Académique Documents
Professionnel Documents
Culture Documents
Two Step Design For Personal Authentication Using Finger Vein Recognition and GSM Technology
Transféré par
ijtetjournalTitre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Two Step Design For Personal Authentication Using Finger Vein Recognition and GSM Technology
Transféré par
ijtetjournalDroits d'auteur :
Formats disponibles
INTERNATIONAL JOURNAL FOR TRENDS IN ENGINEERING & TECHNOLOGY
VOLUME 4 ISSUE 2 APRIL 2015 - ISSN: 2349 - 9303
Two Step Design for Personal Authentication Using
Finger Vein Recognition and GSM Technology
N.Revathy1
1
Velammal Institute of Technology, Electronics and
Communication Department.
R.Dilli Babu3
Velammal Institute of Technology, Electronics and
Communication Department
rdillibabuece@gmail.com
S.Vijayanarayanan 2
Velammal Institute of Technology, Electronics and
Communication Department.
vijayanarayanans@yahoo.in
A.Vimal Raj4
Velammal Institute of Technology, Electronics and
Communication Department
electronicpostals@gmail.com
Abstract This paper has proposed another methodology of constant implanted finger vein distinguishment alongside GSM innovation
for individual validation and security is made. [1]Unique human attributes are utilized to distinguish an individual or to confirm a character.
Finger vein recognizer, is utilized as a first level security for a confirmation process furthermore for showing or alarming unapproved
individual if entered. The equipment is the procedure with the assistance of Finger vein recognizer and transformed utilizing MATLAB
programming, which is modest and dependable in all the structures. GSM innovation is utilized as a second level security, where the client
sends a Novel code to the GSM recipient which on distinguishment sends a secret key to the Client for opening. [2]The proposed framework
takes just 0.5 seconds to confirm one info finger vein test and the normal mistake rate (ERR) of 0.06.
Index Terms finger vein technology, GSM SIM 300 technology, Security, MATLAB, Personal authentication.
1 INTRODUCTION
These days security assumes an imperative part in our surroundings,
on the grounds that they are utilized as a part of different purposes,
for example, for individual confirmation, managing an account and
for all different purposes. Two essential outlines, for example, Finger
vein distinguishment which is finished with the assistance of the
MATLAB programming, where the examined pictures are
preinstalled in the framework amid the security handle the finger is
kept in the finger vein equipment and with the assistance of the USB
cam and the IR sensor the picture is checked and checked with the
preinstalled picture and GSM SIM 300 advancements has been
utilized as a part of the framework for sending an OTP(one time
password) to the particular client furthermore for cautioning the
unapproved client by communicating something specific.[3]. This
will bring protection everywhere throughout the world, so with the
assistance of these strategies we propose a novel configuration for
two level security framework for individual verification.
Therefore, it is a natural and convincing proof that the subject whose
finger-vein is successfully captured is a live. These workings are still
in progress and they are a little bit not fancy. The quality of fingervein images can be highly influenced by the imaging conditions;
vein patterns can be distorted from the finger pressure in a
conventional setup [6], [7]. They are unique for each and every one
and are stable. Due to its uniqueness, stability, to criminal tampering,
vein pattern recognition offers a more reliable solution for secure
biometric authentication systems. Below we are going to discuss
about structure of the finger vein pattern.
2.2 PROCESS
Finger vein recognition is explained with its components. In the first
stage of security, the finger is kept in the finger vein system
hardware and it is processed for authentication. The finger is kept on
the sensor for processing the device, it consists of a USB camera, IR
sensor, Power supply, cover for protecting the screen, after is it
placed on the screen, the NIR sensor sends a signal to our fingers and
with the help of the USB camera the images are captured and it is
processed. The hardware is connected to a memory device which
stores the original scanned finger vein images and when the person
keeps the finger it will match with the stored images and display the
result for in this case. Few images arent clear while scanning, which
is overcome by using the MATLAB process.
