Académique Documents
Professionnel Documents
Culture Documents
Visual Cryptography
Transféré par
wind_artCopyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Visual Cryptography
Transféré par
wind_artDroits d'auteur :
Formats disponibles
2016 Online International Conference on Green Engineering and Technologies (IC-GET)
Hierarchical Visual Cryptography for Grayscale
Image
Trupti Patel Rohit Srivastava
P.G Student, Department of Computer Science Assistant Professor, Department of Computer Science
Parul Institute of Engineering and Technology Parul Institute of Engineering and Technology
Limda, Gujarat, India Limda, Gujarat, India
truptipatel987@gmail.com rts080185@gmail.com
Abstract— In this technology era, every sensitive data must be
secured. Visual cryptography is a technique to hide the image II. RELATED WORK
based secret. In visual cryptography the secret image is Visual cryptography is an image encryption technique,
encrypted in to shares and at decryption side all shares are
which hide the image based secret. The big advantage of
superimposed with each other so that secret is revealed. The key
feature of visual cryptography is that, no difficult computation is visual cryptography is that it does not require any complex
needed at decryption side to decrypt the secret. In this paper we computation for decryption of secret but it is only performed
are applying Hierarchical Visual Cryptography Scheme on gray by human visual system. Visual cryptography was introduced
image instead of binary image. So, generated shares are gray by Moni Naor and Adi Shamir in 1994. Visual cryptography is
share, not binary shares that are generated by the binary image. a special kind of cryptographic technique, which can decode
Here we are using the new proposed gray share generation concealed images devoid of any cryptographic computation
algorithm for generation of n number of shares. Here original [1]. It involved breaking up the image into n shares so that
image is encrypted in to n number of levels so security of original only authenticated user with all n shares will decrypt the
image is increased. At decryption side all n shares must have to
image by overlaying each of the shares over each other. P. V.
participate to reveal the original secret. Decrypted image has
same size and better visual quality then original secret image. Chavan et al. [2] have introduced a new concept for secret
image sharing. Hierarchical visual cryptography hides the
Index Terms— secret image sharing, pixel expansion, visual secret information in to number of levels. The expansion ratio
cryptographic scheme, visual cryptography of this technique was 1:4. In [3] a new visual secret sharing
scheme was introduced by researchers. In this secret image
I. INTRODUCTION was encoded in to multiple levels. In this secret sharing
scheme grayscale image was an input to the system then
Visual Cryptography is a special encryption technique to grayscale image was transformed in to halftone image using
hide information in images in such a way that it can be halftoning process then kernel’s algorithm was applied on
decrypted by the human vision if the correct key image is halftoned image which was based on histogram of secret
used. The original information that is to be encrypted referred image obtained by cencuing the frequency of each gray value
as secret. Once the encryption is completed, ciphers are and then two shares were generated. In [4] a new scheme was
generated which is referred as shares. The part of secret in proposed (2, 2) and (3, 3) visual cryptography for grayscale
twisted form is known as share. To share the secret among image. The researchers have used randomization and pixel
group of n participants is the fundamental idea behind visual reversal approach for all methods [4]. In [5] authors have
cryptography. The secret is divided into n number of pieces, proposed the design of hierarchical visual cryptography. In
referred as shares, in order to share the secret. After that, these this secret image was divided into two shares, these two shares
shares are distributed among n participants. Each participant were independently generated their own two share, this
provides his own share, to reveal the original secret. method was applied on binary image and the generated share
There are many visual cryptographic schemes are available, was expansion less. In [6] authors have developed a new
but the basic scheme is 2out of 2visual cryptography. In this signature based authentication system which was work on
scheme secret image is divided in to exactly two shares, if hierarchical visual cryptography algorithm mention in [5].
