Académique Documents
Professionnel Documents
Culture Documents
IPC
Transféré par
SudhakarMishraDescription originale:
Titre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
IPC
Transféré par
SudhakarMishraDroits d'auteur :
Formats disponibles
1
1.INTRODUCTION
Crime in any form adversely affects all the members of the society. In developing economies,
cyber crime has increased at rapid strides, due to the rapid diffusion of the Internet and the
digitalization of economic activities. Thanks to the huge penetration of technology in almost
all walks of society right from corporate governance and state administration, up to the lowest
level of petty shop keepers computerizing their billing system, we find computers and other
electronic devices pervading the human life. The penetration is so deep that man cannot
spend a day without computers or a mobile. Snatching some ones mobile will tantamount to
dumping one in solitary confinement.1
The Second industrial revolution, as it is often called, the internet and network computers
have posed the biggest ever challenge to the legal systems all over the world. Paperless
contracts, digital signatures, online transactions and cybercrimes have taken the legal world
by surprise.2
The very nature of crime itself has undergone complete transformation. There is a conceptual
shift in terms of the costs of criminal behavior and the forms of criminality, which merits
state attention. The globalization of the worlds economy and the resultant exponential
growth in the way business is carried out has given rise to a new wave of crime, which
requires more attention than traditional forms of violent crimes that currently command the
vast share of state law enforcement resources. Territory is no longer the barrier, as it may also
exist in cyberspace, where corporations, which serve computer and telecommunication
networks also control access. The capacity of criminals has been enhanced to perpetrate
serious offences manifolds due to progress in computer and communications technologies
and that too with a greatly diminished risk of apprehension. The defense mechanisms of
states appear fragile when it comes to advanced technology, telecommunication and
cyberspace. The concept of jurisdiction becomes meaningless when an individual has only an
address on a computer network as identity.3 Cyber world is the world without specific
boundaries.
1 Cyber laws in India, available at http://www.iibf.org.in/documents/Cyber-Laws-chapter-inLegal-Aspects-Book.pdf.
2 Talat Fatima, Cyber Crimes p.51, Eastern Book Company (1st ed, 2011).
3 Dr. Amita Verma, Cyber Crimes and Law, p.32, Central Law Publivations(1st ed, 2009).
1
Although the computer world may exist only in intangible form, it affects the physical and
real environment. The shift of crime to intangibles has a staggering impact on society, both
socially and economically. Never before in the history of mankind has science been so cruel
to the legal world.4
With the advent of the internet, cyberlaw has become an emerging field. Cyberlaw
encompasses electronic commerce, freedom of expression, intellectual property rights,
jurisdiction and choice of law, and privacy rights. There have been various kinds of
computers and internet related crimes. In fact, the growth of crime on the internet is directly
proportional to the growth of the internet itself, and so is the variety of crimes being
committed or attempted.5
Computer technology is the major integral part of everyday human life, and it is growing
rapidly, as are computer crimes such as financial fraud, unauthorized intrusion, identity theft
and intellectual theft. To counteract those computer-related crimes, Computer Forensics plays
a very important role. Computer Forensics involves obtaining and analysing digital
information for use as evidence in civil, criminal or administrative cases.6
Cyber forensics is an upcoming field in India and Indian legal and judicial system has to
adapt itself according to the same. Till now cyber forensics is not widely and appropriately
used by the law enforcement agencies, lawyers, judges, etc in India. As a result most of the
cyber criminals are either not prosecuted at all or they are acquitted in the absence of
adequate evidence.7
4 Talat Fatima, Cyber Crimes, p.53, Eastern Book Company (1st ed, 2011).
5 Dr. Amita Verma, Cyber Crimes and Law, p.32-33, Central Law Publivations(1st ed, 2009).
6
Computer
Forensics
Investigation
Case
Study,
available
at
http://resources.infosecinstitute.com/computer-forensics-investigation-case-study/.
7 Cyber Forensics Trends And Developments In India 2014-Part 1(June 24, 2014), available
at http://computerforensicsinindia.blogspot.jp/.
In the following chapters we will try to understand the Indian law regarding cyber crime and
analyze how cyber forensics has been used by law enforcement agencies, whether it is
appropriately used or not.
2.Cyber Crime and the Information Technology Act, 2000
Nobody had anticipated that one day development of internet, a great opportunity of
communication and data transfer could also become a curse for the mankind in a number of
ways and internet could be misused for criminal activities.
