Académique Documents
Professionnel Documents
Culture Documents
Lab 5
Transféré par
Tomas Rodriguez RamirezTitre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Lab 5
Transféré par
Tomas Rodriguez RamirezDroits d'auteur :
Formats disponibles
Lab ID: 9.9K317A061.DHI2.
Reviewing Access Lists
Objective
Isolate the two virtual LANs (VLANs) by using access control lists (ACLs) on Router1 to prevent hosts in
the 192.168.101.0 network from communicating with hosts in the 192.168.102.0 network. After the ACLs
have been configured, PC1 should be able to use Ping and Telnet to communicate with all other hosts.
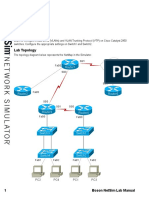
Lab Topology
The topology diagram below represents the NetMap in the Simulator. The topology in this lab consists of
a LAN that has two switches connected by a trunk link. Each switch has two PC hosts connected. VLANs
have been implemented on both switches. The VLANs are used to create separate networks with two PC
hosts in each VLAN. A router connected to one of the switches handles interVLAN routing.
Router1
Fa0/0
Fa0/1
Fa0/2 Fa0/1
Switch1 Switch2
Fa0/3 Fa0/4 Fa0/3 Fa0/4
PC1 PC2 PC3 PC4
Command Summary
Command Description
access-list access-list-number {deny | defines an extended IP ACL for the traffic type specified by the
permit} protocol source source-wildcard protocol parameter
[operator [port]] destination destination-
wildcard [operator [port]] [log]
configure terminal enters global configuration mode from privileged EXEC mode
enable enters privileged EXEC mode
end ends and exits configuration mode
exit exits one level in the menu structure
interface type number changes from global configuration mode to interface
configuration mode
ip access-group {access-list-number | controls access to an interface
access-list-name} {in | out}
ip address ip-address subnet-mask assigns an IP address to an interface
ipconfig /all is used in NetSim to display the IP addresses and Media Access
Control (MAC) address on a workstation
1 Boson NetSim Lab Manual
Command Description
ping ip-address sends an Internet Control Message Protocol (ICMP) echo
request to the specified address
show ip interface brief displays a brief summary of interface status and configuration
show mac-address-table displays the Media Access Control (MAC) forwarding table
show running-config displays the active configuration file
show vlan displays VLAN information
telnet ip-address starts the terminal emulation program from a PC, router, or
switch; permits you to access devices remotely over the network
The IP addresses and subnet masks used in this lab are shown in the tables below:
IP Addresses
Device Interface IP Address Subnet Mask
Router1 FastEthernet 0/0 192.168.100.1 255.255.255.0
FastEthernet 0/0.11 192.168.101.1 255.255.255.0
FastEthernet 0/0.22 192.168.102.1 255.255.255.0
Switch1 VLAN 1 192.168.100.2 255.255.255.0
Switch2 VLAN 1 192.168.100.3 255.255.255.0
Device IP Address Subnet Mask Default Gateway
PC1 192.168.101.11 255.255.255.0 192.168.101.1
PC2 192.168.102.22 255.255.255.0 192.168.102.1
PC3 192.168.101.13 255.255.255.0 192.168.101.1
PC4 192.168.102.24 255.255.255.0 192.168.102.1
Lab Tasks
All configuration passwords have been configured as cisco.
Task 1: Examine the Initial Network Configuration
A. Examine the Current VLAN Configuration
1. Two VLANs are configured in the simulated network. What are the VLAN IDs? ________________
What are the VLAN names? _______________________________________________________
2. To which VLAN does each PC host belong?
PC1: __________________________________________________________________________
PC2: __________________________________________________________________________
PC3: __________________________________________________________________________
PC4: __________________________________________________________________________
2 Boson NetSim Lab Manual
B. Examine Network Connectivity
1. From PC1, attempt to ping PC2 (192.168.102.22). Is the ping successful? ___________________
2. Are PC1 and PC2 in the same VLAN? ________________________________________________
If the ping is successful, explain how the ping succeeds while PC1 and PC2 are in different VLANs.
______________________________________________________________________________
3. From PC1, attempt to ping PC3 (192.168.101.13). Is the ping successful? Why or why not? ______
______________________________________________________________________________
Task 2: Configure ACLs
A. Review Characteristics of ACLs
1. What are ACLs used for? __________________________________________________________
______________________________________________________________________________
2. What are some differences between standard ACLs and extended ACLs? ____________________
______________________________________________________________________________
3. What are the numeric ID ranges for standard ACLs? What are the numeric ID ranges for extended
ACLs? ________________________________________________________________________
______________________________________________________________________________
4. Can access lists consist of multiple access list statements? In what order are these statements
evaluated? _____________________________________________________________________
______________________________________________________________________________
5. Describe the implicit deny rule. _____________________________________________________
______________________________________________________________________________
B. Prepare for ACLs
1. To what network do PC1 and PC3 connect? ___________________________________________
2. To what network do PC2 and PC4 connect? ___________________________________________
3. When PC1 sends traffic to PC2, which device on the network is responsible for moving this traffic
between networks? ______________________________________________________________
4. When PC1 sends traffic to PC4, which device on the network is responsible for moving this traffic
between networks? ______________________________________________________________
5. What Transport layer protocol is used by Telnet? _______________________________________
6. What Transport layer protocol is used by Ping? _________________________________________
3 Boson NetSim Lab Manual
C. Implement an Extended ACL for Traffic Flowing from VLAN 11 to VLAN 22
The objective for this lab is to use ACLs to prevent any traffic from flowing between the two VLANs, with
the exception that PC1 should be able to communicate with any of the hosts in VLAN 22 by using only
Ping and Telnet. Hosts in both VLANs should be able to communicate with any other networks except the
network for the other VLAN.