2 SYSTEM ARCHITECTURE
2.1 FINGER VEIN RECOGNITION
The finger-vein is a biometrics pattern for personal identification for
security purposes. Vein patterns are the vast network of blood vessels
underneath a persons skin. The finger-vein has the more advantage
than the other systems. The vein is hidden inside the body and is
mostly invisible to human eyes, so it is difficult to forge or steal.
[5]The finger-vein pattern can only be taken from alive body.
60
INTERNATIONAL JOURNAL FOR TRENDS IN ENGINEERING & TECHNOLOGY
VOLUME 4 ISSUE 2 APRIL 2015 - ISSN: 2349 - 9303
2.3 BLOCK DIAGRAM
2.4 WORKING
[1] Once our finger is kept on the sensor, the image is captured and it
is sent for matching. The matching process is done with the help of
the MATLAB process. Fig 1.2 tells us about the working of the
MATLAB process where each and every block is explained in detail.
The Structural image of the finger vein is shown below. First the
image is acquired and then it is processed which is shown in Fig
1.3(a). In order to obtain a clean image the excessive and the
unwanted area and the lossy parts should be removed from the
sampled image. First, the image is converted into a binarized image
as shown in Fig 1.3(b) and the edge mapping is done. This is done in
two steps. First, the edge detector which we are using here is SOBEL
edge detector which is applied to the entire image(c), and the output
edge map is removed from the binarized image. And then sampled
image is compared with the saved image
Fig 1.3. (a) Acquired image sample. (b) Binarized image.
(c) The subtracted edge mapping image (d) ROI mask from the
Image in (e) ROI finger vein image. [1]
Fig 1.1 block diagram of working of Finger vein system linked
with MATLAB process
On the off chance that in case the picture is not clear or the picture is
mutilated we need to take after an alternate strategy for transforming
the picture. Initially an imprint is kept in the beginning of the picture
and afterward the fact of the matter is augmented, bending in the
picture or the lossy disengagement is acquired. This is then corrected
and prepared as a solitary picture and afterward it is sent for the
coordinating procedure.
Fig 1.4 (a) Acquired finger vein image. (b) ROI mask from (a).
(c) ROI mask after refinement. [1]
The same process, for example, 1) Division 2) Improvement 3)
Extraction 4) Coordinating with the database is completed in the
above procedure once in the wake of discovering the disengaged
district or the intruded on an area in the examined picture. It then
matches with the preinstalled picture in the database and then it
sends a data to the Microcontroller.
Fig 1.2 Block diagram of whats happening inside the MATLAB
processing.
The principle work of the microcontroller, it gets the sign from the
MATLAB processor and on the off chance that it is a "YES" then the
Entryway is opened (we are considering an entryway in this
clarification) on the off chance that it is a "NO" then it gives a ready
that an unapproved individual is attempting to enter inside.
61
INTERNATIONAL JOURNAL FOR TRENDS IN ENGINEERING & TECHNOLOGY
VOLUME 4 ISSUE 2 APRIL 2015 - ISSN: 2349 - 9303
3 GSM SIM 300
Wrongdoing is heading consistently and it is vital to take essential
measures on security. In present day innovation, we must utilize vital
structures with simple establishment in evading manual work. Our
task gives the best approach to ensure home, office and so on
through GSM innovation by sending OTP (ONE TIME
PASSWORD) to the separate client. In the present day development
of remote correspondence, we thusly utilize this framework to
upgrade the security that satisfies the need of advanced innovation.
The utilization of GSM framework in security applications, controls
the use of wired structures which gets to be more muddled and very
problematic. In such case, this GSM model can enhance the
productivity of the methodology considered, supposed security
framework. It likewise improves as an alternative.
