Académique Documents
Professionnel Documents
Culture Documents
CCNASv1.1 Chp09 Lab-A Sec-Pol Student
Transféré par
luisdg930 évaluation0% ont trouvé ce document utile (0 vote)
60 vues32 pagesCopyright
© © All Rights Reserved
Formats disponibles
DOC, PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme DOC, PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
60 vues32 pagesCCNASv1.1 Chp09 Lab-A Sec-Pol Student
Transféré par
luisdg93Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme DOC, PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 32
CCNA Security
Chapter 9 Lab A: Security Policy Development and
Implementation
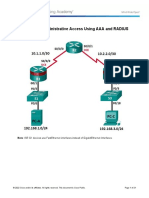
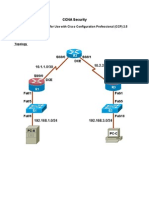
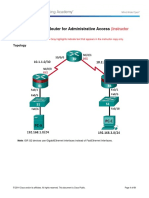
Topology
Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet Interfaces.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1 of (2
CCNA Security
IP Addressing Table
Device Interace IP Address Subnet !as" Deault #ate$ay S$itch Port
R1 FA")1 12.1*+.1.1 2,,.2,,.2,,." -)A S1 FA"),
S")")" ./CE0 1".1.1.1 2,,.2,,.2,,.2,2 -)A -)A
R2 S")")" 1".1.1.2 2,,.2,,.2,,.2,2 -)A -)A
S")")1 ./CE0 1".2.2.2 2,,.2,,.2,,.2,2 -)A -)A
R( FA")1 12.1*+.(.1 2,,.2,,.2,,." -)A S( FA"),
S")")1 1".2.2.1 2,,.2,,.2,,.2,2 -)A -)A
S1 12A- 1 12.1*+.1.11 2,,.2,,.2,,." 12.1*+.1.1 -)A
S2 12A- 1 12.1*+.1.12 2,,.2,,.2,,." 12.1*+.1.1 -)A
S( 12A- 1 12.1*+.(.11 2,,.2,,.2,,." 12.1*+.(.1 -)A
'C3A -IC 12.1*+.1.( 2,,.2,,.2,,." 12.1*+.1.1 S1 FA")*
'C34 -IC 12.1*+.1.2 2,,.2,,.2,,." 12.1*+.1.1 S2 FA")1+
'C3C -IC 12.1*+.(.( 2,,.2,,.2,,." 12.1*+.(.1 S( FA")1+
%b&ectives
Part ': Create a (asic Technical Security Policy
/evelop a -et5or6 /evice Sec&rity G&idelines doc&#ent.
Part ): (asic Net$or" Device Coniguration
Config&re hostna#es$ interface I' addresses$ and pass5ords.
Config&re static ro&ting.
Part *: Secure Net$or" +outers
Config&re pass5ords and a login banner.
Config&re SS7 access and disable %elnet.
Config&re 7%%' sec&re server access.
Config&re a synchroni8ed ti#e so&rce &sing -%'.
Config&re ro&ter syslog s&pport.
Config&re centrali8ed a&thentication &sing AAA and RA/I9S.
9se Cisco I:S to disable &nneeded services and sec&re against login attac6s.
9se CC' to disable &nneeded services.
Config&re a C4AC fire5all.
Config&re a ;4F fire5all.
Config&re intr&sion prevention syste# .I'S0 &sing Cisco I:S and CC'.
4ac6 &p and sec&re the Cisco I:S i#age and config&ration files.
Part ,: Secure Net$or" S$itches
Config&re pass5ords$ and a login banner.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2 of (2
CCNA Security
Config&re #anage#ent 12A- access.
Config&re a synchroni8ed ti#e so&rce &sing -%'.
Config&re syslog s&pport.
Config&re SS7 access.
Config&re AAA and RA/I9S.
Sec&re tr&n6 ports.
Sec&re access ports.
'rotect against S%' attac6s.
Config&re port sec&rity and disable &n&sed ports.
Part -: Conigure .PN remote access
9se CC' to config&re Easy 1'- Server.
9se the Cisco 1'- Client to test the re#ote access 1'-.
(ac"ground
A co#prehensive sec&rity policy covers three #ain areas< governing policies$ end3&ser policies$ and technical
policies. %echnical policies can incl&de e3#ail$ re#ote access$ telephony$ applications$ and net5or6 policies$
s&ch as device access controls and logging. %he foc&s of this lab is the creation of a technical net5or6 policy
that specifies sec&rity #eas&res to be config&red for net5or6 devices and i#ple#entation of those #eas&res.
In 'art 1 of this lab$ yo& create a basic -et5or6 /evice Sec&rity G&idelines doc&#ent that can serve as part
of a co#prehensive policy. %his doc&#ent addresses specific ro&ter and s5itch sec&rity #eas&res and
describes the sec&rity re=&ire#ents to be i#ple#ented on the infrastr&ct&re e=&ip#ent. %he -et5or6 /evice
Sec&rity G&idelines doc&#ent is presented to yo&r instr&ctor for revie5 prior to starting 'art 2 of the lab.
In 'art 2$ yo& b&ild the net5or6 and config&re basic device settings. In 'arts ( and >$ yo& sec&re ro&ters and
s5itches. In 'art ,$ yo& config&re a ro&ter for 1'- re#ote access. %he -et5or6 /evice Sec&rity G&idelines
policy is &sed as the g&iding doc&#ent.
%he co#pany yo& are 5or6ing for has t5o locations connected by an IS'. Ro&ter R1 represents a re#ote site$
and R( represents the corporate head=&arters. Ro&ter R2 represents the IS'.
Note: %he ro&ter co##ands and o&tp&t in this lab are fro# a Cisco 1+>1 5ith Cisco I:S Release 12.>.2"0%
.Advanced I' i#age0. %he s5itch co##ands and o&tp&t are fro# a Cisco ?S3C2*"32>%%32 5ith Cisco I:S
Release 12.2.>*0SE .C2*"32A-4ASE@3A i#age0. :ther ro&ters$ s5itches$ and Cisco I:S versions can be
&sed. See the Ro&ter Interface S&##ary table at the end of the lab to deter#ine 5hich interface identifiers to
&se based on the e=&ip#ent in the lab. /epending on the ro&ter or s5itch #odel and Cisco I:S version$ the
co##ands available and o&tp&t prod&ced #ight vary fro# 5hat is sho5n in this lab.
Note: Aa6e s&re that the ro&ters and s5itches have been erased and have no start&p config&rations.
+e/uired +esources
2 ro&ters .Cisco 1+>1 5ith Cisco I:S Release 12.>.2"0%1 Advanced I' Service or co#parable0
1 ro&ter .Cisco 1+>1 5ith Cisco I:S Release 12.>.2"0%1 I' 4ase or co#parable0
( s5itches .Cisco 2*" 5ith Cisco I:S Release 12.2.>*0SE C2*"32A-4ASE@3A i#age or
co#parable0
'C3A< ?indo5s B'$ 1ista$ or ?indo5s C 5ith CC' 2.,$ RA/I9S$ %F%'$ and syslog servers pl&s
'&%%D and Cisco 1'- Client soft5are available
'C34< ?indo5s B'$ 1ista$ or ?indo5s C
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age ( of (2
CCNA Security
'C3C< ?indo5s B'$ 1ista$ or ?indo5s C 5ith CC' 2.,$ RA/I9S$ %F%'$ and syslog servers pl&s
'&%%D soft5are available and S&perScan .optional0
Serial and Ethernet cables as sho5n in the topology
Rollover cables to config&re the ro&ters via the console
CCP Notes:
Refer to Chp "" 2ab A for instr&ctions on ho5 to install and r&n CC'. 7ard5are)soft5are
reco##endations for CC' incl&de ?indo5s B'$ 1ista$ or ?indo5s C 5ith Eava version 1.*."F11 &p to
1.*."F21$ Internet EGplorer *." or above and Flash 'layer 1ersion 1".".12.(* and later.
If the 'C on 5hich CC' is installed is r&nning ?indo5s 1ista or ?indo5s C$ it #ay be necessary to
right3clic6 on the CC' icon or #en& ite#$ and choose +un as administrator.
In order to r&n CC'$ it #ay be necessary to te#porarily disable antivir&s progra#s and :)S fire5alls.
Aa6e s&re that all pop3&p bloc6ers are t&rned off in the bro5ser.
Part ': Create a (asic Technical Security Policy
In 'art 1$ yo& create a -et5or6 /evice Sec&rity G&idelines doc&#ent that can serve as part of a
co#prehensive net5or6 sec&rity policy. %his doc&#ent addresses specific ro&ter and s5itch sec&rity
#eas&res and describes the sec&rity re=&ire#ents to be i#ple#ented on the infrastr&ct&re e=&ip#ent.
Tas" ': Identiy potential sections o a basic net$or" security policy 0Chapter 91
A net5or6 sec&rity policy sho&ld incl&de several 6ey sections that can address potential iss&es for &sers$
net5or6 access$ device access and other areas. 2ist so#e 6ey sections yo& thin6 co&ld be part of good
basic sec&rity policy.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" ): Create Net$or" 2/uipment Security #uidelines as a Supplement to a
(asic Security Policy 0Chapter 91
Step ': +evie$ the ob&ectives rom previous CCNA Security labs3
a. :pen each of the previo&s labs co#pleted fro# chapters one thro&gh eight and revie5 the obHectives
listed for each one.
b. Copy the obHectives to a separate doc&#ent for &se as a starting point. Foc&s #ainly on those
obHectives that involve sec&rity practices and device config&ration.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age > of (2
CCNA Security
Step ): Create a Net$or" Device Security #uidelines document or router and s$itch security3
Create a high3level list of tas6s to incl&de for net5or6 access and device sec&rity. %his doc&#ent sho&ld
reinforce and s&pple#ent the infor#ation presented in a basic Sec&rity 'olicy. It is based on the content
of previo&s CC-A Sec&rity labs and on the net5or6ing devices present in the co&rse lab topology.
Note: %he -et5or6 /evice Sec&rity G&idelines doc&#ent sho&ld be no #ore than t5o pages and is the
basis for the e=&ip#ent config&ration in the re#aining parts of the lab.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: Submit the Net$or" Device Security #uidelines to your instructor3
'rovide the -et5or6 /evice Sec&rity G&idelines doc&#ents to yo&r instr&ctor for revie5 before starting
'art 2 of the lab. Do& can send the# as e3#ail attach#ents or p&t the# on re#ovable storage #edia$
s&ch as a flash drive.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age , of (2
CCNA Security
Part ): (asic Net$or" Device Coniguration 0Chapters ) and 41
In 'art 2$ yo& set &p the net5or6 topology and config&re basic settings$ s&ch as the interface I' addresses
and static ro&ting. 'erfor# steps on ro&ters and s5itches as indicated.
Step ': Cable the net$or" as sho$n in the topology3
Attach the devices sho5n in the topology diagra#$ and cable as necessary.