1. Examine the network. Which device is responsible for moving traffic between VLANs? __________
2. In order to accomplish the objective, how many extended ACLs will you need to create on the device
you noted in step 1? What is the purpose of each ACL? __________________________________
3. On the device you noted in step 1, create an entry for ACL number 111 that allows Ping traffic from
PC1 to reach any host on VLAN 22.
4. On the device you noted in step 1, create an entry for ACL 111 that allows Telnet traffic from PC1 to
reach any host on VLAN 22.
5. On the device you noted in step 1, create an entry for ACL 111 that denies any traffic other than
Telnet and Ping traffic from VLAN 11 to VLAN 22.
6. On the device you noted in step 1, create an entry for ACL 111 that permits any other traffic from
VLAN 11 to reach any destination other than VLAN 22. Keep in mind that there is an implied deny at
the end of every ACL.
7. ACL 111 has now been created, but it will not affect the traffic flow until it is assigned to an interface.
Keep in mind that ACL 111 will be used to filter traffic flowing from the PC hosts in VLAN 11. Which
interface will receive traffic from the PC hosts in VLAN 11? _______________________________
8. From the perspective of the router, which direction will the traffic flow through this interface as it
moves from the PC hosts in VLAN 11 to VLAN 22: in or out? ______________________________
9. On the device you noted in step 1, assign ACL 111 to the appropriate interface in the appropriate
direction.
D. Implement an Extended ACL for Traffic Flowing from VLAN 22 to VLAN 11
1. Create an entry for ACL number 122 that allows Ping reply traffic from any host on VLAN 22 to flow
back to PC1.
2. Create an entry for ACL number 122 that allows Telnet traffic from any host on VLAN 22 to reach
PC1.
3. Create an entry for ACL number 122 that denies any traffic other than Telnet and ping traffic from
VLAN 22 to VLAN 11.
4. Create an entry for ACL number 122 that permits any other traffic from VLAN 22 to reach any
destination other than VLAN 11. Keep in mind that there is an implied deny at the end of every ACL.
4 Boson NetSim Lab Manual
5. ACL 122 has now been created, but it will not affect the traffic flow until it is assigned to an interface.
Keep in mind that ACL 122 will be used to filter traffic flowing from the PC hosts in VLAN 22. Which
interface will receive traffic from the PC hosts in VLAN 22? _______________________________
6. From the perspective of the router, which direction will traffic flow through this interface as it moves
from the PC hosts in VLAN 22 to VLAN 11: in or out? ____________________________________
7. Assign ACL 122 to the appropriate interface in the appropriate direction.
Task 3: Verify ACLs
A. Verify Ping
1. From PC1, attempt to ping PC3 (192.168.101.13). Is the ping successful? ___________________
How do the ACLs affect the flow of traffic from PC1 to PC3? ______________________________
2. From PC1, attempt to ping PC2 (192.168.102.22) and PC4 (192.168.102.24). Are the pings
successful? ____________________________________________________________________
How do the ACLs affect the flow of traffic from PC1 to PC4? ______________________________
3. From PC3, attempt to ping PC2 (192.168.102.22) and PC4 (192.168.102.24). Are the pings
successful? ____________________________________________________________________
Briefly explain why the behavior you observe when you ping from the console of PC3 may differ from
the behavior you observe when you ping from the console of PC1. _________________________
______________________________________________________________________________
B. Verify Telnet
1. From PC1, attempt to telnet to the FastEthernet 0/0.22 interface on Router1 (192.168.102.1). Can
you successfully use Telnet to connect to this IP address? ________________________________
How do the ACLs affect the Telnet session? ___________________________________________
2. From PC3, attempt to telnet to the FastEthernet 0/0.22 interface on Router1 (192.168.102.1). Can
you successfully use Telnet to connect to this IP address? ________________________________
How do the ACLs affect the Telnet session? ___________________________________________
______________________________________________________________________________
Once you have completed this lab, be sure to check your work by using the grading function.
You can do so by clicking the Grade Lab icon ( ) in the toolbar or by pressing Ctrl+G.
5 Boson NetSim Lab Manual
Lab Solutions
All configuration passwords have been configured as cisco.
Task 1: Examine the Initial Network Configuration
A. Examine the Current VLAN Configuration
1. The two VLAN IDs are VLAN 11 and VLAN 22. VLAN 11 is named odd and VLAN 22 is named
even. You can view this information by using the show vlan command on Switch1 or Switch2.
