Académique Documents
Professionnel Documents
Culture Documents
Likewise Enterprise Version 4.0 Administrators Guide
Transféré par
Likewise SoftwareCopyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Likewise Enterprise Version 4.0 Administrators Guide
Transféré par
Likewise SoftwareDroits d'auteur :
Formats disponibles
9 Product Documentation
Likewise 4.0
Administrator’s Guide
IN THIS DOCUMENT
Abstract
• Managing Likewise licenses.
Likewise seamlessly joins Linux, Unix, and Mac OS X computers to
• Deploying and troubleshooting
the Likewise Agent. Microsoft Active Directory so that you can centrally manage all your
• Joining an Active Directory
computers, authenticate users, authorize access to resources, and apply
domain. group policies to non-Windows computers. This guide describes how to
• Using the Likewise Console. administer Likewise 4.0, including both the Likewise Console and the
• Managing cells, users, groups.
Likewise Agent. The guide covers deploying and troubleshooting the agent,
managing Linux and Unix users in Active Directory, and applying group
• Generating reports.
policies.
• Migrating users and groups.
• Applying group policies.
Copyright © 2007 Likewise Software. All rights reserved. 1
Product Documentation 9
Likewise 4.0: Administrator’s Guide
The information contained in this document represents the current view of Likewise
Software on the issues discussed as of the date of publication. Because Likewise
Software must respond to changing market conditions, it should not be interpreted to be a
commitment on the part of Likewise, and Likewise Software cannot guarantee the
accuracy of any information presented after the date of publication.
These documents are for informational purposes only. LIKEWISE SOFTWARE MAKES
NO WARRANTIES, EXPRESS OR IMPLIED.
Complying with all applicable copyright laws is the responsibility of the user. Without
limiting the rights under copyright, no part of this document may be reproduced, stored in,
or introduced into a retrieval system, or transmitted in any form, by any means
(electronic, mechanical, photocopying, recording, or otherwise), or for any purpose,
without the express written permission of Likewise Software.
Likewise may have patents, patent applications, trademarks, copyrights, or other
intellectual property rights covering subject matter in this document. Except as expressly
provided in any written license agreement from Likewise, the furnishing of this document
does not give you any license to these patents, trademarks, copyrights, or other
intellectual property.
© 2007 Likewise Software. All rights reserved.
Likewise and the Likewise logo are either registered trademarks or trademarks of
Likewise Software in the United States and/or other countries. All other trademarks are
property of their respective owners.
Likewise Software
15395 SE 30th Place, Suite #140
Bellevue, WA 98007
USA
Copyright © 2007 Likewise Software. All rights reserved. 2
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Table of Contents
INTRODUCTION............................................................................8
About Likewise....................................................................................................8
Overview of Components and Concepts..........................................................9
Contact Technical Support ..............................................................................10
MANAGING LICENSES...............................................................11
About License Management ............................................................................11
Import a License File ........................................................................................11
Assign a License to a Computer .....................................................................11
Set a License Key .............................................................................................12
Revoke a License..............................................................................................13
Delete a License ................................................................................................13
About Evaluation Licenses ..............................................................................13
DEPLOYING THE AGENT...........................................................15
About the Likewise Agent ................................................................................15
Check System Health Before Installing the Agent ........................................16
Install the Agent on a Linux Computer...........................................................21
Install the Agent on a Mac Computer .............................................................22
Uninstall the Agent on a Linux or Unix Computer.........................................23
Uninstall the Agent on a Mac...........................................................................23
Make Sure Outbound Ports Are Open ............................................................23
Command-Line Tools .......................................................................................24
Using Command-Line Tools to Deploy Agents .............................................25
JOINING A DOMAIN ...................................................................26
Join a Linux Computer to Active Directory....................................................26
Join a Mac Computer to Active Directory ......................................................28
Join Active Directory Without Changing /etc/hosts ......................................29
Join Active Directory with the Command Line ..............................................30
Options and Commands .................................................................................32
Rename a Joined Computer ............................................................................33
Interactive Linux Sign-On ................................................................................36
Leave a Domain.................................................................................................36
USING THE LIKEWISE CONSOLE.............................................38
WORKING WITH CELLS.............................................................41
Creating Cells..................................................................................................42
The Default Cell ..............................................................................................42
Copyright © 2007 Likewise Software. All rights reserved. 3
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Linking Cells....................................................................................................42
Cell Manager...................................................................................................43
Migrating NIS Domains ...................................................................................43
Using Multiple Cells ........................................................................................44
Migration Tool .................................................................................................45
Orphaned Objects Tool...................................................................................45
Manage Cells .....................................................................................................48
Start Cell Manager ..........................................................................................49
Delegate Management....................................................................................49
Change Permissions of a Cell, Group, or User...............................................50
Add a Cell........................................................................................................50
Give a User Access to a Cell ..........................................................................51
Give a Group Access to a Cell........................................................................51
Filter Cells .......................................................................................................51
Connect to a Different Domain........................................................................51
Assign a Group ID.............................................................................................52
Set a Group Alias ..............................................................................................52
Specify a User's ID and Unix or Linux Settings .............................................53
Apply Unix or Linux Settings to Multiple Users.............................................55
