Académique Documents
Professionnel Documents
Culture Documents
Reviewer in EmTech
Transféré par
Reinn DionisioCopyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Reviewer in EmTech
Transféré par
Reinn DionisioDroits d'auteur :
Formats disponibles
EMPOWERMENT TECHONOLOGIES
INTRODUCTION TO ICT WEB 2.0: DYNAMIC WEB PAGE
Evolution of Wed 1.0
INFORMATION The user is able to see a website differently than others
Knowledge communicated or received concerning a Allows users to interact with the page
particular fact or circumstance Can make comments and create an account
“Fragmented Future” Darcy DiNucci, 1999
COMMUNICATION Social Networking Sites:
The act or process of using words, sounds, signs or - Blogs
behaviors - Wikis
- Video sharing sites
- Hosted services
TECHNOLOGY
Methods, systems and devices which are the result of
scientific knowledge being used for practical purposes WEB 2.0: KEY FEATURES
Folksonomy – allows the user to categorize and
classify/arrange information using freely chosen keyboards
INFORMATION & COMMUNICATION TECHNOLOGY
Rich User Experience – content is dynamic and is
(ICT)
responsive to user’s input
The use of different communication technologies such as
User Participation – the owner of the website is not only
phones, telephones & internet to locate, save, send & edit
the one who is able to put content
information
Longtail – services that are offered/demand rather than on
a one-time purchase
ICT IN THE PHILIPPINES Software as a Service – users will subscribe to a software
“ICT Hub of Asia” only when needed rather than purchasing them
Huge growth of ICT-related jobs around the country, one of Mass Participation – diverse information staring through
which is called the call center or BPO (Business Process universal web access
Outsourcing) centers.
WEB 3.0
WORLD WIDE WEB (WWW) Semantic Web
Collection of public websites connected to the internet World Wide Web Consortium (W3C) – the semantic web
worldwide provides a common framework that allows data to be
shared & reused across application, enterprise, etc.
TIM BERNERS-LEE PROBLEMS:
Timothy John Berners-Lee - COMPATIBILITY - HTML Files & current web
Created HTML & WWW browsers could not support Web 3.0
- SECURITY - The user’s security is also in question
HTML since the machine is saving his/her preferences
Hypertext Markup Language - VASTNESS - The WWW already contains billions
of web pages
HTTP - VAUGNESS - Certain words are imprecise
- LOGIC - These are certain limitations for a
Hypertext Transfer Protocol
computer to be able to predict what the user is
Set up rules for transferring files
referring to a given time
WEB 1.0 TRENDS IN ICT
Static – flat page or stationary pages
1. Convergence – technological convergence is the synergy
of technological achievements to work on a similar goal or
Milestones: task
- Invention of HTML, CSS & Javascript
2. Social Media – a website that enables web users to
- Invention of Java & Flash
create, co-create, discuss, modify & exchange user-
- Multimedia via <img> & <iframe> tags
generated content
3. Mobile Technologies – smartphones and tablets
- iOS – used in Apple devices b) Worm – malicious program that transfers from
- Android – open source operating system one computer to another by any type of means.
developed by Google c) Trojan – malicious program disguised as a useful
- Blackberry OS – used in Blackberry devices program
- Windows Phone OS – closed source and - Rogue security software – tricks the
proprietary operating system developed by user into posing that it is a security
Microsoft software.
- Symbian – original smartphone OS; used by d) Spyware – program that runs in the background
Nokia without you knowing it
- WebOS – originally for smartphones; now used - Keyloggers – used to record the
for smart TV’s keystroke done by the users.
- Windows Mobile – developed by Microsoft for e) Adware – program designed to send you
smartphones and tablets advertisements
4. Assistive Media – nonprofit service designed to help 2. Spam – unwanted email mostly from bots and
people who have visual & reading impairments. A advertisers
database of audio recordings is used to read the user.
