Académique Documents
Professionnel Documents
Culture Documents
Congestion Control Algorithms
Transféré par
Ami VermaCopyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Congestion Control Algorithms
Transféré par
Ami VermaDroits d'auteur :
Formats disponibles
Congestion control algorithms
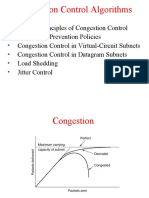
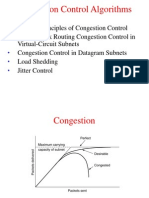
Congestion is a situation in which too many packets are present in (a part of) the subnet,
performance degrades. The symptom is depicted in Fig .
Figure: When too much traffic is offered, congestion sets in and performance degrades
sharply.
Factors causing congestion:
The input traffic rate exceeds the capacity of the output lines.
The routers are too slow to perform bookkeeping tasks (ueueing buffers,
updating tables, etc.).
The routers! buffer is too limited.
"dding more memory may help up to a point, but if routers ha#e an infinite amount of
memory, congestion gets worse. (Why $ %elay timeout retransmission more traffic
load).
Congestion control is different from flow control&
Congestion is a global issue, in#ol#ing the beha#ior of all the hosts, all the
routers, the store'and'forward processing within the routers, etc.
Flow control relates to the point'to'point traffic between a gi#en sender and a
gi#en recei#er.
" situation reuiring flow control& a fiber optic network with a capacity of ()))
gigabits*sec on which a supercomputer was trying to transfer a file to a personal
computer at (+bps.
" situation reuiring congestion control& a store'and'forward network with (',bps lines
and ())) large minicomputers, half of which were trying to transfer files at ()) kbps to
the other half.
5.3.1. General principles of congestion control
From a control theory point of #iew, all solutions to problems in complex systems , such
as computer networks, can be di#ided into two groups&
Open loop solutions sol#e the problem by good design, in essence, to make sure
the problem does not occur in the first place.
Tools include deciding when to accept new traffic, when to discard packets and
which ones, and how to schedule packets at #arious points in the network.
" common fact& they make
decisions without regard to
the current state of the network.
Closed loop solutions are based on the concept of a feedback loop, which consists
of the following three parts&
(. ,onitor the system to detect when and where congestion occurs.
-. .ass this information to places where actions can be taken.
/. "d0ust system operation to correct the problem.
Chief metrics for monitoring the subnet for congestion are&
the percentage of all packets discarded for lack of buffer space,
the a#erage ueue lengths,
the number of packets that time out and are retransmitted,
the a#erage packet delay, and
the standard de#iation of packet delay.
1ow to propagate the monitored congestion information $
The router detecting the congestion sends a separate warning packet to the traffic
source.
" bit or field can be reser#ed in each packet. When a router detects a congested
state, it fills in the field in all outgoing packets to warn the neighbors.
1osts or routers send probe packets out periodically to explicitly ask about
congestion and to route traffic around problem areas.
1ow to correct the congestion problem $
2ncrease the resource&
o 3sing an additional line to temporarily increase the bandwidth between
certain points.
o 4plitting traffic o#er multiple routes.
o 3sing spare routers.
%ecrease the load&
o denying ser#ice to some users,
o degrading ser#ice to some or all users, and
o ha#ing users schedule their demands in a more predictable way.
The open loop congestion control approach tries to achie#e the goal by using appropriate
policies at #arious le#els, as shown in Fig.
Figure: .olicies that affect congestion.
The leaky bucket algorithm
(a) " leaky bucket with water. (b) a leaky bucket with packets.
The token bucket algorithm
The leaky bucket algorithm enforces a rigid output pattern at the a#erage rate, no matter
how bursty the traffic is.
For many applications, it is better to allow the output to speed up somewhat when large
bursts arri#e, so a more flexible algorithm is needed, preferably on that ne#er loses data.
The bucket holds tokens, generated by a clock at the rate of one token e#ery sec.
For a packet to be transmitted, it must capture and destroy one token.
The token bucket algorithm allows sa#ing up to the maximum si5e of the bucket, ,
which means that bursts of up to packets can be sent at the maximum speed (for a
certain period of time).
Token bucket
" token bucket is a common algorithm used to control the amount
of data that is in0ected into a network, allowing for bursts of data to
be sent. "lthough it has se#eral uses, it is best understood in the
context of network traffic shaping or rate limiting.
