Académique Documents
Professionnel Documents
Culture Documents
SQL Server 2005 Security Datasheet
Transféré par
azmath0 évaluation0% ont trouvé ce document utile (0 vote)
50 vues3 pagesSecurity is a key feature of SQL Server 2005, which provides confidentiality, integrity, and availability of mission-critical data. Database administrators must properly secure them from both internal and external threats. SQL Server 2005 provides automatic secured updates and encryption of sensitive data.
Description originale:
Copyright
© Attribution Non-Commercial (BY-NC)
Formats disponibles
PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentSecurity is a key feature of SQL Server 2005, which provides confidentiality, integrity, and availability of mission-critical data. Database administrators must properly secure them from both internal and external threats. SQL Server 2005 provides automatic secured updates and encryption of sensitive data.
Droits d'auteur :
Attribution Non-Commercial (BY-NC)
Formats disponibles
Téléchargez comme PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
50 vues3 pagesSQL Server 2005 Security Datasheet
Transféré par
azmathSecurity is a key feature of SQL Server 2005, which provides confidentiality, integrity, and availability of mission-critical data. Database administrators must properly secure them from both internal and external threats. SQL Server 2005 provides automatic secured updates and encryption of sensitive data.
Droits d'auteur :
Attribution Non-Commercial (BY-NC)
Formats disponibles
Téléchargez comme PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 3
Security-Enhanced Database Platform
Overview of SQL Server 2005 SQL Server and Trustworthy Computing
Today, database professionals need more tools to fight security Security, Privacy, Reliability and Business Practices are the
threats as database systems are being widely used for critical driving forces of the Microsoft Trustworthy Computing initiative.
applications. Because databases are increasingly exposed via web Security is a key feature of SQL Server 2005, which provides
servers, administrators must properly secure them from both confidentiality, integrity, and availability of mission-critical data.
internal and external threats. Securing a database involves As part of our focus on technology investments, Microsoft takes a
establishing a strong policy as well as adequate access controls. "defense-in-depth" approach to protect and align three core
In response to these needs, Microsoft has implemented strong elements: fundamentals, threat and vulnerability mitigation, and
security features into the Microsoft® SQL Server™ 2005, which identity and access control.
provides a security-enabled platform for enterprise-class relational Microsoft commits significant resources toward enhancing
database and analysis solutions. SQL Server 2005 provides privacy protection, from the software itself to the services and
cutting edge security technology and addresses several security products we offer customers to help them manage the privacy of
issues, including automatic secured updates and encryption of their information.
sensitive data.
Microsoft addresses reliability by providing dependable software
In addition to these enhanced security features, SQL Server 2005 and support. We also provide value by being a reliable business
running on Microsoft Windows Server® works well with other partner, maintaining an open dialogue with customers and
Microsoft platforms and products. Microsoft has also invested industry partners, and actively seeking feedback about improving
deeply in standards-based interoperability with other platforms software and services.
and products.
Microsoft follows the concept of citizenship. We conduct business
Security Features of SQL Server 2005 in the communities as a responsible global corporate citizen. High
standards of transparency and integrity have helped to build
SQL Server 2005 provides enhanced security features that continually-increasing trust of communities for Microsoft.
allow you to meet the following security challenges:
Security Challenge Security Feature
Keeping your installation updated Automated software updates
Managing services exposure Reduced surface area
Guidance for secure deployment Knowledge resources for secure
deployment
Weak passwords Password policy enforcement
Lack of audit information Capture and audit DDL activities
Data confidentiality Built-in encryption and Key Management
Metadata protection Catalog security
Agent services security Roles-based agent services management
Insecure application code Secure development and code execution
Schema level permission User – schema separation
Granular permission to execute Execution context
statements in a module.
Security Features at a Glance
Automated Software Updates
Windows Update is built to ensure timely download and
application of patches that significantly reduce specific security
vulnerabilities. Windows Update automatically detects any edition
of SQL Server 2005 installed on a particular machine and—based
on the update analysis—can automatically install particular
patches, greatly reducing the threat caused by known software
vulnerabilities.
Reduced Surface Area
In any database, maximum security is achieved by limiting surface
area exposure. The Surface Area Configuration tool of SQL Server
2005 allows administrators to manage services and connections—
including analysis services, remote connections, full-text search
service, SQL Server browser service, anonymous connection,
linked objects, user-defined functions, CLR integration, SQL Mail,
and native XML Web services—with an easy-to-use, graphical user
interface. By limiting exposure of these services, security
vulnerabilities can be greatly reduced.
Knowledge Resources for Secure Deployment Roles
A set of new deployment tools and documentation helps ensure Granting role-based access to SQL Server Agents gives database
that SQL Server 2005 can be securely deployed into an existing administrators more flexibility in managing the Agent services.