3. Phishing – its goal is to acquire sensitive personal
TYPES OF SOCIAL MEDIA information like passwords and credit card details. This is
done by sending an email that will direct the user to visit a
Social Network – sites that allow you to connect with website
people with same interest (Ex. Facebook)
Social News – sites that allows users to post their own - Pharming – it exploits the DNS
news (Ex. Reddit and Digg) (Domain Name Service) system
Bookmarking Sites – sites that allow you to store &
ADVANCED WORD PROCESSING SKILLS
manage links to various websites (Ex. Pinterest)
Media Sharing – sites that allow you to upload & share MAIL MERGE AND LABEL GENERATION
media content like images, music & video
(Ex. Youtube, Instagram & Flicker) MAIL MERGE
Microblogging – sites that focus on short updates from the
user. (Ex. Twitter & Pkurk) Create documents and combine or merge them
Blogs & Forums – sites that allow you to post their Commonly used when sending out advertising materials to
content. Other users are able to comment on the said various recipients
topic. (Ex. Tumblr, WordPress, Blogger) Two Components of Mail Merge
1. Form Document
RULES OF NETIQUETTE - Contains the body of the message
- The main body of the message is the part of the
Internet – information superhighway form document that remains the same no
Intellectual property - If you create something, you have matter whom you send it to
the right as to how it should be used by others. - Place Holders
Fair Use – an intellectual property may be used without - Data fields or merge fields
consent as long as it is used in commentaries, criticisms, - Marks the position on your form
search engines, etc. document where individual data or
Cybercrime – crime committed through the use of internet information will be inserted
Privacy Policy – tells the used how the website handle its 2. List or Data File
data - Two essential components of creating a merged
Copyright – part of the law; those who use your work document are present: the form document and
without your consent is punishable by law the data file
INRERNET THREATS INTEGRATING IMAGES AND EXTERNAL MATERIALS
1. Malware – malicious software KINDS OF MATERIALS
a) Virus – malicious program designed to replicate 1. Pictures – electronic or digital pictures or photographs you
itself and transfer from one computer to another have saved in your device
1. JPG. (Joint Photographic Experts Group)
- “Jay-peg” POWERPOINT
- Can support 16.7 million colors
- Does not support transparency Created by Robert Gaskins and Dennis Austin
- Work well on lettering, line drawings, or simple Provide visuals for group presentation
graphics
TIPS IN CREATING AN EFECTIVE PRESENTAITON
- Relatively small in file size
2. .GIF (Graphic Interchange Format) 1. MINIMIZE – keep slide counts to a minimum to maintain a
- Capable of displaying transparencies clear message and to keep the audience
- Good for blending with other materials or 2. Clarity – avoid being fancy by using a font style that is east
elements in your document to read.
- Also capable of displaying simple animations 3. Simplicity – use bullets or short sentences.
- May not be too useful on a printed document 4. Visuals – use graphics to help ion your presentation but
not too many to distract the audience.
- Can only support up to 256 colors
5. Consistency – make your design uniform. avoid having
- Much better for logos, drawings, etc.
different font styles and backgrounds
3. .PNG (Portable Network Graphics) 6. Contrast – use light font or dark background or vice versa.
- “ping” this is done so that it is easier to read. in most instances, it
- Developed basically for the purpose of is easier to read on screen if the background is dark
transporting images on the internet at faster
rates USING HYPERLINKS IN MICROSOFT POWERPOINT
- Good with transparencies
1. Select an object or highlight a text
- Does not support animation
2. Place in this document
- Can display up to 16 million colors 3. Create new document
- Allows the control of the transparency level or 4. Email address
capacity of images 5. When done, click OK
2. Clip Art – generally a .GIF type
3. Shapes – printable objects or materials that you can EMBEDDING OBJECTS IN MICROSOFT POWERPOINT
integrate in your document to enhance its appearance
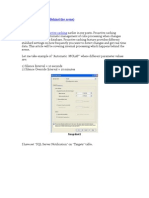
1. Go to the insert tab
4. Smart Art – sets of different shapes grouped together to
2. On the text group, click on object
form ideas 3. The insert object dialog box would appear
5. Chart - allow you to represent data characteristics and
trends; suited for preparing reports
6. Screenshot – more realistic image of what you are
discussing on your report or manual.
IMAGE PLACEMENT
TEXT WRAPPING
1. In Line with Text – usually used when you need to place
your image at the beginning of a paragraph.