The token bucket is a control mechanism that dictates when traffic can be
transmitted, based on the presence of tokens in the bucket''an abstract
container that holds aggregate network traffic to be transmitted. The bucket
contains tokens, each of which can represent a unit of bytes or a single packet
of predetermined si5e. Tokens in the bucket are remo#ed (6cashed in6) for the
ability to send a packet. The network administrator specifies how many
tokens are needed to transmit how many bytes. When tokens are present, a
flow is allowed to transmit traffic. 2f there are no tokens in the bucket, a flow
cannot transmit its packets. Therefore, a flow can transmit traffic up to its
peak burst rate if there are adeuate tokens in the bucket and if the burst
threshold is configured appropriately.
Vous aimerez peut-être aussi
- Online Class 14 Congestion ControlDocument17 pagesOnline Class 14 Congestion ControlAshPas encore d'évaluation
- CN Unit 3 Part 2Document26 pagesCN Unit 3 Part 2Himanshu DubeyPas encore d'évaluation
- Congestion in Computer NetworkDocument10 pagesCongestion in Computer Network1DA19CS111 PrajathPas encore d'évaluation
- Congestion Control in Computer NetworksDocument4 pagesCongestion Control in Computer NetworksGarima MaharjanPas encore d'évaluation
- Session22 (Quality of Service)Document25 pagesSession22 (Quality of Service)Dummy HackerPas encore d'évaluation
- Presentation On: Congestion in NetworkDocument16 pagesPresentation On: Congestion in NetworkAnjilaPas encore d'évaluation
- Congestion Control: Factors That Cause CongestionDocument5 pagesCongestion Control: Factors That Cause CongestionSonu GuptaPas encore d'évaluation
- Transport Layer Protocols: 2. Congestion Control and QosDocument35 pagesTransport Layer Protocols: 2. Congestion Control and Qosmm_sharma71Pas encore d'évaluation
- QuestionsDocument34 pagesQuestionssujeen killaPas encore d'évaluation
- CN - Unit3.3Document30 pagesCN - Unit3.3Kanika TyagiPas encore d'évaluation
- 05 U5 KKP FCN NetworkLayer (RoutingAlgorithms)Document59 pages05 U5 KKP FCN NetworkLayer (RoutingAlgorithms)romitPas encore d'évaluation
- Congestion Control AlgorithmsDocument33 pagesCongestion Control AlgorithmsRajaram PandianPas encore d'évaluation
- 13-CongestioninDataNetworks REALDocument36 pages13-CongestioninDataNetworks REALmemo1023Pas encore d'évaluation
- Cat3 DCN Group-1Document14 pagesCat3 DCN Group-1HARSH CHAUHAN 20SCSE1010094Pas encore d'évaluation
- CN - Unit3.3 PDFDocument30 pagesCN - Unit3.3 PDFKanika TyagiPas encore d'évaluation
- Using Fuzzy Logic Control To Provide Intelligent Traffic Management Service For High-Speed NetworksDocument9 pagesUsing Fuzzy Logic Control To Provide Intelligent Traffic Management Service For High-Speed NetworksanraomcaPas encore d'évaluation
- Networking Asignment Outcome 3Document10 pagesNetworking Asignment Outcome 3Chamoadh DissanayakePas encore d'évaluation
- Congestion ControlDocument15 pagesCongestion ControlVivek BhattPas encore d'évaluation
- NetworkingDocument8 pagesNetworkingSouvik DebnathPas encore d'évaluation
- Congestion Control AlgorithmsDocument42 pagesCongestion Control AlgorithmsSatish NaiduPas encore d'évaluation
- Leaky Bucket Algorithm: 171FA04014 171FA04042 171FA04276Document22 pagesLeaky Bucket Algorithm: 171FA04014 171FA04042 171FA04276Pradeep reddy JonnalaPas encore d'évaluation
- The Network Layer: Congestion Control Algorithms & Quality-of-ServiceDocument36 pagesThe Network Layer: Congestion Control Algorithms & Quality-of-ServiceSai RangaPas encore d'évaluation
- Combined To Many Logics: Iii. ImplementationDocument4 pagesCombined To Many Logics: Iii. ImplementationNandkishore PatilPas encore d'évaluation
- Leaky BucketDocument4 pagesLeaky BucketRanjith ChandrashekarPas encore d'évaluation