Sample output from Switch1 is shown below:
Switch1#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
11 odd active Fa0/3
22 even active Fa0/4
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
<output omitted>
2. PC1 belongs to VLAN 11.
PC2 belongs to VLAN 22.
PC3 belongs to VLAN 11.
PC4 belongs to VLAN 22.
There are several correct methods that will enable you to learn which VLAN each PC belongs
to. The best method is to issue the ipconfig /all command on each PC host to determine the
computer’s MAC address. Below is sample output for PC1; the MAC address in your output might
vary:
Boson BOSS 5.0 IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
IP Address. . . . . . . . . . . . : 192.168.101.11
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.101.1
Description . . . . . . . . . . . : Realtek RTL8139/810X Family PCI Fast Ethernet NIC
Physical Address. . . . . . . . . : 000C.1380.3538
DHCP Enabled. . . . . . . . . . . : No
Link-local IPv6 Address . . . . . : FE80::20C:13FF:FE80:3538%1
DHCPv6 IAID . . . . . . . . . . . : 51866776888
DHCPv6 Client DUID. . . . . . . . : 00-30-30-30-43-31-33-38-30-33-35-33-38
DNS Servers . . . . . . . . . . . :
(continued on next page)
6 Boson NetSim Lab Manual
(continued from previous page)
The MAC address of PC1 in the sample output is 000C.1380.3538, which is displayed next to
Physical Address in the sample output from the ipconfig /all command issued on PC1.
You should then issue the show mac-address-table command on Switch1. The show mac-
address-table command maps each MAC address to a specific VLAN. Below is sample output for
Switch1. The MAC addresses in your output might vary.
Switch1#show mac-address-table
Mac Address Table
------------------------------------------
Vlan Mac Address Type Ports
---- ----------- ---- -----
22 000C.2638.6059 DYNAMIC Fa0/4
11 000C.1380.3538 DYNAMIC Fa0/3
1 000C.7805.1951 DYNAMIC Fa0/2
1 000C.3962.6232 DYNAMIC Fa0/1
1 000C.3962.6233 DYNAMIC Fa0/1
Total Mac Addresses for this criterion: 5
In this example, the show mac-address-table command output enables you to determine that the
MAC address 000C.1380.3538 is mapped to the FastEthernet 0/3 port on Switch1, which is in VLAN
11. Therefore, PC1 belongs to VLAN 11. Issuing the ipconfig /all command on PC2 will enable you
to determine that PC2 has a MAC address of 000C.2638.6059 and that PC2 is connected to the
FastEthernet 0/4 port on Switch1, which is in VLAN 22. Therefore, PC2 belongs to VLAN 22.
B. Examine Network Connectivity
1. Yes, the ping from PC1 to PC2 (192.168.102.22) is successful.
C:>ping 192.168.102.22
2. No, PC1 and PC2 are in different VLANs. PC1 is in VLAN 11, and PC2 is in VLAN 22.
The two VLANs are configured with different IP network addresses. The ping is successful because
PC1 determines that the destination IP address for PC2 is in a different network and therefore
forwards the traffic to its default gateway, Router1, for delivery. Router1 has subinterfaces in each
VLAN, connected by a trunk link to Switch1. Router1 handles inter-VLAN routing for the simulated
network.
3. Yes, the ping from PC1 to PC3 (192.168.101.13) is successful, because both PC1 and PC3 belong
to the same VLAN and are configured with the same network address. PC1 determines that PC3 is
in the same network and sends its traffic to PC3 directly.
C:>ping 192.168.101.13
7 Boson NetSim Lab Manual
Task 2: Configure ACLs
A. Review Characteristics of ACLs
1. ACLs can be used to permit or deny traffic passing through a router.
2. Standard ACLs can filter traffic based on only the source IP address. Extended ACLs can filter traffic
based on source or destination IP addresses. In addition, extended ACLs can filter traffic based on
the type of traffic.
3. Standard ACLs are identified by a numeric ID from 1 through 99 and from 1300 through 1999.
Extended ACLs are identified by a numeric ID from 100 through 199 and from 2000 through 2699.
4. An access list can consist of multiple access list statements. These statements are evaluated from
top to bottom, so the sequence in which the statements are entered is very important. As soon as a
packet matches an access list statement, it is either forwarded or dropped, depending upon whether
the access list statement allows or denies matched packets.
5. The implicit deny rule, which is added to the end of every access list, means that if a packet has not
already been allowed or denied by one of the statements in the access list, it is automatically denied.
B. Prepare for ACLs
1. PC1 and PC3 connect to the 192.168.101.0/24 network.
2. PC2 and PC4 connect to the 192.168.102.0/24 network.
3. When PC1 sends traffic to PC2, Router1 is the device on the network responsible for moving this
traffic between networks. PC1 must first forward this traffic to its default gateway, 192.168.101.1,
which is the IP address of subinterface FastEthernet 0/0.11 on Router1.
4. When PC1 sends traffic to PC4, Router1 is the device on the network responsible for moving this
traffic between networks. PC1 must first forward this traffic to its default gateway, 192.168.102.1,
which is the IP address of subinterface FastEthernet 0/0.22 on Router1.