2. Square – placed anywhere within the paragraph with the
text going around the image in a square pattern
3. Tight – the text “hugs” or conforms to the general shape
of the image
4. Through – allows the text on your document to flow even
tighter, taking the contours and shape of the image
5. Top and Bottom – pushes the text away vertically to the
top and bottom
6. Behind Text – can be dragged and placed anywhere on
your document; background
7. In Front of Text – Allows your image to be placed right on
top of the text; the text will be covered by the image
Vous aimerez peut-être aussi
- Empowerment TechnologiesDocument24 pagesEmpowerment TechnologiesJulian LuPas encore d'évaluation
- Emtech Quarter 1Document9 pagesEmtech Quarter 1Patricia Gabriell MulaPas encore d'évaluation
- Empowerment Technology1Document2 pagesEmpowerment Technology1Elite-sunpink Printing PressPas encore d'évaluation
- E Tech RebyuwerDocument21 pagesE Tech RebyuwerIrish MaireignPas encore d'évaluation
- Reviewer Lect in EmptechDocument2 pagesReviewer Lect in EmptechNagum RhiannePas encore d'évaluation
- Information and Communication Technologies (ICT)Document8 pagesInformation and Communication Technologies (ICT)Ha? HalamanPas encore d'évaluation
- Et ReviewerDocument5 pagesEt ReviewerCessna Ursolino InciongPas encore d'évaluation
- Emp Tech - ReviewerDocument4 pagesEmp Tech - ReviewerYianna SibayanPas encore d'évaluation
- Empowerment Tech - MidtermsDocument4 pagesEmpowerment Tech - MidtermsPolPas encore d'évaluation
- Ict (Lesson 1)Document2 pagesIct (Lesson 1)Sofia CastroPas encore d'évaluation
- Information and Communication Technologies (ICT)Document7 pagesInformation and Communication Technologies (ICT)Ha? HalamanPas encore d'évaluation
- Empowerment Technology - Midterm HandoutDocument6 pagesEmpowerment Technology - Midterm HandoutRigene LaredePas encore d'évaluation
- Lesson 1Document2 pagesLesson 1Kiean CupinPas encore d'évaluation
- Empow Tech-L1Document45 pagesEmpow Tech-L1CON REGASPIPas encore d'évaluation
- EmpTech NotesDocument8 pagesEmpTech Notesayaka kamisatoPas encore d'évaluation
- LESSON 1. Information and Communication Technlogy TodayDocument2 pagesLESSON 1. Information and Communication Technlogy TodayAngelo QuintoPas encore d'évaluation
- EmpowermentDocument2 pagesEmpowermentEvelyn BautistaPas encore d'évaluation
- Emtech ReviewerDocument6 pagesEmtech ReviewerFerdinand Roman Manalang Jr0% (1)
- EMPTECH Notes 1-6Document14 pagesEMPTECH Notes 1-6Mark Vincent AyapanaPas encore d'évaluation
- EmpTech Lesson 1Document7 pagesEmpTech Lesson 1Princessmae BermejoPas encore d'évaluation
- Ict - Module 1Document5 pagesIct - Module 1Stephanie ClairePas encore d'évaluation
- Introduction To Ict PDFDocument36 pagesIntroduction To Ict PDFSlient KillerPas encore d'évaluation
- ICT1. Introduction To Information and Communication TechnologiesDocument3 pagesICT1. Introduction To Information and Communication Technologiesesther smntPas encore d'évaluation
- Mst122 Ref. 2Document32 pagesMst122 Ref. 2johnpatrickbajamundePas encore d'évaluation
- Etech ReviewerDocument12 pagesEtech ReviewerRhaiven Carl YapPas encore d'évaluation
- Emtech ReviewerDocument9 pagesEmtech ReviewerKelly Jane ChuaPas encore d'évaluation
- Module 1 - The Current State of Ict TechnologiesDocument4 pagesModule 1 - The Current State of Ict TechnologiesErichelle Espineli100% (5)
- Lesson 1: Introduction To ICTDocument12 pagesLesson 1: Introduction To ICTArjay NatividadPas encore d'évaluation