Disable a User ...................................................................................................56
Set the Default Home Directory .......................................................................56
Set the Home Directory for a Cell ...................................................................57
Set the Home Directory for Multiple Users .....................................................57
Set the Home Directory for a Single User.......................................................58
Set the Default Login Shell ..............................................................................58
Set the Login Shell for a Cell ..........................................................................58
Set the Login Shell for Multiple Users.............................................................59
Set the Login Shell for a Single User ..............................................................59
MIGRATING USERS AND FINDING ORPHANED OBJECTS....61
Migrate Users to Active Directory ...................................................................61
What You Need Before You Begin .................................................................61
Run the Migration Tool....................................................................................62
Find Orphaned Objects ....................................................................................64
GENERATING REPORTS ...........................................................65
Create a Computer Access Report .................................................................66
Create a Forest Users and Groups Report.....................................................67
Create a Group Access Report........................................................................68
Create a Group Membership Report ...............................................................69
Create a User Access Report...........................................................................70
Show Computer Access by Cell ......................................................................71
Show Duplicate UIDs, GIDs, Login Names, and Group Aliases...................73
Copyright © 2007 Likewise Software. All rights reserved. 4
Product Documentation 9
Likewise 4.0: Administrator’s Guide
WORKING WITH GROUP POLICIES..........................................76
User Settings...................................................................................................77
The Group Policy Agent..................................................................................78
The GPO Refresh Tool ...................................................................................78
Inheritance ......................................................................................................78
Filtering by Target Platform.............................................................................79
Create or Edit a Group Policy ..........................................................................80
Apply a Group Policy to a Cell.........................................................................81
Set Target Platforms.........................................................................................81
Create and Test a Sudo Group Policy ............................................................83
Create a Sudo Group Policy ...........................................................................83
Test the Sudo Group Policy ............................................................................86
Test Sudo Security..........................................................................................87
About User Settings .........................................................................................88
Storing Gnome GConf Preferences ................................................................90
GConf Per-User Daemon................................................................................90
GConf Tool......................................................................................................90
Schema Files ..................................................................................................90
Add Gnome Schemas.......................................................................................91
Example: Set a Firefox Home Page URL ........................................................94
Example: Set the Default Web Browser for a Gnome Desktop ....................96
Display Settings ................................................................................................97
Change the Screen Saver Theme Interval .....................................................97
Display a Keyboard in the Screen Saver ........................................................98
Display a Screen Saver Logout Option...........................................................98
Display a Switch User Option with the Screen Saver .....................................99
Display Screen Saver When a Session Is Idle .............................................100
Embed a Keyboard Command in the Screen Saver.....................................100
Lock the Screen with the Screen Saver........................................................101
Run a Logout Command from the Screen Saver Dialog ..............................102
Set the Screen Lockout Interval....................................................................103
Set the Screen Saver Idle Delay...................................................................103
Set the Time till the Logout Option Is Available ............................................104
File System Settings.......................................................................................105
Automount a File System..............................................................................105
Create Directories, Files, and Links ..............................................................106
Specify the File System Mounts (fstab) ........................................................107
Likewise Settings............................................................................................108
Acquire Kerberos Tickets on Logon..............................................................108
Allow Access to Samba Server Null-Password Accounts ............................109
Allow Cached Logons ...................................................................................109
Allow Logon Rights .......................................................................................110
Allow Offline Logon Support .........................................................................111
Copy Template Files When Creating a Home Directory...............................112
Create a .k5login File in a User's Home Directory........................................112
Create a Home Directory for a User Account at Logon ................................113
Copyright © 2007 Likewise Software. All rights reserved. 5
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Digitally Sign Client Communications ...........................................................114
Digitally Sign Server Communications..........................................................115
Log on using Kerberos Authentication..........................................................116
Log Winbind Debugging Information ............................................................116
Refresh Kerberos Tickets .............................................................................117
Replace Spaces in Names with a Character ................................................118
Send Encrypted Passwords to Third-Party SMB Servers ............................119
Set Permissions with a File Creation Mask ..................................................119
Set the Depth of Nested Group Expansion...................................................120
Set the ID Mapping Cache Expiration Time..................................................121
Set the ID Mapping Negative Cache Expiration Time ..................................122
Set the Machine Account Password Expiration Time...................................122
Set the Maximum Tolerance for Kerberos Clock Skew ................................123
Set the Minimum UID-GID Value ..................................................................123
Set the Samba Hostname Resolver Cache Timeout ....................................124
Set the Samba Server LDAP Connection Timeout.......................................125
Set the Winbind Cache Expiration Time .......................................................125