Step ): Conigure basic settings or all routers3
a. Config&re hostna#es as sho5n in the topology.
b. Config&re the interface I' addresses as sho5n in the I' addressing table.
c. Config&re a cloc6 rate for the ro&ters 5ith a /CE serial cable attached to their serial interface.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
d. /isable /-S loo6&p to prevent the ro&ter fro# atte#pting to translate incorrectly entered co##ands
as tho&gh they 5ere hostna#es.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: Conigure static deault routes on +' and +*3
Config&re a static defa< ro&te fro# R1 to R2 and fro# R( to R2.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ,: Conigure static routes on +)3
Config&re a static ro&te fro# R2 to the R1 2A- and fro# R2 to the R( 2A-.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step -: Conigure basic settings or each s$itch3
a. Config&re hostna#es as sho5n in the topology.
b. Config&re the 12A- 1 #anage#ent addresses as sho5n in the I' Addressing table.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. Config&re the I' defa< gate5ay for each of the three s5itches. %he gate5ay for the S1 and S2
s5itches is the R1 Fa")1 interface I' address. %he gate5ay for the S( s5itch is the R( Fa")1
interface I' address.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
d. /isable /-S loo6&p to prevent the s5itches fro# atte#pting to translate incorrectly entered
co##ands as tho&gh they 5ere hostna#es.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age * of (2
CCNA Security
Step 4: Conigure PC host IP settings3
Config&re a static I' address$ s&bnet #as6$ and defa< gate5ay for 'C3A$ 'C34$ and 'C3C$ as sho5n in
the I' addressing table.
Step 5: .eriy connectivity bet$een PC6A and PC6C3
_____________________________________________________________________________
Step 7: Save the basic running coniguration or each router3
Part *: Secure Net$or" +outers
In 'art ($ yo& config&re device access$ pass5ords$ fire5alls$ and intr&sion prevention. 'erfor# steps on
ro&ters as indicated.
Tas" ': Conigure Pass$ords and a Login (anner 0Chapter )1
Step ': Conigure a minimum pass$ord length o '8 characters on all routers3
_____________________________________________________________________________
Step ): Conigure the enable secret pass$ord on all routers3
9se an enable secret pass5ord of cisco')*,-.
_____________________________________________________________________________
Step *: 2ncrypt plainte9t pass$ords3
_____________________________________________________________________________
Step ,: Conigure the console lines on all routers3
Config&re a console pass5ord of ciscoconpass and enable login. Set the eGec3ti#eo&t to log o&t after ,
#in&tes of inactivity. 'revent console #essages fro# interr&pting co##and entry.
_____________________________________________________________________________
Step -: Conigure the vty lines on +)3
Config&re a vty lines pass5ord of ciscovtypass and enable login. Set the eGec3ti#eo&t to log o&t after ,
#in&tes of inactivity.
_____________________________________________________________________________
Note: %he vty lines for R1 and R( are config&red for SS7 in %as6 2.
Step 4: Conigure a login $arning banner on routers +' and +*3
Config&re a 5arning to &na&thori8ed &sers 5ith a #essage3of3the3day .A:%/0 banner that says
I9na&thori8ed access strictly prohibited and prosec&ted to the f&ll eGtent of the la5J.
_____________________________________________________________________________
Tas" ): Conigure the SS: Server on +outers +' and +* 0Chapter )1
Step ': Conigure a privileged user or login rom the SS: client3
Create the &ser Ad#in"1 acco&nt 5ith a privilege level of 1, and a secret pass5ord of Ad#in"1pa,,.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age C of (2
CCNA Security
_____________________________________________________________________________
Step ): Conigure the domain name ccnasecurity3com3
_____________________________________________________________________________
Step *: Conigure the incoming vty lines3
Specify a privilege level of 1, so that a &ser 5ith the highest privilege level .1,0 5ill defa< to privileged
EBEC #ode 5hen accessing the vty lines. :ther &sers 5ill defa< to &ser EBEC #ode. Specify local &ser
acco&nts for #andatory login and validation$ and accept only SS7 connections.
_____________________________________________________________________________
Step ,: #enerate the +SA encryption "ey pair or the router3
Config&re the RSA 6eys 5ith 1"2> for the n&#ber of #od&l&s bits.
_____________________________________________________________________________
Step -: .eriy SS: connectivity to +' rom PC6A3
a. If the SS7 client is not already installed$ do5nload either %era%er# or '&%%D.
b. 2a&nch the SS7 client$ enter the Fa")1 I' address$ and enter the Admin8' &serna#e and pass5ord
Admin8'pa--.
%as6 (< Config&re a Synchroni8ed %i#e So&rce 9sing -%' 0Chapter )1
Step ': Set up the NTP master using Cisco I%S commands3
R2 5ill be the #aster -%' server. All other ro&ters and s5itches learn their ti#e fro# it$ either directly or
indirectly.
a. Ens&re that R2 has the correct coordinated &niversal ti#e. Set the ti#e if it is not correct.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Config&re R2 as the -%' #aster 5ith a strat&# n&#ber of (.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ): Conigure +' and +* as NTP clients3
a. Config&re R1 and R( to beco#e -%' clients of R2.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. 1erify that R1 and R( have #ade an association 5ith R2 &sing the show ntp associations
co##and.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age + of (2
CCNA Security
Tas" ,: Conigure +outer Syslog Support 0Chapter )1
Step ': 0%ptional1 Install the syslog server on PC6A and PC6C3
If a syslog server is not c&rrently installed on the host$ do5nload the latest version of @i5i fro#
http<))555.6i5isyslog.co# or %ftpd(2 fro# http<))tftpd(2.Ho&nin.net and install it on yo&r des6top. If it is already
installed$ go to Step 2.
Step ): Conigure +' to log messages to the PC6A syslog server3
a. 1erify that yo& have connectivity bet5een R1 and host 'C3A by pinging the R1 Fa")1 interface I'
address 12.1*+.1.1 fro# 'C3A. If the pings are not s&ccessf&l$ tro&bleshoot as necessary before
contin&ing.
b. Config&re logging on the ro&ter to send syslog #essages to the syslog server.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: Conigure +* to log messages to the PC6C syslog server3
a. 1erify that yo& have connectivity bet5een R( and the host 'C3C by pinging the R( Fa")1 interface I'
address 12.1*+.(.1 fro# 'C3C. If the pings are not s&ccessf&l$ tro&bleshoot as necessary before
contin&ing.
b. Config&re logging on the ro&ter to send syslog #essages to the syslog server.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" -: Conigure Authentication ;sing AAA and +ADI;S 0Chapter *1
'C3A 5ill serve as the local RA/I9S server for the re#ote site and R1 accesses the eGternal RA/I9S server
for &ser a&thentication. %he free5are RA/I9S server ?inRadi&s is &sed for this section of the lab.
Step ': 0%ptional1 Do$nload and conigure the <in+adius sot$are3
a. If ?inRadi&s is not c&rrently installed on 'C3A$ do5nload the latest version fro#
http<))555.s&ggestsoft.co#)soft)itcons<2""")5inradi&s)$ http<))5inradi&s.soft(2.co#$
http<))555.brothersoft.co#)5inradi&s32"1>.ht#l. %here is no installation set&p. %he eGtracted
?inRadi&s.eGe file is eGec&table.
b. Start the ?inRadi&s.eGe application. If the application is being started for the first ti#e$ follo5 the
instr&ctions to config&re the ?inRadi&s server database.
Note: If ?inRadi&s is &sed on a 'C that &ses the Aicrosoft ?indo5s 1ista operating syste# or the
Aicrosoft ?indo5s C operating syste#$ :/4C #ay fail to create s&ccessf&lly beca&se it cannot 5rite to
the registry.
Possible solutions:
1. Co#patibility settings<
a. Right clic6 on the ?inRadi&s.eGe icon and select Properties.
b. ?hile in the Properties dialog boG$ select the Compatibility tab. In this tab$ select the
chec6boG for +un this program in compatibility mode or. %hen in the drop do5n #en&
belo5$ choose <indo$s =P 0Service Pac" *1 for eGa#ple$ if it is appropriate for yo&r
syste#.
c. Clic6 %>.
2. +un as Administrator settings<
a. Right clic6 on the ?inRadi&s.eGe icon and select Properties.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age of (2
CCNA Security
b. ?hile in the Properties dialog boG$ select the Compatibility tab. In this tab$ select the
chec6boG for +un this program as administrator in the 'rivilege 2evel section.
c. Clic6 %>.
(. +un as Administration for each la&nch<
a. Right clic6 on the ?inRadi&s.eGe icon and select +un as administrator.
b. ?hen ?inRadi&s la&nches$ clic6 ?es in the 9ser Acco&nt Control dialog boG.
Step ): Conigure users and pass$ords on the <in+adius server3
a. Add &serna#e +adAdmin 5ith a pass5ord of +adAdminpa--.
b. Add &serna#e +ad;ser 5ith a pass5ord of +ad;serpa--.
Step *: 2nable AAA on +'3
9se the aaa new-model co##and to enable AAA.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ,: Conigure the deault login authentication list3
Config&re the list to first &se radius for the a&thentication service and then local to allo5 access based
on the local ro&ter database if a RA/I9S server cannot be reached.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step -: .eriy connectivity bet$een +' and the PC6A +ADI;S server3
'ing fro# R1 to 'C3A.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
If the pings are not s&ccessf&l$ tro&bleshoot the 'C and ro&ter config&ration before contin&ing.
Step 4: Speciy a +ADI;S server on +'3
Config&re the ro&ter to access the RA/I9S server at the 'C3A I' address. Specify port n&#bers '7')
and '7'*$ along 5ith the defa< secret 6ey of <in+adius for the RA/I9S server.
_____________________________________________________________________________
Step 5: Test your coniguration by logging into the console on +'3
a. EGit to the initial ro&ter screen that displays the follo5ing<
R1 con0 is now available.
b. 2og in 5ith the &serna#e +adAdmin and pass5ord +adAdminpa--. Are yo& able to login 5ith
#ini#al delayK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Note: If yo& close the ?inRadi&s server and restart it$ yo& #&st recreate the &ser acco&nts fro# Step 2.
Step 7: Test your coniguration by connecting to +' $ith SS:3
a. Clear the log display for the ?inRadi&s server by choosing Log @ Clear.
b. 9se '&%%D or another ter#inal e#&lation client to open an SS7 session fro# 'C3A to R1.
c. At the login pro#pt$ enter the &serna#e +adAdmin defined on the RA/I9S server and the pass5ord
+adAdminpa--.
Are yo& able to login to R1K FFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1" of (2
CCNA Security
d. EGit the SS7 session.
e. Stop the ?inRadi&s server on 'C3A by choosing %peration @ 29it.
f. :pen an SS7 session and atte#pt to log in again as +adAdmin.
Are yo& able to login to R1K FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
g. Close the SS7 client and open another SS7 session to R1 and atte#pt to log in as Admin8' 5ith a
pass5ord of Admin8'pa--.
?ith the ?inRadi&s server &navailable$ are yo& able to log in to R1K ?hy or 5hy notK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 9: Conigure +ADI;S support on +*3
Repeat steps 1 thro&gh * to config&re R( to access 'C3C as a RA/I9S server.
Tas" 4: ;se CLI to Disable ;nneeded Services on +' and Secure Against Login
Attac"s 0Chapter )1
Step ': ;se CLI to disable common IP services that can be e9ploited or net$or" attac"s3
Tip: Do& can iss&e the auto secure management co##and to see the #anage#ent related co##ands
that 5o&ld be generated. ?hen pro#pted 5ith IApply this configuration to running-config?