The general assembly of the United Nations by resolution number A/RES/51/162 dated 30 th
January 1997 has adopted the model law on electronic commerce regarding electronic mail,
data interchange, internet etc. to adopt uniform, international, adequate and effective law.
According to the United Nations Model (UNCITRAL) law, there must be equal legal
treatments for users of electronic communication and paper based manual communication.
Internet pedophilia, cyber defamation, cyber pornography, computer network break-ins,
industrial espionage, child password sniffing, spoofing, telecommunications fraud, software
piracy, email bombing, spamming, phishing, the availability of illicit or unlicensed products
and services are offences in the cyberspace. Emerging problems include credit card fraud,
cyber terrorism, cyber hacking, cyber laundering, child pornography in cyberspace, and
criminal use of secure internet communications. The huge growth of internet will breed cyber
fraud especially in the area of share holdings of companies.8
Cyber world is the combination of computers and other communication convergence
technologies. It raises complex problems for traditional laws. Traditional laws are to be
applied in super highway with new spectacle. But these laws are not adequate in cyberspace
8 Dr. M. Dasgupta, Cyber Crime in India,p.3, Eastern Law House(2009)
always.9 Cyber crime is the deadliest epidemic confronting our planet in this millennium.
Realizing the potentials of cyber crimes mentioned in second paragraph, laws are being
formulated and security agencies are being trained and equipped to handle such cases in
many countries.
India has taken the lead in this sphere. It is after all, one of the few countries to enact a law
fully meant for cybercrime viz. Information Technology(IT) Act 2000. Although the
magnitude of cyber crime in India is, nowhere near the developed world, but it has the
potential of becoming rampant and rise to shocking levels. The UNCITRAL, i.e. the United
Nations Commission on International Trade Law adopted the Model Law of electronic
commerce in 1996. It was followed by the General Assembly of United Nations
recommending that all states should give favourable considerations to the State Model Law,
when they enact or revise their laws, by its resolution No.51/162, dated 30 th January, 1997. In
discharge of its international responsibility, Government of India also recognized the need to
legislate and came out with the Information Technology Act 2000. It recognized the equal
treatment of users of electronic communication and paper based communication urgently
needed. The new legislation, therefore, provides for legal recognition of electronic records
and digital signatures and to enable the conclusion of contracts and the creation of rights and
obligations through the electronic media. It also provides for regulatory regime to supervise
the Certifying Authorities, issuing digital signature certificates and to prevent the possible
issues arising out of transactions and other dealings concluded through the electronic media
and to create civil and criminal liabilities for contravention of the provisions of the Act. 10 The
above Act was further amended in the form of IT Amendment Act, 2008. This act has also
made amendments to the Indian Penal Code 1860, Indian Evidence Act 1872, The Bankers
Books of Evidence Act 1891, and the Reserve Bank of India Act 1934 in order to tackle the
problems arising out of cyberspace more effectively.
9 Ibid,p.1.
10 Dr. Amita Verma, Cyber Crimes and Law, p.392-393, Central Law Publivations(1st ed,
2009).
The scope and applicability of ITA-2000 was increased by its amendment in 2008. The word
'communication devices' was inserted having an inclusive definition, taking into its coverage
cell phones, personal digital assistance or such other devices used to transmit any text, video
etc. like what was later being marketed as iPad or other similar devices on Wi-fi and cellular
models. Though ITA- 2000 defined 'digital signature', however said definition was incapable
to cater needs of hour and therefore the term 'Electronic signature' was introduced and
defined in the ITAA -2008 as a legally valid mode of executing signatures. This includes
digital signatures as one of the modes of signatures and is far broader in ambit covering
biometrics and other new forms of creating electronic signatures not confining the
recognition to digital signature process alone.11
The new amendment has replaced Section 43 with Section 66. The Word "hacking" used in
Section 66 of earlier Act has been removed and named as "data theft" in this section and has
further been widened in the form of Sections 66A to 66F. The section covers the offences
such as the sending of offensive messages through communication service, misleading the
recipient of the origin of such messages, dishonestly receiving stolen computers or other
communication device, stealing electronic signature or identity such as using another persons'
password or electronic signature, cheating by personation through computer resource or a
communication device, publicly publishing the information about any person's location
without prior permission or consent, cyber terrorism, the acts of access to a commuter
resource without authorization, such acts which can lead to any injury to any person or result
in damage or destruction of any property, while trying to contaminate the computer through
any virus like Trojan etc. The offences covered under section 66 are cognizable and nonbailable. Whereas, the consequence of Section 43 of earlier Act were Civil in nature having
its remedy in the form of damages and compensation only, but under Section 66 of the
11 Rohit K. Gupta, India: An Overview Of Cyber Laws vs. Cyber Crimes: In Indian
Perspective,
(12th
Aug.2013),
availablehttp://www.mondaq.com/india/x/257328/Data+Protection+Privacy/An+Overview+O
f+Cyber+Laws+vs+Cyber+Crimes+In+Indian+Perspective.