Fig 2.1 shows the block diagram of the basic block diagram of the
working of this method
4 OUR WORK
SMS is defined as a SHORT MESSAGE SERVICE also defined as a
text based service that enables us to use 160 characters for
communication. It is also similar to email where the texts are stored
and forwarded from a center that is normally associated for SMS. If
the person is not available immediately for the process the message
is stored and retrieved automatically. Unlike calls they cannot be
excluded from the user if he is not available at a right time. The
message is retrieved later, whenever the user is available. It is also
one of the major advantages of Short Message Service.
The Fundamental idea of our undertaking is to give GSM based
security by sending an interesting secret key through SMS the
security framework which comprises of its own GSM module and
perceives the watchword and itself checking it sending an OTP to the
client. This GSM Modem can acknowledge any GSM system
administrator SIM card and act much the same as a cellular
telephone with its own extraordinary telephone number. The client
on getting the OTP through SMS from the framework, sorts the
relating OTP in the keypad, as data, which checks coordinating,
lastly the secured framework under lock is opened. We therefore
utilize GSM in light of the fact that it is shabby, simple and promptly
accessible innovation. Further the framework itself comprises of
GSM modem for sending and tolerating messages. ATMEL 89S52
microcontroller is utilized to control the framework. The LCD is
utilized for presentation. A key cushion is utilized for entering the
secret word. Here the individual who is approved has the general
control. As said before, the person who has to open the
corresponding security system has his own password which is
preloaded in the end system. Now the person has his own password.
He has to send the password as SMS to the system. Once the
password is matched, the microcontroller operates the system and
initiates the sending of OTP to the user. The user who had received
OTP via SMS uses this to type as key on the keypad. The
microcontroller checks the match. Depending on the response it
decides to open or stay closed. Once the match is authorized the
microcontroller itself switches the relay and turns it on. The relay
works and opens the corresponding security system. The GSM
system used makes the communication mechanism between user and
system through SMS. Microcontroller is growing filed when the
present day situation is considered. Embedded designs can also be
installed easily. The project, explained above is also a good example
of embedded system design. Significantly, we can develop the
project using this embedded design and much easily. As we know
the basics of embedded design is microcontroller. Microcontroller is
a chip which consists of all support functions such as clock, reset,
memory and I/O built inside the device. Also the basic block
diagram of this system is given below.
5 TECHNOLOGY INSIDE
62
Microcontroller is the central core of the present day embedded
system. Here we are using ATMEL 89S52. It has 6 clock cycles per
period instead of 12. So the system speed can be increased further.
Thus the communication can be increased by 115200kbps.The core
of the circuit is ATMEL 89S52. It is a single chip 8-bit
microcontroller. It has I/O ports of 8 bits. Timer event counters of 16
bits. It also consists of enhanced UART, oscillator, and timing
circuits. It is also inbuilt with 4kb flash memory. It enhances the use
of parallel programming, in-system and in-application programming.
Further the controller consists of various ports. Port 0, 1, 2, 3. Each
performing its own tasks. The pin associated with controller consists
of RST input, i.e. reset that resets whenever the pin becomes high.
ALE pin or address latch enable. It is also used as program pulse
input during flash memory operation. If desired, the operation can be
stopped by setting 0 of SFR location 8EH. PSEN is the Program
Store Enable strobe to external program memory. Further the XTAL
is the oscillator used. The next part in our project is IC MAX 232A.
Its used for serial communication in the design. It also acts as a
voltage converter. We all know that RS232 is not compatible with a
microcontroller. So we need a voltage converter which converts
Transistor Logic voltage levels that will be acceptable to the 89S51.
INTERNATIONAL JOURNAL FOR TRENDS IN ENGINEERING & TECHNOLOGY
VOLUME 4 ISSUE 2 APRIL 2015 - ISSN: 2349 - 9303
Fig 2.2 shows the basic block diagram of the working of the GSM
SIM 300 module embedded with the XBOARD attached with the
LCD display
the database. To begin with, the filtered picture is binarized and the
inordinate area and lossy territories are disposed off. The picture is
further refined through the MATLAB process and the first district of
investment is put away inside the database. At the point when the
individual who needs to gets past the entryway must keep his finger
on the identifier. The identifier is contained USB cam above and IR
Drove underneath.