Show a Denied Logon Rights Message........................................................126
Show a Password Expiration Warning..........................................................127
Turn Off Client LANMAN Authentication.......................................................127
Turn On Client NTLMv2 Authentication ........................................................128
Logging and Auditing Settings......................................................................129
Create a SysLog Policy.................................................................................129
Rotate Logs...................................................................................................131
Secure Computers with an AppArmor Policy................................................132
Secure Computers with an SELinux Policy ..................................................133
Message Settings............................................................................................136
Display a Message of the Day ......................................................................136
Display a Message with a Login Prompt Policy ............................................136
Message Settings............................................................................................137
Display a Message of the Day ......................................................................137
Display a Message with a Login Prompt Policy ............................................138
Security Settings.............................................................................................139
Define a Sudo Policy.....................................................................................139
Require Complex Passwords........................................................................140
Set the Maximum Password Age..................................................................141
Set the Minimum Password Age...................................................................142
Set the Minimum Password Length ..............................................................142
Task Settings...................................................................................................143
Run a Script File ...........................................................................................143
Schedule Cron Jobs with a crontab or cron.d Policy ....................................144
Mac System Preferences................................................................................146
Allow Bluetooth Devices to Find the Computer ............................................146
Allow Bluetooth Devices to Wake the Computer ..........................................146
Block UDP Traffic on a Mac..........................................................................147
Disable Automatic User Login on a Mac.......................................................148
Copyright © 2007 Likewise Software. All rights reserved. 6
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Log Firewall Activity on a Mac ......................................................................148
Secure System Preferences on a Mac .........................................................149
Set DNS Servers and Search Domains on a Mac ........................................149
Show Bluetooth Status in the Menu Bar .......................................................150
Turn Bluetooth On or Off...............................................................................151
Turn On AppleTalk ........................................................................................152
Use Firewall Stealth Mode on a Mac ............................................................152
Use Secure Virtual Memory on a Mac ..........................................................153
SINGLE SIGN-ON......................................................................154
Single Sign On ................................................................................................154
About Single Sign-On ...................................................................................154
FTP ...............................................................................................................154
Logging In and Verifying Kerberos Tickets ...................................................156
Perform an Authenticated LDAP Search ......................................................157
rlogin .............................................................................................................161
rsh .................................................................................................................162
Telnet ............................................................................................................163
Use Firefox to Single Sign-On to Intranet Sites ............................................165
TROUBLESHOOTING THE AGENT .........................................166
Check Authentication .....................................................................................166
Check the Status of the Authentication Daemon ........................................166
Check the Status of the Group Policy Daemon ...........................................167
Check the Version and Build Number ..........................................................167
Clear the Authentication Cache.....................................................................168
Determine a Computer's FQDN .....................................................................170
Force Group Policies to Refresh ...................................................................170
Generate a Domain-Join Log .........................................................................170
Generate a Group Policy Agent Debug Log.................................................171
Generate a Network Trace..............................................................................171
Generate a PAM Debug Log...........................................................................172
Generate an Authentication Agent Debug Log............................................172
Make Sure Outbound Ports Are Open ..........................................................173
Restart the Authentication Daemon..............................................................173
Restart the Group Policy Daemon ................................................................174
CONTACT TECHNICAL SUPPORT ..........................................175
PLATFORM SUPPORT .............................................................176
Copyright © 2007 Likewise Software. All rights reserved. 7
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Introduction
This guide describes how to deploy the Likewise Agent; how to
administer product licenses; how to use Likewise to join computers
running Linux, Unix, or Mac OS X to Microsoft Active Directory; how to
manage groups, users, and machine accounts; and how to define group
policies.
The target audience is network directory administrators who manage
access to workstations, servers, and other network resources within
Active Directory. The guide assumes that you have a working knowledge
of how to administer Active Directory as well as computers running
Linux, Unix, and Mac OS X.
This guide assumes that you have installed Likewise. For instructions on
how to install Likewise, see the Installation Guide.
About Likewise
Likewise seamlessly joins Linux, Unix, and Mac OS X computers to
Microsoft Active Directory so that you can centrally manage all your
computers, authenticate users, control access to resources, and apply
group policies to non-Windows computers.
By joining non-Windows computers to Active Directory – a secure,
scalable, stable, and proven identity management system – Likewise
gives you the power to manage all your users' identities in one place, use
the highly secure Kerberos 5 protocol to authenticate users in the same
way on all your systems, apply granular access controls to sensitive
resources, and centrally administer Linux, Unix, Mac, and Windows
computers with group policies. The Likewise group policies are simple to
manage because they are integrated into the Microsoft Group Policy
Object Editor.
Likewise comprises two main components: The Likewise Console and
the Likewise Agent.
The console runs on a Windows administrative workstation that can
connect to the Active Directory domain controller and includes tools that
are integrated into Active Directory Users and Computers, the Group
Policy Management Console, and the Group Policy Object Editor.
