Académique Documents
Professionnel Documents
Culture Documents
AI-driven security measures to prevent fraud
Transféré par
Ajin Paul0 évaluation0% ont trouvé ce document utile (0 vote)
42 vues5 pagesThe document discusses preventative measures and security threats related to mobile wallet applications and transactions. It outlines several artificial intelligence-driven security measures used by banks to detect fraudulent transactions and advise users to uninstall rogue apps. Additionally, it discusses setting app passwords for wallets, only accepting payments via QR codes, not keeping too much money in wallets, and not saving card info when recharging wallets. The document then lists potential security threats like phishing attacks, social engineering, malware installation, and reverse engineering of mobile wallet apps. It concludes with possible security measures apps can take like secure coding practices and source code protections.
Description originale:
Titre original
PAYTM PHASE 3
Copyright
© © All Rights Reserved
Formats disponibles
DOCX, PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentThe document discusses preventative measures and security threats related to mobile wallet applications and transactions. It outlines several artificial intelligence-driven security measures used by banks to detect fraudulent transactions and advise users to uninstall rogue apps. Additionally, it discusses setting app passwords for wallets, only accepting payments via QR codes, not keeping too much money in wallets, and not saving card info when recharging wallets. The document then lists potential security threats like phishing attacks, social engineering, malware installation, and reverse engineering of mobile wallet apps. It concludes with possible security measures apps can take like secure coding practices and source code protections.
Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme DOCX, PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
42 vues5 pagesAI-driven security measures to prevent fraud
Transféré par
Ajin PaulThe document discusses preventative measures and security threats related to mobile wallet applications and transactions. It outlines several artificial intelligence-driven security measures used by banks to detect fraudulent transactions and advise users to uninstall rogue apps. Additionally, it discusses setting app passwords for wallets, only accepting payments via QR codes, not keeping too much money in wallets, and not saving card info when recharging wallets. The document then lists potential security threats like phishing attacks, social engineering, malware installation, and reverse engineering of mobile wallet apps. It concludes with possible security measures apps can take like secure coding practices and source code protections.
Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme DOCX, PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 5
PREVENTATIVE MEASURES
1)Artificial Intelligence(AI)-driven security measures
to safeguard users from fraudsters and protect their
transactions.
One of the new features analyses 'rogue' apps on
user devices which might trigger fraudulent
transactions and advises users to uninstall them.
The bank is also leveraging AI to instantly detect
suspicious transactions. Depending on the
identified threat level of a transaction, the AI either
slows it down or completely blocks the payment
from getting completed, the company said in a
statement. No transactions will be possible until the
user uninstalls that fraudulent app.
2. Use app password: Paytm recently rolled out an app
password feature for Paytm wallet. The features ensures
that the money in wallet stays safe even if one loses or
misplaces the phone. To set up the password, first set the
Phone's default Android security password. Go to
Phone's Settings > Security > Screen Lock > Choose
Screen Loc/ Pin/ Password/ Pattern or Fingerprint to
protect the phone. Now open the Paytm app & click on
"Pay" or "Passbook". You will be prompted to enable
this optional feature. Now click on Add Security
Feature. User will be asked to reconfirm your Phone's
Pin/Password/Pattern/Fingerprint depending on what is
selected as the default protection. Once confirmed, the
new App Password is now set.
3. If you are accepting a Paytm payment, do so through
QR code. Quick Response Codes or QR codes are
unique and encrypted.
4. Don't keep too much money in your wallet. There's no
such thing as unhackable. Every information you put on
web is linked to one another and hacking your Paytm
wallet is no rocket science.
5. Don't save your card while recharging wallet:
although little inconvenient it is always better not to
save the card info while a transaction.
SECURITY THREATS
Phishing attacks: Mobiles have personal and
corporate information of customer which may to
carry out sophisticated attacks. These attacks user by
phishing emails. It is an attempt to trap a user to
disclose the information.
Social engineering: In social engineering, user
data available in the public domain and the attackers
can steal it from there. This information monetized or
sold in underground market forums or used for
fraudulent payments. Sometimes attackers use this
theft information as their identity.
Unintentional installation of rogue and malware
applications: Attackers will install malware by
malicious attachment, Redirecting the user to a
malicious URL, insecure WiFi hotspots, a network
spoofing attack, fake access point with same network,
fake website, etc. Then use user information for mobile
wallet payment.
Mobile Operating System Access Permissions:
Users give certain permission to OS access, that can be
use by attackers to access sensitive data and harm
the mobile application
Mobile Wallet Applications Threats
Reverse engineering: Reverse engineering offers to
attack on hardcoded passwords and encryption keys
like data. For that attackers have high level of
understanding of mobile wallet payment applications.
