Académique Documents
Professionnel Documents
Culture Documents
TLS Protocol Explained
Transféré par
Avinash KhantwalDescription originale:
Titre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
TLS Protocol Explained
Transféré par
Avinash KhantwalDroits d'auteur :
Formats disponibles
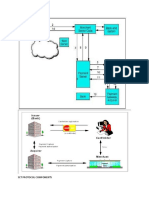
SSL / TLS: Transport Layer Security Protocol
TLS is based on the Secure Socket Layer (SSL), a protocol originally created by Netscape.
One advantage of TLS is that it is application protocol independent.
The TLS protocol runs above TCP/IP and below application protocols such as HTTP or IMAP.
The HTTP running on top of TLS or SSL is often called HTTPS.
Transport Layer Security (TLS) Protocol provides privacy and data integrity between two
communicating applications.
The protocol is composed of two layers: the TLS Record Protocol and the TLS Handshake Protocol.
At the lowest level, layered on top of some reliable transport protocol (TCP) is the TLS Record Protocol.
DEFINITION of 'Secure Electronic Transaction - SET'
Secure electronic transaction (SET) was an early protocol for electronic credit card payments.
As the name implied, SET was used to facilitate the secure transmission of consumer credit
card information via electronic avenues, such as the Internet. SET blocked out the details of
credit card information, thus preventing merchants, hackers and electronic thieves from
accessing this information.
How Secure Electronic Transaction Protocols were Used
The underlying protocols and standards for secure electronic transactions were backed and
supported by Microsoft, IBM, MasterCard, Visa, Netscape, and others. Digital certificates were
assigned to provide the electronic access to funds, whether it was a credit line or bank account.
When a purchase was made electronically, encrypted digital certificates were what let the
customer, merchant, and financial institution complete a verified transaction. Digital certificates
were generated for participants in the transaction, along with matching digital keys that allowed
them to confirm the certificates of the other party.
The algorithms used would ensure that only a party with the corresponding digital key would be
able to confirm the transaction. This way a consumer’s credit card or bank account could be
used without revealing details such as the account number. Thus, SET was a form of security
against account theft, hacking, and other criminal actions.
What encouraged the development of Secure Electronic Transaction
Protocols
The development of SET came in response to the emergence and growth of e-commerce
transactions over networks, especially consumer-driven purchases over the Internet.
Conducting business online was a new, untamed frontier in the mid to late 1990s, and the same
could be said of the varying degrees of security available across the developing networks. The
protocols defined by the secure electronic transaction standards allowed for payment systems
to be developed and used retailers and financial institutions. Merchants and financial institutions
needed to have the appropriate software to properly decrypt and process the digital
transactions.
Vous aimerez peut-être aussi
- Critical Control Formulas Security AssessmentDocument9 pagesCritical Control Formulas Security AssessmentUrai Yc0% (1)
- Ethical HackerDocument196 pagesEthical HackerLayla83% (6)
- Analyst IT Security Sample ResumeDocument3 pagesAnalyst IT Security Sample ResumeSoumya RoutPas encore d'évaluation