Copyright © 2007 Likewise Software. All rights reserved. 8
Product Documentation 9
Likewise 4.0: Administrator’s Guide
The agent runs on Linux, Unix, and Mac OS computers so that you can
join them to a domain and manage them within Active Directory.
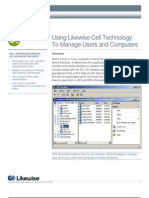
Overview of Components and Concepts
Likewise comprises two main components: The Likewise Console and
the Likewise Agent.
The agent runs on Linux, Unix, and Mac OS computers so that you can
join them to a domain and manage them within Active Directory. The
agent integrates with the operating system to implement the mapping for
any application that uses the name service (nsswitch) or pluggable
authentication module (PAM). The agent also pulls group policies and
enforces them.
The console runs on a Windows administrative workstation that connects
to an Active Directory domain controller. The console software includes
tools that are automatically integrated into Active Directory Users and
Computers, the Group Policy Management Console, and the Group
Policy Object Editor. You use the console and its tools to manage Linux,
Unix, and Mac OS X computers within Active Directory. Here’s what the
console looks like:
Copyright © 2007 Likewise Software. All rights reserved. 9
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Cells
Active Directory uses organizational units to group related objects in a
common container so that you can manage the objects in a uniform and
consistent way. With Likewise, you can associate cells with
organizational units to map Active Directory users to user identifiers
(UIDs) and group identifiers (GIDs). A cell is, in effect, a custom mapping
of Active Directory users to UIDs and GIDs.
When you associate a cell with an organizational unit, Linux and Unix
computers that are in the OU (or an OU nested in it) use the cell to map
AD users to UIDs and GIDs. By using cells, you can map a user to
different UIDs and GIDs for different computers.
Contact Technical Support
For either post-sales technical support or for free technical support
during an evaluation period, please visit the Likewise support Web page
at http://www.likewisesoftware.com/support/. You can use the support
page to register for support, submit incidents, and receive direct
technical assistance.
Technical support may ask for your Likewise version, Linux version, and
Microsoft Windows version. To find the Likewise product version, in the
Likewise Console, on the menu bar, click Help, and then click About.
Copyright © 2007 Likewise Software. All rights reserved. 10
Product Documentation
Likewise 4.0: Administrator’s Guide
Managing Licenses
About License Management
The console's License Management tab lets you manage the assignment
of Likewise licenses.
To obtain additional licenses or to convert from a trial to a full license,
please visit the Likewise web site or email sales@likewisesoftware.com.
For information about installing Likewise, see the Installation Guide at
http://www.likewisesoftware.com/resources/product_documentation/.
View the License Key on a Computer
To view the license key that is installed on a Unix, Linux, or Mac OS X
computer, execute the following command at the shell prompt:
/usr/centeris/bin/setkey-gui
or
/usr/centeris/bin/setkey-cli
Import a License File
By using the Likewise Console, you can import a file that contains
licenses.
1. In the Likewise Console, click the License Management tab.
2. Under Tasks, click Import License File.
3. Locate the file that contains the licenses, and then click Open.
The licenses appear in the table.
Assign a License to a Computer
Likewise automatically assigns licenses to computers running the
Likewise Agent when the computers connect to the domain. You can,
however, manually assign a license to a Unix or Linux computer in an
Active Directory domain.
1. In the Likewise Console, click the License Management tab.
Copyright © 2007 Likewise Software. All rights reserved. 11
Product Documentation 9
Likewise 4.0: Administrator’s Guide
2. In the list of licenses, under Key, click the license that you want to
assign.
3. Under Tasks, click Assign License.
4. In the Select Computer dialog box, click Locations, select the
location that contains the computer you want, and then click OK.
5. In the Enter the object names to select box, type the name of one
or more computers -- for example, AppSrvSea-1. Separate multiple
entries with semicolons. For a list of examples, click examples.
6. Click Check Names, and then click OK.
Tip: To use additional criteria to search for and select computers,
click Advanced. Then, to show more information about a computer
in the Search results box, click Columns, and add or remove
columns.
Set a License Key
When you install Likewise only within an Active Directory organizational
unit, you must manually set the license key on each Linux, Unix, and
Mac OS X computer before you join it to the organizational unit.
Set a License Key by Using the Command-Line Interface
On Linux, Unix, and Mac OS X computers, you can set a license key for
the Likewise Agent by using the shell prompt.
• At the shell prompt, execute the following command, replacing
LicenseKeyNumber with a valid license key number:
/usr/centeris/bin/setkey-gui --key LicenseKeyNumber
Set a License Key by Using the Graphical User Interface
You can set a license key for the Likewise Agent on a Linux computer or
a Unix computer running Mono by using a graphical user interface.