both two shares are superimposed then secret will be revealed. HVC encrypts the secret in three different levels. Shares
In (k, n) visual cryptographic scheme secret image is divided generated out of HVC were used for authentication
into n shares; if k or more then k shares are superimposed then mechanism. All shares were high contrast in nature. Signature
secret will be decoded. The (n, n) visual cryptographic scheme based authentication was found to be powerful than biometric
is extended version of (k, n) visual cryptographic scheme. In authentication as biometric patterns changes over time. Shares
(n, n) visual cryptographic scheme all n shares are require to generated with this scheme were random in nature giving no
decrypt secret while revealing the secret. information by visual inspection and graying effect was
978-1-5090-4556-3/16/$31.00 ©2016 IEEE
2016 Online International Conference on Green Engineering and Technologies (IC-GET)
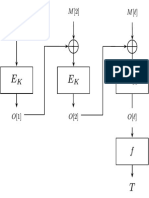
reduced to zero due to high contrast nature of shares [6]. In [7] and original secret image is revealed. Fig. 3 indicates the
researchers were proposed an extension of the capabilities of decryption phase in which final key mask is XORed with
XORed based visual cryptography for general access shares to reveal the secret.
structure. The advantages of using this technique are that no
codebook is needed; decryption is done by XOR operation, no
pixel expansion and perfect reconstruction of secret. In [8] a
new (t, n) visual cryptography scheme was proposed. In this
paper researches have used basis matrices and probabilistic
model for secret image retrieval. In [9] a new algorithm was
proposed for extended embedded visual cryptography for
color image using artificial bee colony algorithm. In this first
halftoning process was applied over color image then
embedding process was applied. The visual quality was
increased then other methods. In [11] authors have proposed a
new condition for hierarchical secret image sharing. In this
decryption will be performed if the access condition was
satisfied. Biswapati Jana et al. [12] have proposed a new
protocol for hierarchical visual secret sharing using
steganography, which maintain hierarchy and detect fake
share. The PSNR value of this method was higher than other
method [12]. In [14] a new algorithm proposed for extended
embedded visual cryptography for color image using artificial
bee colony algorithm. First halftoning process was applied
over color image then embedding process was applied. The
visual quality was increased then other methods [14]. In [15]
minimization of pixel expansion using integer linear program
visual cryptography for general access structure was
introduced by researchers.
Organization of this paper is organized as follows.
The related work is introduced in section II. Section III
discusses about proposed scheme. Section IV discusses the
simulation results of proposed algorithm. Finally the
conclusion is given. Fig. 1 Hierarchical Visual Cryptography Scheme
III. PROPOSED WORK
We have design a new scheme for visual cryptography
which will use hierarchical VCS technique to generate n gray
shares in to levels. Figure 1 shows hierarchical VCS. Proposed
scheme consists of three phases which are described as follow:
The original secret image is fed as an input to the system and
two share1 and share 2 are generated which is called as a first
phase of encryption. Share 1 and share2 are again generate
their own two share which is share 11, share 12, share 21,
share22 respectively which is known as second phase of
encryption. In third phase of encryption share 11 generated
share 111 and share 112, share 12 generate share 121 and
share122, share 21 generate share 211 and share 212, share 22
generate share 221 and share 222. At decryption side if all 8
shares are stacked together then original secret will be
revealed. The Gray share generation algorithm is shown in fig.
2. In this algorithm final key mask is generated using
systematic randomization with key then the original secret
image is fed as an input to the system. The secret image is
XORed with final key mask and n gray shares are generated. Fig. 2 Gray N Share Generation Algorithm
On Decryption side all shares are XORed with final key mask
2016 Online International Conference on Green Engineering and Technologies (IC-GET)
Fig. 6 (a) Share 11 Fig. 6 (b) Share 12
Fig. 3 Decryption Phase
IV. SIMULATION RESULTS
The simulation result of proposed scheme of gray
hierarchical visual cryptography is shown below. Fig. 4 shows
the original secret image. Fig.5 shows first phase of
encryption share1 and share2. In fig.6 second level of
encryption is shown which are share11, share12, share21 and
share22. In fig.7 share111, share112, share121, share122,
share211, share212, share221 and share222 which is third
phase of encryption. Fig.8 shows decrypted image. Decrypted Fig. 6 (c) Share 21 Fig. 6(d) Share 22
image has same size as original secret image and better visual
Fig. 6 Second Phase of Encryption share11, share12, share21 andshare22
quality then original image.