Amendment Act, if such act is done with criminal intention that is mens rea, then it will
attract criminal liability having remedy in imprisonment or fine or both.12
Moreover, under Sections 71, 72, 73 of the Information Technology Act 2000 some acts or
omissions have been made criminally liable with strict liability e.g. Penalty for breach of
confidentiality and privacy, penalty for misrepresentation etc. Section 67 of the original Act
dealt with publishing or transmitting obscene material in electronic form but the scope of this
section was widened by the amendment which included child pornography under section 67B and also the act of retention of records by the intermediaries. And such offences under
section 67-A will be punished with conviction of a term up to 3 years and fine of Rs.5 lakh
and in case it is the second conviction then conviction will be for five years and fine of Rs.10
Lack or both. But for offence under section 67-B the provision is for stricter conviction which
is for 5 years and fine of Rs. 10 Lakh or both in case of first conviction, and the same will be
increased to 7 years and fine of Rs. 10 lakh in case of second conviction.13
The contravention of any rule, regulation, direction or order made thereunder by a person
which renders him liable to pay penalty or compensation under the IT Act, are adjudicated
upon by an officer appointed by the Central Government. The adjudicating officer appointed
under the IT Act shall have all the powers of a civil court which are conferred on the Cyber
Appellate Tribunal (CAT) under section 58(2) and also all powers which are envisaged in the
amended Section 46(5).14
Even though this piece of legislation has proved to be a big leap in the field of cyber crimes,
there still is a need for further changes which can improve its efficacy such as there is lack of
effective mechanism for the appropriate retention of electronic evidence.15 As country
develops into a more robust economy and use of computers becomes ubiquitous, it is
imperative that our laws are updated to respond to changing scenario. Quite unlike other
12 Ibid.
13
Cyber
Crimes
in
India
an
Introduction,
available
http://www.vakilno1.com/legalviews/cyber-crimes-in-india.html.
14 Talat Fatima, Cyber Crimes, p.472-473, Eastern Book Company (1st ed. 2011).
at
penal laws IT Act in particular needs revision and reviews much more regularly mainly due to
rapid changes in use of Information Technology.
15
Cyber
Crimes
in
India
an
Introduction,
http://www.vakilno1.com/legalviews/cyber-crimes-in-india.html.
available
at
Vous aimerez peut-être aussi
- Cybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringD'EverandCybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringÉvaluation : 5 sur 5 étoiles5/5 (40)
- Directory Submit: Url Site StatusDocument17 pagesDirectory Submit: Url Site StatusduttbhavikPas encore d'évaluation
- Cyber Crime in Bangladesh The Problems and Prospects of Current Regulatory RegimeDocument60 pagesCyber Crime in Bangladesh The Problems and Prospects of Current Regulatory Regimemd khanPas encore d'évaluation
- Cyberspace and Jurisdiction Final PaperDocument15 pagesCyberspace and Jurisdiction Final PaperjaishreePas encore d'évaluation
- SECURITY AND PRIVACY IN AN IT WORLD: Managing and Meeting Online Regulatory Compliance in the 21st CenturyD'EverandSECURITY AND PRIVACY IN AN IT WORLD: Managing and Meeting Online Regulatory Compliance in the 21st CenturyÉvaluation : 5 sur 5 étoiles5/5 (1)