The picture of the finger once kept is examined and caught with the
cam and the picture is send for further handling. After a few courses
of action of picture division, and picture improvement the ideal
picture without commotion is send to the database in pairs
arrangement. The coordinating of the constant result is finished with
the effectively put away information in the database. The coordinated
is carried out by the microcontroller. When the outcome is sure, the
microcontroller works the transfer and make access to gets past the
entryway. Subsequently the client completes his first level security.
The second level security is GSM innovation. Once the client goes
into the room. He himself utilizes his cellular telephone to send a
SMS to the end security framework which is as of now preloaded
with the GSM module. The framework on getting the SMS checks
for its uniqueness with the operation of the microcontroller. In the
event that the coordinating is carried out the yield of the
microcontroller is certain. When the outcome is certain the
framework is made to produce the arbitrary one time secret key and
make it answer to the client. The client on accepting the one time
secret word by means of SMS needs to sort this as a key on the
keypad. Once the framework created one time secret word is
coordinated with the particular case that is being written, the
microcontroller works the hand-off joined to it and opens the locker.
Along these lines the two level verification makes high security and
further improved security to enhance the framework wellbeing.
7.1 CONCLUSION
This paper has proposed another level of security frameworks for
individual confirmation furthermore for different applications. With
the assistance of the finger vein indicator, we can secure a steady,
novel and a secured biometric framework with the assistance of the
above segments the framework can be solid and transformed with no
deviations. Despite the fact that the gadget is expensive it can
transform consistently and the level of the security is high when
contrasted and alternate techniques for biometric filtering. With
respect to second level security is concerned, which is GSM SIM
300 innovation, it is a shabby and dependable framework which
conveys between the client and the gadget continually with no
obstruction. What's more the fundamental focal point of this
framework is the novel arbitrary code which is produced by the
gadget and sent to the client for confirmation which makes this
framework profoundly securable. Although more work is to be
transformed, our outcomes to the blend of the Finger vein innovation
and the GSM SIM 300 innovation is guaranteed and it is a superior
development in the field of security. This is particularly utilized as a
part of the field of security frameworks and all different fields
identified with it.
Finally, it uses RS232 cables to send the data. The IC is a dual
driver or dual receiver. It also has a capacitive voltage generator for
supplying TIA/EIA 232F. The receiver converts those inputs to 5V
TTL/CMOS. Each driver converts them back to TIA/EIA 232F.
Further, this is the first IC which contains the set of the necessary
drivers and receivers, each 2. It is also easy in adapting the RS 232
signals TTL logic. It also finds its way in simplifying or minimizing
the circuitry. The introduction of MAX232, there is also the net level
IC of same family i.e. MAX 232A. But MAX232A is just a driver
and receiver. Further, it does not generate necessary RS232 signals or
provide serial/parallel conversion. But it converts signal voltage
levels. Extra circuits can be used to decode serial data and to
generate serial data at the correct timing. The recent MAX233 can be
used, the difference between the prior versions is that it has built in
capacitor while the last version has to be attached with an external
capacitor. It is used under fixed voltages for one device. But planned
cabling can be used to avoid those distortions. It also loaded with
protocol ability to send and receive to and from the attached device.
We use TTL logic or CMOS, the prior step is connecting RS 232
port. Hence serial communication is enhanced mainly due to these
couplings at particular voltage levels. GSM stands for Global System
for Mobile communications. The modem used here is GSM modem.
It is not similar to other conventional modems used. It also send or
receive calls/SMS using Subscriber Identity Module (SIM), which is
used as an identity. The system is connected to the RF antenna that
transmits and receives data. The advantage of using this is it is
digitally processed. It refers to Subscriber Identity Module. It stores
the information of the operator and user and it also acts as a separate
identity for each user. It allows the handset to stay connected to the
particular network by constant connectivity through the information
through the SIM.