Fig.7 (a) Share 111 Fig.7 (b) Share 112
Fig. 4 Original Secret Image
Fig.7 (c) Share 121 Fig.7 (d) Share 122
Fig 5(a) Share 1 Fig 5 (b) Share 2
Fig. 5 First Phase of Encryption
2016 Online International Conference on Green Engineering and Technologies (IC-GET)
V. CONCLUSION
This paper proposed a new hierarchical visual
cryptography scheme for grayscale image. In this scheme
secret image is encrypted in to levels. Shares generated by this
scheme are gray and highly secured because original secret
image is encrypted in to levels so more secrecy maintain in to
shares. In this paper the visual quality is improved and size of
original secret image and decrypted image is same. In future
we can generate color share by applying this algorithm on any
of R, G and B component of color image.
Fig.7 (e) Share 211 Fig.7 (f) Share 212
REFERENCES
[1] Moni Naor and Adi Shamir, "Visual Cryptography," Eurocrypt, 1994.
[2] Pallavi V. Chavan, Dr.Mohammad Atique, ”Design of Hierarchical
Visual Cryptography”, IEEE, 2013.
[3] Cheng-Chi Lee, Hong-Hao Chen, Hung-Ting Liu, Guo-Wei Chen,
Chwei-Shyong Tsai, ”A new visual cryptography with multi-level
encoding”, Elsevier/Journal of visual language and computing,2013.
[4] Shubhra Dixit, Deepak Kumar Jain and Ankita Saxena, ” An Approach
for Secret Sharing Using Randomised Visual Secret Sharing”,
IEEE,2014.
[5] Pallavi V. Chavan, Dr. Mohammad Atique,Dr. Latesh Malik,”Design
and Implemantation of Hierarchical Visual Cryptography with
Expansionless Shares”, International Journal of Network Security &It’s
Applications,vol-6,2014.
Fig.7 (g) Share 221 Fig.7 (h) Share 222
[6] Pallavi V. Chavan, Dr. Mohammad Atique, Dr. Latesh Malik,
”Signature Based Authentication using Contrast Enhanced Hierarchical
Fig. 7 Third Phase of Encryption share111, share112, share121, share122, Visual Cryptography”, IEEE Conference on Elecrical, Electronics and
share211, share212, share221, share222 Computer Science,2014.
[7] Xiaotian Wu and Wei Sun,.”Extended Capabilities for XOR-Based
Visual Cryptography”, IEEE, VOL. 9, NO. 10, 2014.
[8] M. Sukumar Reddy, S. Murali Mohan, ”Visual Cryptography Scheme
for Secret Image Retrieval” , IJCSNS International Journal of Computer
Science and Network Security, Vol.14 No.6, June 2014.
[9] Deepa A K and Bento Benziger, ”Embedded Extended Visual
Cryptography Scheme for Color Image using ABC Algorithm”, IEEE,
2014.
[10] J. Ramya,B. Parvathavarthini, ”An Extensive Review on Visual
Cryptography Schemes”, IEEE,2014.
[11] Shyong Jian Shyu, Ming Ching Chen, ”Mininizing Pixel Expansion in
Visual Cryptographic Scheme for General Access Structure”, IEEE
Transaction On Circuit and System for Video Technology, 2015.
[12] Biswapati Jana, Amita Samanta and Debasis Giri, ” Hierarchical Visual
Secret Sharing Scheme Using Steganography”, Springer, 2015.
[13] Pradnya S.Nagdive, A.B. Raut, ”Visual Cryptography and
Steganography:A Review”, International Journal of Advanced Research
in Computer Science and Management Studies,vol-3,2.
[14] Deepa A K and Bento Benziger,” Embedded Extended Visual
Fig. 8 Decrypted Secret Image Cryptography.
[15] Shyong Jian Shyu, Ming Ching Chen, ”Mininizing Pixel Expansion in
Visual Cryptographic Scheme for General Access Structure”, IEEE
ACKNOWLEDGMENT Transaction On Circuit and System for Video Technology, 2015.
We would like to thank anonymous referees for
his/her valuable comments and suggestion.