- Ict ReviewerDocument5 pagesIct Reviewerpmjoygarciaandal09Pas encore d'évaluation
- Lesson 1: Introduction To Information and Communication To TechnologyDocument12 pagesLesson 1: Introduction To Information and Communication To TechnologyJustin De OcampoPas encore d'évaluation
- E-Tech Lesson 1 - 3Document5 pagesE-Tech Lesson 1 - 3Jeandra VillanuevaPas encore d'évaluation
- Hello:, Block 3, 12, 13, 14, 15, 17, 21, 25, 26 AND 27!Document29 pagesHello:, Block 3, 12, 13, 14, 15, 17, 21, 25, 26 AND 27!Ma. Judy Vinne AvilaPas encore d'évaluation
- w2 Introduction To IctDocument25 pagesw2 Introduction To IctadharaPas encore d'évaluation
- Empowerment Technology (Empotek) : Mr. Enrico HidalgoDocument69 pagesEmpowerment Technology (Empotek) : Mr. Enrico HidalgoJessabel ChavezPas encore d'évaluation
- Lesson 1 Information and Communication TechnologyDocument2 pagesLesson 1 Information and Communication TechnologyKaizel BritosPas encore d'évaluation
- EMTECH REVIEWER - W1 and W2Document3 pagesEMTECH REVIEWER - W1 and W2Royu BreakerPas encore d'évaluation
- Empowerment Technologies Topic: Introduction To Information & Communicaions Technology Ict, Internet, and WWWDocument12 pagesEmpowerment Technologies Topic: Introduction To Information & Communicaions Technology Ict, Internet, and WWWNrop VoxPas encore d'évaluation
- 11 SHS IctDocument6 pages11 SHS IctMARIAL JUNE BALDOPas encore d'évaluation
- Empowerment Technologies Quarter 1Document67 pagesEmpowerment Technologies Quarter 1Propsero Luke Godfrey CabertePas encore d'évaluation
- Url Means Uniform Resources Locator: Features of Web 2.0Document6 pagesUrl Means Uniform Resources Locator: Features of Web 2.0Jhon JhonPas encore d'évaluation
- Ict - Week 2Document39 pagesIct - Week 2Bridgette Niña OrolfoPas encore d'évaluation
- Empowerment Technologies: LESSON 1: Introduction To Information and Communication TechnologiesDocument29 pagesEmpowerment Technologies: LESSON 1: Introduction To Information and Communication TechnologiesAdam Galay100% (1)
- Empowerment Technology Prelim HandoutDocument4 pagesEmpowerment Technology Prelim HandoutLar KenPas encore d'évaluation
- Empowerment TechDocument47 pagesEmpowerment TechVCIT incPas encore d'évaluation
- ETECH ReviewerDocument6 pagesETECH ReviewerMhariane MabborangPas encore d'évaluation
- Empowerment Technology L1Document3 pagesEmpowerment Technology L1Ara Belle PoncePas encore d'évaluation
- Lesson 1.1 ICT and Its Current StateDocument3 pagesLesson 1.1 ICT and Its Current StateJoross SabadoPas encore d'évaluation
- EMTECHDocument5 pagesEMTECHcandace arvyPas encore d'évaluation
- Empowerment Technologies: StaticDocument7 pagesEmpowerment Technologies: StaticEryka ChloePas encore d'évaluation
- Litera03z Finals ReviewerDocument17 pagesLitera03z Finals Reviewerkharen loroPas encore d'évaluation
- 12-E-Tech Reviewer (1-3)Document5 pages12-E-Tech Reviewer (1-3)Blessy Myl MagrataPas encore d'évaluation
- Ict Chapter 1 ReviewerDocument6 pagesIct Chapter 1 ReviewerYasmien ReyesPas encore d'évaluation
- Information and Communication TechnologiesDocument2 pagesInformation and Communication TechnologiesRenalyn Salde PesqueraPas encore d'évaluation
- Empowerment TechnologiesDocument2 pagesEmpowerment TechnologiesBianca Eunice MarcaidaPas encore d'évaluation
- PPT1 Introduction To Information and Communication Technology PDFDocument43 pagesPPT1 Introduction To Information and Communication Technology PDFRAIHAANA MINONG NAMLAPas encore d'évaluation