SQL Server topology or a new installation. These tools provide a Execution of the SQL Server Integration Services (SSIS) package as
step-by-step approach by giving detailed information, analyzing a job step is more secure with Multiple Proxy Accounts in SQL
the existing topology, checking for prerequisites, recommending a 2005. By default, in SQL Server 2005, only system administrators
configuration setting, and validating each step. Microsoft also can create the following tasks in a job:
publishes security bulletins and patches as appropriate for SQL • Active Scripting
Server 2005. • SQL Server Integration Services Package
The security-enhanced development environment enabled by SQL • Analysis Command
Server 2005 allows developers easy sign on, verification, and • Analysis Query
code management. Common Language Runtime (CLR) • All replication subsystems
assemblies that run in the database and all managed code uses
Code Access Security (CAS). Catalog Security
SQL Server 2005 provides a more secure environment for
Password Policy Enforcement metadata accessibility than SQL Server 2000. Catalog views of
Strong password policies lead to more secure passwords and SQL Server 2005 now include both INFORMATION_SCHEMA and
fewer opportunities for security breaches of database servers. compatibility views. Additionally, catalog views are more secure as
Under strong password policies, SQL Server 2005 supports users are able to only view objects they are permitted to see.
password complexity and password expiration. These policies
require minimum password length, proper character Execution Context
combinations, and regularly-changing passwords. When SQL SQL Server 2005 introduces the ability to mark modules with an
Server 2005 is running on Microsoft Windows Server 2003, execution context, such that the statements within the module can
Windows® secure password policies can also be applied to SQL execute as a particular user as opposed to the calling user. This
Server password policies, providing enhanced security. way, while the calling user still needs permissions to execute the
MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.
Microsoft Corporation One Microsoft Way Redmond, WA 98052-6399 USA
Part No. 098-107473
module, the permissions for statements within the module are Conclusion
checked against the execution context that the module was As one of the first products to complete the Security
marked with. This behavior can be used to overcome some of the Development Lifecycle, SQL Server 2005 offers security
shortcomings of ownership chaining because it applies to all enhancements that provide reduced surface area exposure,
statements within the module. An alternative to marking more secure code execution, and better management of
execution context on modules is the signing feature. By adding a authentication and access. The revamped security infrastructure
signature to a module, permissions can be associated to the within SQL Server 2005 offers a significantly more secure
signature for the duration of the execution of the procedure. database platform with a guiding principle of least privilege,
which limits users to only the information they need to complete
User Schema Separation their tasks.
User schema separation simplifies managing large databases by
providing flexibility in assigning permissions. In SQL Server 2005, Additionally, the availability of data encryption secures
by granting permissions on a schema, administrators can grant confidential, mission-critical data in case of physical compromise
permissions to every object currently contained in the schema and or otherwise unauthorized access to the database system.
any objects added to the schema in the future. They do not need
to update permissions for every user when a new object is added.
Additional Resources
Built-in Encryption
For more information about Microsoft SQL Server 2005, see
SQL Server 2005 provides data encryption directly in the
the following:
database and is available across all SKUs.
SQL Server Homepage
Key Management http://www.microsoft.com/sql
To enhance security, SQL Server 2005 maintains certificate stores,
provides key management for symmetric and asymmetric keys, Product Overview Whitepaper
and uses algorithms like 2-key TripleDES, AES, DES, RC2, and RSA. http://www.microsoft.com/sql/2005/productinfo/overview.
The key management of a SQL Server 2005 instance is based on a mspx
hierarchy of keys rooted in the Service Master Key (SMK), which is
encrypted using both the machine key and service key. Developer Center
http://msdn.microsoft.com/sql/
An asymmetric key consists of a private key and public key pair.
Information is encrypted using the public key and can only be
Attend a free webcast or chat
decrypted using the private key. A symmetric key is a single key
http://www.microsoft.com/sql/community/webcasts.asp
that can be used for both encryption and decryption.
Capture and Audit DDL Activities
The powerful features of Data Manipulation Language (DML)
triggers have been extended to Data Definition Language (DDL)
statements. At the server or database level, certain occurrences of
events can fire DDL triggers. As DDL responds to the server- and
database-level events, these events can be logged, which is
important for auditing activities and enhancing security.
MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.