5. Telnet uses Transmission Control Protocol (TCP) as its Transport layer protocol.
6. Ping uses ICMP as its transport Tayer protocol.
C. Implement an Extended ACL for Traffic Flowing from VLAN 11 to VLAN 22
1. Router1 is responsible for moving traffic between the two VLANs in this simulated network.
2. To accomplish the objective in this lab, you will need to create two ACLs. One ACL will control the
flow of traffic from VLAN 11 to VLAN 22, and the other ACL will control the flow of traffic from VLAN
22 to VLAN 11.
8 Boson NetSim Lab Manual
3. On Router1, issue the following command to create an entry for ACL 111 that allows Ping traffic from
PC1 to reach any host on VLAN 22:
Router1(config)#access-list 111 permit icmp host 192.168.101.11 192.168.102.0 0.0.0.255 echo
The echo keyword in the access list statement will match echo request messages in ICMP packets.
When a source host attempts to ping a destination host, the source host sends an ICMP echo
request message to determine whether a destination host is reachable. If the destination host is
reachable, the destination host sends an ICMP echo reply message to the source host. An echo
reply message indicates that the destination host successfully received an echo request message.
ICMP echo message types are permitted in ACL 111, and ACL 111 is associated with the
FastEthernet 0/0.11 interface on Router1 in the inbound direction; therefore, Router1 will not drop
incoming ICMP echo request packets and Router1 will allow echo reply messages to be sent to the
initiating host specified in the access-list 111 statement.
4. On Router1, issue the following command to create an entry for ACL 111 that allows Telnet traffic
from PC1 to reach any host on VLAN 22:
Router1(config)#access-list 111 permit tcp host 192.168.101.11 192.168.102.0 0.0.0.255 eq telnet
5. On Router1, issue the following command to create an entry for ACL 111 that denies any traffic other
than Telnet and Ping traffic from VLAN 11 to VLAN 22:
Router1(config)#access-list 111 deny ip 192.168.101.0 0.0.0.255 192.168.102.0 0.0.0.255
6. On Router1, issue the following command to create an entry for ACL 111 that permits any other
traffic from VLAN 11 to reach any destination other than VLAN 22:
Router1(config)#access-list 111 permit ip 192.168.101.0 0.0.0.255 any
7. The subinterface FastEthernet0/0.11 on Router1, which has the IP address 192.168.101.1, is
configured as the default gateway for the PC hosts in VLAN 11; therefore, this interface will receive
traffic from the PC hosts in VLAN 11. You should issue the ipconfig /all command on PC1 and PC2
to determine the IP address of their default gateway. Issuing the show ip interface brief command
on Router1 will enable you to determine which interface the IP address is assigned to.
8. From the perspective of Router1, traffic will be flowing in, toward FastEthernet 0/0.11.
9. On Router1, issue the following commands to assign ACL 111 to the interface in the inbound
direction:
Router1(config)#interface fastethernet 0/0.11
Router1(config-subif)#ip access-group 111 in
9 Boson NetSim Lab Manual
D. Implement an Extended ACL for Traffic Flowing from VLAN 22 to VLAN 11
1. On Router1, issue the following command to create an entry for ACL 122 that allows Ping reply
traffic from any host on VLAN 22 to flow back to PC1:
Router1(config)#access-list 122 permit icmp 192.168.102.0 0.0.0.255 host 192.168.101.11 echo-reply
The echo-reply keyword in the access list statement will match echo reply message types in ICMP
packets.
If ACL 122 is associated with FastEthernet 0/0.22 on Router1 in the outbound direction, Router1 will
not drop echo reply messages sent in response to pings that were initiated by internal hosts and
were sent to the host IP address specified in the access-list 122 statement.
2. On Router1, issue the following command to create an entry for ACL 122 that allows Telnet traffic
from any host on VLAN 22 to reach PC1:
Router1(config)#access-list 122 permit tcp 192.168.102.0 0.0.0.255 host 192.168.101.11 eq telnet
3. On Router1, issue the following command to create an entry for ACL 122 that denies any traffic other
than Telnet and Ping traffic from VLAN 22 to VLAN 11:
Router1(config)#access-list 122 deny ip 192.168.102.0 0.0.0.255 192.168.101.0 0.0.0.255
4. On Router1, issue the following command to create an entry for ACL 122 that permits any other
traffic from VLAN 22 to reach any destination other than VLAN 11:
Router1(config)#access-list 122 permit ip 192.168.102.0 0.0.0.255 any
5. The subinterface FastEthernet 0/0.22 on Router1, which has the IP address 192.168.102.1, is
configured as the default gateway for the PC hosts in VLAN 22; this interface will receive traffic from
the PC hosts in VLAN 22.
6. From the perspective of Router1, traffic will be flowing in, toward FastEthernet 0/0.22.
7. On Router1, issue the following commands to assign ACL 122 to the interface in the inbound
direction:
Router1(config)#interface fastethernet 0/0.22
Router1(config-subif)#ip access-group 122 in
10 Boson NetSim Lab Manual
Task 3: Verify ACLs
A. Verify Ping
1. Yes, the ping from PC1 to PC3 (192.168.101.13) is successful.
C:>ping 192.168.101.13
The flow of traffic from PC1 to PC3 is not affected by the ACLs on Router1. This is because PC1 and
PC3 are in the same VLAN and are configured with IP addresses in the same network; therefore,
this traffic never passes through Router1.