- ETECHmodule Week 1-4Document18 pagesETECHmodule Week 1-4Ralph John Basingan TenorioPas encore d'évaluation
- E TechDocument25 pagesE TechKristel Kate Melchor TugadePas encore d'évaluation
- Etech MidtermsDocument4 pagesEtech MidtermsLJ D. TanjayPas encore d'évaluation
- Empowerment Technology11Document7 pagesEmpowerment Technology11Roy OpredoPas encore d'évaluation
- In Re Max ShoopDocument9 pagesIn Re Max ShoopReinn Dionisio100% (2)
- Course SyllabusDocument2 pagesCourse SyllabusReinn DionisioPas encore d'évaluation
- People Vs VistanDocument4 pagesPeople Vs VistanReinn DionisioPas encore d'évaluation
- 123720-1999-Ramos v. Court of Appeals PDFDocument32 pages123720-1999-Ramos v. Court of Appeals PDFMau AntallanPas encore d'évaluation
- Negros Navigation Vs CaDocument14 pagesNegros Navigation Vs CaReinn DionisioPas encore d'évaluation
- Separate OpinionsDocument6 pagesSeparate OpinionsReinn DionisioPas encore d'évaluation
- Martinez Vs Buskirk PDFDocument5 pagesMartinez Vs Buskirk PDFReinn DionisioPas encore d'évaluation
- Cang Vs Cullen PDFDocument10 pagesCang Vs Cullen PDFReinn DionisioPas encore d'évaluation
- Andamo v. IACDocument9 pagesAndamo v. IACHershey Delos SantosPas encore d'évaluation
- Africa Vs CaltexDocument10 pagesAfrica Vs CaltexAriel Conrad MalimasPas encore d'évaluation
- Batiquin Vs CADocument10 pagesBatiquin Vs CAbeljoe12345Pas encore d'évaluation
- Petitioner Vs Vs Respondents: Second DivisionDocument11 pagesPetitioner Vs Vs Respondents: Second DivisionAriel Conrad MalimasPas encore d'évaluation
- People Vs VistanDocument4 pagesPeople Vs VistanReinn DionisioPas encore d'évaluation
- Negros Navigation Vs CaDocument14 pagesNegros Navigation Vs CaReinn DionisioPas encore d'évaluation
- Africa Vs CaltexDocument10 pagesAfrica Vs CaltexAriel Conrad MalimasPas encore d'évaluation
- Republic v. Luzon Stevedoring CorpDocument5 pagesRepublic v. Luzon Stevedoring CorpMico Maagma CarpioPas encore d'évaluation
- Batiquin Vs CADocument10 pagesBatiquin Vs CAbeljoe12345Pas encore d'évaluation
- Petitioner Vs Vs Respondents: Second DivisionDocument11 pagesPetitioner Vs Vs Respondents: Second DivisionAriel Conrad MalimasPas encore d'évaluation
- Sample Brochure 2Document1 pageSample Brochure 2Reinn Dionisio100% (1)
- Araneta Vs de JoyaDocument3 pagesAraneta Vs de JoyaReinn DionisioPas encore d'évaluation
- Andamo v. IACDocument9 pagesAndamo v. IACHershey Delos SantosPas encore d'évaluation
- Affidavit of SupportDocument1 pageAffidavit of SupportReinn DionisioPas encore d'évaluation
- Acknowledgement by CorporationDocument1 pageAcknowledgement by CorporationReinn DionisioPas encore d'évaluation
- Reviewer in EmTechDocument3 pagesReviewer in EmTechReinn DionisioPas encore d'évaluation
- General Chemistry: Nature and States of MatterDocument3 pagesGeneral Chemistry: Nature and States of MatterReinn DionisioPas encore d'évaluation
- Practical Research Lesson 1Document2 pagesPractical Research Lesson 1Reinn DionisioPas encore d'évaluation
- Example Practical ReportDocument45 pagesExample Practical ReportMohd Zulhilmi84% (19)
- GE8151 Phython QB - by WWW - EasyEngineering.net 4Document4 pagesGE8151 Phython QB - by WWW - EasyEngineering.net 4widav34409Pas encore d'évaluation
- XIInfo Pract H Y 129Document3 pagesXIInfo Pract H Y 129ashish barwarPas encore d'évaluation
- Quality Form: Dr. Cesar A. Villariba Research and Knowledge Management InstituteDocument2 pagesQuality Form: Dr. Cesar A. Villariba Research and Knowledge Management Institutewatak ONLINEPas encore d'évaluation
