Académique Documents
Professionnel Documents
Culture Documents
Pri NT On L Y: Hardware
Transféré par
satrio ing bayuTitre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Pri NT On L Y: Hardware
Transféré par
satrio ing bayuDroits d'auteur :
Formats disponibles
Hardware mass storage: Better than footlockers: battlefield data storage
Solid-state drives meet
military storage
security requirements
By Gary Drossel
consumer applications, military embedded
systems require data to be rendered invalid
y
l
and inaccessible when the storage device is
n
improperly removed from the host system
for which it was intended. The host system
O
must maintain ultimate control over security
t
While many designers still utilize consumer-grade storage in algorithms to protect data and prevent IP theft. These algorithms
n
military applications, these solutions offer sub-par security can be as simple as ensuring that the correct storage product is
ri
and insufficient reliability in the long-term compared to in the host, or as intricate as tying the software IP and mission
solid-state storage technologies developed for use in critical data directly to the storage device. Since the security algorithm
P
environments. Solid-state drives offer robust, customizable, and is host-centric and not device-centric, the algorithm itself can
e
scalable security algorithms that, when combined with inherent be completely proprietary and therefore much more secure.
l
environmental ruggedness, make solid-state drives ideal for This security platform – combined with mechanical scalability,
g
military embedded systems. low power consumption, and long product life cycle – makes
n
i
solid-state drives very attractive to military embedded system
A captain in the Dutch Air Force leaves a portable hard drive in designers.
S
his rental car. The contents: details of reconnaissance missions
r
and security measures for the 1,200-man Dutch military presence Examining the considerations
o
in Afghanistan. The drive, which had no security encryption, is Storage devices for military embedded systems must meet a
F
later found by two young men and copied onto a computer. daunting number of criteria in addition to protecting mission or
application data and software intellectual property. Data integrity
The data is later returned to the officer, but incidents such as is paramount, and the drive itself must not be susceptible to corrup-
this one demonstrate all too clearly the need for the security of tion due to power disturbances. The equipment needs to be highly
military systems worldwide. portable, so the technology must have low power consumption
characteristics and must be small and light enough to fit seamlessly
Designers must come to understand that the security require- in a vehicle or aircraft, or be carried by an individual soldier. Such
ments of military embedded systems are fundamentally differ- systems must be able to handle extreme environmental conditions
ent from those of consumer electronic devices. In contrast to such as shock, vibration, and altitude, and should tolerate a wide
Market concern Hard drive Solid-state drive Flash card
Corruption due to power Requires enhanced protection
Adequate Poor
disturbances circuitry
Product life cycle Less than one year Multiple years Less than one year
Environmental and mechanical Very good – write/erase endurance Write/erase endurance less than
Wear-out
concerns exceeds 2 M cycles 10 K cycles
Possible password protection via High-end drives provide several Possible password protection via
Security ATA specifications. No sweep, security options such as password CompactFlash specifications. No
scrub, or purge protection, sweep, scrub, and purge sweep, scrub, or purge
Power consumption > 2.5 W > 2.5 W <1W
Mechanical dimensions 2.5" 2.5" CF
Table 1
Military Embedded Systems ©2007 OpenSystems Publishing. Not for Distribution
mass storage: Better than footlockers: battlefield data storage Hardware
range of temperatures. There is a need for a multiple-year product computers require features such as ultra-fast data erasure and
life cycle and high endurance rating to make sure the drives oper- sanitization, data zones with independent security parameters,
ate reliably for several years. and secure areas for designers to access and create their own
encryption and decryption keys. These features protect appli-
How different forms of storage stack up cation data and software IP from theft or from falling into the
With all these considerations, it is not surprising that storage wrong hands as illustrated in the 2001 incident where a Navy
products originally designed for the consumer electronics market surveillance plane collided with a Chinese jet and was forced to
do not in general meet the needs of military embedded systems. make an emergency landing in China.