[yes]:J respond N% and then selectively copy the desired co##ands to a teGt file for editing and application
to the ro&ter.
a. /isable the follo5ing global services on the ro&ter.
service finger
service pad
service udp-sall-servers
service tcp-sall-servers
cdp run
ip bootp server
ip http server
ip finger
ip source-route
ip gratuitous-arps
ip identd
___________________________________________________________________________
_________________________________________________________________________
Note: /isabling the 7%%' server prevents 5eb3based access to the ro&ter via CC'. If yo& 5ant sec&re
access to the ro&ter via CC'$ yo& can enable it &sing the co##and ip http secure-server.
b. For each serial interface$ disable the follo5ing interface services.
ip redirects
ip pro!y-arp
ip unreachables
ip directed-broadcast
ip as"-reply
___________________________________________________________________________
_________________________________________________________________________
c. For each Fast Ethernet interface$ disable the follo5ing interface services.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 11 of (2
CCNA Security
ip redirects
ip pro!y-arp
ip unreachables
ip directed-broadcast
ip as"-reply
op enabled
___________________________________________________________________________
_________________________________________________________________________
Step ): Secure against login attac"s on +' and +*3
Config&re the follo5ing para#eters<
4loc6ing period 5hen login attac6 detected< *"
AaGi#&# login fail&res 5ith the device< 2
AaGi#&# ti#e period for crossing the failed login atte#pts< ("
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: Save the running coniguration to the startup coniguration or +' and +*3
Tas" 5: ;se CCP to Disable ;nneeded Services on +* 0Chapter )1
Step ': Conigure user credentials or :TTP router access prior to starting CCP3
a. Enable the 7%%' server on R(.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
:r enable the 7%%' sec&re server to connect sec&rely.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Create an ad#in acco&nt on R( 5ith privilege level 1, and pass5ord cisco')*,- for &se 5ith AAA
and CC'.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. 7ave CC' &se the local database to a&thenticate 5eb sessions.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ): Access CCP and discover +*3
a. R&n the CC' application on 'C3C. In the Select)Aanage Co##&nity 5indo5$ inp&t the R( I' address
'9)3'473*3' in the first I' Address)7ostna#e field. Enter admin in the 9serna#e field$ and
cisco')*,- in the 'ass5ord field. Clic6 on the %> b&tton.
b. At the CC' /ashboard$ clic6 the Discovery b&tton to discover and connect to R(. If the discovery
process fails$ &se the Discover Details b&tton to deter#ine the proble# in order to resolve the iss&e.
Step *: (egin the security audit3
a. Choose Conigure @ Security @ Security Audit and clic6 the Perorm Security Audit b&tton. Clic6
Ne9t at the 5elco#e screen
b. Choose Aast2thernet 8B' as the Inside %r&sted interface and Serial 8B8B' as the :&tside 9ntr&sted
interface.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 12 of (2
CCNA Security
c. 1ie5 the Sec&rity A&dit report and note 5hich services did not pass. Clic6 Close.
d. In the FiG It 5indo5$ clic6 Ai9 it to disable the follo5ing global and interface services<
#lobal services to disable:
service pad
cdp run
ip bootp server
ip source-route
$er-interface service to disable:
ip redirects
ip unreachables
op enabled
Note: /o not fiG .disable0 'roGy AR' beca&se this disables AR' on all R( interfaces and ca&ses a
proble#$ specifically 5ith interface Fa")1$ and pings to the R( 1'- server 2A-. %he 1'- server is
config&red in 'art , of the lab.
e. Clic6 Ne9t to vie5 a s&##ary of the proble#s that 5ill be fiGed. Clic6 Ainish and deliver the
co##ands to the ro&ter.
Tas" 7: Conigure a C(AC Aire$all on +' 0Chapter ,1
Step ': ;se the Cisco I%S AutoSecure eature to enable a C(AC ire$all on +'3
a. %o config&re only the ConteGt 4ased Access Control .C4AC0 fire5all on R1$ &se the auto secure
co##and and specify the firewall option. Respond as sho5n in the follo5ing A&toSec&re o&tp&t
to the A&toSec&re =&estions and pro#pts. %he responses are in bold.
R1% auto secure firewall
--- Auto&ecure 'onfiguration ---
((( Auto&ecure configuration enhances the security of the router) but it will
not a"e it absolutely resistant to all security attac"s (((
Auto&ecure will odify the configuration of your device* All configuration
changes will be shown* +or a detailed e!planation of how the configuration
changes enhance security and any possible side effects) please refer to
'isco*co for
Autosecure docuentation*
At any propt you ay enter ,?, for help*
-se ctrl-c to abort this session at any propt*
#athering inforation about the router for Auto&ecure
.s this router connected to internet? [no]: yes
/nter the nuber of interfaces facing the internet [1]: 1
.nterface .$-Address 01? 2ethod &tatus $rotocol
+ast/thernet030 unassigned 4/& unset adinistratively down down
+ast/thernet031 156*178*1*1 4/& anual up up
&erial03030 10*1*1*1 4/& &9AR$ up up
&erial03031 unassigned 4/& unset adinistratively down down
/nter the interface nae that is facing the internet: serial0/0/0
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1( of (2
CCNA Security
'onfigure ':A' +irewall feature? [yes3no]: yes
;his is the configuration generated:
ip inspect audit-trail
ip inspect dns-tieout <
ip inspect tcp idle-tie 1==00
ip inspect udp idle-tie 1800
ip inspect nae autosec_inspect cuseee tieout >700
ip inspect nae autosec_inspect ftp tieout >700
ip inspect nae autosec_inspect http tieout >700
ip inspect nae autosec_inspect rcd tieout >700
ip inspect nae autosec_inspect realaudio tieout >700
ip inspect nae autosec_inspect stp tieout >700
ip inspect nae autosec_inspect tftp tieout >0
ip inspect nae autosec_inspect udp tieout 1?
ip inspect nae autosec_inspect tcp tieout >700
ip access-list e!tended autosec_firewall_acl
perit udp any any e@ bootpc
deny ip any any
interface &erial03030
ip inspect autosec_inspect out
ip access-group autosec_firewall_acl in
A
end
Apply this configuration to running-config? [yes]: yes
Applying the config generated to running-config
R1%
+eb 16 18:>=:?8*0=0: BA-;0&/'-?-/CA:9/D: Auto&ecure is configured on the
device
Step ): +evie$ the AutoSecure C(AC coniguration3
a. %o 5hich interface is the a&tosecFinspect na#e applied and in 5hat directionK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. %o 5hich interface is the AC2 a&tosecFfire5allFacl applied and in 5hich directionK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. ?hat is the p&rpose of the AC2 a&tosecFfire5allFaclK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: Arom PC6AC ping the +) e9ternal <AN interace3
a. Fro# 'C3A$ ping the R2 interface S")")" at I' address 1".1.1.2.
b. Are the pings s&ccessf&lK ?hy or 5hy notK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ,: Add IC!P to the autosecDinspect list3
Config&re R1 to inspect ICA' and allo5 ICA' echo replies fro# o&tside hosts 5ith a ti#eo&t of *"
seconds.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1> of (2
CCNA Security
Step -: Arom PC6AC ping the +) e9ternal <AN interace3
a. Fro# 'C3A$ ping the R2 interface S")")" at I' address 1".1.1.2.
b. Are the pings s&ccessf&lK ?hy or 5hy notK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 4: Arom +)C ping PC6A3
Fro# R2 ping 'C3A. FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Are the pings s&ccessf&lK ?hy or 5hy notK FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 5: Test SS: access rom PC6C to +'3
Fro# eGternal host 'C3C$ start a '&%%D session to R1.
Is the SS7 session connection s&ccessf&lK ?hy or 5hy notK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 7: Conigure the +' ire$all to allo$ SS: access rom e9ternal hosts on the '9)3'473*38B),
net$or"3
a. /isplay the eGtended AC2 na#ed a&tosecFfire5allFacl that is applied to S")")" inbo&nd.
R1% show access-list autosec_firewall_acl
/!tended .$ access list autosec_firewall_acl
10 perit udp any any e@ bootpc
60 deny ip any any E?< atchesF
b. Config&re R1 to allo5 SS7 access by adding a state#ent to the eGtended AC2 a&tosecFfire5allFacl
that per#its the SS7 %C' port 22.
R1EconfigF% ip access-list extended autosec_firewall_acl
R1Econfig-e!t-naclF% 13 permit tcp 192.1!.3.0 0.0.0.2"" any e# 22
R1Econfig-e!t-naclF% end
c. Fro# eGternal host 'C3C$ start a '&%%D SS7 session to R1 at I' address 1".1.1.1 and log in as
RA/I9S &ser RadAd#in 5ith a pass5ord of RadAd#inpa,,.
d. Fro# the SS7 session on R1$ display the #odified eGtended AC2 a&tosecFfire5allFacl.
R1% show access-list autosec_firewall_acl
/!tended .$ access list autosec_firewall_acl
10 perit udp any any e@ bootpc
1> perit tcp 156*178*>*0 0*0*0*6?? any e@ 66 E17 atchesF
60 deny ip any any E70 atchesF
Step 9: Conigure the +' ire$all to allo$ NTP and .PN traic3
a. Config&re R1 to allo5 -et5or6 %i#e 'rotocol .-%'0 &pdates fro# R2 by adding a state#ent to the
eGtended AC2 a&tosecFfire5allFacl that per#its the -%' .9/' port 12(0.
R1EconfigF% ip access-list extended autosec_firewall_acl
R1Econfig-e!t-naclF% 1" permit udp host 10.1.1.2 host 10.1.1.1 e# ntp
b. Config&re R1 to allo5 I'sec 1'- traffic bet5een 'C3A and R( by adding a state#ent to the eGtended
AC2 a&tosecFfire5allFacl that per#its the I'sec Encaps&lating Sec&rity 'rotocol .ES'0.
Note: In 'art , of the lab$ R( 5ill be config&red as a 1'- server$ and 'C3A 5ill be the re#ote client.
R1Econfig-e!t-naclF% 1! permit esp any any
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1, of (2
CCNA Security
R1Econfig-e!t-naclF% end
c. /isplay the #odified eGtended AC2 a&tosecFfire5allFacl.
R1% show access-list autosec_firewall_acl
/!tended .$ access list autosec_firewall_acl
10 perit udp any any e@ bootpc
1> perit tcp 156*178*>*0 0*0*0*6?? any e@ 66 E7< atchesF
1? perit udp host 10*1*1*6 host 10*1*1*1 e@ ntp E> atchesF
18 perit esp any any
60 deny ip any any E61 atchesF
Step '8: Test Telnet access rom internal PC6A to e9ternal router +)3
a. Fro# 'C3A$ %elnet to R2 at I' address '83'3'3) &sing the vty line pass5ord ciscovtypass.
':GH telnet 10.1.1.2
Is the %elnet atte#pt s&ccessf&lK ?hy or 5hy notK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. 2eave the %elnet session open.
Step '': Display C(AC inspection sessions3
/isplay the I' inspect session to see the active %elnet session fro# 'C3A to R2.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" 9: Conigure a E(A Aire$all on +* 0Chapter ,1
Step ': ;se CCP to discover +*3
a. R&n the CC' application on 'C3C. In the Select)Aanage Co##&nity 5indo5$ inp&t the R( I' address
'9)3'473*3' in the first I' Address)7ostna#e field. Enter admin in the 9serna#e field$ and
cisco')*,- in the 'ass5ord field. Clic6 on the %> b&tton.
b. At the CC' /ashboard$ clic6 on the Discovery b&tton to discover and connect to R(. If the discovery
process fails$ &se the Discover Details b&tton to deter#ine the proble# in order to resolve the iss&e.