1. At the shell prompt, execute the following command:
/usr/centeris/bin/setkey-gui
2. In the License Key box, type a valid Likewise license number.
Copyright © 2007 Likewise Software. All rights reserved. 12
Product Documentation 9
Likewise 4.0: Administrator’s Guide
3. Click Set Key, and then click Close.
Revoke a License
1. In the Likewise Console, click the License Management tab.
2. In the list of licenses, under Key, click the license that you want to
revoke.
3. Under Tasks, click Revoke License.
4. Click OK.
Delete a License
When you rename or remove a domain from Active Directory, you might
also need to delete Likewise license keys from Active Directory.
If you rename an Active Directory domain, you must obtain new license
keys from Likewise Software. Licenses are provided on a per-domain
basis; domain licenses apply only to the fully qualified domain name or
child domain to which they were issued.
Note: You can obtain an enterprise site license from Likewise Software.
A site license does not require domain licenses or machine licenses.
1. In the Likewise Console, click the License Management tab.
2. In the list of licenses, under Key, click the license that you want to
delete.
3. Under Tasks, click Delete, and then click OK.
Tip: If you inadvertently delete a license, you can restore it by importing
the license file that contains it. For more information, see Import a
License File.
About Evaluation Licenses
30-Day Evaluation Licenses
When you install the Likewise Agent without a permanent license on a
Unix or Linux computer, a 30-day product evaluation key is automatically
generated. If after 30 days you do not provide a permanent license key
or an extended evaluation license key, authentication for the computer
through Active Directory ceases to function.
Copyright © 2007 Likewise Software. All rights reserved. 13
Product Documentation 9
Likewise 4.0: Administrator’s Guide
The evaluation license applies only to the computer on which the agent
is installed; other computers running the agent under an evaluation key
will continue to authenticate to Active Directory until their individual 30-
day trial periods expire.
To download an evaluation version of Likewise, please visit:
http://www.likewisesoftware.com.
Upgrading from an Evaluation License
You can upgrade an evaluation license to a permanent license by using
the Likewise Console to import a license key for the agent.
To obtain licenses, contact Likewise:
Email: sales@likewisesoftware.com
Phone (US): 1-800-378-1330
Phone (International): +1-425-378-7887
Copyright © 2007 Likewise Software. All rights reserved. 14
Product Documentation
Likewise 4.0: Administrator’s Guide
Deploying the Agent
About the Likewise Agent
The agent is installed on Linux and Unix computers and integrates with
the core operating system to implement the mapping for any application
that uses the name service (NSS) or pluggable authentication module
(PAM). An example of a PAM-aware application is the login process
(/bin/login).
The agent acts as a Kerberos 5 client for authentication and as a LDAP
client for authorization. The agent also operates as the group policy
enforcing service, using secure credentials created through the Active
Directory domain to update local software configurations, such as the
sudo configuration file.
Likewise's group policies for Linux and Unix give you powerful method to
manage multiple machines remotely and uniformly from a single point of
control.
The Likewise Agent comprises the following daemons:
Agent Daemon Description
/etc/init.d/centeris.com- The Likewise authentication
lwiauthd daemon. It handles
authentication, authorization,
caching, and idmap lookups.
/etc/init.d/centeris.com- The Group Policy Agent. It runs
gpagent as a background service to pull
Group Policy Objects from
Active Directory and apply them
to the computer.
The agent also includes two libraries:
• The NSS library: lwidentity.so
• The PAM library: pam_lwidentity.so
The agent uses the following ports for outbound traffic. The agent is a
client only; it does not listen on any ports.
Copyright © 2007 Likewise Software. All rights reserved. 15
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Port Protocol Use
53 UDP/TCP DNS
88 UDP/TCP Kerberos
123 UDP NTP
137 UDP NetBIOS Name
Service
139 TCP NetBIOS Session
(SMB)
389 UDP/TCP LDAP
445 TCP SMB over TCP
Check System Health Before Installing the Agent
Likewise includes a shell script to check the health of a Linux or Unix
computer on which you plan to install the Likewise Agent. The script
helps you identity potential system configuration issues before you install
the agent and join a Linux or Unix computer to an Active Directory
domain.
The name of the script is healthchk.sh. To execute it, copy the script
to the Unix, Linux, or Mac OS X computer that you want to check, and
then execute the following command from the shell prompt:
healthchk.sh
The script outputs the results of its scan to /tmp/healthchk.out.
The following table lists each item the script checks, describes the item,
and suggests action to correct the issue.
Copyright © 2007 Likewise Software. All rights reserved. 16
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Item Checked Description Corrective Action
Type of operating The operating system must Install the agent on a computer that is running
system be one of the platforms that a supported operating system.
Likewise supports.
Supported platforms are
listed later in this guide.
Hostname Informational. Not applicable.
Processor type The processor type must be Install the agent on a computer with a
supported by the Likewise supported processor.
Agent. See the list of
supported platforms later in
this guide.
Disk usage Checks the disk space Increase the amount of disk space available to
available to /opt (on Unix) /opt or /usr.
or /usr (on Linux) to
ensure that there is enough
to install the agent and its
accompanying packages.