Table 1 illustrates the design trade-offs of traditional storage
solutions for military embedded systems. Military-focused OEMs want to perform two key functions in
their application to protect mission data and software IP. First,
y
As the table shows, solid-state drives offer more advanced there is a need to ensure that the end user is utilizing a qualified
l
security options, better environmental performance, and storage device in the system. In some instances, perhaps for
n
longer product life cycles than hard disk drives, but designers security, warranty, or service purposes, the OEM needs to know
O
must be careful when choosing these solutions. Traditional that the specific drive originally shipped with the equipment is
solid-state storage solutions designed to satisfy high capacity indeed still in the system. This type of technology prevents a
t
and advanced data security requirements have been mechani- rogue storage device from entering a secured system. Without
n
i
cally confined to 2.5"or 3.5" hard drive form factors. This this technology, it is possible to place a similar product with
r
is not only because of the number of storage components – the same part number from the same vendor into a system. That
P
usually NAND flash – required to achieve the desired capacity, similar part number may contain incorrect or malicious data that
but also because of the physical size of the microprocessor and may or may not be detected before it is too late. With the type of
e
l
associated logic used to provide the host system interface and technology described here, the system would not even boot and
g
the solid-state memory management algorithms. These circuits the chances for errors (or worse) would be greatly diminished.
n
have neither been able to scale to smaller form factors nor have Second, there is a need to tie mission data and software IP to the
i
they been able to achieve power consumption rates less than the specific drive for which they were intended to prevent theft and
S
typical 2.5 W of rotating hard drives. ensure software integrity.
or
Applications requiring smaller mechanical form factors such as
CompactFlash or PC cards used in consumer applications present
One possible method to accomplish this is for the drive to reserve
a specific area that is only accessible to the OEM through a pro-
F
their own set of challenges. While these products offer relatively prietary command. That area could store specific host system
good environmental performance and consume little power – in information so that when the drive boots up, the host reads the
general, less than 1 W – there are still concerns about product life data in this secure area and looks to match that data with a host
cycles, endurance, and security capabilities. serial number or other identifier. If there is no match, the drive is
inaccessible. That area could also store data that the host could
In addition, most drives and flash cards customarily designed for use as the key to its proprietary encryption algorithm.
use in consumer applications do not provide security technology
such as fast erase or purge that will prohibit data from falling Preventing data from falling into the wrong hands
into the wrong hands. In addition, their password protection Data in a hard drive, a solid-state drive, or a flash card is stored in
algorithms may not be flexible enough to allow the host system 512-byte increments called sectors. Each sector also has associ-
to implement its desired algorithm. ated with it a 16-byte control block as illustrated in Figure 1.
Control blocks store bad block information, error correction, and
The ideal solution for military applica-tions, therefore, is a perhaps some proprietary monitoring information that must be
mechanically scalable, low-power storage solution that is maintained if the drive is to be reused.
impervious to power disturbances,
maintains a long product life cycle,
prevents field failures due to wear-
Sector
{
out, and provides access to low-level
security hooks so the host can define
CTRL
CTRL
CTRL
its own security algorithm.
USER USER USER
.....
Security concerns worth
consideration
Many military embed- Sectors: USER = User Data
ded applications re- CTRL = ECC, Bad Block and Other Information
quire advanced security levels. Data re-
corders and wearable and field Figure 1
Military Embedded Systems ©2007 OpenSystems Publishing. Not for Distribution
Hardware mass storage: Better than footlockers: battlefield data storage
Data security features can be initiated via software it certain drawbacks. For one, even badly mutilated drives can
through hardware initiation such as a switch connected still yield useful amounts of data. Another factor is the machinery
directly to the storage device, a vendor-specific command necessary to destroy the drives, which can be very heavy. As with
structure, or through some combina- using heavy magnets, the extra steps of removing the drives from
tion of both. Consideration should be given to their enclosures and inserting them into the machinery for destruc-
the specific implementation and the re-quired drive technol- tion make this more awkward.