2. Yes, the pings from PC1 to PC2 (192.168.102.22) and PC4 (192.168.102.24) are successful.
C:>ping 192.168.102.22
C:>ping 192.168.102.24
Access list 111 is configured to allow ping traffic (ICMP echo) from PC1 (192.168.101.11) to the
192.168.102.0/24 network. PC2 and PC4 are configured with IP addresses that fall within the
192.168.102.0/24 network; therefore, the ping traffic is permitted by the access list.
3. No, the pings from PC3 to PC2 (192.168.102.22) and PC4 (192.168.102.24) fail.
C:>ping 192.168.102.22
C:>ping 192.168.102.24
Ping traffic sent from PC3 to PC2 and PC4 is forwarded to Router1, the default gateway for PC3,
because PC2 and PC4 are configured with IP addresses that are not in the same network as PC3.
ACL 111 is configured to allow ping traffic (ICMP echo) from only host PC1, not from the entire
192.168.101.0/24 network; therefore, these packets are dropped when the ping is initiated from PC3
but are forwarded when the ping is initiated from PC1.
B. Verify Telnet
1. Yes, a Telnet connection from PC1 to FastEthernet 0/0.22 of Router1 (192.168.102.1) is successful.
C:>telnet 192.168.102.1
Password:cisco
Router1>exit
[Connection to 192.168.102.1 closed by foreign host]
C:>
ACL 111 is configured to allow Telnet traffic flowing into FastEthernet 0/0.11 as long as this traffic is
coming from PC1 and is addressed to a host in the 192.168.102.0/24 network.
11 Boson NetSim Lab Manual
2. No, a Telnet connection from PC3 to the FastEthernet 0/0.22 of Router1 fails.
C:>telnet 192.168.102.1
Trying 192.168.102.1 ...
% Destination unreachable; gateway or host down
C:>
ACL 111 is configured to allow Telnet traffic flowing into interface FastEthernet 0/0.11 only if the
traffic is coming from PC1 and is addressed to a host in the 192.168.102.0/24 network. In this case,
the traffic is not coming from PC1 but is instead coming from PC3; therefore, the traffic is dropped
and the Telnet connection fails.
Copyright © 1996–2017 Boson Software, LLC. All rights reserved. NetSim software and documentation are protected by copyright law.
12 Boson NetSim Lab Manual
Sample Configuration Script
Router1
Router1#show running-config
Building configuration...
Current configuration : 1545 bytes
!
Version 15.b
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname Router1
enable secret 5 $1$lYSY$Ai2eZ8KpUCL9ptJCN1c41w
!
ip subnet-zero
!
ip cef
no ip domain-lookup
!
interface Serial0/0
no ip address
no ip directed-broadcast
!
interface FastEthernet0/0
encapsulation dot1q 1
ip address 192.168.100.1 255.255.255.0
no ip directed-broadcast
!
interface FastEthernet0/0.11
encapsulation dot1q 11
ip address 192.168.101.1 255.255.255.0
ip access-group 111 in
!
interface FastEthernet0/0.22
encapsulation dot1q 22
ip address 192.168.102.1 255.255.255.0
ip access-group 122 in
!
interface FastEthernet0/1
no ip address
no ip directed-broadcast
shutdown
!
ip classless
no ip http server
!
access-list 111 permit icmp host 192.168.101.11 192.168.102.0 0.0.0.255 echo
access-list 111 permit tcp host 192.168.101.11 192.168.102.0 0.0.0.255 eq telnet
access-list 111 deny ip 192.168.101.0 0.0.0.255 192.168.102.0 0.0.0.255
access-list 111 permit ip 192.168.101.0 0.0.0.255 any
access-list 122 permit icmp 192.168.102.0 0.0.0.255 host 192.168.101.11 echo-reply
access-list 122 permit tcp 192.168.102.0 0.0.0.255 host 192.168.101.11 eq telnet
access-list 122 deny ip 192.168.102.0 0.0.0.255 192.168.101.0 0.0.0.255
access-list 122 permit ip 192.168.102.0 0.0.0.255 any
!
line con 0
line aux 0
line vty 0 4
login
password cisco
!