Contents of Displays the operating Install the agent on a computer that is running
/etc/*release (for system and version number a supported operating system and version.
AIX, to determine the to ensure that they are
oslevel) supported by Likewise. See
the list of supported
platforms later in this guide.
Network interface and Displays network interfaces Configure the computer so that it has network
its status and IP addresses to ensure access and can communicate with the domain
that the system has controller.
network access.
Contents of the IP To determine whether a If the computer does not use a single default
routing table single default gateway is gateway, you must define a route to a single
defined for the computer. default gateway.
For example, you can run the route -n to
view the IP routing table and set a static route.
For more information, see the man pages for
your system.
On Solaris, you may need to create or edit
/etc/defaultrouter.
On Linux, you can set the default gateway by
running the network utility for your distribution.
Connectivity to the Pings the default gateway Configure the computer and the network so
default gateway to ensure that the computer that the computer can connect to the default
Copyright © 2007 Likewise Software. All rights reserved. 17
Product Documentation 9
Likewise 4.0: Administrator’s Guide
can connect to it. A gateway.
connection to the default
gateway is required.
Contents of Displays information about The nsswitch.conf file must contain the
nsswitch.conf (or, the nsswitch configuration. following line:
for AIX, netsvc.conf) hosts: files dns
Computers running Solaris, in particular, may
not contain this line in nsswitch.conf.
FQDN Determines the fully Make sure the computer's FQDN is correct in
qualified domain name of /etc/hosts.
the computer to ensure that You can determine the fully qualified domain
it is set properly. name of a computer running Linux, Unix, or
Mac OS X by executing the following
command:
ping -c 1 `hostname`
When you execute this command, the
computer looks up the primary host entry for its
hostname. In most cases, it looks for its
hostname in /etc/hosts, returning the first
FQDN name on the same line. So, for the
hostname qaserver, here's an example of a
correct entry in /etc/hosts:
10.100.10.10
qaserver.corpqa.centeris.com
qaserver
If, however, the entry in /etc/hosts
incorrectly lists the hostname (or anything
else) before the FQDN, the computer's FQDN
becomes, using the malformed example
below, qaserver:
10.100.10.10 qaserver
qaserver.corpqa.centeris.com
If the host entry cannot be found in
/etc/hosts, the computer looks for the
results in DNS instead. This means that the
computer must have a correct A record in
DNS. If the DNS information is wrong and you
cannot correct it, add an entry to
/etc/hosts.
IP address of local NIC Determines whether the IP Either update DNS or change the local IP
address of the local address so that the IP address of the local
network card matches the network card matches the IP address returned
IP address returned by by DNS for the computer.
Copyright © 2007 Likewise Software. All rights reserved. 18
Product Documentation 9
Likewise 4.0: Administrator’s Guide
DNS for the computer. The
IP address of the local NIC
must match the IP address
for the computer in DNS.
Contents of Returns the address for the Compare against the results of the items
resolv.conf nameserver set in checked next.
resolv.conf.
The address of
nameserver must point to
a DNS server that can
resolve the Active Directory
domain name and return
the SRV records for the
domain controllers.
The SRV record is a DNS
resource record that is used
to identify computers that
host specific services. SRV
resource records are used
to locate domain controllers
for Active Directory.
DNS query results for The IP address for the host Either update DNS or change the local IP
system (hostname and name from DNS must address so that the IP address of the local
IP) match the IP address of the network card matches the IP address returned
computer's local NIC. by DNS for the computer.
DNS name resolution Pings the domain name to Correct resolv.conf so that the
and connectivity to get the IP address. nameserver points to a DNS server that can
specified domain resolve the Active Directory domain name --
controller typically the domain controller running DNS.
SRV records from DNS Performs a DNS lookup for Correct resolv.conf so that the
the SRV records to get the nameserver points to a DNS server that can
IP addresses for the resolve the SRV records.
domain controller.
Connectivity to the Informational. Although Not applicable.
Internet connectivity to the Internet
is optional, it makes it
easier to download the
installer for the agent
installer.
Location and version Checks whether required Likewise requires the following utilities: ssh
information for sudo, utilities are installed and are and openssl.
openssl, bash, rpm, in expected locations. The other utilities are optional but may be
and ssh useful.
Copyright © 2007 Likewise Software. All rights reserved. 19
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Selected firewall Tests whether the computer Reconfigure the firewall to allow the computer
settings (Kerberos, can connect to ports on the to access the domain controller.
NetBIOS, and LDAP) domain controller to make
sure that a firewall will not
block the computer's
attempt to join the domain.
Listing of files in Lists other software that Not applicable. Save this information for
/etc/pam.d requires PAM. Likewise support staff in case they need to
troubleshoot the installation.
Contents of selected May reveal installation of Not applicable. Save this information for
pam files (pam.conf, other applications that are Likewise support staff in case they need to
common-auth, system- incompatible with the troubleshoot the installation.
auth) installer.