- Techniques To Improve QosDocument13 pagesTechniques To Improve QosArun Kumar Singh100% (1)
- Unit 5C - TL - Congestion Control - All TypesDocument25 pagesUnit 5C - TL - Congestion Control - All TypesshenoykunaltanPas encore d'évaluation
- Chapter 3.1.3Document20 pagesChapter 3.1.3Harsh Vardhan kaushikPas encore d'évaluation
- Techniques To Improve QoSDocument10 pagesTechniques To Improve QoSNITESHWAR BHARDWAJPas encore d'évaluation
- "Congestion Control": Antrang Arora 21MCA0121Document5 pages"Congestion Control": Antrang Arora 21MCA0121Antrang AroraPas encore d'évaluation
- TRFCCTRL QoSDocument46 pagesTRFCCTRL QoSRohan NathiPas encore d'évaluation
- Unit-3 PART-C Congestion Control AlgorithmsDocument12 pagesUnit-3 PART-C Congestion Control AlgorithmsAkhila VeerabommalaPas encore d'évaluation
- COngestion COntrolDocument32 pagesCOngestion COntrolRANGAM NAGARAJUPas encore d'évaluation
- Ec8551-Communication Networks Topic: Qos: Prepared by J.L.LakshmiDocument43 pagesEc8551-Communication Networks Topic: Qos: Prepared by J.L.LakshmilakshmiPas encore d'évaluation
- CH 5 Network Layer CongestionDocument42 pagesCH 5 Network Layer CongestionDaryl ShaverPas encore d'évaluation
- Notes On Computer Networks Unit 3Document13 pagesNotes On Computer Networks Unit 3Rohit Chaudhary83% (6)
- 4-Network Layer-1Document133 pages4-Network Layer-1cepifav400Pas encore d'évaluation
- 11 Routing AlgorithmsDocument13 pages11 Routing AlgorithmsRahul AryanPas encore d'évaluation
- Destination, Computes The Delay and Sends A Backward: Iv Snapshots SourceDocument4 pagesDestination, Computes The Delay and Sends A Backward: Iv Snapshots SourceNandkishore PatilPas encore d'évaluation
- Lec 23Document7 pagesLec 23Lewis IssacPas encore d'évaluation
- Cas Cs 835: Qos Networking SeminarDocument27 pagesCas Cs 835: Qos Networking SeminarUrvarshi GhoshPas encore d'évaluation
- Main Paper PDFDocument5 pagesMain Paper PDFSiva Prasad GottumukkalaPas encore d'évaluation
- CongestionDocument5 pagesCongestionAnjali MohiniPas encore d'évaluation
- Quality of Services: Presented by Saurabh BatraDocument16 pagesQuality of Services: Presented by Saurabh BatraSaurabh BatraPas encore d'évaluation
- Leaky BucketDocument19 pagesLeaky BucketIzharPas encore d'évaluation
- Data Link Control: B. R. Chandavarkar CSE Dept., NITK SurathkalDocument37 pagesData Link Control: B. R. Chandavarkar CSE Dept., NITK SurathkalSoham Raje PatilPas encore d'évaluation
- 12 Troubleshooting in Full-Fiber Access ScenariosDocument71 pages12 Troubleshooting in Full-Fiber Access ScenariosAbel PerezPas encore d'évaluation
- Ethernet SwitchingDocument11 pagesEthernet SwitchingShahzaibAshrafPas encore d'évaluation
- TCP - Congestion Control Algorithm For Enhancing High-Speed NetworksDocument5 pagesTCP - Congestion Control Algorithm For Enhancing High-Speed NetworksJournal of Computer ApplicationsPas encore d'évaluation
- Host-To-Host Congestion Control For TCPDocument9 pagesHost-To-Host Congestion Control For TCPSantosh RaiPas encore d'évaluation
- Quality of ServicesDocument22 pagesQuality of Servicesavantika bishtPas encore d'évaluation
- SChapter5 5.3 5.5CongestionQualityService 04Document17 pagesSChapter5 5.3 5.5CongestionQualityService 04KunaljitPas encore d'évaluation
- Congestion in Data NetworksDocument11 pagesCongestion in Data NetworksMiM1990Pas encore d'évaluation
- Transport Layer Notes Module 3Document10 pagesTransport Layer Notes Module 3amukhopadhyayPas encore d'évaluation
- Arp: Address Resolution Protocols: H?V Cn8Zxh9BpioDocument17 pagesArp: Address Resolution Protocols: H?V Cn8Zxh9BpiofrtessPas encore d'évaluation
- Securing Data in Communication NetworksDocument3 pagesSecuring Data in Communication NetworksJournal of Computer ApplicationsPas encore d'évaluation
- CONGESTIONDocument29 pagesCONGESTIONEstelle MandengPas encore d'évaluation