- Can we make the Digital World ethical?: A report exploring the dark side of the Internet of Things and Big DataD'EverandCan we make the Digital World ethical?: A report exploring the dark side of the Internet of Things and Big DataPas encore d'évaluation
- 08 - Chapter 2Document107 pages08 - Chapter 2Priya PandeyPas encore d'évaluation
- Cyber Law ProjectDocument14 pagesCyber Law ProjectDivyansh Sharma33% (3)
- Cyber Law Raunak SinhaDocument8 pagesCyber Law Raunak Sinhasinharaunak_1Pas encore d'évaluation
- Cyber Crime in IndiaDocument119 pagesCyber Crime in Indiajassi7nishadPas encore d'évaluation
- The Effects of Cybercrime in the U.S. and AbroadD'EverandThe Effects of Cybercrime in the U.S. and AbroadPas encore d'évaluation
- Full TextDocument47 pagesFull TextDhandapani ParasuramanPas encore d'évaluation
- Cyber Notes OnlineDocument107 pagesCyber Notes OnlineashishPas encore d'évaluation
- IT Law AssigmentDocument6 pagesIT Law AssigmentNiharika VermaPas encore d'évaluation
- Cyber Laws in Pakistan: Presented byDocument26 pagesCyber Laws in Pakistan: Presented bySajjadPas encore d'évaluation
- 11 - Chapter 5Document129 pages11 - Chapter 5rubabshaikhPas encore d'évaluation
- Putting An End To Cyber CrimeDocument3 pagesPutting An End To Cyber Crimeashok dekaPas encore d'évaluation
- Cyber Security and LawDocument3 pagesCyber Security and Lawakshai maniPas encore d'évaluation
- Cyber Law Also Called IT Law Is The Law Regarding Information-TechnologyDocument2 pagesCyber Law Also Called IT Law Is The Law Regarding Information-TechnologyVaalu MuthuPas encore d'évaluation
- CyberDocument6 pagesCyberAbhilasha PantPas encore d'évaluation
- Introduction To Cyber Law in IndiaDocument11 pagesIntroduction To Cyber Law in IndiaParamvir SinghPas encore d'évaluation
- Unit 1 Domestic Laws: Backgrounder: StructureDocument11 pagesUnit 1 Domestic Laws: Backgrounder: StructureAanika AeryPas encore d'évaluation
- 07 - Chapter 1Document23 pages07 - Chapter 1Tushar KapoorPas encore d'évaluation
- Maharshi Dayanand University, Rohtak: Assignment - IiDocument7 pagesMaharshi Dayanand University, Rohtak: Assignment - IiJames TaylorPas encore d'évaluation
- Un Pan 005846 Unpam TestDocument5 pagesUn Pan 005846 Unpam TestAdam Chabrini PrakosoPas encore d'évaluation
- CYBER LAW Case StudiesDocument15 pagesCYBER LAW Case StudiesManish DhanePas encore d'évaluation
- UntitledDocument3 pagesUntitledJifsina NaserPas encore d'évaluation
- Unit-Iv Cyber-Crime and The Legal Landscape Around The WorldDocument20 pagesUnit-Iv Cyber-Crime and The Legal Landscape Around The WorldayushPas encore d'évaluation
- Chapter - I: 1.1 Background of The StudyDocument51 pagesChapter - I: 1.1 Background of The StudyBabita BasnetPas encore d'évaluation
- Cyber SecurityDocument17 pagesCyber Securitysonu khanPas encore d'évaluation
- Module - 1 (Cyber Law)Document30 pagesModule - 1 (Cyber Law)ShreyaPas encore d'évaluation
- Joga Rao S. V (2004), Law of Cyber Crimes & Information Technology Law. 1st Edition, p.46Document21 pagesJoga Rao S. V (2004), Law of Cyber Crimes & Information Technology Law. 1st Edition, p.46shamaPas encore d'évaluation
- What Is Domain NameDocument30 pagesWhat Is Domain NameAzaan NavidPas encore d'évaluation
- Investigation of Cyber CrimesDocument9 pagesInvestigation of Cyber CrimesHitesh BansalPas encore d'évaluation
- CYBER LAW Notes MBADocument6 pagesCYBER LAW Notes MBADipon GhoshPas encore d'évaluation
- Computer Crime: The Law On The Misuse of Computers and NetworksDocument13 pagesComputer Crime: The Law On The Misuse of Computers and NetworksBridgestone55Pas encore d'évaluation
- Privacy and Freedom IssuesDocument8 pagesPrivacy and Freedom Issuesxyzxxx2010Pas encore d'évaluation