- Secure Electronic Transaction (Set Protocol) : Yang Li & Yun WangDocument16 pagesSecure Electronic Transaction (Set Protocol) : Yang Li & Yun Wangsharma@delhiPas encore d'évaluation
- MITRE ATT&CK FrameworkDocument11 pagesMITRE ATT&CK FrameworkchamathmPas encore d'évaluation
- Ch03-Security Part 1. Auditing Operating Systems and NetworksDocument42 pagesCh03-Security Part 1. Auditing Operating Systems and NetworksAlfin Abdullah100% (1)
- E Commerce PDFDocument254 pagesE Commerce PDFAbhiPas encore d'évaluation
- Card Payment Security Using RSADocument23 pagesCard Payment Security Using RSAKaataRanjithkumar100% (2)
- Card Payment Security Using RSADocument23 pagesCard Payment Security Using RSAKaataRanjithkumar100% (1)
- NSC Unit - 3 - 221210 - 134942Document29 pagesNSC Unit - 3 - 221210 - 134942SurenderPas encore d'évaluation
- Secure Electronic TransactionDocument2 pagesSecure Electronic TransactionAnjaliPas encore d'évaluation
- Design and Implementation of Electronic Payment Gateway For Secure Online Payment SystemDocument6 pagesDesign and Implementation of Electronic Payment Gateway For Secure Online Payment SystemEditor IJTSRDPas encore d'évaluation
- E-COMMERCE SECURITY PROTOCOLSDocument17 pagesE-COMMERCE SECURITY PROTOCOLSRahul TiwariPas encore d'évaluation
- Webp - Case Study - 601Document15 pagesWebp - Case Study - 601Prateek KumarPas encore d'évaluation
- Security Protocols: Prepared By-Shobhit Gupta Bca-Vi 718006Document10 pagesSecurity Protocols: Prepared By-Shobhit Gupta Bca-Vi 718006Shoorveer ShahPas encore d'évaluation
- Egerton University COMP 424: Computer SecurityDocument10 pagesEgerton University COMP 424: Computer SecuritySylas Okong'oPas encore d'évaluation
- Role of Cryptography in Securing EcommerceDocument4 pagesRole of Cryptography in Securing EcommerceGanggah Devi MurugayaPas encore d'évaluation
- ECommerce Unit 2Document21 pagesECommerce Unit 2Prabakaran VPas encore d'évaluation
- Security in e - CommerceDocument4 pagesSecurity in e - CommerceAlex T BinoyPas encore d'évaluation
- Explain Business Models, Their Types and Examples of EachDocument8 pagesExplain Business Models, Their Types and Examples of EachShriya JainPas encore d'évaluation
- CryptographyDocument2 pagesCryptographyrsoni soniPas encore d'évaluation
- Assignment Cyber Law E.N 54Document6 pagesAssignment Cyber Law E.N 54Tajamul IslamPas encore d'évaluation
- A Secure Electronic Transaction Payment Protocol DDocument9 pagesA Secure Electronic Transaction Payment Protocol DVukašin KolarevićPas encore d'évaluation
- Unit 4 - Presentation2Document28 pagesUnit 4 - Presentation2parthjethva1407Pas encore d'évaluation
- C C C !"#$# %&' 'CC $ C$ ? ? !Document5 pagesC C C !"#$# %&' 'CC $ C$ ? ? !Anchugam KeerthiPas encore d'évaluation
- Consepp: Convenient and Secure Electronic Payment Protocol Based On X9.59Document10 pagesConsepp: Convenient and Secure Electronic Payment Protocol Based On X9.59Vishwas BijjahalliPas encore d'évaluation
- E Commerce Security Protocols: Presentation By: Jyotsna Mishra Id: 618057 BSC 6 SemesterDocument8 pagesE Commerce Security Protocols: Presentation By: Jyotsna Mishra Id: 618057 BSC 6 SemesterJyotsna MishraPas encore d'évaluation
- Transport Layer Security (TLS)Document14 pagesTransport Layer Security (TLS)svmc bcaPas encore d'évaluation
- Transport Layer Security (TLS)Document14 pagesTransport Layer Security (TLS)svmc bcaPas encore d'évaluation
- UntitledDocument10 pagesUntitledJkuat MSc. P & LPas encore d'évaluation
- Electronic Payment Systems and SecurityDocument21 pagesElectronic Payment Systems and Securitysimbu50Pas encore d'évaluation
- Application Area of CryptographyDocument8 pagesApplication Area of CryptographySanjana Jaiswal100% (2)