no scheduler allocate
end
13 Boson NetSim Lab Manual
Vous aimerez peut-être aussi
- Lab 1Document11 pagesLab 1Tomas Rodriguez RamirezPas encore d'évaluation
- ACL Practice Lab 3Document8 pagesACL Practice Lab 3LGBT Việt NamPas encore d'évaluation
- ACL Practice Lab 2Document7 pagesACL Practice Lab 2LGBT Việt NamPas encore d'évaluation
- ACL Practice Lab 1Document8 pagesACL Practice Lab 1LGBT Việt NamPas encore d'évaluation
- 2 Basic Switch ConfigurationDocument9 pages2 Basic Switch ConfigurationNAHUM ZERAH SACAYPas encore d'évaluation
- Lab 5Document12 pagesLab 5Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 9Document16 pagesLab 9Tomas Rodriguez RamirezPas encore d'évaluation
- ESwitching PTAct 2 5 1-Answer 3Document10 pagesESwitching PTAct 2 5 1-Answer 3Hari HermanPas encore d'évaluation
- Lab 2 Configuring Basic Routing and Switching PDFDocument11 pagesLab 2 Configuring Basic Routing and Switching PDFDennis Masuku MacfeePas encore d'évaluation
- 3.1.4 Applying Basic Switch SecurityDocument6 pages3.1.4 Applying Basic Switch SecuritysalsalolitaPas encore d'évaluation
- Take Assessment - Enetwork Practice Final Exam - Ccna Exploration: Network Fundamentals (Version 4.0)Document18 pagesTake Assessment - Enetwork Practice Final Exam - Ccna Exploration: Network Fundamentals (Version 4.0)Korisne SlikePas encore d'évaluation
- Lab - Configuring and Verifying VTY RestrictionsDocument6 pagesLab - Configuring and Verifying VTY Restrictionsdaniel ramirezPas encore d'évaluation
- Ccna1 V7 Cap 1-3Document6 pagesCcna1 V7 Cap 1-3ask_gaby100% (1)
- CCNA 1 Chapter 2 Exam Answer v5 & v5.02 2015 (100%) : March 21, 2015 byDocument14 pagesCCNA 1 Chapter 2 Exam Answer v5 & v5.02 2015 (100%) : March 21, 2015 byAmine MaachePas encore d'évaluation
- ESwitching Lab 1 3 1Document12 pagesESwitching Lab 1 3 1Derek Ang Yew PinPas encore d'évaluation
- Lab For Extended AclsDocument5 pagesLab For Extended Aclscasilan_90Pas encore d'évaluation
- Lab1: Learning About Switches: 1 ObjectivesDocument4 pagesLab1: Learning About Switches: 1 ObjectivesPrinoPas encore d'évaluation
- NET201 Lab Experiment # 3 - Configuring Per-Interface Inter-VLAN RoutingDocument13 pagesNET201 Lab Experiment # 3 - Configuring Per-Interface Inter-VLAN RoutingJasmin Cez MabilanganPas encore d'évaluation
- Migrating To H3C Lab Guide Lab01 Basic Config v2.8Document32 pagesMigrating To H3C Lab Guide Lab01 Basic Config v2.8Vargas AlvaroPas encore d'évaluation
- Ccna 1 Final - WWW - MediafireDocument20 pagesCcna 1 Final - WWW - MediafireAntónio MarquesPas encore d'évaluation
- Prctice Final Exam Ccna1Document24 pagesPrctice Final Exam Ccna1Kristo RadionPas encore d'évaluation
- 1 - Configuration Demo I PDFDocument8 pages1 - Configuration Demo I PDFPriyanka BeheraPas encore d'évaluation
- Lab 2.5.1C: Basic Switch Configuration: Lab. Session: Name: Cityu Id: Group No.: DateDocument14 pagesLab 2.5.1C: Basic Switch Configuration: Lab. Session: Name: Cityu Id: Group No.: DateLawrenceLamPas encore d'évaluation
- CCNA Lab M4 5.5.1Document6 pagesCCNA Lab M4 5.5.1vadancorneliuPas encore d'évaluation
- Ccna Acl Lab: School of Information Studies Syracuse University Created by 4/22/2008 By: James Benninger Used in CCNADocument18 pagesCcna Acl Lab: School of Information Studies Syracuse University Created by 4/22/2008 By: James Benninger Used in CCNAFaby ReveloPas encore d'évaluation
- Lab 1.3.1Document12 pagesLab 1.3.1Alondra CarmonaPas encore d'évaluation
- IP Access Lists: Objective Lab TopologyDocument5 pagesIP Access Lists: Objective Lab TopologyTomas Rodriguez RamirezPas encore d'évaluation
- Final 3Document22 pagesFinal 3Tạ Thịnh PhátPas encore d'évaluation
- Packet Tracer 1.3.1Document11 pagesPacket Tracer 1.3.13qtrtymPas encore d'évaluation
- CCNA 1 Final v5.0 Exam Answers 2015 100Document50 pagesCCNA 1 Final v5.0 Exam Answers 2015 100ovidiu0702Pas encore d'évaluation
- LabDocument11 pagesLableonora KrasniqiPas encore d'évaluation
- Lab 11.2.1a Configuring Standard Access Lists: ObjectiveDocument45 pagesLab 11.2.1a Configuring Standard Access Lists: ObjectivetieuphapsPas encore d'évaluation
- CCNA1 v5 + v5.02 Final Exam Answers: LAN MAN WlanDocument37 pagesCCNA1 v5 + v5.02 Final Exam Answers: LAN MAN WlanIon CaramanPas encore d'évaluation
- 7.2.3.4 Lab - Configuring and Verifying VTY Restrictions Act 16Document8 pages7.2.3.4 Lab - Configuring and Verifying VTY Restrictions Act 16ErvinYanoPas encore d'évaluation
- NET201: Networking With Lab 2: Configuring Per-Interface Inter-VLAN RoutingDocument42 pagesNET201: Networking With Lab 2: Configuring Per-Interface Inter-VLAN RoutingMatthew Sta. MonicaPas encore d'évaluation