- Lecture 3 - 3 Evaluating Static Interconnection NetworksDocument41 pagesLecture 3 - 3 Evaluating Static Interconnection NetworkswmanjonjoPas encore d'évaluation
- DCN Unit-VDocument99 pagesDCN Unit-VRohan SaiPas encore d'évaluation
- Using Fuzzy Logic Control To Provide Intelligent Traffic Management Service For High Speed NetworksDocument4 pagesUsing Fuzzy Logic Control To Provide Intelligent Traffic Management Service For High Speed NetworksNandkishore PatilPas encore d'évaluation
- Android Application DevelopmentDocument32 pagesAndroid Application DevelopmentAmi VermaPas encore d'évaluation
- Access SchoolDocument3 pagesAccess SchoolAmi VermaPas encore d'évaluation
- Database Using MS AccessDocument2 pagesDatabase Using MS AccessAmi VermaPas encore d'évaluation
- Microsoft Access AssignmentDocument3 pagesMicrosoft Access AssignmentAmi Verma100% (1)
- Introduction To Marketing ManagementDocument45 pagesIntroduction To Marketing ManagementAmi VermaPas encore d'évaluation
- Error - Detection and Correction CodesDocument7 pagesError - Detection and Correction CodesAmi VermaPas encore d'évaluation
- About The Conference About PIMTDocument4 pagesAbout The Conference About PIMTAmi VermaPas encore d'évaluation
- SQUID On CentOS 6.7Document6 pagesSQUID On CentOS 6.7jpgonzalezjPas encore d'évaluation
- ADSL Modem User and PasswordDocument47 pagesADSL Modem User and PasswordHamid Reza BarzegarPas encore d'évaluation
- CCNA 1 v7 Modules 1 - 3 - Basic Network Connectivity and Communications Exam AnswersDocument36 pagesCCNA 1 v7 Modules 1 - 3 - Basic Network Connectivity and Communications Exam AnswersMAISA REIS ARAUJOPas encore d'évaluation
- Cisco IOS Mobile Wireless Gateway GPRS Support Node Configuration Guide, Release 12.4Document338 pagesCisco IOS Mobile Wireless Gateway GPRS Support Node Configuration Guide, Release 12.4karimjiwaniPas encore d'évaluation
- DS SG-9000Document5 pagesDS SG-9000Chatpoom PaitoonPas encore d'évaluation
- NM PDFDocument62 pagesNM PDFWWE ROCKERSPas encore d'évaluation
- How Communication Works in Real-Time ProjectsDocument131 pagesHow Communication Works in Real-Time ProjectsKrishna OodhorahPas encore d'évaluation
- Actatek Training Manual: Nov 8, 2006 Hectrix LimitedDocument101 pagesActatek Training Manual: Nov 8, 2006 Hectrix LimitedEmir KunalićPas encore d'évaluation
- Mpls VPN Pe-Ce Ospf Default RouteDocument8 pagesMpls VPN Pe-Ce Ospf Default RouteEmad MohamedPas encore d'évaluation
- FBN 16-09 (2P)Document2 pagesFBN 16-09 (2P)TariqPas encore d'évaluation
- Da 1646219337072.Document2 pagesDa 1646219337072.dhisny giovannyPas encore d'évaluation
- Provides Update Free of Charge in One Year!: Dump StepDocument6 pagesProvides Update Free of Charge in One Year!: Dump StepPaulo DembiPas encore d'évaluation
- Radio Link TimeoutDocument3 pagesRadio Link TimeoutYe Yesus LijPas encore d'évaluation
- 2 Services and Ports: Product Specific Attributes Hipath HG 1500 V7Document14 pages2 Services and Ports: Product Specific Attributes Hipath HG 1500 V7Richard KxorrolokoPas encore d'évaluation
- Chapter 3Document22 pagesChapter 3dennis tanPas encore d'évaluation
- NHL-2342N Datasheet VolktekDocument3 pagesNHL-2342N Datasheet VolktekeravadheshPas encore d'évaluation
- 2009-12-10 LTESecurityTutorial PDFDocument55 pages2009-12-10 LTESecurityTutorial PDFGokulraj PandiyanPas encore d'évaluation
- Module-4 RaspberryPiDocument23 pagesModule-4 RaspberryPiRajesh PandaPas encore d'évaluation
- 2.2.2.4 Packet Tracer - Configuring IPv4 Static and Default Routes InstructionsDocument4 pages2.2.2.4 Packet Tracer - Configuring IPv4 Static and Default Routes InstructionsResty AnnisaPas encore d'évaluation
- Cs601-Quiz 1Document8 pagesCs601-Quiz 1Sara MehmoodPas encore d'évaluation
- V1 - 7750 SR-7 Installation Guide PDFDocument162 pagesV1 - 7750 SR-7 Installation Guide PDFPedritoCCNPPas encore d'évaluation