- E Commm PDFDocument5 pagesE Commm PDFChamoadh DissanayakePas encore d'évaluation
- Web Security: Secure Socket Layer (SSL)Document6 pagesWeb Security: Secure Socket Layer (SSL)Lokesh Sai Kumar DasariPas encore d'évaluation
- How secure are online payment systemsDocument7 pagesHow secure are online payment systemsso guptaPas encore d'évaluation
- Btech It Ecommerce ReportDocument11 pagesBtech It Ecommerce Reportdishant_kapadiaPas encore d'évaluation
- Issues of Security and Privacy in Electronic Commerce: Part I - Introduction & MotivationDocument24 pagesIssues of Security and Privacy in Electronic Commerce: Part I - Introduction & MotivationziabuttPas encore d'évaluation
- DocumentDocument1 pageDocumentHassan AhmadPas encore d'évaluation
- Cyber Ethics (Part-1)Document23 pagesCyber Ethics (Part-1)anjumjamal8174Pas encore d'évaluation
- Secure Electronic Transactions-SET: January 2017Document23 pagesSecure Electronic Transactions-SET: January 2017Vikas SharmaPas encore d'évaluation
- E&clDocument10 pagesE&clSBAPas encore d'évaluation
- E-Commerce: Technical and Market Approach: UktiDocument4 pagesE-Commerce: Technical and Market Approach: UktiAvisheik Barua 1721158Pas encore d'évaluation
- Topic1 Lesson1to9 IAaS1Document62 pagesTopic1 Lesson1to9 IAaS1Kervi Sanares BacuelPas encore d'évaluation
- Assingnment E CommerceDocument4 pagesAssingnment E CommerceROHIT JAISWALPas encore d'évaluation
- E-Commerce TechnologiesDocument16 pagesE-Commerce TechnologiesGlenn John BalongagPas encore d'évaluation
- 02 AuthenticationDocument20 pages02 AuthenticationSai KrishnaPas encore d'évaluation
- The Security of Electronic BankingDocument11 pagesThe Security of Electronic BankingSUSHILRRAVALPas encore d'évaluation
- Major Issues SummaryDocument36 pagesMajor Issues SummaryRasika BhargavaPas encore d'évaluation
- ETIT NotesDocument14 pagesETIT NotesAniket BinewalePas encore d'évaluation
- An Evaluated Comparison of SSL and SetDocument3 pagesAn Evaluated Comparison of SSL and SetSandeepPas encore d'évaluation
- Vulnerabilities of The SSL Tls ProtocolDocument12 pagesVulnerabilities of The SSL Tls ProtocolManish AgarwalPas encore d'évaluation
- Digital CertificatesDocument34 pagesDigital CertificatesSheetal VermaPas encore d'évaluation
- Lecture 09Document23 pagesLecture 09Rehan UllahPas encore d'évaluation
- (2014) A Critical Study - Secure Gateway in Payment System For Electronic Transaction PDFDocument7 pages(2014) A Critical Study - Secure Gateway in Payment System For Electronic Transaction PDFAkram PashaPas encore d'évaluation
- Final RSA DocumentationDocument125 pagesFinal RSA DocumentationKishore PinnintiPas encore d'évaluation
- RajanDocument3 pagesRajanvijetameenaPas encore d'évaluation
- E CommerceDocument15 pagesE Commercersoni soniPas encore d'évaluation
- E-Commerce Notes at HomeDocument12 pagesE-Commerce Notes at HomeLaxmiPantPas encore d'évaluation
- Secure Socket Layer: M S.Bhiogade Patni Computer Services, Mumbai, IndiaDocument6 pagesSecure Socket Layer: M S.Bhiogade Patni Computer Services, Mumbai, Indiadidiey87Pas encore d'évaluation
- Confidentiality and Authentication For Secure CommunicationDocument4 pagesConfidentiality and Authentication For Secure CommunicationRakeshconclavePas encore d'évaluation
- Web SecurityDocument18 pagesWeb Securitykrii24u8Pas encore d'évaluation
- Ecommerce Security BasicsDocument2 pagesEcommerce Security BasicskalpanamcaPas encore d'évaluation
- Secure Socket Layer (SSL)Document47 pagesSecure Socket Layer (SSL)Wasif ImranPas encore d'évaluation