6 WORKING OF THE SYSTEM
Finger vein innovation is utilized as a first level security framework
and the GSM SIM 300 innovation is utilized as a second level
security framework. Inevitably, the finger vein recognizer is
appended to the entryway. On the off chance that a man needs to
enter through the entryway, the individual ought to pass the
individual security i.e. the finger vein perceiving innovation. The
individual ought to keep his finger in the locator, which filters the
picture and matches with the database introduce inside the
framework. This methodology is completed utilizing MATLAB
programming. The individual's tested picture is now nourished into
63
INTERNATIONAL JOURNAL FOR TRENDS IN ENGINEERING & TECHNOLOGY
VOLUME 4 ISSUE 2 APRIL 2015 - ISSN: 2349 - 9303
REFERENCES
[1] Zhi Liu and Shangling Song An EmbeddedReal-Time FingerVein Recognition SystemFor Mobile Devices,IEEE Transactions on
Consumer Electronics, Vol. 58, No. 2, May2012.
[2] V.Ramya, P.Vijaya kumar, B.Palaniappan ANOVEL DESIGN
OF FINGER VEIN RCOGNITION FOR PERSONAL
UTHENTICATION AND VEHICE SECURITY Journal of
Theoretical and Applied Information Technology, Vol. 65, No.1.
[3] T.Y.V BhanuKiranmai, K.Amruthavally, andG.Harish An
Embedded Real-Time Finger-Vein Recognition System for Security
Levels,International Journal of Application orInnovation in
Engineering & Management(ijaiem), Volume. 2, Issue. 6, June 2013.
[4] Caixia Liu, Study on Finger Vein Feature Extraction
Algorithm, International Journal of Computer Science Issues, vol.
10, no 3, 2012.
[5] Ajay Kumar and Yingbo Zhou Human Identification Using
Finger Vein, IEEE Transaction on image processing, Vol.21, No.4,
2012.
[6] E. C. Lee and K. R. Park, Restoration method of skin scattering
blurred vein image for finger vein recognition, Electron. Lett., vol.
45, no. 21, pp.10741076, Oct. 2009.
[7] Ma Yuchun; Huang Yinghong; Zhang Kun; LiZhuang, "General
Application Research on GSM module," Internet Computing &
Information Services(ICICIS), 2011 International Conference on ,
vol., n., pp.525,528, 17-18 Sept. 2011
[8] Jingjing Wang, "Realizing SMS Using PC's Serial Port Based on
VC++," Computer Science an Engineering, 2009. WCSE '09. Second
International Workshop on, vol.2, no., pp.382, 384,8-30 Oct. 2009
64
Vous aimerez peut-être aussi
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5795)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (588)
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (400)
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2259)
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (74)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (266)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (345)
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (121)
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)
- Installation - Hardware Key (Network Driverless Red)Document10 pagesInstallation - Hardware Key (Network Driverless Red)icaro100% (1)
- StarPassPRNT Ios SM enDocument29 pagesStarPassPRNT Ios SM enUlises ContrerasPas encore d'évaluation
- HIKVision NVR and Camera ConnectionsDocument3 pagesHIKVision NVR and Camera ConnectionsNanang HadiPas encore d'évaluation
- Lenovo EMC Px4-300r ProDocument4 pagesLenovo EMC Px4-300r ProEldar IsgenderovPas encore d'évaluation
- Parallel Computing TerminologyDocument11 pagesParallel Computing Terminologymaxsen021Pas encore d'évaluation