ogy. Magnetic media such as hard disks and tape drives
provide the lowest initial price per gigabyte at the expense of The solid-state difference
environmental performance, multi-year product life cycles, Because the physics of solid-state drives are signifi-
and the ability to quickly erase all data on the drive. It can take cantly different from those of their magnetic counterparts,
a matter of hours for large amounts of data to be scrubbed from so is the way solid-state drives write and erase data.
y
magnetic media. Even then, the process needs to be repeated to Figure 2 illustrates a typical floating gate cell in a nonvolatile storage
l
prevent data ghosts or portions of data that remain on the drive component. Charge on the floating gate allows the threshold volt-
n
that can be recovered with specialized equipment. The result is age to be electrically manipulated to levels that represent a logical
O
a very time-intensive process not at all well-suited to the quick- 0 or 1. The process of erasing and writing revolves around tunnel
erase needs of military systems. release and tunnel injection of electrons onto the floating gate.
t
These processes allow no possibility of ghost images on the device
n
i
Attempts were recently made by military contractors after an erase, so no scrubbing technology is required. In fact, the
r
and research institutions to improve erasure time by erase process itself is a form of data scrubbing since the operation
P
exposing drives to extremely high-powered magnets – consists of writing “00”s then “FF”s.
a process also known as degaussing. Researchers made custom
e
l
neodymium iron-boron magnets and special pole pieces made of In addition to the type of media, the system designer must deter-
g
cobalt alloys and used them to erase hard drive data. mine whether or not the drive should be reusable or rendered
n
unrecoverable after executing the fast erase – or sweep. He
i
Erasure time was reduced from several hours to several should also determine what needs to happen with any data that
S
minutes, but other problems presented themselves. For one, may be in non-user-addressable areas like bad blocks or spares.
r
the magnets weighed about 125 pounds, causing severe Standard ATA commands will not be able to address these areas.
limitations in most field applications and virtually eliminating The designer may also want to implement a multiple-step com-
o
possible use in mobile computers. The mechanics of the magnets mand sequence to ensure the erase is not initiated erroneously.
F
proved to be a challenge as well. Mechanisms had to be fabri-
cated that would push the drives past the magnets, further adding Consideration should also be given to providing enough power
to the weight consideration. Users had to physically pull drives to complete the erase, but this may not always be possible. In
out of their enclosures to pass them through the magnetic field. such an event, intelligence must be built into the drive so that an
This added more steps to the data removal and greatly impacted incomplete sweep operation will finish the next time the power
the amount of time required to erase the data. is applied – independent of the host system. The designer must
also model the time required to fully erase the drive based on the
Later improvements on the magnet expos-ure process have brought criticality of the data. Table 2 and Figure 3 illustrate the benefits
the weight down to as little as six pounds, still a consideration for of proprietary commands that can be used to provide a fast erase
wearable computers but better for vehicle and aircraft mounted mechanism versus using standard ATA commands.
equipment. There is still the necessity of
pulling the drives from their enclosures to
place into the mechanism by hand, which can
significantly slow the overall process. IPD Control Gate
Other methods of eliminating data are still
under consideration. In recent years, expos-
SiO2
ing drives to heat-generating ther-mal mate- Floating Gate
rial has been explored. Repeated tests of this
method, however, have not been promising.
Gate Oxide
Evidence has shown that despite the damage Source Drain
a thermal reaction can inflict, amounts of N Channel
data on drives could still be recovered.
The act of physically crushing or shredding a
drive to prevent future use and data access is P Substrate
another alternative, but one that carries with Figure 2
Military Embedded Systems ©2007 OpenSystems Publishing. Not for Distribution
mass storage: Better than footlockers: battlefield data storage Hardware
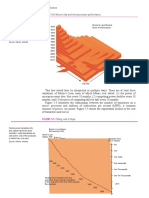
Table 2 contrasts the time it would take to fully erase a storage The future of storage
product by using advanced storage technology (for example, a New technology is continually evolving to meet the stringent
vendor-specific command) and using standard ATA commands. security demands of military embedded systems. The over-
These benchmark times show that data can be erased signifi- whelming success of solid-state drives in the consumer electron-
cantly faster if advanced security technology (such as fast erase ics sector will continue to motivate traditional hard drive users
or sweep) is used. to seek lower-power, more portable, more rugged solutions.