Vous aimerez peut-être aussi
- (IJCST-V8I3P1) :U. Udayakumar, G.S. Gayathri, K. VijayaranganDocument3 pages(IJCST-V8I3P1) :U. Udayakumar, G.S. Gayathri, K. VijayaranganEighthSenseGroupPas encore d'évaluation
- Securing Visual Cryptographic Shares Using Public Key EncryptionDocument6 pagesSecuring Visual Cryptographic Shares Using Public Key EncryptionRamesh MohapatraPas encore d'évaluation
- 29 Denslin Brabin Region Based CDocument5 pages29 Denslin Brabin Region Based CVinay VamsiPas encore d'évaluation
- Encryption and Decryption of Color Images Using Visual CryptographyDocument6 pagesEncryption and Decryption of Color Images Using Visual CryptographyKalyan DasPas encore d'évaluation
- (IJCST-V5I3P26) :kirti RawatDocument9 pages(IJCST-V5I3P26) :kirti RawatEighthSenseGroupPas encore d'évaluation
- Design and Implementation of Visual Cryptography System For Transmission of Secure DataDocument4 pagesDesign and Implementation of Visual Cryptography System For Transmission of Secure DataEditor IJRITCCPas encore d'évaluation
- Compusoft, 3 (8), 1065-1069 PDFDocument5 pagesCompusoft, 3 (8), 1065-1069 PDFIjact EditorPas encore d'évaluation
- Related Work1Document5 pagesRelated Work1Vipul AggarwalPas encore d'évaluation
- 1.1 Image EncryptionDocument19 pages1.1 Image EncryptionGabrealDisalelPas encore d'évaluation
- A Review Paper On Visual Cryptography Technique: Pooja Maan, Mrs. Raman ChawlaDocument3 pagesA Review Paper On Visual Cryptography Technique: Pooja Maan, Mrs. Raman ChawlaerpublicationPas encore d'évaluation
- An Efficient Tagged Visual Cryptography For Color ImagesDocument4 pagesAn Efficient Tagged Visual Cryptography For Color ImagesooooPas encore d'évaluation
- Securing Data Through Steganography and Secret Sharing SchemesDocument6 pagesSecuring Data Through Steganography and Secret Sharing SchemesgestPas encore d'évaluation
- Secured Data Hiding by Using Extended VisualDocument5 pagesSecured Data Hiding by Using Extended VisualInternational Journal of Research in Engineering and TechnologyPas encore d'évaluation
- Development of Visual Cryptography Technique For Authentication Using Facial ImagesDocument8 pagesDevelopment of Visual Cryptography Technique For Authentication Using Facial ImagesEditor IJRITCCPas encore d'évaluation
- Title: Visual CryptographyDocument11 pagesTitle: Visual CryptographySharaqh IbadPas encore d'évaluation
- Embedded Extended Visual Cryptography SchemesDocument6 pagesEmbedded Extended Visual Cryptography SchemesShreyanshPas encore d'évaluation
- A Novel Technique of Visual Cryptography For Maintaining The Security of Visual Information TransactionDocument6 pagesA Novel Technique of Visual Cryptography For Maintaining The Security of Visual Information TransactionIAEME PublicationPas encore d'évaluation
- Image Authentication by Using Visual CryptographyDocument8 pagesImage Authentication by Using Visual CryptographyShabana BanoPas encore d'évaluation
- Visual CryptographyDocument90 pagesVisual CryptographyChokkalingam Balasubramanian100% (1)
- The International Journal of Science & TechnoledgeDocument5 pagesThe International Journal of Science & TechnoledgeellyanovaPas encore d'évaluation
- Extending The Visual Cryptography Algorithm Without Removing Cover ImagesDocument4 pagesExtending The Visual Cryptography Algorithm Without Removing Cover ImagesseventhsensegroupPas encore d'évaluation
- Cry Literature SurveyDocument4 pagesCry Literature SurveyharshaPas encore d'évaluation