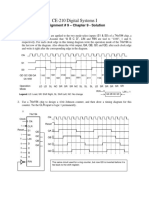
- Solution - Ass # 9 - CH 9 - s2016Document3 pagesSolution - Ass # 9 - CH 9 - s2016Abigail EnglePas encore d'évaluation
- Raspberry Pi CourseDocument2 pagesRaspberry Pi CourseIEEE Projects BengaluruPas encore d'évaluation
- Lenovo V14 G2 ALC SpecDocument7 pagesLenovo V14 G2 ALC SpeckevinaprizaPas encore d'évaluation
- Backup LogDocument2 pagesBackup LogDito ArdantoPas encore d'évaluation
- Compellent Best Practices For LinuxDocument31 pagesCompellent Best Practices For LinuxSujit FrancisPas encore d'évaluation
- Sof Nco - Class 8Document2 pagesSof Nco - Class 8pasenthPas encore d'évaluation
- Department of Labor and Employment Information Technology (It) Assessment and Preventive Maintenance Checklist As of (YEAR)Document4 pagesDepartment of Labor and Employment Information Technology (It) Assessment and Preventive Maintenance Checklist As of (YEAR)Nestor Adrian LatogaPas encore d'évaluation
- Vsan 70 Planning Deployment GuideDocument77 pagesVsan 70 Planning Deployment GuideRosembert AvilaPas encore d'évaluation
- Report On Attendance Management System PDFDocument62 pagesReport On Attendance Management System PDFAbhishek100% (1)
- It Essentials & Comptia A+: Cisco NetacadDocument43 pagesIt Essentials & Comptia A+: Cisco NetacadThilina A PereraPas encore d'évaluation
- Introduction To Profibus DP: Busworks 900Pb Series Profibus/Rs485 Network I/O Modules Technical ReferenceDocument38 pagesIntroduction To Profibus DP: Busworks 900Pb Series Profibus/Rs485 Network I/O Modules Technical ReferenceDineshkumarPas encore d'évaluation
- NUC7i5BN NUC7i7BN TechProdSpecDocument83 pagesNUC7i5BN NUC7i7BN TechProdSpecJuan Martín Bresciano O'NeillPas encore d'évaluation
- Docslide - Us Ibm-275 PDFDocument377 pagesDocslide - Us Ibm-275 PDFdanmierlutPas encore d'évaluation
- FZ300 Firmware Update LDocument4 pagesFZ300 Firmware Update LrethalesPas encore d'évaluation
- (Guide) (How To Port Roms) (Snapdragon) (Window - Android Development and HackingDocument1 page(Guide) (How To Port Roms) (Snapdragon) (Window - Android Development and HackingJus RajPas encore d'évaluation
- 2002 Display Products (With Dealer Pricing)Document9 pages2002 Display Products (With Dealer Pricing)ericksgalaPas encore d'évaluation
- Computer Hardware Intro&Input UACE Sub-ICTDocument84 pagesComputer Hardware Intro&Input UACE Sub-ICTCharles Lwanga NjalaPas encore d'évaluation
- Uninstall w7 N ProgramsDocument7 pagesUninstall w7 N ProgramsgangudangPas encore d'évaluation
- Compact NVR As 4000 Datasheet LetterDocument2 pagesCompact NVR As 4000 Datasheet LetterDocUploader22Pas encore d'évaluation
- Progfunhandouts 2010Document43 pagesProgfunhandouts 2010Alji MartinezPas encore d'évaluation
- PIC18XXXDocument332 pagesPIC18XXXmilenarico100% (1)
- DDR5 Vs DDR4 - All The Design Challenges & Advantages - RambusDocument4 pagesDDR5 Vs DDR4 - All The Design Challenges & Advantages - Rambussantosh soodPas encore d'évaluation
- Memorii Ram Q45MDocument2 pagesMemorii Ram Q45MElena MitruPas encore d'évaluation
- Brother DL Series - MFC-L5900DWDocument3 pagesBrother DL Series - MFC-L5900DWDonPas encore d'évaluation
- Cloudera Data Platform - Data Center (CDP-DC) Reference ArchitectureDocument38 pagesCloudera Data Platform - Data Center (CDP-DC) Reference ArchitectureTech Flame100% (1)