- Law & IT Ass. IX Sem. - Anas MohsinDocument36 pagesLaw & IT Ass. IX Sem. - Anas MohsinIzaan RizviPas encore d'évaluation
- 19 - Conclusion and SuggestionsDocument5 pages19 - Conclusion and SuggestionsBazim sayd usmanPas encore d'évaluation
- Law & ITDocument20 pagesLaw & ITAkash NarayanPas encore d'évaluation
- Cyber Laws in India - Research ArticleDocument9 pagesCyber Laws in India - Research ArticlekalaivaniPas encore d'évaluation
- Dr. Ram Manohar Lohia National Law University Lucknow, U.P.: Submitted To: Submitted byDocument21 pagesDr. Ram Manohar Lohia National Law University Lucknow, U.P.: Submitted To: Submitted bylokesh4nigamPas encore d'évaluation
- Cyber Law Project Lokesh NigamDocument21 pagesCyber Law Project Lokesh Nigamlokesh4nigamPas encore d'évaluation
- Dr. Ram Manohar Lohia National Law University Lucknow, U.P.: Submitted To: Submitted byDocument21 pagesDr. Ram Manohar Lohia National Law University Lucknow, U.P.: Submitted To: Submitted bylokesh4nigamPas encore d'évaluation
- Project PGDCL & IprDocument121 pagesProject PGDCL & IprIsaac New100% (1)
- Evolution Need of Cyber LawDocument20 pagesEvolution Need of Cyber LawJaspal KaurPas encore d'évaluation
- Ashutosh 09Document17 pagesAshutosh 09Ashutosh VermaPas encore d'évaluation
- The Indian Law Institute, New Delhi: Cyber Law - A Way AheadDocument36 pagesThe Indian Law Institute, New Delhi: Cyber Law - A Way AheadAmardeep KumarPas encore d'évaluation
- Philippines Cybercrime Law PaperDocument2 pagesPhilippines Cybercrime Law PaperPaul Claro CágroPas encore d'évaluation
- Emergence of Cyber Crimes: A Challenge For The New MillenniumDocument18 pagesEmergence of Cyber Crimes: A Challenge For The New Millenniumprayog.prayashPas encore d'évaluation
- Cyber LawDocument4 pagesCyber LawnovaPas encore d'évaluation
- 1504181797CyberCrime PDFDocument17 pages1504181797CyberCrime PDFPronay DhakPas encore d'évaluation
- Cyber Laws: Meaning, Types, Statistics, Measures IT Act of 2000 and 2008, About Cyber CellsDocument5 pagesCyber Laws: Meaning, Types, Statistics, Measures IT Act of 2000 and 2008, About Cyber CellssrivatsatjPas encore d'évaluation
- Cyber Law in IndiaDocument4 pagesCyber Law in Indiadrishti guptaPas encore d'évaluation
- Robert Moore, Cybercrime Investigating High-Technology Computer Crime. 2 Ed. (New York: Routledge, 2015) P. IxDocument50 pagesRobert Moore, Cybercrime Investigating High-Technology Computer Crime. 2 Ed. (New York: Routledge, 2015) P. IxTechnical SupportPas encore d'évaluation
- Vishal Dhotre PDFDocument11 pagesVishal Dhotre PDFAshish ThakurPas encore d'évaluation
- Cyber Security Meets National Security: International Perspectives on Digital Era ThreatsD'EverandCyber Security Meets National Security: International Perspectives on Digital Era ThreatsPas encore d'évaluation
- Scandinavian Realist V American RealistDocument13 pagesScandinavian Realist V American RealistSudhakarMishraPas encore d'évaluation
- Legal Remedies in TortDocument25 pagesLegal Remedies in TortSudhakarMishra81% (16)
- Cover LetterDocument9 pagesCover LetterSudhakarMishraPas encore d'évaluation
- State of Maharashtra and Anr. vs. AND vs. AND VsDocument2 pagesState of Maharashtra and Anr. vs. AND vs. AND VsSudhakarMishraPas encore d'évaluation
- 012 IC20 Manual enDocument39 pages012 IC20 Manual enRahul RaveendranPas encore d'évaluation
- Gmail - Urgent Hearing On IA (L) No. 34649 of 2023 in WP (L) No. 10862 of 2023 - CJEX Biochem V. Board of Directors of Pegasus AssetsDocument2 pagesGmail - Urgent Hearing On IA (L) No. 34649 of 2023 in WP (L) No. 10862 of 2023 - CJEX Biochem V. Board of Directors of Pegasus Assetsshameem fayizPas encore d'évaluation