Step ): ;se the CCP Aire$all $iFard to conigure a E(A on +*3
a. Clic6 the Conigure b&tton at the top of the CC' screen$ and then clic6 Security @ Aire$all @
Aire$all.
b. Select (asic Aire$all and clic6 the Launch the selected tas" b&tton. :n the 4asic Fire5all
Config&ration 5i8ard screen$ clic6 Ne9t.
c. Chec6 the Inside 0trusted1 chec6 boG for Aast 2thernet8B' and the %utside 0untrusted1 chec6 boG
for Serial8B8B'. Clic6 Ne9t. Clic6 %> 5hen the CC' access 5arning is displayed.
d. Choose Lo$ Security and clic6 Ne9t. In the S&##ary 5indo5$ clic6 Ainish and deliver the
co##ands to the ro&ter.
e. Clic6 %> in the Co##ands /elivery Stat&s 5indo5.
Step *: .eriy E(A unctionality3
a. Fro# 'C3C$ ping the R2 interface S")")1 at I' address 1".2.2.2. FFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Are the pings s&ccessf&lK ?hy or 5hy notK FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Fro# eGternal ro&ter R2$ ping 'C3C at I' address 12.1*+.(.(. FFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1* of (2
CCNA Security
Are the pings s&ccessf&lK ?hy or 5hy notK FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. Fro# ro&ter R2$ %elnet to R( at I' address 1".2.2.1. FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Is the %elnet atte#pt s&ccessf&lK ?hy or 5hy notK FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
d. Fro# 'C3C on the R( internal 2A-$ %elnet to R2 at I' address '83)3)3) and &se pass5ord
ciscovtypass. FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
e. ?ith the %elnet session open fro# 'C3C to R2$ iss&e the co##and show policy-map type
inspect $one-pair session on R(. Contin&e pressing 2nter &ntil yo& see an Inspect
Established session section to5ard the end.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ,: Save the running coniguration to the startup coniguration3
Tas" '8: Conigure Intrusion Prevention System 0IPS1 on +' ;sing Cisco I%S
0Chapter -1
Step ': 0%ptional1 Install the TATP server on PC6A3
If a %F%' server is not c&rrently installed on 'C3A$ do5nload %ftpd(2 fro# http<))tftpd(2.Ho&nin.net and install
it on yo&r des6top. If it is already installed$ go to Step 2.
Step ): Prepare the router and TATP server3
%o config&re Cisco I:S I'S ,.G$ the I:S I'S Signat&re pac6age file and p&blic crypto 6ey files #&st be
available on 'C3A. Chec6 5ith yo&r instr&ctor if these files are not on the 'C. %hese files can be do5nloaded
fro# Cisco.co# 5ith a valid &ser acco&nt that has proper a&thori8ation.
a. 1erify that the I%S6Sxxx6CLI3p"g signat&re pac6age file is in a %F%' folder. %he xxx is the version
n&#ber and varies depending on 5hich file 5as do5nloaded.
b. 1erify that the realm6cisco3pub3"ey3t9t file is available and note its location on 'C3A. %his is the
p&blic crypto 6ey &sed by I:S I'S.
c. 1erify or create the I'S directory in ro&ter flash on R1. Fro# the R1 C2I$ display the content of flash
#e#ory &sing the show flash co##and. Chec6 5hether the ipsdir directory eGists and if it has files
in it. FFFFFFFFFFFFFFFFFFFFFFFFFF
d. If the ipsdir directory is not listed$ create it.
R1% m%dir ipsdir
'reate directory filenae [ipsdir]? &ress 'nter
'reated dir flash:ipsdir
e. If the ipsdir directory eGists and the signat&re files are in it$ yo& #&st re#ove the files to perfor# this
part of the lab. S5itch to the ipsdir directory and verify that yo& are in the directory. Re#ove the files
fro# the directory$ and then ret&rn to the flash root directory 5hen yo& are finished.
R1% cd ipsdir
R1% pwd
flash:3ipsdir3
R1% delete (1)
Delete filenae [3ipsdir3R1(]?
Delete flash:3ipsdir3R1-sigdef-typedef*!l? [confir]
Delete flash:3ipsdir3R1-sigdef-category*!l? [confir]
Delete flash:3ipsdir3R1-sigdef-default*!l? [confir]
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1C of (2
CCNA Security
Delete flash:3ipsdir3R1-sigdef-delta*!l? [confir]
Delete flash:3ipsdir3R1-seap-delta*!l? [confir]
Delete flash:3ipsdir3R1-seap-typedef*!l? [confir]
R1% cd flash*/
R1% pwd
flash:3
Step *: %pen the IPS crypto "ey ile and copy the contents to the router3
:n 'C3A$ locate the crypto 6ey file na#ed real#3cisco.p&b.6ey.tGt and open it &sing -otepad or another
teGt editor. :n R1$ enter global config #ode$ copy the contents of the file$ and paste the contents to the
ro&ter.
%he contents sho&ld loo6 si#ilar to the follo5ing<
crypto "ey pub"ey-chain rsa
naed-"ey real-cisco*pub signature
"ey-string
>0860166 >00D0705 6A87=887 +<0D0101 010?000> 86010+00 >086010A 06860101
00'15/5> A8A+16=A D7''<A6= ?05<A5<? 607:/>A6 07+:A1>+ 7+16':?: =/==1+17
1</7>0D? '06A'6?6 516:/6<+ ><+DD5'8 11+'<A+< D'DD81D5 =>'DA:'> 700<D168
:155A:': D>=/D0+5 08?+AD'1 >?5'185/ +>0A+10A '0/+:76= </0<7=:+ >/?>0?>/
?:61=7A5 D<A?/D/> 0658A+0> D/D<A?:8 5=<50>5D 60+>077> 5A'7=:5> '0116A>?
+/>+0'8< 85:':<:: 55=A/<=' +A5/=81D +7?8<?D7 8?/A+5<= 7D5''8/> +0:08:8?
?0=><<66 ++:/8?:5 ?/=185++ ''185':5 75'=7+5' A8=D+:A? <A0A+55/ AD<78'>7
007'+=58 0<5+88+8 A>:>+:1+ 5+:<:>': ??>5/1D1 575>'':: ??1+<8D6 856>?7A/
6+?7D867 8518/+>' 80'A=+=D 8<:+'A>: :++778/5 785<86A? '+>1':7/ :=:05=D>
+>060>01 0001
@uit
Step ,: Create an IPS rule3
:n R1$ create an I'S r&le na#ed iosips. %his r&le 5ill be &sed later on an interface to enable I'S.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step -: Conigure the IPS signature storage location in router lash memory3
Specify the location lash:ipsdir 5here the signat&re files 5ill be stored.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 4: Conigure Cisco I%S IPS to use a pre6deined signature category3
Retire all signat&res in the IallJ category and then &nretire the iosDips basic category.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 5: Apply the IPS rule to interaces S8B8B8 and Aa8B'3
a. Apply the iosips r&le that yo& created on the S8B8B8 interface in the inbound direction.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1+ of (2
CCNA Security
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Apply the I'S r&le to the R1 Aa8B' interface in the inbound direction.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 7: .eriy the I%S IPS signature pac"age location and TATP server setup
a. 1erify connectivity bet5een R1 and 'C3A$ the %F%' server.
b. 1erify that the 'C has the I'S signat&re pac6age file in a directory on the %F%' server. %his file is
typically na#ed I:S3Sxxx3C2I.p6g$ 5here xxx is the signat&re file version.
Note: 9se the ne5est signat&re file available if the ro&ter #e#ory can s&pport it. If a signat&re file is
not present$ contact yo&r instr&ctor before contin&ing.
c. Start the %F%' server and set the defa< directory to the one that contains the I'S signat&re
pac6age.
Step 9: Copy the signature pac"age rom the TATP server to the router3
a. 9se the copy tftp co##and to retrieve the signat&re file. 4e s&re to &se the idconf 6ey5ord at
the end of the copy co##and.
Note: I##ediately after the signat&re pac6age is loaded to the ro&ter$ signat&re co#piling begins.
Allo5 ti#e for this process to co#plete. It can ta6e several #in&tes.
DDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD
b. /isplay the contents of the ipsdir directory created earlier.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. 9se the show ip ips all co##and to see an I'S config&ration stat&s s&##ary. %o 5hich
interfaces and in 5hich direction is the iosips r&le appliedK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step '8: Save the running coniguration to the startup coniguration3
Tas" '': Conigure IPS on +* ;sing CCP 0Chapter -1
Step ': 0%ptional1 Install the TATP server on PC6C3
If a %F%' server is not c&rrently installed on 'C3C$ do5nload %ftpd(2 fro# http<))tftpd(2.Ho&nin.net and install
it on yo&r des6top. If it is already installed$ go to Step 2.
Step ): Prepare the router and TATP server3
%o config&re Cisco I:S I'S ,.G$ the I:S I'S signat&re pac6age file and p&blic crypto 6ey files #&st be
available on 'C3C. Chec6 5ith yo&r instr&ctor if these files are not on the 'C. %hese files can be do5nloaded
fro# Cisco.co# 5ith a valid &ser acco&nt that has proper a&thori8ation.
a. 1erify that the I%S6Sxxx6CLI3p"g signat&re pac6age file is in a %F%' folder. %he xxx is the version
n&#ber and varies depending on 5hich file 5as do5nloaded.
Note: 9se the ne5est signat&re file available if the ro&ter #e#ory can s&pport it. If a signat&re file is
not present$ contact yo&r instr&ctor before contin&ing.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 1 of (2
CCNA Security
b. 1erify that the realm6cisco3pub3"ey3t9t file is available and note its location on 'C3C. %his is the
p&blic crypto 6ey &sed by Cisco I:S I'S.
c. 1erify or create the I'S directory in ro&ter flash on R1. Fro# the R1 C2I$ display the content of flash
#e#ory and chec6 to see if the ipsdir directory eGists.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
d. If the ipsdir directory is not listed$ create it in privileged EBEC #ode.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: .eriy the I%S IPS signature pac"age and TATP server setup3
a. 1erify connectivity bet5een R( and 'C3C$ the %F%' server$ &sing the ping co##and.
b. 1erify that the 'C has the I'S signat&re pac6age file in a directory on the %F%' server. %his file is
typically na#ed I:S3Sxxx3C2I.p6g$ 5here xxx is the signat&re file version n&#ber.
Note: If this file is not present$ contact yo&r instr&ctor before contin&ing.
c. Start %ftpd(2 or another %F%' server and set the defa< directory to the one 5ith the I'S signat&re
pac6age in it. %a6e note of the filena#e for &se in the neGt step.
Step ,: Conigure +* to allo$ CCP Access and Discovery3
a. R&n the CC' application on 'C3C. In the Select)Aanage Co##&nity 5indo5$ inp&t R( I' address
'9)3'473*3' in the first I' Address)7ostna#e field. Enter admin in the 9serna#e field$ and
cisco')*,- in the 'ass5ord field. Clic6 on the %> b&tton.
b. At the CC' /ashboard$ clic6 on the Discovery b&tton to discover and connect to R(. If the discovery
process fails$ &se the Discover Details b&tton to deter#ine the proble# in order to resolve the iss&e.