Contents of Shows Kerberos 5 Not applicable. Save this information for
/etc/krb5.conf configuration. Likewise support staff in case they need to
troubleshoot the installation.
DHCP Checks whether DHCP is in Set the computer to a static IP address or
use. configure DHCP so that it does not update
When the Likewise Agent such files as /etc/resolv.conf and
joins the computer to the /etc/hosts.
domain, the agent restarts
the computer. DHCP can
then change the contents of
/etc/resolv.conf,
/etc/hosts, and other
files, causing the computer
to fail to join the domain.
ISA type Returns 32-bit or 64-bit Use the installer for your ISA type.
information.
Read-only filespaces Checks whether /opt (for Make sure that /usr or /opt are writable.
Unix) or /usr (for Linux)
are not mounted as
readonly.
AIX TL levels Determines the AIX TL Not all TL levels are supported. For AIX, check
level. with Likewise support to make sure that
Likewise is compatible with the TL level you
are using.
Copyright © 2007 Likewise Software. All rights reserved. 20
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Install the Agent on a Linux Computer
You must install the Likewise Agent on each Linux or Unix computer that
you want to join to Active Directory and manage with Likewise.
1. Obtain the appropriate installation package from Likewise. For a list
of supported platforms, see the release notes or
www.likewisesoftware.com. The installer's name is composed of the
product name, version, operating system, type, platform (32/64), and
control build and patch numbers. Example:
lwidentity-3.2.0.1170-linux-i386-rpm-installer
Note: The examples shown are for Linux RPM-based platforms.
For other platforms (Debian, HP-UX, AIX, Solaris, etc.) simply
substitute the appropriate package. The installation steps are the
same across all platforms.
2. If not handled in Step 1, copy the Likewise Agent to your Linux or
Unix system. In this example, scp is shown using the /tmp
directory, but you can use any file-copy utility (wget, winscp, ncftp,
copy from CD):
scp user@host:folder/SourceFile TargetFile
scp ddallas@10.100.1.50:tmp/lwidentity-3* /tmp
Note: In the string, 3* is a notation for the complete file name.
3. As the root user or with sudo permission, modify the execute bit on
the installer by executing the following command at the shell prompt
on the Linux or Unix computer:
chmod a+x /tmp/lwidentity-3*
4. To launch the installer, at the shell prompt, type the following
command, press TAB to complete it, and then execute it:
/tmp/lwidentity-3
Copyright © 2007 Likewise Software. All rights reserved. 21
Product Documentation 9
Likewise 4.0: Administrator’s Guide
5. Follow the instructions in the installation wizard.
Tip: See the Installation Guide at
http://www.likewisesoftware.com/resources/product_documentation/.
Install the Agent on a Mac Computer
To install the Likewise Agent on a computer running Mac OS X, you
must have administrative privileges on the Mac. Likewise supports Mac
OS X 10.4 or later.
1. Log on the Mac with a local account.
2. On the Apple menu , click System Preferences.
3. Under Internet & Network, click Sharing, and then select the
Remote Login check box.
4. Go to http://www.likewisesoftware.com/support/ and download to
your desktop the Likewise Agent installation package for your Mac.
Important: To install the agent on an Intel-based Mac, use the i386
version of the .dmg package. To install the agent on a Mac that
does not have an Intel chip, use the powerpc version of the .dmg
package.
5. On the Mac computer, go to the Desktop and double-click the
Likewise .dmg file.
6. In the Finder window that appears, double-click the .mpkg file -- for
example, centeris-likewise-identity-3.5.0.1554-
powerpc.mpkg.
7. Follow the instructions in the installation wizard.
When the wizard finishes installing the package, which includes the
Likewise Agent, you are ready to join the Mac to the Active Directory
domain.
Copyright © 2007 Likewise Software. All rights reserved. 22
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Uninstall the Agent on a Linux or Unix Computer
On a Linux or Unix computer, you can uninstall the Likewise Agent from
the command line if you originally installed the agent with the BitRock
installer.
Note: Execute the uninstall command from a directory other than
centeris so that the uninstall program can delete the centeris
directory and all its subdirectories. For example, execute the command
from the root directory.
• To uninstall the agent on a Linux computer, run the following
command as root:
/usr/centeris/setup/uninstall
• To uninstall the agent on a Unix computer, run the following command
as root:
/opt/centeris/setup/uninstall
Uninstall the Agent on a Mac
On a Mac computer, you must uninstall the Likewise Agent by using the
Terminal.
1. Log on the Mac by using a local account with privileges that allow
you to use sudo.
2. Open a Terminal window: In Finder, on the Go menu, click Utilities,
and then double-click Terminal.
3. At the Terminal shell prompt, execute the following command:
sudo /opt/centeris/bin/lwi-uninstall.sh
Make Sure Outbound Ports Are Open
If you are using local firewall settings, such as iptables, on a computer
running the Likewise Agent, make sure the following ports are open for
outbound traffic.