- Lte CV Engineer PDFDocument4 pagesLte CV Engineer PDFSABER1980Pas encore d'évaluation
- Fortigate Transparent Mode 56Document49 pagesFortigate Transparent Mode 56Log BwdPas encore d'évaluation
- R 6Document4 pagesR 6mohammadPas encore d'évaluation
- C3871Document5 pagesC3871ghiulaivPas encore d'évaluation
- WhereLan III Datasheet (LOS)Document2 pagesWhereLan III Datasheet (LOS)joker8832Pas encore d'évaluation
- CommblksDocument583 pagesCommblksgvirbila1298Pas encore d'évaluation
- Digital and Data CommunicationsDocument7 pagesDigital and Data CommunicationsyaelfabulousPas encore d'évaluation
- How To - Add Active or Backup Gateway For Load Balancing and Gateway FailoverDocument5 pagesHow To - Add Active or Backup Gateway For Load Balancing and Gateway Failoverbirungi jeromePas encore d'évaluation
- GH - CP443 1 Adv GX30 - 76 PDFDocument112 pagesGH - CP443 1 Adv GX30 - 76 PDFjcadvPas encore d'évaluation
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsD'EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsÉvaluation : 5 sur 5 étoiles5/5 (1)
- Hacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxD'EverandHacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxÉvaluation : 4.5 sur 5 étoiles4.5/5 (67)
- Microsoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsD'EverandMicrosoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsPas encore d'évaluation
- Cybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringD'EverandCybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringÉvaluation : 5 sur 5 étoiles5/5 (40)
- AWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamD'EverandAWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamPas encore d'évaluation
- Microsoft Certified Azure Fundamentals Study Guide: Exam AZ-900D'EverandMicrosoft Certified Azure Fundamentals Study Guide: Exam AZ-900Pas encore d'évaluation
- Open Radio Access Network (O-RAN) Systems Architecture and DesignD'EverandOpen Radio Access Network (O-RAN) Systems Architecture and DesignPas encore d'évaluation
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionD'EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionÉvaluation : 5 sur 5 étoiles5/5 (4)
- Cybersecurity: The Beginner's Guide: A comprehensive guide to getting started in cybersecurityD'EverandCybersecurity: The Beginner's Guide: A comprehensive guide to getting started in cybersecurityÉvaluation : 5 sur 5 étoiles5/5 (2)
- ITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationD'EverandITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationÉvaluation : 5 sur 5 étoiles5/5 (2)
- Palo Alto Networks: The Ultimate Guide To Quickly Pass All The Exams And Getting Certified. Real Practice Test With Detailed Screenshots, Answers And ExplanationsD'EverandPalo Alto Networks: The Ultimate Guide To Quickly Pass All The Exams And Getting Certified. Real Practice Test With Detailed Screenshots, Answers And ExplanationsPas encore d'évaluation
- Azure Networking: Command Line Mastery From Beginner To ArchitectD'EverandAzure Networking: Command Line Mastery From Beginner To ArchitectPas encore d'évaluation
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPND'EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNÉvaluation : 5 sur 5 étoiles5/5 (1)
- ITIL 4 : Drive Stakeholder Value: Reference and study guideD'EverandITIL 4 : Drive Stakeholder Value: Reference and study guidePas encore d'évaluation
- Digital Health: Mobile and Wearable Devices for Participatory Health ApplicationsD'EverandDigital Health: Mobile and Wearable Devices for Participatory Health ApplicationsShabbir Syed-AbdulPas encore d'évaluation
- AWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamD'EverandAWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamÉvaluation : 5 sur 5 étoiles5/5 (1)