Step -: ;se the CCP IPS $iFard to conigure IPS3
a. Clic6 the Conigure b&tton at the top of the CC' screen and then choose Security @ Intrusion
Prevention @ Create IPS. Clic6 the Launch IPS +ule <iFard b&tton to begin the I'S config&ration. If
pro#pted regarding S/EE notification$ clic6 %>. Clic6 Ne9t at the 5elco#e screen.
b. Apply the I'S r&le in the inbo&nd direction for FastEthernet")1 and Serial")")1. Clic6 Ne9t.
c. In the Signat&re File and '&blic @ey 5indo5$ specify the signat&re file 5ith a 9R2 and &se %F%' to
retrieve the file fro# 'C3C. Enter the I' address of the 'C3C %F%' server and the filena#e. Clic6 %>.
d. In the Signat&re File and '&blic @ey 5indo5$ enter the na#e of the p&blic 6ey file realm6cisco3pub.
e. :pen the p&blic 6ey file and copy the teGt that is bet5een the phrase I6ey3stringJ and the 5ord I=&it.J
'aste the teGt into the >ey field in the Config&re '&blic @ey section. Clic6 Ne9t.
f. In the Config 2ocation and Category 5indo5$ specify lash:Bipsdir as the location to store the
signat&re infor#ation. Clic6 %>.
g. In the Choose Category field of the Config 2ocation and Category 5indo5$ choose basic.
h. Clic6 Ne9t to display the S&##ary 5indo5$ and clic6 Ainish and deliver the co##ands to the ro&ter.
Clic6 %>.
Note: Allo5 the signat&re config&ration process to co#plete. %his can ta6e several #in&tes.
Step 4: 0%ptional1 .eriy IPS unctionality $ith CCP !onitor and SuperScan3
a. If S&perScan is not on 'C3C$ do5nload the S&perScan >." tool fro# the Scanning %ools gro&p at
http<))555.fo&ndstone.co#.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2" of (2
CCNA Security
b. Start S&perScan on 'C3C. Clic6 the :ost and Service Discovery tab. Chec6 the Timestamp
+e/uest chec6 boG$ and &nchec6 the 2cho +e/uest chec6 boG. Scroll the 9/' and %C' port
selection lists and notice the range of ports that 5ill be scanned.
c. Clic6 the Scan tab and enter the I' address of R2 S")")1 .'83)3)3)0 in the :ostnameBIP field.
Note: Do& can also specify an address range$ s&ch as 1".1.1.1 to 1".1.1.2,>$ by entering an address
in the Start IP and 2nd IP fields. %he progra# scans all hosts 5ith addresses in the range specified.
d. Clic6 the b&tton 5ith the bl&e arro5 in the lo5er left corner of the screen to start the scan.
Step 5: Chec" the results $ith CCP logging3
a. Enter the logging +uffered co##and in config #ode on R(.
b. Fro# Cisco CC'$ choose !onitor @ +outer @ Logging.
c. Clic6 the ;pdate b&tton. Do& 5ill see that Cisco I:S I'S has been logging the port scans generated
by S&perScan.
d. ?hat syslog #essages did yo& seeK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 7: Save the running coniguration to the startup coniguration3
Tas" '): (ac" ;p and Secure the Cisco +outer I%S Image and Coniguration
Ailes 0Chapter )1
Note: %he proced&res described here can also be &sed to bac6 &p the s5itch I:S i#ages and config&ration
files.
Step ': (ac" up the I%S Image rom +' and +* to a TATP server3
a. Create a directory for the I:S i#ages on 'C3A and 'C3C.
b. Start the %F%' server on 'C3A and choose the I:S i#ages directory as the defa< directory.
c. Copy the R1 I:S i#age to the 'C3A %F%' server as a bac6&p in case the c&rrent i#age beco#es
corr&pted. FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
d. Start the %F%' server on 'C3C and choose the I:S i#ages directory as the defa< directory.
e. Copy the R( I:S i#age to the %F%' server as a bac6&p in case the c&rrent i#age beco#es
corr&pted.
Note: %he I:S i#age on R1 sho&ld be the sa#e as the one for R($ so a single bac6&p co&ld s&ffice for
both ro&ters.
Step ): (ac" up the coniguration iles rom +' and +* to a TATP server3
a. Create a directory for config&rations on 'C3A and 'C3C.
b. Start the %F%' server on 'C3A and choose the Configs directory as the defa< directory.
c. Copy the R1 start&p3config file to the 'C3A %F%' server as a bac6&p.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Note: If changes have been #ade to the r&nning config$ yo& can save the# to the start&p config
before bac6ing &p the config file.
d. Start the %F%' server on 'C3C and choose the Configs directory as the defa< directory.
e. Copy the R( start&p3config file to the 'C3C %F%' server as a bac6&p.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 21 of (2
CCNA Security
Step *: Secure the Cisco I%S image and archive a copy o the running coniguration or +' and
+*3
a. Sec&re the I:S boot i#age to enable Cisco I:S i#age resilience and hide the file fro# dir and
show co##ands. FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Sec&re the ro&ter r&nning config&ration and sec&rely archive it in persistent storage .flash0.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ,: .eriy that the image and coniguration are secured3
/isplay the stat&s of config&ration resilience and the pri#ary bootset filena#e.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Part ,: Secure Net$or" S$itches 0Chapter 41
Tas" ': Conigure Pass$ords and a Login (anner on All S$itches 0Chapter )1
Step ': Conigure the enable secret pass$ord3
9se an enable secret pass5ord of cisco')*,-. FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ): 2ncrypt a plainte9t pass$ord3
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: Conigure the console line3
Config&re a console pass5ord of ciscoconpass and enable login. Set the eGec3ti#eo&t to log o&t after -
#in&tes of inactivity. 'revent console #essages fro# interr&pting co##and entry.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Note: %he vty lines for the s5itches are config&red for SS7 in %as6 2.
Step ,: Conigure a login $arning banner3
Config&re a 5arning to &na&thori8ed &sers 5ith a #essage3of3the3day .A:%/0 banner that says
I9na&thori8ed access strictly prohibited and prosec&ted to the f&ll eGtent of the la5J.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step -: Disable :TTP access3
7%%' access to the s5itch is enabled by defa<. %o prevent 7%%' access$ disable the 7%%' server and
7%%' sec&re server.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 22 of (2
CCNA Security
Tas" ): Conigure S$itches as NTP Clients 0Chapter )1
Note: Ro&ter R2 is the #aster -%' server. All other ro&ters and s5itches learn their ti#e fro# it$ either
directly or indirectly.
Step ': Conigure S'C S)C and S* to become NTP clients o +)3
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ): .eriy that S' has made an association $ith +)3 FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" *: Conigure Syslog Support on All S$itches 0Chapter )1
Step ': 0%ptional1 Install the syslog server on PC6A and PC6C3
If a syslog server is not c&rrently installed on the host$ do5nload the latest version of @i5i fro#
http<))555.6i5isyslog.co# or %ftpd(2 fro# http<))tftpd(2.Ho&nin.net and install it on yo&r des6top. If it is already
installed$ go to Step 2.
Step ): Conigure S' to log messages to the PC6A syslog server3
a. 1erify that yo& have connectivity bet5een S1 and host 'C3A by pinging the S1 12A- 1 interface I'
address 12.1*+.1.11 fro# 'C3A. If the pings are not s&ccessf&l$ tro&bleshoot as necessary before
contin&ing.
b. Config&re the syslog service on the s5itch to send syslog #essages to the syslog server.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" ,: Conigure the SS: Server on All S$itches 0Chapter )1
Step ': Conigure a domain name3
Enter global config&ration #ode and set the do#ain na#e.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ): Conigure a privileged user or login rom the SS: client3
9se the username co##and to create the &ser I/ 5ith the highest possible privilege level and a secret
pass5ord.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: Conigure the incoming vty lines3
Config&re vty access on lines " thro&gh 1,. Specify that a privilege level of 1, is re=&ired to access the
vty lines$ &se the local &ser acco&nts for #andatory login and validation$ and accept only SS7
connections.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2( of (2
CCNA Security
Step ,: #enerate the +SA encryption "ey pair3
%he s5itch &ses the RSA 6ey pair for a&thentication and encryption of trans#itted SS7 data. Config&re
the RSA 6eys 5ith 1"2> for the n&#ber of #od&l&s bits.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step -: .eriy SS: connectivity to S' rom the SS: client PC6A3
a. If the SS7 client is not already installed$ do5nload either %era%er# or '&%%D.
b. 2a&nch the client$ enter the 12A- 1 I' address$ and enter the Admin8' &serna#e and pass5ord.
c. Close the '&%%D SS7 session 5indo5 5ith the exit or #uit co##and.
d. %ry to open a %elnet session to s5itch S1 fro# 'C3A. Are yo& able to open the %elnet sessionK ?hy
or 5hy notK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" -: Conigure Authentication ;sing AAA and +ADI;S on All S$itches
0Chapter *1
Step ': 0%ptional1 Do$nload and conigure the <in+adius sot$are3
a. If ?inRadi&s is not c&rrently installed on 'C3A and 'C3C$ do5nload the latest version fro#
http<))555.s&ggestsoft.co#)soft)itcons<2""")5inradi&s)$ http<))5inradi&s.soft(2.co#$
http<))555.brothersoft.co#)5inradi&s32"1>.ht#l. %here is no installation set&p. %he eGtracted
?inRadi&s.eGe file is eGec&table.
b. Start the ?inRadi&s.eGe application. If the application is being started for the first ti#e$ follo5 the
instr&ctions to config&re the ?inRadi&s server database.
Step ): Conigure users and pass$ords on the <in+adius server3
Note: If the RA/I9S &ser acco&nts 5ere previo&sly config&red$ yo& can s6ip this step. If the RA/I9S
server has been sh&t do5n and restarted$ yo& #&st recreate the &ser acco&nts.
a. Add &serna#e +adAdmin 5ith a pass5ord of +adAdminpa--.
b. Add &serna#e +ad;ser 5ith a pass5ord of +ad;serpa--.
Step *: 2nable AAA3
Create a AAA ne5 #odel to enable AAA.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ,: Conigure the deault login authentication list3
Config&re the list to first &se RA/I9S for the a&thentication service and then localC to allo5 access based
on the local s5itch database if a RA/I9S server cannot be reached.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step -: .eriy connectivity bet$een S' and the PC6A +ADI;S server3
'ing fro# S1 to 'C3A. FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
If the pings are not s&ccessf&l$ tro&bleshoot the 'C and s5itch config&ration before contin&ing.
Step 4: Speciy a +ADI;S server3
Config&re the s5itch to access the RA/I9S server at 'C3A. Specify auth6port '7') and acct6port '7'*$
along 5ith the I' address and secret 6ey of ?inRadi&s for the RA/I9S server.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2> of (2
CCNA Security
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 5: Test the +ADI;S coniguration by logging in to the console on S'3
a. EGit to the initial s5itch screen that displays the follo5ing< &1 con0 is now available* $ress
R/;-RC to get started.
b. 2og in 5ith the &serna#e +adAdmin and pass5ord +adAdminpa--. Can yo& log in 5ith #ini#al
delayK FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Note: If yo& eGit the ?inRadi&s server and restart it$ yo& #&st recreate the &ser acco&nts fro# Step 2.
Step 7: Test your coniguration by connecting to S' $ith SS:3
a. Clear the log on the ?inRadi&s server by choosing Log @ Clear.
b. 9se '&%%D or another ter#inal e#&lation client to open an SS7 session fro# 'C3A to S1.
c. At the login pro#pt$ enter the &serna#e +adAdmin defined on the RA/I9S server and a pass5ord
of +adAdminpa--.