Microsoft Corporation One Microsoft Way Redmond, WA 98052-6399 USA
Part No. 098-107473
Vous aimerez peut-être aussi
- Pen Testing With Burp SuiteDocument41 pagesPen Testing With Burp Suiteazmath100% (2)
- John Grinder & Judith DeLozier - Turtles All The Way DownDocument414 pagesJohn Grinder & Judith DeLozier - Turtles All The Way Downadela_adela100% (3)
- Principles of The A Good SalesmanDocument2 pagesPrinciples of The A Good SalesmanJemeia Mae Eslabon100% (1)
- ApostilleDocument5 pagesApostilleazmathPas encore d'évaluation
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (587)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (265)
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (73)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (119)
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)
- Syllabus IBADocument1 pageSyllabus IBAK.m.khizir AhmedPas encore d'évaluation
- Monitoring Loads Duration Flowcurve TutorialDocument35 pagesMonitoring Loads Duration Flowcurve TutorialmimahmoudPas encore d'évaluation
- Kpi RNC LevelDocument24 pagesKpi RNC LevelIan Juanda MarboenPas encore d'évaluation
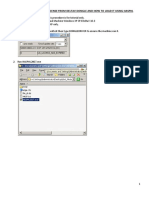
- The Following Code Snippet Is Implemented For The: Function Diff - Actfun (Self, Z, Type)Document2 pagesThe Following Code Snippet Is Implemented For The: Function Diff - Actfun (Self, Z, Type)saheb_juPas encore d'évaluation
- Word - Exercise 1Document5 pagesWord - Exercise 1RonellOropesaPas encore d'évaluation
- Active Data Guard 11g DatasheetDocument2 pagesActive Data Guard 11g DatasheetRaghu ChiranjiviPas encore d'évaluation
- My - Statement - 1 Dec, 2017 - 30 Dec, 2017 - 7014139395Document11 pagesMy - Statement - 1 Dec, 2017 - 30 Dec, 2017 - 7014139395dr.rakeshPas encore d'évaluation
- About TCS Cloud PlusDocument4 pagesAbout TCS Cloud Pluskmanikannan1977_7427Pas encore d'évaluation
- The CPOCDocument2 pagesThe CPOCnurulshakierahPas encore d'évaluation
- Playboy Philippines Mocha Girls PDF 154Document4 pagesPlayboy Philippines Mocha Girls PDF 154Glen S. Reyes0% (2)
- 8051 Chap6 InterruptsDocument13 pages8051 Chap6 InterruptsDangthieuhoi VuPas encore d'évaluation
- Tax Does Not Calculate in R12 E-Business Tax (EBTAX)Document4 pagesTax Does Not Calculate in R12 E-Business Tax (EBTAX)msalahscribdPas encore d'évaluation
- 4D Construction Sequence Planning - New Process and Data Model PDFDocument6 pages4D Construction Sequence Planning - New Process and Data Model PDFel_residentePas encore d'évaluation
- Chapter 2.1-Multimedia Storage TechniquesDocument41 pagesChapter 2.1-Multimedia Storage Techniqueshubillanth67% (3)
- Zeroth Review PPT - Sample Format 1Document13 pagesZeroth Review PPT - Sample Format 1Madhesh EPas encore d'évaluation
- DPA ImplementationDocument4 pagesDPA ImplementationsreekanthdamaPas encore d'évaluation
- AlphaGo Tutorial SlidesDocument16 pagesAlphaGo Tutorial SlidesDaniel Andrés CrespoPas encore d'évaluation
- Bluecat Networks Whitepaper - How To Integrate Active Directory and DNSDocument11 pagesBluecat Networks Whitepaper - How To Integrate Active Directory and DNSRahmiAmaliaPas encore d'évaluation
- MCQ Bank Computer PDFDocument10 pagesMCQ Bank Computer PDFEjazAhmadPas encore d'évaluation
- Blockchain Application On Financial Sector in The FutureDocument12 pagesBlockchain Application On Financial Sector in The FutureVincent RinaldyPas encore d'évaluation
- Tom Vande Stouwe: 755 Caro Ct. Phone 803-233-3724 Chapin, SC 29036 NYC 212-380-1680Document4 pagesTom Vande Stouwe: 755 Caro Ct. Phone 803-233-3724 Chapin, SC 29036 NYC 212-380-1680Jeremiah MartinezPas encore d'évaluation
- TLDK NginxDocument3 pagesTLDK NginxmaasaPas encore d'évaluation
- USM’s Shriram Mantri Vidyanidhi Info Tech Academy PG DAC Feb 19 Data Base Technologies Question BankDocument50 pagesUSM’s Shriram Mantri Vidyanidhi Info Tech Academy PG DAC Feb 19 Data Base Technologies Question BankOm Ji100% (1)
- Regulatory requirements for renewable energy projectsDocument3 pagesRegulatory requirements for renewable energy projectsAnil PooniaPas encore d'évaluation
- Ob Ia2Document24 pagesOb Ia2Sougata SamadderPas encore d'évaluation
- Numerical Analysis - MTH603 Handouts Lecture 21Document5 pagesNumerical Analysis - MTH603 Handouts Lecture 21roshanpateliaPas encore d'évaluation
- Compal LA-7201P M/B Schematic and NotesDocument53 pagesCompal LA-7201P M/B Schematic and NotesmilanTT11Pas encore d'évaluation
- SQL Server TutorialDocument25 pagesSQL Server TutorialDhiren PatelPas encore d'évaluation
- How To Retrieve License From Deltav Dongle and How To Load It Using Hasphl PDFDocument9 pagesHow To Retrieve License From Deltav Dongle and How To Load It Using Hasphl PDFyuriy2fedorovych0% (1)