Tampering with the mobile payment application
and the use of rootkits: An attacker may choose to
backdoor a mobile payment application to capture
login details and send these to an attacker controlled
server. By this attacker can downloading and uploading
any data from user application. This is a very realistic
threat on mobile devices.
Installation of rootkits/malware: Discussed in
mobile device threats.
Mobile Operating System Access Permissions:
Discussed in mobile application user threats. The
Possible Vulnerabilities of Mobile Wallet Apps are:
Hardcoded secrets as private keys.
Missing to disable code debugging routines.
Unsigned production binaries.
Credit card provisioning weaknesses like stolen
credit cards to affect sensitive data.
Weaknesses in biometric identification for initial
authorization of transactions
. S/W vulnerabilities and weaknesses in third
party applications that provide access to mobile wallets.
Weaknesses in payment authorization provisioning
with mobile paired smartwatch device.
Credit/debit card not stored encrypted in Secure
Element or processed in Trusted Execution
Environment.
Weak PINs exposing them to brute force attacks.
Insecure communication channels with Point of Sale
(POS) contactless terminals.
Insecure tokens used in Magnetic Secure
Transmission (MST) connections.
Poor signal strength for MST processing. Possible
Security Measures of Mobile Wallet Applications
Adopt secure coding practices and secure code
reviews manual and automated via tools.
Source code complication an untrusted code
detection.
Anti-debug and Integrity source code protections.
White-box cryptography.
Secure application provisioning through trusted
application stores.
Takedown rogue applications from unauthorized
application stores.
Vous aimerez peut-être aussi
- Digital Dangers and It's Security Measures: Afzaal Khan Sub Inspector MP PoliceDocument34 pagesDigital Dangers and It's Security Measures: Afzaal Khan Sub Inspector MP PoliceRakesh SoniPas encore d'évaluation
- UNIT-5 (Security Environment) January 10, 2023Document31 pagesUNIT-5 (Security Environment) January 10, 2023Dev ParmarPas encore d'évaluation
- Unit IIIDocument90 pagesUnit IIIKhushbu BoraPas encore d'évaluation
- 12063690Document70 pages12063690saba janelidzePas encore d'évaluation
- Common Scams On Mobile DevicesDocument4 pagesCommon Scams On Mobile Devicessam shaikhPas encore d'évaluation
- Information Security Essentials for Mobile AppsDocument21 pagesInformation Security Essentials for Mobile Appsyogesh_8488Pas encore d'évaluation
- OTP Based 2F AuthenticationDocument16 pagesOTP Based 2F AuthenticationCao ThủPas encore d'évaluation
- Mobile Devices and WirelessDocument21 pagesMobile Devices and WirelessabdulhafithPas encore d'évaluation
- Mobile Banking Security and Why ItDocument2 pagesMobile Banking Security and Why ItAjayPanickerPas encore d'évaluation
- Unit 3 SE PDFDocument78 pagesUnit 3 SE PDFSwetha DPas encore d'évaluation
- How Secure R Current Mobile OSDocument17 pagesHow Secure R Current Mobile OSMadhav SabarishPas encore d'évaluation
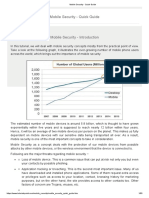
- Mobile Security Quick GuideDocument63 pagesMobile Security Quick GuideVenkatPas encore d'évaluation
- USB AttackDocument26 pagesUSB AttackRahib RahmanPas encore d'évaluation
- Cyber Security Awareness ManualDocument37 pagesCyber Security Awareness ManualDarmoni LaishramPas encore d'évaluation
- Mobile WalletDocument14 pagesMobile WalletMelanie MorandartePas encore d'évaluation
- Device For Off Line Micro Payments Resistant To Fraud by Using Wearable Physiological SensorsDocument3 pagesDevice For Off Line Micro Payments Resistant To Fraud by Using Wearable Physiological SensorsNationalinstituteDsnrPas encore d'évaluation
