Académique Documents
Professionnel Documents
Culture Documents
Through Detailed Security and Performance Analysis
Transféré par
nezclark0 évaluation0% ont trouvé ce document utile (0 vote)
10 vues1 pageTitre original
Through detailed security and performance analysis.docx
Copyright
© © All Rights Reserved
Formats disponibles
DOCX, PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme DOCX, PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
10 vues1 pageThrough Detailed Security and Performance Analysis
Transféré par
nezclarkDroits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme DOCX, PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 1
Through detailed security and performance analysis, they show
that their scheme is highly efficient and resilient to Byzantine
failure, malicious data modification attack, and even server
colluding attacks. The computing power in a Cloud computing
environment is supplied by a collection of data centers, which are
typically installed with hundreds to thousands of servers (Buyya
R. & Murshed, M, 2002). The authors-built architecture of a typical
Cloud-based data center consisting of four layers. At the lowest
layers, there exist massive physical resources (storage servers
and application servers) that power the data centers. These
servers are transparently managed by the higher-level
virtualization services and toolkits that allow sharing of their
capacity among virtual instances of servers. These virtual
instances are isolated from each other, which aid in achieving
fault tolerant behavior and isolated security context (Smith J. E,
& Nair. R., 2005) (Juels et al., 2007) described a formal “proof of
retrievability” (POR) model for ensuring the remote data integrity.
Their scheme combines spot-checking and error-correcting code
to ensure both possession and retrievability of files on archive
service systems.
Vous aimerez peut-être aussi
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (895)
- Food PromoDocument3 pagesFood PromonezclarkPas encore d'évaluation
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- Employee RecordsDocument2 pagesEmployee RecordsnezclarkPas encore d'évaluation
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
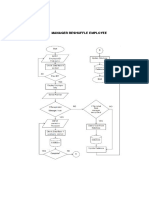
- Manager Reshuffle EmployeeDocument2 pagesManager Reshuffle EmployeenezclarkPas encore d'évaluation
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5794)
- Admin ViewsDocument2 pagesAdmin ViewsnezclarkPas encore d'évaluation
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
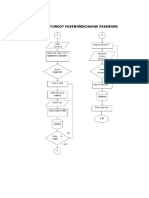
- User Forgot PasswordDocument1 pageUser Forgot PasswordnezclarkPas encore d'évaluation
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (266)
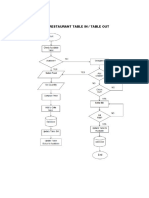
- Restaurant Table inDocument1 pageRestaurant Table innezclarkPas encore d'évaluation
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (400)
- Framework For Evaluation of Programming Language Examinations (2014) Recent Advancements in The Field of eDocument2 pagesFramework For Evaluation of Programming Language Examinations (2014) Recent Advancements in The Field of enezclarkPas encore d'évaluation
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- Usability of Mobile Applications (2013) : Case Study of A Computer Based Examination System (2015)Document2 pagesUsability of Mobile Applications (2013) : Case Study of A Computer Based Examination System (2015)nezclarkPas encore d'évaluation
- The Development ApproachDocument1 pageThe Development ApproachnezclarkPas encore d'évaluation
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- Respondents of StudyDocument1 pageRespondents of StudynezclarkPas encore d'évaluation
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (588)
- Understanding The Effect of eDocument2 pagesUnderstanding The Effect of enezclarkPas encore d'évaluation
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- Scope and LimitationsDocument1 pageScope and LimitationsnezclarkPas encore d'évaluation
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (74)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (345)
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2259)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (121)
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)