- Bitcoin: How Can A Virtual Currency Attain Real Market Value?D'EverandBitcoin: How Can A Virtual Currency Attain Real Market Value?Pas encore d'évaluation
- Decentralization, Security and Business Autonomy (English Version)D'EverandDecentralization, Security and Business Autonomy (English Version)Pas encore d'évaluation
- RC4 Vector Key Based Conditional Access SystemDocument5 pagesRC4 Vector Key Based Conditional Access SystemAlad Manoj PeterPas encore d'évaluation
- T4 Homework 4 AnswersDocument3 pagesT4 Homework 4 Answersmanasdamle6Pas encore d'évaluation
- CAST - Ethical Hacking Course OutlineDocument2 pagesCAST - Ethical Hacking Course Outlinerazu1234Pas encore d'évaluation
- Lab #6: Define A Remote Access Policy To Support Remote Healthcare ClinicsDocument6 pagesLab #6: Define A Remote Access Policy To Support Remote Healthcare ClinicsDuong Van QuyetPas encore d'évaluation
- 1b Cybercrime InterpolDocument3 pages1b Cybercrime InterpolMarielle CaralipioPas encore d'évaluation
- Ch07+-+Block Cipher OperationDocument26 pagesCh07+-+Block Cipher OperationSawsan TawfiqPas encore d'évaluation
- Computer Awareness PDFDocument7 pagesComputer Awareness PDFrajithaalugati100% (1)
- Computer Security Fundamentals: by Chuck EasttomDocument42 pagesComputer Security Fundamentals: by Chuck EasttomNick InkerPas encore d'évaluation
- Detecting Password File Theft Using Predefined Time-Delays Between Certain Password CharactersDocument8 pagesDetecting Password File Theft Using Predefined Time-Delays Between Certain Password Charactersתומר שרהבניPas encore d'évaluation
- Asymmetric Cryptography:: Generating Private KeyDocument4 pagesAsymmetric Cryptography:: Generating Private KeyGaurav SrivastavPas encore d'évaluation
- Cns Classical Encryption TechniqueDocument14 pagesCns Classical Encryption TechniqueKssanthosh KumarPas encore d'évaluation
- LTE Security KeysDocument3 pagesLTE Security Keysmima imenePas encore d'évaluation
- Cryptography and NetworkDocument7 pagesCryptography and NetworkNymur RahmanPas encore d'évaluation
- Kikondo Citambi Rodrigues - Informationsecurity2020Document17 pagesKikondo Citambi Rodrigues - Informationsecurity2020Citambi RodriguesPas encore d'évaluation
- CS409 Cryptography and Network SecurityDocument2 pagesCS409 Cryptography and Network SecuritySidharth SanilPas encore d'évaluation
- TrojanDocument9 pagesTrojanJhonna Marie B. Bueno100% (1)
- VirtuCrypt Brochure1Document2 pagesVirtuCrypt Brochure1adamPas encore d'évaluation
- Prisma Cloud Onboarding - AssessmentDocument6 pagesPrisma Cloud Onboarding - Assessmentkya1005Pas encore d'évaluation
- SecureToken - 2 Factor Authentication SecurityDocument4 pagesSecureToken - 2 Factor Authentication SecuritycjsioPas encore d'évaluation
- Identity and Cloud Governance Enhances NSA Guidance For Improving Cloud SecurityDocument4 pagesIdentity and Cloud Governance Enhances NSA Guidance For Improving Cloud Securityleejiacheng13636Pas encore d'évaluation
- Verify login functionality and create account validation of TT projectDocument12 pagesVerify login functionality and create account validation of TT projecthemantrulzPas encore d'évaluation
- CrowdsecDocument8 pagesCrowdsecMihai ClaudiuPas encore d'évaluation
- Palladium CryptographyDocument21 pagesPalladium CryptographyDisha Makkar100% (1)
- Confiabilidade IEEE 3000 - GoldenDocument5 pagesConfiabilidade IEEE 3000 - GoldenFabrizio FclPas encore d'évaluation
- What Is Phishing? How This Cyber Attack Works and How To Prevent ItDocument2 pagesWhat Is Phishing? How This Cyber Attack Works and How To Prevent ItRanjith pPas encore d'évaluation