Are yo& able to login to S1K FFFFFFFFFFF
Tas" 4: Secure Trun" Ports 0Chapter 41
Step ': Conigure trun" ports on S' and S)3
a. Config&re port Fa")1 on S1 as a tr&n6 port.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Config&re port Fa")1 on S2 as a tr&n6 port.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. 1erify that S1 port Fa")1 is in tr&n6ing #ode.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ): Change the native .LAN or the trun" ports on S' and S)3
Changing the native 12A- for tr&n6 ports to an &n&sed 12A- helps prevent 12A- hopping attac6s.
a. Set the native 12A- on the S1 Fa")1 tr&n6 interface to an &n&sed .LAN 99.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Set the native 12A- on the S2 Fa")1 tr&n6 interface to .LAN 99.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step *: Prevent the use o DTP on S' and S)3
Set the tr&n6 ports on S1 and S2 so that they do not negotiate by t&rning off the generation of /%'
fra#es.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2, of (2
CCNA Security
Step ,: .eriy the trun"ing coniguration on port Aa8B'3
______________________________________________________________________________
____________________________________________________________________________
Step -: 2nable storm control or broadcasts3
Enable stor# control for broadcasts on the tr&n6 port 5ith a ," percent rising s&ppression level &sing the
storm-control +roadcast co##and.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step 4: .eriy the coniguration $ith the sho$ run command3
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" 5: Secure Access Ports 0Chapter 41
4y #anip&lating the S%' root bridge para#eters$ net5or6 attac6ers hope to spoof his or her syste# as the
root bridge in the topology. Alternatively$ they can spoof a rog&e s5itch that they added to the net5or6 as the
root bridge. If a port that is config&red 5ith 'ortFast receives a 4'/9$ S%' can p&t the port into the bloc6ing
state by &sing a feat&re called 4'/9 g&ard.
Step ': Disable trun"ing on S'C S)C and S* access ports3
a. :n S1$ config&re ports Fa"), and F")* as access #ode only.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. :n S2$ config&re Fa")1+ as access #ode only.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. :n S($ config&re ports Fa"), and Fa")1+ as access #ode only.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" 7: Protect Against STP Attac"s 0Chapter 41
%he topology has only t5o s5itches and no red&ndant paths$ b&t S%' is still active. In this step$ yo& enable
so#e s5itch sec&rity feat&res that can help red&ce the possibility of an attac6er #anip&lating s5itches via
S%'3related #ethods.
Step ': 2nable PortAast on S'C S)C and S* access ports3
'ortFast is config&red on access ports that connect to a single 5or6station or server to enable the# to
beco#e active #ore =&ic6ly.
a. Enable 'ortFast on the S1 Fa"), and Fa")* access ports.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Enable 'ortFast on the S2 Fa")1+ access port.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. Enable 'ortFast on the S( Fa"), and Fa")1+ access port.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2* of (2
CCNA Security
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ): 2nable (PD; guard on the S'C S)C and S* access ports3
4'/9 g&ard is a feat&re that can help prevent rog&e s5itches and spoofing on access ports. Enable 4'/9
g&ard on the s5itch ports previo&sly config&red as access only.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Tas" 9: Conigure Port Security and Disable ;nused Ports 0Chapter 41
Step ': Conigure basic port security3
Sh&t do5n all end3&ser access ports that are in &se and enable basic defa< port sec&rity. %his sets the
#aGi#&# AAC addresses to 1 and the violation action to sh&tdo5n. Reiss&e the port sec&rity co##and
&sing the stic%y option to allo5 the sec&re AAC address that is dyna#ically learned on a port$ to be added
to the s5itch r&nning config&ration. Re3enable each access port to 5hich port sec&rity 5as applied.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ): Disable unused ports on S' and S)3
As a f&rther sec&rity #eas&re$ disable any ports not being &sed on the s5itch.
a. 'orts Fa")1$ Fa"),$ and Fa")* are &sed on s5itch S1. Sh&t do5n the re#aining Fast Ethernet ports
and the t5o Gigabit Ethernet ports.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. 'orts Fa"1) and Fa")1+ are &sed on s5itch S2. Sh&t do5n the re#aining Fast Ethernet ports and the
t5o Gigabit Ethernet ports.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. 'orts Fa"), and Fa")1+ are &sed on s5itch S(. Sh&t do5n the re#aining Fast Ethernet ports and the
t5o Gigabit Ethernet ports.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2C of (2
CCNA Security
Step *: 0%ptional1 !ove active ports to another .LAN and change the management .LAN3
As a f&rther sec&rity #eas&re$ yo& can #ove all active end3&ser and ro&ter ports to a 12A- other than the
defa< 12A- 1 on the s5itches. Do& can also change the #anage#ent 12A- fro# 12A- 1 to another 12A-$
b&t yo& #&st have at least one end3&ser host port in that 12A- to #anage the s5itch re#otely &sing %elnet$
SS7$ or 7%%'.
Note: %he follo5ing config&ration allo5s yo& to #anage either s5itch re#otely fro# either 'C3A or 'C34. Do&
can only access the s5itches re#otely &sing SS7$ beca&se %elnet and 7%%' have been disabled. %he
proced&re for s5itch S( is also sho5n.
a. Config&re a ne5 12A- for &sers on each s5itch &sing the follo5ing co##ands.
Note: Do& co&ld also config&re 12A- 1" on s5itch S($ b&t it 5o&ld not co##&nicate 5ith 12A- 1" on
s5itches S1 and S2.
DDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD
DDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD
DDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD
DDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD
DDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD
b. Add the c&rrent active access .non3tr&n60 ports to the ne5 12A-.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. :n each s5itch$ re#ove the #anage#ent 12A- I' address fro# 12A- 1 .config&red in 'art 1 of the
lab0 and sh&t it do5n.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
d. Config&re a #anage#ent 12A- I' address for the 12A- 1" interface on S1 and S2 and enable it.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
e. Config&re a #anage#ent 12A- I' address for the 12A- (" interface on S( and enable it.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ,: Save the running6conig to the startup6conig3
Part -: Coniguring .PN +emote Access
In 'art ,$ config&re a re#ote access I'sec 1'-. R( is config&red via CC' as an Easy 1'- server$ and the Cisco
1'- Client is config&red on 'C3A. %he 'C3A host si#&lates an e#ployee connecting fro# ho#e or a re#ote
office over the Internet. Ro&ter R2 si#&lates an Internet IS' ro&ter.
Tas" ': ;se the CCP .PN <iFard to Conigure the 2asy .PN Server 0Chapter 71
Step ': Conigure +* to allo$ CCP Access and Discovery3
a. Enable the 7%%' server on R(.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2+ of (2
CCNA Security
:r enable the 7%%' sec&re server to connect sec&rely.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
b. Create an ad#in acco&nt on R( 5ith privilege level 1, for &se 5ith AAA and CC'.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
c. 7ave CC' &se the local database to a&thenticate 5eb sessions.
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
d. R&n the CC' application on 'C3C. In the Select)Aanage Co##&nity 5indo5$ inp&t the R( I' address
12.1*+.(.1 in the first I' Address)7ostna#e field. Enter admin in the 9serna#e field$ and
cisco')*,- in the 'ass5ord field. Clic6 on the %> b&tton.
e. At the CC' /ashboard$ clic6 on the Discovery b&tton to discover and connect to R(. If the discovery
process fails$ clic6 the Discover Details b&tton to deter#ine the proble# in order to resolve the
iss&e.
Step ): Launch the 2asy .PN Server $iFard3
Clic6 the Conigure b&tton at the top of the CC' ho#e screen and choose Security @ .PN @ 2asy .PN
Server$ and then clic6 Launch 2asy .PN Server <iFard. Clic6 Ne9t on the ?elco#e Screen to
contin&e.
Note: %he Easy 1'- Server ?i8ard chec6s the ro&ter config&ration to see if AAA is enabled. If AAA is not
enabled$ the Enable AAA 5indo5 displays. AAA 5as enabled on the ro&ter previo&sly.
Step *: Conigure the virtual tunnel interace and authentication3
a. Choose the interface on 5hich the client connections ter#inate. Clic6 the ;nnumbered to radio
b&tton$ and choose the Serial8B8B' interface fro# the drop3do5n #en&.
b. Choose Pre6shared >eys for the a&thentication type and clic6 Ne9t to contin&e.
Step ,: Select an I>2 proposal3
In the Internet @ey EGchange .I@E0 'roposals 5indo5$ the defa< I@E proposal is &sed for R(. Clic6 Ne9t
to accept the defa< I@E policy.
Step -: Select the transorm set3
In the %ransfor# Sets 5indo5$ the defa< CC' transfor# set is &sed. Clic6 Ne9t to accept the defa<
transfor# set.
Step 4: Speciy the group authoriFation and group policy loo"up3
a. In the Gro&p A&thori8ation and Gro&p 'olicy 2oo6&p 5indo5$ choose the Local option.
b. Clic6 Ne9t to create a ne5 AAA #ethod list for gro&p policy loo6&p that &ses the local ro&ter
database.
Step 5: Conigure user authentication 0=Auth13
a. In the 9ser A&thentication .BA&th0 5indo5$ chec6 the 2nable ;ser Authentication chec6 boG and
choose Local %nly.
b. Clic6 the Add ;ser Credentials b&tton. In the 9ser Acco&nts 5indo5$ yo& can vie5 c&rrently defined
local &sers or add ne5 &sers. ?hich &ser acco&nt is c&rrently defined locallyK FFFFFFFFFFFFFFFFFF
c. Add the ne5 &ser .PN;ser' 5ith a pass5ord of .PN;ser'pa-- and clic6 %>.
d. Clic6 %> to close the 9ser Acco&nts 5indo5. Clic6 Ne9t.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age 2 of (2
CCNA Security
Step 7: Speciy group authoriFation and user group policies3
In the Gro&p A&thori8ation and 9ser Gro&p 'olicies 5indo5$ yo& #&st create at least one gro&p policy for the
1'- server.
a. Clic6 Add to create a gro&p policy.
b. In the Add Gro&p 'olicy 5indo5$ enter .PN6Access in the Name o This #roup field. Enter a ne5
pre3shared 6ey of cisco')*,- and then re3enter it. 2eave the Pool Inormation boG chec6ed. Enter a
starting address of '9)3'473*3)88$ an ending address of '9)3'473*3)-8$ and a s&bnet #as6 of
)--3)--3)--38.
c. Clic6 %> to accept the entries.
d. A CC' 5arning #essage displays indicating that the I' address pool and the Fast Ethernet ")1
address are in the sa#e s&bnet. Clic6 ?es to contin&e.
e. Chec6 the Conigure Idle Timer chec6 boG and enter 1 ho&r$ " #in&tes$ and " seconds.
f. ?hen the Cisco %&nneling Control 'rotocol .c%C'0 5indo5 displays$ do not enable c%C'. Clic6 %> if
a fire5all 5arning #essage displays. Clic6 Ne9t to contin&e.
g. ?hen the Easy 1'- Server 'ass3thro&gh Config&ration 5indo5 displays$ #a6e s&re that the Action
!odiy chec6 boG is chec6ed. %his option allo5s CC' to #odify the fire5all on S")")1 to allo5 I'sec
1'- traffic to reach the internal 2A-.
Step 9: +evie$ the coniguration summary and deliver the commands3
Scroll thro&gh the co##ands that CC' 5ill send to the ro&ter. Clic6 Ainish.
Step '8: Test the .PN Server
Do& are ret&rned to the #ain 1'- 5indo5 5ith the Edit 1'- Server tab selected. Clic6 the Test .PN Server
b&tton in the lo5er right corner of the screen. In the 1'- %ro&bleshooting 5indo5$ clic6 the Start b&tton. Clic6
Close to eGit the 1'- %ro&bleshooting 5indo5.