- All The 12 Payment Enabling Technologies & 54 Illustrative Companies, A White PaperDocument15 pagesAll The 12 Payment Enabling Technologies & 54 Illustrative Companies, A White PaperLtpAdminPas encore d'évaluation
- Presentation Top 7 Mobile Security Threats in 2020 (Ahmad f2008, Hidayat f2036, Syafiq f2056)Document18 pagesPresentation Top 7 Mobile Security Threats in 2020 (Ahmad f2008, Hidayat f2036, Syafiq f2056)F2056 SyafiqPas encore d'évaluation
- Cellular Network Fraud & Security, Jamming Attack and DefensesDocument8 pagesCellular Network Fraud & Security, Jamming Attack and Defensesamar kingPas encore d'évaluation
- Atm & ThreatsDocument12 pagesAtm & ThreatsDeepika PriyaPas encore d'évaluation
- Trusteer Mobile Risk EngineDocument4 pagesTrusteer Mobile Risk EngineAugust Majer IIIPas encore d'évaluation
- Information Systems For Managers JUNE 2022Document11 pagesInformation Systems For Managers JUNE 2022Rajni KumariPas encore d'évaluation
- Chapter 1: Introducing Anti-Fraud ATM SecurityDocument4 pagesChapter 1: Introducing Anti-Fraud ATM SecurityShrikant ChamlatePas encore d'évaluation
- Hardware Based Anti-Theft System For SmartphonesDocument4 pagesHardware Based Anti-Theft System For SmartphonesMaxbuub AxmedPas encore d'évaluation
- CERT-In NCSAM Book - 20231002 - 182603 - 0000Document17 pagesCERT-In NCSAM Book - 20231002 - 182603 - 0000winkrish8805Pas encore d'évaluation
- Unit 3Document81 pagesUnit 3gbuzzz31Pas encore d'évaluation
- 13 E WalletsDocument14 pages13 E WalletsGurjit SinghPas encore d'évaluation
- The Following Are The Most Serious Security Risks Around Online BankingDocument3 pagesThe Following Are The Most Serious Security Risks Around Online BankingJessica G HollerPas encore d'évaluation
- Iot Security and PrivacyDocument37 pagesIot Security and PrivacyYashraj Motwani 18BEC0762Pas encore d'évaluation
- Android SecurityDocument32 pagesAndroid SecurityPeerukkan Nazrin Beham Assistant ProfessorPas encore d'évaluation
- Rishi Tiwari - E Com. AssignDocument3 pagesRishi Tiwari - E Com. AssignRishiPas encore d'évaluation
- Mobile Wallet Payments Recent Potential Threats AnDocument8 pagesMobile Wallet Payments Recent Potential Threats AnSi kwok liangPas encore d'évaluation
- FcsDocument11 pagesFcsMvk MvkPas encore d'évaluation
- MFA Study and ResearchDocument8 pagesMFA Study and ResearchI'm sunflowerPas encore d'évaluation
- 2FA Security IssuesDocument15 pages2FA Security Issuesabc3728372832Pas encore d'évaluation
- IT NMIMS AssignmentDocument13 pagesIT NMIMS AssignmentTajinder MatharuPas encore d'évaluation
- Use of Biometrics To Tackle ATM Fraud: Lawan Ahmed MohammedDocument5 pagesUse of Biometrics To Tackle ATM Fraud: Lawan Ahmed MohammedalamsboyPas encore d'évaluation
- Materi Chpt.5 E-Commerce Security and Payment SystemsDocument37 pagesMateri Chpt.5 E-Commerce Security and Payment Systemsdonny antaraPas encore d'évaluation
- How 36 Million Euros Was Stolen in a Multi-Country Eurograbber Malware AttackDocument2 pagesHow 36 Million Euros Was Stolen in a Multi-Country Eurograbber Malware AttackChristian Jay HallazgoPas encore d'évaluation
- Cyber CrimeDocument7 pagesCyber CrimePOORVI AGRAWAL Jaipuria-JaipurPas encore d'évaluation
- Automatic Teller Machine System Security by Using Mobile SMS CodeDocument7 pagesAutomatic Teller Machine System Security by Using Mobile SMS CodeSaad BashirPas encore d'évaluation
- Do New Mobile Devices in Enterprises Pose A Serious Security Threat?Document5 pagesDo New Mobile Devices in Enterprises Pose A Serious Security Threat?Anonymous IlrQK9HuPas encore d'évaluation
- Malware: Iii. Motives To Create Mobile MalwareDocument10 pagesMalware: Iii. Motives To Create Mobile MalwareNida NawazPas encore d'évaluation
- Pear Hishing Ttack: How The Attack Works?Document15 pagesPear Hishing Ttack: How The Attack Works?Ranjith KumarPas encore d'évaluation