- Welcome To The Seminar Titled: Visual CryptographyDocument26 pagesWelcome To The Seminar Titled: Visual Cryptography5A3Khaja Vali PathanPas encore d'évaluation
- A Secure and Verifiable Color Visual Cryptography Scheme With LSB Based Image SteganographyDocument9 pagesA Secure and Verifiable Color Visual Cryptography Scheme With LSB Based Image SteganographyWARSE JournalsPas encore d'évaluation
- Novel Approach For Color Extended Visual Cryptography Using Error DiffusionDocument9 pagesNovel Approach For Color Extended Visual Cryptography Using Error Diffusionsurendiran123Pas encore d'évaluation
- ISMreportDocument23 pagesISMreportS DubeyPas encore d'évaluation
- Image Encryption Using Blowfish AlgorithmDocument3 pagesImage Encryption Using Blowfish AlgorithmAnuj SingjPas encore d'évaluation
- Secured Lossless Share WatermarkingDocument4 pagesSecured Lossless Share WatermarkingEditor IJRITCCPas encore d'évaluation
- New Reversible Data Hiding - Journal - ASPNET22 123Document4 pagesNew Reversible Data Hiding - Journal - ASPNET22 123yogiPas encore d'évaluation
- Authentication of Grayscale Document Images Using Shamir Secret Sharing SchemeDocument5 pagesAuthentication of Grayscale Document Images Using Shamir Secret Sharing SchemeInternational Organization of Scientific Research (IOSR)Pas encore d'évaluation
- Performance Evaluation of Hybrid Method For Securing and Compressing ImagesDocument10 pagesPerformance Evaluation of Hybrid Method For Securing and Compressing ImagesiirPas encore d'évaluation
- Bit Slicng Based Visual Cryptography On Gray Scale ImageDocument4 pagesBit Slicng Based Visual Cryptography On Gray Scale ImageEditor IJRITCCPas encore d'évaluation
- Final Project NewDocument53 pagesFinal Project Newgopi_96100% (1)
- Ijaiem 2013 09 16 019 PDFDocument5 pagesIjaiem 2013 09 16 019 PDFInternational Journal of Application or Innovation in Engineering & ManagementPas encore d'évaluation
- Visual Secret Sharing Using Cryptography: K.K.W.I.E.E.R, Nashik, Maharashtra IndiaDocument3 pagesVisual Secret Sharing Using Cryptography: K.K.W.I.E.E.R, Nashik, Maharashtra IndiaInnovative Research PublicationsPas encore d'évaluation
- 05760187-Visual Crypto Scheme, Medical Image, Forgery DetectionDocument6 pages05760187-Visual Crypto Scheme, Medical Image, Forgery DetectionAzalika RfPas encore d'évaluation
- Result of Digital Image Sharing by Diverse Image Media: Mayuri Sonkusare, Prof. Nitin JanweDocument3 pagesResult of Digital Image Sharing by Diverse Image Media: Mayuri Sonkusare, Prof. Nitin JanweerpublicationPas encore d'évaluation
- Proposed Method of Cryptographic Key Generation For Securing Digital ImageDocument7 pagesProposed Method of Cryptographic Key Generation For Securing Digital ImageVikas PatelPas encore d'évaluation
- Information Security Analysis and Audit: Team MembersDocument11 pagesInformation Security Analysis and Audit: Team MembersSaahil SmsPas encore d'évaluation
- (IJETA-V7I4P6) :alex MathewDocument6 pages(IJETA-V7I4P6) :alex MathewIJETA - EighthSenseGroupPas encore d'évaluation
- Visual CryptographyDocument3 pagesVisual CryptographyChinky GargPas encore d'évaluation
- Visual Cryptography Schemes For Secret Image ProjectDocument5 pagesVisual Cryptography Schemes For Secret Image ProjectSuhaib Ahmed ShajahanPas encore d'évaluation
- Choase Based Image Encryption Using Block-Based Transformation AlgorithmDocument5 pagesChoase Based Image Encryption Using Block-Based Transformation Algorithmvol1no3Pas encore d'évaluation
- New Chaos-Based Image Encryption Scheme For RGB Components of Color ImageDocument9 pagesNew Chaos-Based Image Encryption Scheme For RGB Components of Color ImageMagdalene HanahPas encore d'évaluation