- 7.2.3.4 Lab - Configuring and Verifying VTY Restrictions WB PDFDocument7 pages7.2.3.4 Lab - Configuring and Verifying VTY Restrictions WB PDFAriana Olea CortezPas encore d'évaluation
- Lab 2.5.1 - Basic Switch ConfigurationDocument15 pagesLab 2.5.1 - Basic Switch ConfigurationSarah Manich50% (2)
- Lab 5 - Basic Switch ConfigurationDocument13 pagesLab 5 - Basic Switch ConfigurationPES MASTER GAMEPLAYSPas encore d'évaluation
- 11 5 1Document56 pages11 5 1Mario Alejandro Godoy PatiñoPas encore d'évaluation
- Lab 5.6.2 Challenge RIP ConfigurationDocument4 pagesLab 5.6.2 Challenge RIP ConfigurationJosue Isahu Sanchez MedinaPas encore d'évaluation
- 4.4.2 LabDocument5 pages4.4.2 LabLHPas encore d'évaluation
- D 3 Challenge Acl LabDocument5 pagesD 3 Challenge Acl LabAmadouMalickMouamfonMoumbagnaPas encore d'évaluation
- CCENT Practice Certification Exam # 2Document21 pagesCCENT Practice Certification Exam # 2Luang Kai LiangPas encore d'évaluation
- Lab 4 1 6Document6 pagesLab 4 1 6HamzaSpahijaPas encore d'évaluation
- Lab 8 Packet Tracer VersionDocument6 pagesLab 8 Packet Tracer VersionOsGuIsPas encore d'évaluation
- Ccna Answers by AbhishekkunalDocument23 pagesCcna Answers by AbhishekkunalAbhishek KunalPas encore d'évaluation
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationD'EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationPas encore d'évaluation
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksD'EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksPas encore d'évaluation
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkD'EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkPas encore d'évaluation
- Next-Generation switching OS configuration and management: Troubleshooting NX-OS in Enterprise EnvironmentsD'EverandNext-Generation switching OS configuration and management: Troubleshooting NX-OS in Enterprise EnvironmentsPas encore d'évaluation
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3D'EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Pas encore d'évaluation
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingD'EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingPas encore d'évaluation
- Exploring BeagleBone: Tools and Techniques for Building with Embedded LinuxD'EverandExploring BeagleBone: Tools and Techniques for Building with Embedded LinuxÉvaluation : 4 sur 5 étoiles4/5 (1)
- First Hop Redundancy Protocol: Network Redundancy ProtocolD'EverandFirst Hop Redundancy Protocol: Network Redundancy ProtocolPas encore d'évaluation
- PLC Programming from Novice to Professional: Learn PLC Programming with Training VideosD'EverandPLC Programming from Novice to Professional: Learn PLC Programming with Training VideosÉvaluation : 5 sur 5 étoiles5/5 (1)
- LEARN MPLS FROM SCRATCH PART-A: A Beginner's Guide to Next Level of NetworkingD'EverandLEARN MPLS FROM SCRATCH PART-A: A Beginner's Guide to Next Level of NetworkingPas encore d'évaluation
- Lab 3Document5 pagesLab 3Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 5Document12 pagesLab 5Tomas Rodriguez RamirezPas encore d'évaluation
- MikroTik Routers and Wireless - Products - hAP Ac Lite TCDocument7 pagesMikroTik Routers and Wireless - Products - hAP Ac Lite TCTomas Rodriguez RamirezPas encore d'évaluation
- CIS Cisco IOS 15 Benchmark v4.0.0Document151 pagesCIS Cisco IOS 15 Benchmark v4.0.0Sandro MeloPas encore d'évaluation
- Lab 1Document11 pagesLab 1Tomas Rodriguez RamirezPas encore d'évaluation
- Dgii F 606 02600930602 201905Document1 pageDgii F 606 02600930602 201905Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 7Document8 pagesLab 7Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 4Document6 pagesLab 4Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 9Document16 pagesLab 9Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 1Document10 pagesLab 1Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 6 PDFDocument8 pagesLab 6 PDFTomas Rodriguez RamirezPas encore d'évaluation
- Lab 1Document5 pagesLab 1Tomas Rodriguez RamirezPas encore d'évaluation
- OSPF Authentication II: Objective Lab TopologyDocument9 pagesOSPF Authentication II: Objective Lab TopologyTomas Rodriguez RamirezPas encore d'évaluation