Tas" ): ;se the Cisco .PN Client to Test the +emote Access .PN 0Chapter 71
Step ': 0%ptional1 Install the Cisco .PN client3
If the Cisco 1'- Client soft5are is not already installed on host 'C3A$ install it no5. If yo& do not have the
Cisco 1'- Client soft5are or are &ns&re of the process$ contact yo&r instr&ctor.
Step ): Conigure PC6A as a .PN client to access the +* .PN server
a. Start the Cisco 1'- Client. Select Connection 2ntries @ Ne$ or clic6 the Ne$ icon 5ith the pl&s
sign .L0 on it.
b. Enter the follo5ing infor#ation to define the ne5 connection entry. Clic6 Save 5hen yo& are finished.
Connection Entry< .PN6Corp
/escription< Connection to +* corporate net$or"
7ost< '83)3)3' .I' address of the R( S")")1 interface0
Gro&p A&thentication -a#e< .PN6Access .specifies the address pool config&red in %as6 20
'ass5ord< cisco')*,- .pre3shared 6ey config&red in %as6 20
Confir# 'ass5ord< cisco')*,-
Note: %he gro&p a&thentication na#e and pass5ord are case3sensitive and #&st #atch the ones created
on the 1'- Server.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age (" of (2
CCNA Security
Step *: Test access rom PC6A $ithout a .PN connection3
Note: In the previo&s step$ yo& created a 1'- connection entry on the 1'- client co#p&ter 'C3A$ b&t
have not activated it yet.
:pen a co##and pro#pt on 'C3A and ping the 'C3C I' address at 12.1*+.(.( on the R( 2A-. Are the
pings s&ccessf&lK ?hy or 5hy notK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
Step ,: 2stablish a .PN connection and login3
a. Choose the ne5ly created connection .PN6Corp and clic6 the Connect icon. Do& can also do&ble3
clic6 the connection entry.
b. ?hen the 1'- Client 9ser A&thentication dialog boG displays$ enter the &serna#e .PN;ser'
created previo&sly on the 1'- ro&ter R($ and enter the pass5ord of .PN;ser'pa--. Clic6 %> to
contin&e. %he 1'- Client 5indo5 #ini#i8es to a loc6 icon in the tools tray of the tas6bar. ?hen the
loc6 is closed$ the 1'- t&nnel is &p. ?hen it is open$ the 1'- connection is do5n.
Step -: Test access rom the client $ith the .PN connection3
?ith the 1'- connection fro# co#p&ter 'C3A to ro&ter R( activated$ open a co##and pro#pt on 'C3A
and ping the R( defa< gate5ay at 12.1*+.(.1. %hen ping the 'C3C I' address at 12.1*+.(.( on the R(
2A-. Are the pings s&ccessf&lK ?hy or 5hy notK
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age (1 of (2
CCNA Security
+outer Interace Summary Table
+outer Interace Summary
Ro&ter
Aodel
Ethernet Interface
M1
Ethernet Interface
M2
Serial Interface
M1
Serial Interface
M2
1+""
Fast Ethernet ")"
.Fa")"0
Fast Ethernet ")1
.Fa")10
Serial ")")"
.S")")"0
Serial ")")1
.S")")10
1""
Gigabit Ethernet ")"
.G")"0
Gigabit Ethernet ")1
.G")10
Serial ")")"
.S")")"0
Serial ")")1
.S")")10
2+""
Fast Ethernet ")"
.Fa")"0
Fast Ethernet ")1
.Fa")10
Serial ")")"
.S")")"0
Serial ")")1
.S")")10
2""
Gigabit Ethernet ")"
.G")"0
Gigabit Ethernet ")1
.G")10
Serial ")")"
.S")")"0
Serial ")")1
.S")")10
Note: %o find o&t ho5 the ro&ter is config&red$ loo6 at the interfaces to identify the type of ro&ter
and ho5 #any interfaces the ro&ter has. %here is no 5ay to effectively list all the co#binations of
config&rations for each ro&ter class. %his table incl&des identifiers for the possible co#binations of
Ethernet and Serial interfaces in the device. %he table does not incl&de any other type of interface$
even tho&gh a specific ro&ter #ay contain one. An eGa#ple of this #ight be an IS/- 4RI interface.
%he string in parenthesis is the legal abbreviation that can be &sed in Cisco I:S co##ands to
represent the interface.
All contents are Copyright 12!2"12 Cisco Syste#s$ Inc. All rights reserved. %his doc&#ent is Cisco '&blic Infor#ation. 'age (2 of (2
Vous aimerez peut-être aussi
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3D'EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Pas encore d'évaluation
- CCNASv1.1 Chp10 Lab-A ASA-FW-CLI StudentDocument24 pagesCCNASv1.1 Chp10 Lab-A ASA-FW-CLI StudentLan WanPas encore d'évaluation
- The Complete Guide to Getting Certified Cisco CCNA 200-301: Complete Your CCNA Exam Training and Preparation with 400 Exam Level Practice QuestionD'EverandThe Complete Guide to Getting Certified Cisco CCNA 200-301: Complete Your CCNA Exam Training and Preparation with 400 Exam Level Practice QuestionPas encore d'évaluation
- Ccnasv1.1 Chp03 Lab-A Aaa-Radius StudentDocument25 pagesCcnasv1.1 Chp03 Lab-A Aaa-Radius StudentAngel MendozaPas encore d'évaluation
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkD'EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkPas encore d'évaluation
- Chapter 3 Lab A: Securing Administrative Access Using AAA and RadiusDocument25 pagesChapter 3 Lab A: Securing Administrative Access Using AAA and RadiusfernaleoPas encore d'évaluation
- Cisco Packet Tracer Implementation: Building and Configuring Networks: 1, #1D'EverandCisco Packet Tracer Implementation: Building and Configuring Networks: 1, #1Pas encore d'évaluation
- Ccnasv1.1 Chp10 Lab-F Asa5510-Fw-Asdm InstructorDocument54 pagesCcnasv1.1 Chp10 Lab-F Asa5510-Fw-Asdm Instructormyropie100% (1)
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSDocument21 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSOsman SepulvedaPas encore d'évaluation
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSDocument21 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUSPauloPas encore d'évaluation
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS PDFDocument20 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS PDFLizSocaZevallos100% (1)
- CCNASv1.1 Chp08 Lab A Site2Site VPN InstructorDocument40 pagesCCNASv1.1 Chp08 Lab A Site2Site VPN Instructordotheanhdotramy0% (1)
- CCNA Security: Configuring Devices For Use With Cisco Configuration Professional (CCP) 2.5Document8 pagesCCNA Security: Configuring Devices For Use With Cisco Configuration Professional (CCP) 2.5vmtm7Pas encore d'évaluation
- Bundled Systems For Cisco Integrated Services Routers Generation 2Document14 pagesBundled Systems For Cisco Integrated Services Routers Generation 2Cassandra ShafferPas encore d'évaluation
- 4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsDocument15 pages4.4.1.2 Lab - Configuring Zone-Based Policy FirewallselizaPas encore d'évaluation
- CCNA Security 1.1 Laboratorios Instructor Part 2Document181 pagesCCNA Security 1.1 Laboratorios Instructor Part 2Ricardo Castro TenorioPas encore d'évaluation
- Sol ch14Document4 pagesSol ch14NickHenryPas encore d'évaluation
- Configuring Zone Based Policy FirewallsDocument13 pagesConfiguring Zone Based Policy FirewallsNorman Pal-og Madongit17% (6)
- Installing and Using RSLogix 5000 and RSLogix 500Document90 pagesInstalling and Using RSLogix 5000 and RSLogix 500fsakr2008Pas encore d'évaluation
- 5.4.1.1 Lab - Configure An Intrusion Prevention System (IPS) PDFDocument21 pages5.4.1.1 Lab - Configure An Intrusion Prevention System (IPS) PDFIvan ZuritaPas encore d'évaluation
- Lab 5.3.7 Configuring DHCP With SDM and The Cisco IOS CLIDocument15 pagesLab 5.3.7 Configuring DHCP With SDM and The Cisco IOS CLIArba SudiatmikaPas encore d'évaluation
- CCNASv1 1 Chp08 Lab B RMT Acc VPN Instructor PDFDocument33 pagesCCNASv1 1 Chp08 Lab B RMT Acc VPN Instructor PDFAhmadHijaziPas encore d'évaluation
- 11.3.1.2 Lab - CCNA Security ASA 5506-X Comprehensive - InstructorDocument66 pages11.3.1.2 Lab - CCNA Security ASA 5506-X Comprehensive - Instructorcheicktest1Pas encore d'évaluation
- 5.2.2.9 Lab - Configuring Switch Security FeaturesDocument10 pages5.2.2.9 Lab - Configuring Switch Security FeaturesShadman SifatPas encore d'évaluation
- Lab - Securing The Router For Administrative Access: Taller 2Document28 pagesLab - Securing The Router For Administrative Access: Taller 2murcielago189Pas encore d'évaluation
- CCNAS v1.1 Skills-Based Assessment Hands On AnswersDocument18 pagesCCNAS v1.1 Skills-Based Assessment Hands On AnswersAdelaide-City South Australia86% (14)
- 2.3.3.5 Lab - Configuring A Switch Management AddressDocument8 pages2.3.3.5 Lab - Configuring A Switch Management AddressNicolas Bonina33% (3)
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorDocument27 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorAlexander Lapo Cordova0% (1)
- Lab - Configuring A Site-to-Site VPN Using Cisco IOS and CCPDocument30 pagesLab - Configuring A Site-to-Site VPN Using Cisco IOS and CCPVasan Suryaßoyzz100% (1)
- 4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsDocument13 pages4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsADEL APas encore d'évaluation
- 8.7.1.2 Lab - Configuring A Remote Access VPN Server and Client - InstructorDocument37 pages8.7.1.2 Lab - Configuring A Remote Access VPN Server and Client - InstructorSalem TrabelsiPas encore d'évaluation
- CCNA 4 Chapter 9 v5 Exam Answers 2013Document6 pagesCCNA 4 Chapter 9 v5 Exam Answers 2013adrian743842Pas encore d'évaluation
- 3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorDocument35 pages3.6.1.1 Lab - Securing Administrative Access Using AAA and RADIUS - InstructorSalem TrabelsiPas encore d'évaluation
- Cisco Packet Tracer 6.0.1 Overview PresentationDocument37 pagesCisco Packet Tracer 6.0.1 Overview PresentationIzzat FauziPas encore d'évaluation
- Lab 05 - Configuring Zone-Based Policy FirewallsDocument18 pagesLab 05 - Configuring Zone-Based Policy FirewallsFernando MartinezPas encore d'évaluation
- Visibility - Acceleration - Security: Harri KurronenDocument31 pagesVisibility - Acceleration - Security: Harri KurronenGuy PoakaPas encore d'évaluation
- CIT2251 CCNA Security SyllabusDocument4 pagesCIT2251 CCNA Security SyllabusLaasyaSweetPas encore d'évaluation
- Ccnasv1.1 Chp10 Lab-E Asa5510-Fw-cli StudentDocument22 pagesCcnasv1.1 Chp10 Lab-E Asa5510-Fw-cli StudentHarrison HayesPas encore d'évaluation
- Lab 1 Configuring Basic Routing and SwitchingDocument12 pagesLab 1 Configuring Basic Routing and SwitchingratihwidyastutiPas encore d'évaluation
- EWAN Lab 2 5 3 InstructorDocument10 pagesEWAN Lab 2 5 3 InstructorshouldofduckedPas encore d'évaluation