- Phishing-WPS OfficeDocument13 pagesPhishing-WPS OfficeAlyana SweetyPas encore d'évaluation
- awaz mDocument11 pagesawaz mawaz mustafaPas encore d'évaluation
- Input-processing-output controls ensure data integrityDocument6 pagesInput-processing-output controls ensure data integrityAamirPas encore d'évaluation
- Mobile ThreatsDocument4 pagesMobile ThreatssupptbuddyPas encore d'évaluation
- Threats To DataDocument11 pagesThreats To Dataapi-317018886Pas encore d'évaluation
- Security AlertpsgshhshshhDocument1 pageSecurity AlertpsgshhshshhLalit KumarPas encore d'évaluation
- Computer ScienceDocument1 pageComputer ScienceYolanda Flo SPas encore d'évaluation
- Understanding The Risks of Mobile AppsDocument7 pagesUnderstanding The Risks of Mobile AppsblussierttPas encore d'évaluation
- 5 Facts You Should Know About Mobile Security - ZimperiumDocument7 pages5 Facts You Should Know About Mobile Security - ZimperiumGratouillasPas encore d'évaluation
- Security Issues in Mobile Application DevelopmentDocument14 pagesSecurity Issues in Mobile Application DevelopmentSaurav YadavPas encore d'évaluation
- Mobile Wallet Payments Recent Potential Threats AnDocument8 pagesMobile Wallet Payments Recent Potential Threats AnAisha SinghPas encore d'évaluation
- Mobile Wallet Payments Recent Potential Threats AnDocument8 pagesMobile Wallet Payments Recent Potential Threats AnAisha SinghPas encore d'évaluation
- Reading Advances in Sciences and TechnologyDocument1 pageReading Advances in Sciences and TechnologyDRISS BAOUCHEPas encore d'évaluation
- A Secure Web Authentication ProtocolDocument18 pagesA Secure Web Authentication ProtocolLavanyaPas encore d'évaluation
- Infromation System For Mangers AssignmentDocument7 pagesInfromation System For Mangers AssignmentHimanshu DhanukaPas encore d'évaluation
- Fsa Project PDFDocument6 pagesFsa Project PDFAjin PaulPas encore d'évaluation
- Sample Questions IA Level II 23.1.2017Document16 pagesSample Questions IA Level II 23.1.2017Shemeem S100% (1)
- Roots Institute of Financial Markets RifmDocument24 pagesRoots Institute of Financial Markets RifmUtpal LahkarPas encore d'évaluation
- Banking: Lesson 15Document12 pagesBanking: Lesson 15vkfzrPas encore d'évaluation
- Sample Questions IA Level II 23.1.2017Document16 pagesSample Questions IA Level II 23.1.2017Shemeem S100% (1)
- Businss Analytics-Ajin PDFDocument18 pagesBusinss Analytics-Ajin PDFAjin PaulPas encore d'évaluation
- Factors Impacting Bank Employee Job SatisfactionDocument34 pagesFactors Impacting Bank Employee Job SatisfactionAjin PaulPas encore d'évaluation
- Operation Research Assignment SubmissionDocument20 pagesOperation Research Assignment SubmissionAjin PaulPas encore d'évaluation
- EDITED mm2 Pro Phase1 XIAOMIDocument6 pagesEDITED mm2 Pro Phase1 XIAOMIAjin PaulPas encore d'évaluation
- Factors Impacting Bank Employee Job SatisfactionDocument34 pagesFactors Impacting Bank Employee Job SatisfactionAjin PaulPas encore d'évaluation
- 03 - Litreature Review PDFDocument10 pages03 - Litreature Review PDFMõørthï ShãrmâPas encore d'évaluation
- AMFI Sample 500 QuestionsDocument36 pagesAMFI Sample 500 Questionssukriti_43784905100% (3)
- Saintgits Institute of Management: Environment and Solve Business ProblemsDocument11 pagesSaintgits Institute of Management: Environment and Solve Business ProblemsAjin PaulPas encore d'évaluation
- 03 - Litreature Review PDFDocument10 pages03 - Litreature Review PDFMõørthï ShãrmâPas encore d'évaluation
- CamScanner Scans PDFs from PhotosDocument5 pagesCamScanner Scans PDFs from PhotosAjin PaulPas encore d'évaluation
- I. Sustainable DevelopmentDocument20 pagesI. Sustainable DevelopmentAjin PaulPas encore d'évaluation
- Organisational BehaviourDocument7 pagesOrganisational BehaviourAjin PaulPas encore d'évaluation
- Business Analytics in 40 CharactersDocument6 pagesBusiness Analytics in 40 CharactersAjin PaulPas encore d'évaluation