- Lab 3Document16 pagesLab 3Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 4Document8 pagesLab 4Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 2Document13 pagesLab 2Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 4Document8 pagesLab 4Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 2Document9 pagesLab 2Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 3Document16 pagesLab 3Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 8Document6 pagesLab 8Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 1Document19 pagesLab 1Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 3Document4 pagesLab 3Tomas Rodriguez RamirezPas encore d'évaluation
- IP Access Lists: Objective Lab TopologyDocument5 pagesIP Access Lists: Objective Lab TopologyTomas Rodriguez RamirezPas encore d'évaluation
- Lab 7Document10 pagesLab 7Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 3Document10 pagesLab 3Tomas Rodriguez RamirezPas encore d'évaluation
- Lab 4Document14 pagesLab 4Tomas Rodriguez RamirezPas encore d'évaluation
- Disponible en JM Datasheet Tester CCTV IpDocument2 pagesDisponible en JM Datasheet Tester CCTV IpTomas Rodriguez RamirezPas encore d'évaluation
- Lab 2Document11 pagesLab 2Tomas Rodriguez RamirezPas encore d'évaluation
- JN0-102 2Document31 pagesJN0-102 2KarthikPas encore d'évaluation
- Module 4: Inter-VLAN Routing: Instructor MaterialsDocument44 pagesModule 4: Inter-VLAN Routing: Instructor Materialsgiovannyram8339100% (1)
- Dual ConnectivityDocument73 pagesDual ConnectivitytelcoPas encore d'évaluation
- Iwc DumpDocument66 pagesIwc DumpYolenny AcostaPas encore d'évaluation
- Spark LED Light-RubyDocument14 pagesSpark LED Light-Rubyf136495Pas encore d'évaluation
- Questions On MAC PropertyDocument5 pagesQuestions On MAC PropertySiddhant AltPas encore d'évaluation
- HPing TutorialDocument10 pagesHPing TutorialAsmeromPas encore d'évaluation
- MPLS ConceptsDocument30 pagesMPLS Conceptssyztemlabs100% (37)
- Seminar Report On Integrated Services Digital Network (ISDN)Document26 pagesSeminar Report On Integrated Services Digital Network (ISDN)pepgutsy100% (1)
- Using Zero Touch ProvisioningDocument6 pagesUsing Zero Touch ProvisioningMudasir AhmedPas encore d'évaluation
- Vivekananda Institute of Professional StudiesDocument25 pagesVivekananda Institute of Professional Studiesman ironPas encore d'évaluation
- 02 IK IESYS e Introduction To Industrial EthernetDocument32 pages02 IK IESYS e Introduction To Industrial Ethernetsergio_lindau892Pas encore d'évaluation
- Alcatel-Lucent Omniswitch 6860: Stackable Lan Switches For Mobility, Iot and Network AnalyticsDocument17 pagesAlcatel-Lucent Omniswitch 6860: Stackable Lan Switches For Mobility, Iot and Network AnalyticsRobison Meirelles juniorPas encore d'évaluation
- GSM RR Call FlowsDocument4 pagesGSM RR Call Flowsgalal_a2005Pas encore d'évaluation
- # cs425 - SlidesDocument96 pages# cs425 - SlidesAbhishek AnandPas encore d'évaluation
- 3 G NotesDocument44 pages3 G NotesIrfan KhanPas encore d'évaluation
- Huawei LTE ENodeB CabinetsDocument41 pagesHuawei LTE ENodeB CabinetsSyed Mohsin Ghani100% (1)
- RNL3 LteDocument13 pagesRNL3 LteHoney CharnaliaPas encore d'évaluation
- IP Packet? 2 3 4 1: 1. How Many IP Addresses Can One Find in The Header of AnDocument8 pagesIP Packet? 2 3 4 1: 1. How Many IP Addresses Can One Find in The Header of AnMuhammad Sutra MaulanaPas encore d'évaluation
- Huawei CloudEngine S5731-S BrochureDocument18 pagesHuawei CloudEngine S5731-S BrochurePaulo DinizPas encore d'évaluation
- Chainess Dump - Mode PDFDocument99 pagesChainess Dump - Mode PDFMamaru Nibret DesyalewPas encore d'évaluation
- Catalyst 4500 Series Switch Cisco IOS Software Config GuideDocument570 pagesCatalyst 4500 Series Switch Cisco IOS Software Config Guideraj_rp2Pas encore d'évaluation
- BMS Automation Protocol Converter: Indications PowerDocument3 pagesBMS Automation Protocol Converter: Indications PowerRAJIV KUMARPas encore d'évaluation
- 5.4.12 Packet Tracer - Configure Extended IPv4 ACLs - Scenario 1Document5 pages5.4.12 Packet Tracer - Configure Extended IPv4 ACLs - Scenario 1WerrtyPas encore d'évaluation
- Computer Network - RoutingDocument5 pagesComputer Network - RoutingSheba ParimalaPas encore d'évaluation
- 3GPP TS 23.401: Technical SpecificationDocument418 pages3GPP TS 23.401: Technical SpecificationDani SusantoPas encore d'évaluation
- Ms/Me BSC VLR HLR MSC SMSC UssdcDocument5 pagesMs/Me BSC VLR HLR MSC SMSC UssdcДанил ДробицкийPas encore d'évaluation
- PRS Performance Report Reference (V100R017 - 01) (PDF) - enDocument1 266 pagesPRS Performance Report Reference (V100R017 - 01) (PDF) - enHumberto Jose Arias Barros100% (1)
- Chapter 9 WNDocument36 pagesChapter 9 WNAla'a HassanPas encore d'évaluation
- Dell EMC Networking - QRG - Data CenterDocument2 pagesDell EMC Networking - QRG - Data CenterCristiano GuedesPas encore d'évaluation