Storage vendors targeting the military
Vendor-specific commands Standard ATA commands embedded system space will continue to
Capacity
(in seconds) (in seconds) leverage the economies of scale this success
32 MB 3.4 5.2 has brought. However, they must provide
64 MB 5.9 10.4 robust, host-centric security methodologies
y
to enable OEMs to define their own security
l
128 MB 2.8 20.7
algorithms, and they must provide the engi-
n
256 MB 3.3 41.4
neering and technical support required to
512 MB 4.9 82.9 (1.38 minutes)
O
ensure a smooth implementation of storage
1 GB 5.9 166.5 (2.77 minutes) into more complex military and embedded
t
2 GB 6.8 333.5 (5.55 minutes) systems.
n
i
4 GB 8.3 671.5 (11.19 minutes)
r
8 GB 13.8 1343.9 (2239 minutes) Gary Drossel, VP of Product
P
16 GB 14.7 2621.7 (43.69 minutes) Planning, joined SiliconSys-
tems in 2004 and is responsible
e
Table 2
l
for managing technical market-
g
40 ing and application engineer-
n
ing for SiliconSystems’ complete product
i
line. A 16-year embedded computing indus-
S
try veteran with a wealth of knowledge con-
30
r
cerning solid-state storage technology, he
has also played a leading role in developing
o
Time (Seconds)
the company’s marketing strategy, including
F
product roll-out and customer introduction.
20
Gary received a BS degree in Electrical and
Computer Engineering from the University
of Wisconsin.
10
SiliconSystems, Inc.
26940 Aliso Viejo Parkway
Aliso Viejo, CA 92656
0 949-900-9400
32 MB 64 MB 128 MB 256 MB 512 MB 1 GB 2 GB 4 GB 8 GB 16 GB
Capacity gdrossel@siliconsystems.com
Standard ATA Vendor Specific
www.siliconsystems.com
Commands Commands
Figure 3
It is also important to understand how the drive implements the
fast erase feature. Some require the entire contents of the drive
to be erased. Others can sweep only the most critical or classified
data by implementing advanced zoning technology. Use of this
technology allows the system designer to be able to partition
the drive into different zones with different security parameters.
One zone could hold standard operating systems or nonclassi-
fied data files. A second zone could be a read-only lookup table,
and a third zone could store classified data. Designers then have
the flexibility to only sweep that zone with the classified data.
Depending on the size of the classified partition versus the size
of the drive, erase times could be cut by more than half.
Military Embedded Systems ©2007 OpenSystems Publishing. Not for Distribution
Vous aimerez peut-être aussi
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (121)
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (588)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (266)
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (399)
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5794)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2259)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (895)
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- Complete Note On Solar Panel InstallationDocument3 pagesComplete Note On Solar Panel InstallationtowfiqeeePas encore d'évaluation
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (73)
- Lithium-Ion Battery Recycling White PaperDocument24 pagesLithium-Ion Battery Recycling White PaperCornelius YosafatPas encore d'évaluation
- 4-2.0L Gasoline EngineDocument187 pages4-2.0L Gasoline EngineMarco Antonio Tomaylla Huamani100% (1)
- True RMS Voltmeter: Instruction ManualDocument124 pagesTrue RMS Voltmeter: Instruction ManualRafa DuverheisenPas encore d'évaluation