- Apache Spark Fundamentals: Getting StartedDocument28 pagesApache Spark Fundamentals: Getting StartedArunachalam NarayananPas encore d'évaluation
- LOG112Document21 pagesLOG112Otto Lambertus0% (1)
- Computer Science Syllabus For 4th SemesterDocument17 pagesComputer Science Syllabus For 4th SemesterAnkur Goel67% (3)
- Versatech Recloser ManualDocument40 pagesVersatech Recloser ManualmiveyPas encore d'évaluation
- ATV320 Getting Started EN NVE21763 02Document4 pagesATV320 Getting Started EN NVE21763 02Berkah Jaya PanelPas encore d'évaluation
- Prima Efficiency Across BoundariesDocument9 pagesPrima Efficiency Across Boundariescosty_transPas encore d'évaluation
- CM2 Hfa100 2001 - 02Document20 pagesCM2 Hfa100 2001 - 02Ehsan GhanbarzadehPas encore d'évaluation
- 0417 - N18 - Instructions For Conducting The IGCSE ICT Practical TestsDocument6 pages0417 - N18 - Instructions For Conducting The IGCSE ICT Practical TestsRichie HarvyPas encore d'évaluation
- A Framework For Web Based Student Record Management System Using PHPDocument5 pagesA Framework For Web Based Student Record Management System Using PHPDrey Drey IIPas encore d'évaluation
- Dynamics 365 Customer EngagementDocument421 pagesDynamics 365 Customer EngagementMagicMoviesPas encore d'évaluation
- Paddy Leaf Disease DetectionDocument48 pagesPaddy Leaf Disease DetectionAkula SandeepPas encore d'évaluation
- ABS960 Brochure 1113Document4 pagesABS960 Brochure 1113hendryPas encore d'évaluation
- HW2 - TCMT - Nhóm ADocument4 pagesHW2 - TCMT - Nhóm ALớp 18DT3 DUT - Bách Khoa Đà NẵngPas encore d'évaluation
- Chapter 8 - Project Planning - Project Resource ManagementDocument6 pagesChapter 8 - Project Planning - Project Resource ManagementSuada Bőw WéěžýPas encore d'évaluation
- MEO Class 4 Examination - Subjects, Syllabus, Courses, Eligibility EtcDocument10 pagesMEO Class 4 Examination - Subjects, Syllabus, Courses, Eligibility EtcRavi Viknesh67% (3)
- Assignment-6question and SolutionDocument10 pagesAssignment-6question and SolutionMaulinduPas encore d'évaluation
- The Electrical Engineering HandbookDocument24 pagesThe Electrical Engineering HandbookKar GayeePas encore d'évaluation
- Shell Case StudyDocument9 pagesShell Case StudyAnslem MirandaPas encore d'évaluation
- Draft Methodology (G-14)Document14 pagesDraft Methodology (G-14)Javed ParachaPas encore d'évaluation
- Automotive Electronics Council-Q200 Stress Test Qualification For Passive Components Syfer AEC-Q200-Rev C QualificationDocument7 pagesAutomotive Electronics Council-Q200 Stress Test Qualification For Passive Components Syfer AEC-Q200-Rev C QualificationgubiliPas encore d'évaluation
- 3D Printing of Core and Cavity InsertsDocument15 pages3D Printing of Core and Cavity InsertsSushmaPas encore d'évaluation
- 13.proactive CachingDocument8 pages13.proactive Cachingprasad_nagireddyPas encore d'évaluation
- Shneiderman's 8 Golden Rules of Interface Design: The Principles Questions To Consider Mark CompleteDocument1 pageShneiderman's 8 Golden Rules of Interface Design: The Principles Questions To Consider Mark CompletellPas encore d'évaluation
- Hitz Work and PayDocument2 pagesHitz Work and Paynajergodfred12Pas encore d'évaluation
- User'S Manual: Digital Satellite Meter SH-500Document8 pagesUser'S Manual: Digital Satellite Meter SH-500josewanPas encore d'évaluation
- Flexi Cabinet For Outdoor Quick GuideDocument15 pagesFlexi Cabinet For Outdoor Quick Guideprashant gauravPas encore d'évaluation