- An Approach of Deep Learning Neural Network Model For Image SecurityDocument12 pagesAn Approach of Deep Learning Neural Network Model For Image SecurityIJRASETPublicationsPas encore d'évaluation
- Generalized random grid based threshold visual cryptography with meaningful sharesDocument14 pagesGeneralized random grid based threshold visual cryptography with meaningful sharesK8suser JPas encore d'évaluation
- Data Hiding and Retrieval Using Visual CryptographyDocument9 pagesData Hiding and Retrieval Using Visual CryptographyIJIRAEPas encore d'évaluation
- Enhancing Security Using Digital Image ProcessingDocument8 pagesEnhancing Security Using Digital Image ProcessingTanya GuptaPas encore d'évaluation
- Term PaperDocument14 pagesTerm PaperK8suser JPas encore d'évaluation
- 9 Image FullDocument8 pages9 Image FullTJPRC PublicationsPas encore d'évaluation
- Chapter 1Document5 pagesChapter 1pius1985Pas encore d'évaluation
- Sciencedirect: Fuzzy Logic Based Image Encryption For Confidential Data Transfer Using (2, 2) Secret Sharing SchemeDocument8 pagesSciencedirect: Fuzzy Logic Based Image Encryption For Confidential Data Transfer Using (2, 2) Secret Sharing SchemeIsrarAhmadMarwatPas encore d'évaluation
- Digital Signal Processing: Xiaotian Wu, Ching-Nung YangDocument12 pagesDigital Signal Processing: Xiaotian Wu, Ching-Nung YangAshhad ImamPas encore d'évaluation
- Boolean XOR Visual Cryptography for Grayscale ImagesDocument4 pagesBoolean XOR Visual Cryptography for Grayscale ImagesmariatantiriPas encore d'évaluation
- A Comparative Study and Literature Review of Image Steganography TechniquesDocument4 pagesA Comparative Study and Literature Review of Image Steganography TechniquesIJSTE100% (1)
- Visual Cryptography: Heritage Institute of Technology, Kolkata, India Heritage Institute of Technology, Kolkata, IndiaDocument3 pagesVisual Cryptography: Heritage Institute of Technology, Kolkata, India Heritage Institute of Technology, Kolkata, IndiaooooPas encore d'évaluation
- A Survey On Different Image Encryption and Decryption TechniquesDocument5 pagesA Survey On Different Image Encryption and Decryption Techniquesraad albayatiPas encore d'évaluation
- 2014 A ICSIP Chaos SurveyDocument7 pages2014 A ICSIP Chaos Surveysofyah312Pas encore d'évaluation
- International Journal of Computational Engineering Research (IJCER)Document6 pagesInternational Journal of Computational Engineering Research (IJCER)International Journal of computational Engineering research (IJCER)Pas encore d'évaluation
- IoT-data FlowDocument1 pageIoT-data Flowwind_artPas encore d'évaluation
- AQM - A Survey PDFDocument52 pagesAQM - A Survey PDFwind_artPas encore d'évaluation
- SHARVOT - Secret SHARe-based VOTing On The BlockchainDocument5 pagesSHARVOT - Secret SHARe-based VOTing On The Blockchainwind_artPas encore d'évaluation
- Cryptographic ProtocolDocument99 pagesCryptographic Protocolwind_artPas encore d'évaluation
- A Proposal of A Secure P2P-Type Storage Schemeby Using The Secret Sharing and The BlockchainDocument8 pagesA Proposal of A Secure P2P-Type Storage Schemeby Using The Secret Sharing and The Blockchainwind_artPas encore d'évaluation
- Cbcmac RevDocument1 pageCbcmac Revwind_artPas encore d'évaluation
- 0903 2693Document21 pages0903 2693pradeepsonnPas encore d'évaluation
- Session-Layer Encryption: Re-Walls Active AttacksDocument9 pagesSession-Layer Encryption: Re-Walls Active Attackswind_artPas encore d'évaluation