- Cyber Crime PDFDocument3 pagesCyber Crime PDFarchanaPas encore d'évaluation
- What Is IctDocument8 pagesWhat Is IctJules GajesPas encore d'évaluation
- SEO Affiliate Marketing: A Comprehensive GuideDocument18 pagesSEO Affiliate Marketing: A Comprehensive GuideSARAHPas encore d'évaluation
- Online Mid Term Examination CC Spring 2021 18052021 021841pmDocument3 pagesOnline Mid Term Examination CC Spring 2021 18052021 021841pmshaikh shahrukhPas encore d'évaluation
- Report CP301Document7 pagesReport CP301Hitesh MinaPas encore d'évaluation
- Kaushlendra Singh - CV PDFDocument2 pagesKaushlendra Singh - CV PDFKaushlendraPas encore d'évaluation
- 3rd Class Mathematics NotesDocument7 pages3rd Class Mathematics Noteskoushikbatra66Pas encore d'évaluation
- Chris Tammar Graphic/Web Designer: Contact AboutDocument1 pageChris Tammar Graphic/Web Designer: Contact AboutSarah YPas encore d'évaluation
- Trustwave Vulnerability Management: Stay Ahead of Network VulnerabilitiesDocument2 pagesTrustwave Vulnerability Management: Stay Ahead of Network VulnerabilitiesEhtasham Ul HaqPas encore d'évaluation
- Outbound Scheduling With Customer CalendarDocument5 pagesOutbound Scheduling With Customer CalendarAnupa Wijesinghe100% (2)
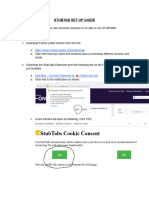
- Stubtabs Set Up GuideDocument4 pagesStubtabs Set Up GuideEdson Ella Jr.Pas encore d'évaluation
- Network & Cyber Security - module3-IPSECURITY - Part2Document12 pagesNetwork & Cyber Security - module3-IPSECURITY - Part2Sushil LamsalPas encore d'évaluation
- Nama: Krisna Dwiki Aldi Kelas: TKK 1B NPM: 183304039Document1 pageNama: Krisna Dwiki Aldi Kelas: TKK 1B NPM: 183304039hanirifdah100% (1)
- An Intelligent Phishing Detection and Protection Scheme Using A Fusion of Images, Frames and TextDocument226 pagesAn Intelligent Phishing Detection and Protection Scheme Using A Fusion of Images, Frames and TextManfred MoreraPas encore d'évaluation
- Aliff Izdiyad Bin Azmi ITT633 NATDocument2 pagesAliff Izdiyad Bin Azmi ITT633 NATNURUL NAZIRA AMINPas encore d'évaluation
- 1.tender Creation - PublishDocument190 pages1.tender Creation - PublishTanuja Sawant 50Pas encore d'évaluation
- CCNA FINAL Exam 2 March 2010 and Some Other ExamDocument189 pagesCCNA FINAL Exam 2 March 2010 and Some Other ExamAli NorooziPas encore d'évaluation
- PROJECT 6 Website PDFDocument2 pagesPROJECT 6 Website PDFMuhd Rasydan100% (2)
- Midterm 40-50 (80%)Document40 pagesMidterm 40-50 (80%)Deuter AbusoPas encore d'évaluation
- SEO ReportDocument22 pagesSEO ReportT HubPas encore d'évaluation
- Cisco Security FilesDocument11 pagesCisco Security FilesmikemalbertPas encore d'évaluation
- Secure Login For SAP NetWeaver Single Sign-On Implementation GuideDocument267 pagesSecure Login For SAP NetWeaver Single Sign-On Implementation GuideJulio MontenegroPas encore d'évaluation
- Ijcnc 050205Document12 pagesIjcnc 050205AIRCC - IJCNCPas encore d'évaluation
- The Role of Digital Forensic in Solving Cyber Crimes PDFDocument3 pagesThe Role of Digital Forensic in Solving Cyber Crimes PDFabhi740% (1)
- CCNA Security Packet Tracer Skill Based Assessment PracticeDocument9 pagesCCNA Security Packet Tracer Skill Based Assessment PracticeFrija011Pas encore d'évaluation
- Module1 PDFDocument11 pagesModule1 PDFhimanshu mauryaPas encore d'évaluation
- Scribd Secures $9M Series B, Hires Bebo COO George ConsagraDocument2 pagesScribd Secures $9M Series B, Hires Bebo COO George ConsagraScribd100% (8)