- 4.4.1.2 Lab - Configuring Zone-Based Policy FirewallsDocument13 pages4.4.1.2 Lab - Configuring Zone-Based Policy Firewallscesar javierPas encore d'évaluation
- 11.3.1.2 Lab - CCNA Security ASA 5506-X ComprehensiveDocument19 pages11.3.1.2 Lab - CCNA Security ASA 5506-X ComprehensiveelizaPas encore d'évaluation
- Chapter 8 Lab B: Configuring A Remote Access VPN Server and ClientDocument24 pagesChapter 8 Lab B: Configuring A Remote Access VPN Server and ClientberlodonPas encore d'évaluation
- Ccnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 AmDocument35 pagesCcnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (2)
- Ccnasv1.1 Chp10 Lab D Asa Isr s2s VPN StudentDocument36 pagesCcnasv1.1 Chp10 Lab D Asa Isr s2s VPN Studentmuscle260% (1)
- Week 5 - Skills ActivityDocument11 pagesWeek 5 - Skills ActivitykonowePas encore d'évaluation
- 4.4.1.2 Lab - Configuring Zone-Based Policy Firewalls-ALDO PUGLIESEDocument21 pages4.4.1.2 Lab - Configuring Zone-Based Policy Firewalls-ALDO PUGLIESEsheckie jarabaPas encore d'évaluation
- 9.3.1.2 Lab - Configure ASA 5506-X Basic Settings and Firewall Using CLIDocument24 pages9.3.1.2 Lab - Configure ASA 5506-X Basic Settings and Firewall Using CLIeliza0% (1)
- 9.3.2.13 Lab - Configuring and Verifying Extended ACLsDocument8 pages9.3.2.13 Lab - Configuring and Verifying Extended ACLsAnonymous cW6o4f886% (14)
- 2.2.4.11 Lab - Configuring Switch Security Features - ILMDocument15 pages2.2.4.11 Lab - Configuring Switch Security Features - ILMJose Maria Rendon Rodriguez100% (1)
- ITNE2005LAB6-SecuringLocalAreaDocument27 pagesITNE2005LAB6-SecuringLocalArearitadhikarycsePas encore d'évaluation
- CCNA Exploration: Network Fundamentals CourseDocument1 pageCCNA Exploration: Network Fundamentals CourseJayme ProniPas encore d'évaluation
- 2.5.1.1 Lab - Securing The Router For Administrative Access - InstructorDocument61 pages2.5.1.1 Lab - Securing The Router For Administrative Access - InstructorLupita VázquezPas encore d'évaluation
- 1.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIDocument16 pages1.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIkashifPas encore d'évaluation
- ITNE2005LAB5-ConfigureanIntrusDocument20 pagesITNE2005LAB5-ConfigureanIntrusritadhikarycsePas encore d'évaluation
- 9.3.1.2 Lab - Configure ASA 5506-X Basic Settings and Firewall Using CLI - InstructorDocument39 pages9.3.1.2 Lab - Configure ASA 5506-X Basic Settings and Firewall Using CLI - InstructorCheickna warké CamaraPas encore d'évaluation
- 4.technical Infrastructure Requirements-2.1Document108 pages4.technical Infrastructure Requirements-2.1Arif MohammedPas encore d'évaluation
- ASA5506 9-3-1-2 Lab - Configure ASA Basic Settings and Firewall Using CLI - 1-26Document31 pagesASA5506 9-3-1-2 Lab - Configure ASA Basic Settings and Firewall Using CLI - 1-26Hoàng Dũng0% (1)
- 3.4.1.5 Lab - Troubleshooting Basic PPP With AuthenticationDocument8 pages3.4.1.5 Lab - Troubleshooting Basic PPP With AuthenticationLarry Abisaí17% (6)
- 9.3.2.13 Lab - Configuring and Verifying Extended ACLsDocument14 pages9.3.2.13 Lab - Configuring and Verifying Extended ACLsDerillioPas encore d'évaluation
- FreeRadius Cisco IOS and RadiusDocument7 pagesFreeRadius Cisco IOS and RadiusCarlos LimaPas encore d'évaluation
- PCS-9882n+ìETHERNET SWITCH 2010catalog-15Document2 pagesPCS-9882n+ìETHERNET SWITCH 2010catalog-15Rinda_RaynaPas encore d'évaluation
- Cisco Wireless Access Point Brochure PDFDocument6 pagesCisco Wireless Access Point Brochure PDFThi HaPas encore d'évaluation
- Gpon Onu - Optical Network Unit: Product DatasheetDocument6 pagesGpon Onu - Optical Network Unit: Product DatasheetFabio SilveiraPas encore d'évaluation
- HCIA-Access V2.5 Training MaterialDocument933 pagesHCIA-Access V2.5 Training MaterialSergio ZaletaPas encore d'évaluation
- 012 ClimatixIC GettingStarted enDocument28 pages012 ClimatixIC GettingStarted enramonmartinezcatalaPas encore d'évaluation
- GCSE (J277) Keywords For GcseDocument16 pagesGCSE (J277) Keywords For GcseEmma StevensPas encore d'évaluation
- Layer - Blog - How We Leverage IOS Push NotificationsDocument9 pagesLayer - Blog - How We Leverage IOS Push NotificationsneokrishPas encore d'évaluation
- TYCODocument3 pagesTYCOAdrian OprisanPas encore d'évaluation
- DEMO User Manualv1.4Document19 pagesDEMO User Manualv1.4Hector ChailePas encore d'évaluation
- DBS3900 IBS Commissioning Guide (V100R001C03 - 01) (PDF) - enDocument38 pagesDBS3900 IBS Commissioning Guide (V100R001C03 - 01) (PDF) - enKandasami SeeranganPas encore d'évaluation
- Deploying and Administering Microsoft Dynamics CRM OnlineDocument297 pagesDeploying and Administering Microsoft Dynamics CRM OnlinejelenaPas encore d'évaluation
- FTP in JavaDocument6 pagesFTP in JavaNivetha SundaresanPas encore d'évaluation
- 3Document23 pages3kinjaldivaPas encore d'évaluation
- TC4 V-Cycle and Tools - Rev13Document14 pagesTC4 V-Cycle and Tools - Rev13駱奎延Pas encore d'évaluation
- LogDocument24 pagesLogMarcos Chevez ArroyoPas encore d'évaluation
- Datasheet Copper SFPDocument5 pagesDatasheet Copper SFPaauniPas encore d'évaluation
- Mutual Exclusion in Distributed SystemDocument39 pagesMutual Exclusion in Distributed SystemChina Toon100% (1)
- Lab #2: Contention-Aware Scheduling To in Wireless NetworksDocument5 pagesLab #2: Contention-Aware Scheduling To in Wireless NetworksvsalaiselvamPas encore d'évaluation
- Cambium PTP 650 Series 01-43 System Release NotesDocument6 pagesCambium PTP 650 Series 01-43 System Release NotesAndres Pipe CasallasPas encore d'évaluation
- Lab 4.5.1 Observing TCP and UDP Using Netstat (Instructor Version)Document7 pagesLab 4.5.1 Observing TCP and UDP Using Netstat (Instructor Version)Rifqi Imaduddin IrfanPas encore d'évaluation
- ASR1000 Series Memory Allocation Between Linux and IOSd - TechZoneDocument3 pagesASR1000 Series Memory Allocation Between Linux and IOSd - TechZoneSaptarshi BhattacharjeePas encore d'évaluation
- Olt Zte Zxa10 c320 Linux SnippetsDocument6 pagesOlt Zte Zxa10 c320 Linux SnippetsJose YesmenPas encore d'évaluation
- HTB Cache Writeup UnlockedDocument7 pagesHTB Cache Writeup UnlockedJean PierrePas encore d'évaluation
- Bn81-22795e-580 em Osndvbadb Ad Eng 221111.0Document280 pagesBn81-22795e-580 em Osndvbadb Ad Eng 221111.0anchalfaltuPas encore d'évaluation
- Somfy - IP Scanning - How To Find Somfy Products On A NetworkDocument3 pagesSomfy - IP Scanning - How To Find Somfy Products On A NetworkAnta MasimmoPas encore d'évaluation
- 02 iPASO 400-1000 Introduction 2Document32 pages02 iPASO 400-1000 Introduction 2Wubie NegaPas encore d'évaluation
- Set Test ForDocument7 pagesSet Test ForSanjeev KumarPas encore d'évaluation
- Host Driver Logs CurrentDocument2 218 pagesHost Driver Logs CurrentGaluh iin FitriantikaPas encore d'évaluation
- ETSI Worshop - Huawei - Marcelo BrazaoDocument27 pagesETSI Worshop - Huawei - Marcelo BrazaoAbdullah N. DwairyPas encore d'évaluation
- Microsoft Certified Azure Fundamentals Study Guide: Exam AZ-900D'EverandMicrosoft Certified Azure Fundamentals Study Guide: Exam AZ-900Pas encore d'évaluation
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionD'EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionÉvaluation : 5 sur 5 étoiles5/5 (4)
- Microsoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsD'EverandMicrosoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsPas encore d'évaluation
- Unlock Any Roku Device: Watch Shows, TV, & Download AppsD'EverandUnlock Any Roku Device: Watch Shows, TV, & Download AppsPas encore d'évaluation
- PHP BLUEPRINT: An Essential Beginners Guide to Learn the Realms of PHP From A-ZD'EverandPHP BLUEPRINT: An Essential Beginners Guide to Learn the Realms of PHP From A-ZPas encore d'évaluation
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsD'EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsÉvaluation : 5 sur 5 étoiles5/5 (1)
- Cybersecurity: The Beginner's Guide: A comprehensive guide to getting started in cybersecurityD'EverandCybersecurity: The Beginner's Guide: A comprehensive guide to getting started in cybersecurityÉvaluation : 5 sur 5 étoiles5/5 (2)
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPND'EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNÉvaluation : 5 sur 5 étoiles5/5 (1)
- AWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamD'EverandAWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamPas encore d'évaluation
- Cybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringD'EverandCybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringÉvaluation : 5 sur 5 étoiles5/5 (40)
- Azure Networking: Command Line Mastery From Beginner To ArchitectD'EverandAzure Networking: Command Line Mastery From Beginner To ArchitectPas encore d'évaluation
- Networking Fundamentals: Develop the networking skills required to pass the Microsoft MTA Networking Fundamentals Exam 98-366D'EverandNetworking Fundamentals: Develop the networking skills required to pass the Microsoft MTA Networking Fundamentals Exam 98-366Pas encore d'évaluation
- Hacking Network Protocols: Complete Guide about Hacking, Scripting and Security of Computer Systems and Networks.D'EverandHacking Network Protocols: Complete Guide about Hacking, Scripting and Security of Computer Systems and Networks.Évaluation : 5 sur 5 étoiles5/5 (2)
- Hacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxD'EverandHacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxÉvaluation : 4.5 sur 5 étoiles4.5/5 (67)
- AWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamD'EverandAWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamÉvaluation : 5 sur 5 étoiles5/5 (1)
- Alcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast ExamsD'EverandAlcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast ExamsPas encore d'évaluation
- Open Radio Access Network (O-RAN) Systems Architecture and DesignD'EverandOpen Radio Access Network (O-RAN) Systems Architecture and DesignPas encore d'évaluation
- ITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationD'EverandITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationÉvaluation : 5 sur 5 étoiles5/5 (2)