- BAN Logic A Logic of AuthenticationDocument23 pagesBAN Logic A Logic of Authenticationwind_artPas encore d'évaluation
- Offline Examination SystemDocument4 pagesOffline Examination Systemஅருண் ராமச்சந்திரன்50% (2)
- JVT D125 LDocument12 pagesJVT D125 LGrupo SolucionesPas encore d'évaluation
- Connect em Cover ViewDocument67 pagesConnect em Cover ViewinterdevcjPas encore d'évaluation
- Organizations and IT Support Systems ExplainedDocument35 pagesOrganizations and IT Support Systems ExplainedvenkeekuPas encore d'évaluation
- Advanced Arm Processors: Ch. S. V. Maruthi Rao Associate Professor Department of ECE, S. I. E. TDocument27 pagesAdvanced Arm Processors: Ch. S. V. Maruthi Rao Associate Professor Department of ECE, S. I. E. TMaruthi RaoPas encore d'évaluation
- Alcatel Lucent End-To-End Triple PlayDocument58 pagesAlcatel Lucent End-To-End Triple PlayChuck CorrellPas encore d'évaluation
- Chap02 - Information System Building BlocksDocument18 pagesChap02 - Information System Building BlockskunsiahPas encore d'évaluation
- Sensor Node Failure Detection Using Round Trip Delay in Wireless Sensor NetworkDocument9 pagesSensor Node Failure Detection Using Round Trip Delay in Wireless Sensor Networksurendar147Pas encore d'évaluation
- 8086 Third Term TopicsDocument46 pages8086 Third Term TopicsgandharvsikriPas encore d'évaluation
- Frequently Asked Questions: " (Type Subject of Faqs) " Rulefinder User GuideDocument1 pageFrequently Asked Questions: " (Type Subject of Faqs) " Rulefinder User GuidesjsshipPas encore d'évaluation
- MG Btech 3rd Sem Cs SyllabusDocument44 pagesMG Btech 3rd Sem Cs SyllabusJinu MadhavanPas encore d'évaluation
- A Desktop Experience From Your Smartphone.: Samsung Dex ProductivityDocument2 pagesA Desktop Experience From Your Smartphone.: Samsung Dex ProductivityBtakeshi1Pas encore d'évaluation
- Combo FixDocument8 pagesCombo FixJesus Jhonny Quispe RojasPas encore d'évaluation
- 1522 4565 1 PBDocument6 pages1522 4565 1 PBIdham TriyunantoPas encore d'évaluation
- BC-5380 LIS ProtocolDocument38 pagesBC-5380 LIS Protocolangga_scribdPas encore d'évaluation
- KillerHomeRecording SettingUpDocument337 pagesKillerHomeRecording SettingUpArtist Recording100% (1)
- Seminar ReportDocument30 pagesSeminar Reportshashank_gowda_7Pas encore d'évaluation
- H820 Usermanual Eng PDFDocument138 pagesH820 Usermanual Eng PDFbogdy00733054Pas encore d'évaluation
- Logical Disk Extension MPDocument48 pagesLogical Disk Extension MPLeit InfoPas encore d'évaluation
- Desired Capabilities in Selenium WebDriver PDFDocument9 pagesDesired Capabilities in Selenium WebDriver PDFInteract peoplePas encore d'évaluation
- VX 9000 IgDocument18 pagesVX 9000 IgJuan PalotePas encore d'évaluation
- 10 NetworkDocument38 pages10 Networkapi-371092170Pas encore d'évaluation
- Component Based ArchitectureDocument4 pagesComponent Based Architecturerajan567Pas encore d'évaluation
- Led TV : Owner'S ManualDocument37 pagesLed TV : Owner'S ManualandreeaPas encore d'évaluation
- Approval SheetDocument10 pagesApproval SheetKim OliverPas encore d'évaluation
- Final Year Project ProposalDocument300 pagesFinal Year Project Proposalalim dublinPas encore d'évaluation
- NCSP Old ExamDocument32 pagesNCSP Old ExamDonia Magdy0% (1)
- Live Agent Developer GuideDocument54 pagesLive Agent Developer GuideHeatherPas encore d'évaluation
- Smart Projectors - Brochure - 20190927 - FN - WebDocument4 pagesSmart Projectors - Brochure - 20190927 - FN - WebCarthick RajPas encore d'évaluation
- DualCell HSDPADocument29 pagesDualCell HSDPASABER1980Pas encore d'évaluation