- Banking in IndiaDocument6 pagesBanking in IndiaAjin PaulPas encore d'évaluation
- Decision TREEDocument19 pagesDecision TREEAjin PaulPas encore d'évaluation
- Private-Sector Banks in India - WikipediaDocument6 pagesPrivate-Sector Banks in India - WikipediaAjin PaulPas encore d'évaluation
- Dhaval Patel ResumeDocument3 pagesDhaval Patel Resumeapi-419784574Pas encore d'évaluation
- Cyber-Crime As A Service: Caas Analysis ReportDocument22 pagesCyber-Crime As A Service: Caas Analysis ReportantoniscsdPas encore d'évaluation
- Firewalls and VPNS: Principles of Information Security, 2Nd Edition 1Document45 pagesFirewalls and VPNS: Principles of Information Security, 2Nd Edition 1Nishanth KrishnamurthyPas encore d'évaluation
- Comandos Configuracion OSPFDocument6 pagesComandos Configuracion OSPFVicente LunaPas encore d'évaluation
- 003 Penetration Testing ReportDocument10 pages003 Penetration Testing ReportgurujmPas encore d'évaluation
- Nova Ran Optimization - Ran Overview: Sofian Ben Khalifa 14/nov/2017Document19 pagesNova Ran Optimization - Ran Overview: Sofian Ben Khalifa 14/nov/2017Sofian Ben KhalifaPas encore d'évaluation
- ICL TroubleshootingDocument17 pagesICL TroubleshootingnokiasiePas encore d'évaluation
- GSM Network Capacity Planning: Traffic Channels DimensioningDocument41 pagesGSM Network Capacity Planning: Traffic Channels DimensioningSushil OjhaPas encore d'évaluation
- Security Awareness TrainingDocument25 pagesSecurity Awareness TrainingMehul dubey100% (1)
- Assignment 1Document3 pagesAssignment 1radeeyjdPas encore d'évaluation
- Ajp 17Document10 pagesAjp 17Prathamesh TambekarPas encore d'évaluation
- Linux Firewall Exploration LabDocument15 pagesLinux Firewall Exploration Labdebut finPas encore d'évaluation
- Avaya CTI Recording - How To DesignDocument17 pagesAvaya CTI Recording - How To DesignPedro EsmeraldaPas encore d'évaluation
- Zebra Printer Setting NewDocument4 pagesZebra Printer Setting NewAmitPas encore d'évaluation
- Introduction To DMX PhilipsDocument27 pagesIntroduction To DMX Philipsmile1966Pas encore d'évaluation
- Wi-Fi: Wireless FidelityDocument24 pagesWi-Fi: Wireless Fidelityayushthegreat123Pas encore d'évaluation
- How To Fix A Bricked Linksys RouterDocument2 pagesHow To Fix A Bricked Linksys RouterBogdan CacuciPas encore d'évaluation
- Advanced Networking Tutorial SheetsDocument19 pagesAdvanced Networking Tutorial SheetsxyzkingPas encore d'évaluation
- Huawei Imaster NCE-CampusInsight Data SheetDocument18 pagesHuawei Imaster NCE-CampusInsight Data Sheets.bruno1Pas encore d'évaluation
- BRKSEC-3001 - Advanced IKEv2 ProtocolDocument64 pagesBRKSEC-3001 - Advanced IKEv2 ProtocolSergey DenisenkoPas encore d'évaluation
- Analyze NAT Translation in Wireshark LabDocument4 pagesAnalyze NAT Translation in Wireshark LabHero NakamuraPas encore d'évaluation
- CCNA 200-301 September 2020-v1.2Document134 pagesCCNA 200-301 September 2020-v1.2Erik LimPas encore d'évaluation
- Secret Code FujitsuDocument6 pagesSecret Code FujitsuAku AfiPas encore d'évaluation
- Chapter 3Document74 pagesChapter 3Berhane KiflePas encore d'évaluation
- EMC Isilon OneFS 8.0.1 CLI Administration GuideDocument1 096 pagesEMC Isilon OneFS 8.0.1 CLI Administration GuideNoso Opforu0% (1)
- Alaba Othman Et Al 2017 Internet of Things - Survey PDFDocument19 pagesAlaba Othman Et Al 2017 Internet of Things - Survey PDFLaura Craig100% (1)
- CyrusOne 2019-PB MegaportDocument3 pagesCyrusOne 2019-PB MegaportLeon MutambalaPas encore d'évaluation
- Quanta 0P5A DA0P5AMB6D00 Rev 1A PDFDocument46 pagesQuanta 0P5A DA0P5AMB6D00 Rev 1A PDFDeMzo SMpPas encore d'évaluation
- Fact Sheet CSU501 enDocument2 pagesFact Sheet CSU501 enankurPas encore d'évaluation
- (FreeCourseWeb - Com) Com...Document516 pages(FreeCourseWeb - Com) Com...cata081100% (4)