pagesHL7 Communication Protocol For QuintusDiego Andres BeltranPas encore d'évaluation
- Abbreviations List for IT and Computer ScienceDocument2 pagesAbbreviations List for IT and Computer ScienceShakeelAhmedPas encore d'évaluation
- Install and Set Up OpenMediaVault 6 on a Raspberry Pi for NFS Sharing in Under 40 StepsDocument9 pagesInstall and Set Up OpenMediaVault 6 on a Raspberry Pi for NFS Sharing in Under 40 StepsSubrat Kumarr PandaPas encore d'évaluation
- ProtocolsDocument37 pagesProtocolsKOMERTDFDF100% (1)
- Adorno - Metaphysics PDFDocument225 pagesAdorno - Metaphysics PDFGustavo AssanoPas encore d'évaluation
- Brocade - FC FundamentalsDocument143 pagesBrocade - FC FundamentalsAbhi YadavPas encore d'évaluation
- DB AsciiDocument3 pagesDB AsciiAbby ARPas encore d'évaluation
- PC Unit 5Document58 pagesPC Unit 5Abhiram PaboluPas encore d'évaluation
- I/O Systems GuideDocument72 pagesI/O Systems Guidedinesh reddyPas encore d'évaluation
- Lecture #2 - Data Warehouse ArchitectureDocument6 pagesLecture #2 - Data Warehouse ArchitectureUdai BhaskerPas encore d'évaluation
- API Security ChecklistDocument4 pagesAPI Security ChecklistAbhijit ChatterjeePas encore d'évaluation
- Best Practices - ETLDocument3 pagesBest Practices - ETLShailendra DubeyPas encore d'évaluation
- 5f299932e82a66e0ecdbba5adfff4bf8.docxDocument2 pages5f299932e82a66e0ecdbba5adfff4bf8.docxsushil@irdPas encore d'évaluation
- WLAN SecuredDocument6 pagesWLAN Securedtritri0808100% (1)
- Huawei FusionCloud Desktop Solution Application Virtualization Main SlidesDocument34 pagesHuawei FusionCloud Desktop Solution Application Virtualization Main SlidesHUMANMANPas encore d'évaluation
- 7b Terraform State LockingDocument2 pages7b Terraform State LockingTITAITOQQPas encore d'évaluation
- Huawei OceanStor SNS2624 SNS3664 SNS3696E Data SheetDocument6 pagesHuawei OceanStor SNS2624 SNS3664 SNS3696E Data SheetdjsonicoPas encore d'évaluation
- Case Studies Data Warehouse PortfolioDocument8 pagesCase Studies Data Warehouse PortfolioZihni ThoriqPas encore d'évaluation
- WSDOT ProjectWise V8i Training 101Document12 pagesWSDOT ProjectWise V8i Training 101nguoituyet66Pas encore d'évaluation
- Ofr02 166Document101 pagesOfr02 166DCSAWPas encore d'évaluation
- Arch 21Document4 pagesArch 21Nishant JaiswalPas encore d'évaluation
- XML Training Course, Best XML Training Institute Hyderabad, India - NareshITDocument3 pagesXML Training Course, Best XML Training Institute Hyderabad, India - NareshITAnand DhanalakotaPas encore d'évaluation