- RR210204 Switching Theory & Logic DesignDocument2 pagesRR210204 Switching Theory & Logic DesignsivabharathamurthyPas encore d'évaluation
- Article PowerIowaBlackStartDocument3 pagesArticle PowerIowaBlackStartFabio PascucciPas encore d'évaluation
- MS Samsung Slim Duct PDFDocument2 pagesMS Samsung Slim Duct PDFMacSparesPas encore d'évaluation
- Motorola JLX Line ExtenderDocument2 pagesMotorola JLX Line Extenderjcarlos1960Pas encore d'évaluation
- Nusaresearch Report Internet Browser 03052013Document29 pagesNusaresearch Report Internet Browser 03052013J.R.IsidorePas encore d'évaluation
- 4.LTE Physical Layer ProcedureDocument82 pages4.LTE Physical Layer ProcedureTri Frida Ningrum100% (1)
- Embedded System Design Using ArduinoDocument4 pagesEmbedded System Design Using ArduinobluesbankyPas encore d'évaluation
- User Manual WINOXLR 3-6-14 ProductsDocument59 pagesUser Manual WINOXLR 3-6-14 ProductslotPas encore d'évaluation
- Mitutoyo - Mikroskopy Pomiarowe TM Seria - E14013 - 2015Document4 pagesMitutoyo - Mikroskopy Pomiarowe TM Seria - E14013 - 2015D.T.Pas encore d'évaluation
- KD36XS55 Service ManualDocument211 pagesKD36XS55 Service ManualRob MyersPas encore d'évaluation
- ATPMAT: An Open Source Toolbox For Systematic Creation of EMTP Cases in ATP Using MatlabDocument6 pagesATPMAT: An Open Source Toolbox For Systematic Creation of EMTP Cases in ATP Using MatlabLalo PatoPas encore d'évaluation
- Charles Proteus SteinmetzDocument7 pagesCharles Proteus SteinmetzKelvinPas encore d'évaluation
- Intelligent Alcohol Detection System For CarDocument4 pagesIntelligent Alcohol Detection System For CarNoslen Alois EstradaPas encore d'évaluation
- Genesis Anaesthesia Workstation enDocument8 pagesGenesis Anaesthesia Workstation enOla Gf OlamitPas encore d'évaluation
- Iec-Vit (Vit-B) - Lti (Lti-B) - 10puDocument1 pageIec-Vit (Vit-B) - Lti (Lti-B) - 10puSergio aldoPas encore d'évaluation
- Mitsubishi Electric PURY-P YLM-A1 PURY-EP YLM A Service Manual EngDocument434 pagesMitsubishi Electric PURY-P YLM-A1 PURY-EP YLM A Service Manual Engsantiago quinterosPas encore d'évaluation
- InTouch Bed - EnService Manual FL27Document247 pagesInTouch Bed - EnService Manual FL27Juan CarrascoPas encore d'évaluation
- Работа №1 Переведите: The Concept of Electrical CurrentDocument5 pagesРабота №1 Переведите: The Concept of Electrical CurrentлюдмилаPas encore d'évaluation
- Chapter 3 - Combinational Logic Circuits (Part 1) - Digital ElectronicsDocument12 pagesChapter 3 - Combinational Logic Circuits (Part 1) - Digital ElectronicsRakesh KumarPas encore d'évaluation
- Lifting Operations and Lifting Equipment Regulations 1998 LOLERDocument34 pagesLifting Operations and Lifting Equipment Regulations 1998 LOLERfaiz_oe100% (1)
- Moore's Law and Microprocessor Performance.Document2 pagesMoore's Law and Microprocessor Performance.pmech consultantPas encore d'évaluation
- BE20S03F003 PS-2 Experiment 1 Rahul GadeDocument9 pagesBE20S03F003 PS-2 Experiment 1 Rahul GadeSwapnil Gade007Pas encore d'évaluation
- Datasheet - HK Peb4266t-V12 6428964Document374 pagesDatasheet - HK Peb4266t-V12 6428964ATP TelecomPas encore d'évaluation
- Windjammer and Nautialir Blowers Catalog PDFDocument136 pagesWindjammer and Nautialir Blowers Catalog PDFrtgeorgePas encore d'évaluation
- 1 0 1 1 0 2 0 Rot OssDocument2 pages1 0 1 1 0 2 0 Rot OssEmerging TubePas encore d'évaluation
- UM1709 User Manual: STM32Cube Ethernet IAP ExampleDocument22 pagesUM1709 User Manual: STM32Cube Ethernet IAP ExampleTameClaudioPas encore d'évaluation