Note: The Likewise Agent is a client only; it does not listen on any ports.
Copyright © 2007 Likewise Software. All rights reserved. 23
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Port Protocol Use
53 UDP/TCP DNS
88 UDP/TCP Kerberos
123 UDP NTP
137 UDP NetBIOS Name
Service
139 TCP NetBIOS Session
(SMB)
389 UDP/TCP LDAP
445 TCP SMB over TCP
464 UDP/TCP Machine password
changes (typically
after 30 days)
Command-Line Tools
After you install the Likewise Agent, the following command-line tools are
available in this directory on Linux computers:
/usr/centeris/bin
On Unix-based computers, including Solaris, AIX, and Mac OS X, the
command-line tools are in this directory:
/opt/centeris/bin
Command-Line Tool Description
domainjoin-cli The command-line interface of the
domain join tool. It prompts you for
a password or accepts password
input from a file. You can also use it
to change the hostname of the
machine and dynamically update a
DNS server.
setkey-cli Lets you provision license keys
manually.
gporefresh Forces the computer to refresh its
group policy objects (GPOs).
Execute this command to obtain
group policy updates from Active
Directory. This command is useful if
you need to have group policy
Copyright © 2007 Likewise Software. All rights reserved. 24
Product Documentation 9
Likewise 4.0: Administrator’s Guide
changes applied before GPOs
automatically refresh, which is
typically every 30 minutes.
Using Command-Line Tools to Deploy Agents
The Likewise command-line tools can help deploy the Likewise Agent to
multiple computers or install the agent remotely.
You can use the command-line tools to automatically install the agent,
join the computer to a domain, acquire a license, and obtain credentials.
For example, you can automate the installation of the agent by using the
installation command in unattended mode:
# ./lwidentity-3.5.0.1533-linux-x86_64-rpm-installer --mode
unattended
For Unix and Linux hosts, you can run the installer from the shell prompt
with no special treatment. The installer detects that it is running in
character mode and displays a character mode user interface, or you
can force it into character mode with the option --mode text:
# chmod +x lwidentity-3.5.0.1533-linux-x86_64-rpm-installer
# ./lwidentity-3.5.0.1533-linux-x86_64-rpm-installer --mode
unattended
After you have installed the agent on Linux computers, additional
command-line tools are in /usr/centeris/bin.
On Unix and Mac OS X computers, the command-line tools are in
/opt/centeris/bin.
Copyright © 2007 Likewise Software. All rights reserved. 25
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Joining a Domain
When Likewise joins a computer to a domain, it uses the hostname of
the computer to create the name of the computer object in Active
Directory. From the hostname, the Likewise Domain Join Tool attempts
to derive a fully qualified domain name.
By default, the domain join tool (/usr/centeris/bin/domainjoin-
gui) creates the Linux and Unix machine accounts in the default
Computers container within Active Directory.
You can, however, choose to create machine accounts in Active
Directory before you join your Unix, Linux, and Mac OS X computers to
the domain. When you join a computer to a domain by running the
Domain Join Tool, Likewise searches Active Directory for existing
machine accounts. If the tool finds a match, Likewise associates the Unix
or Linux host with the pre-existing machine account. If no match is found,
Likewise creates a machine account.
Removing a Computer from a Domain
You can remove a computer from the domain either by removing the
computer's account from Active Directory Users and Computers or by
running the Domain Join Tool on the Unix, Linux, or Mac OS X computer
that you want to remove.
Join a Linux Computer to Active Directory
After you install the Likewise Agent, you can join a Linux or Unix
computer to an Active Directory domain by using the Likewise Domain
Join Tool. The Likewise Domain Join Tool provides a graphical user
interface on Gnome-compatible Linux computers for joining a domain.
Important: To join a computer to a domain, you must have the user
name and password of a user who can join computers to a domain and
the full name of the domain that you want to join.
1. From the desktop with root privileges, double-click the Likewise
Domain Join Tool, or at the shell prompt of a Linux computer, type
the following command:
/usr/centeris/bin/domainjoin-gui
For a Unix computer, type this command:
Copyright © 2007 Likewise Software. All rights reserved. 26
Product Documentation 9
Likewise 4.0: Administrator’s Guide
/opt/centeris/bin/domainjoin-cli
2. On the Welcome panel, click Next.
3. On the Join Active Directory Domain panel, in the Domain to join
box, enter the Fully Qualified Domain Name (FQDN) of the Active
Directory domain.
Note: The domain join tool automatically sets the computer’s FQDN
by modifying the /etc/hosts file. For example, If your computer's
name is qaserver and the domain is corpqa.centeris.com,
the domain join tool adds the following entry to the /etc/hosts file:
qaserver.corpqa.centeris.com. To manually set the
computer's FQDN, see Set the FQDN Manually.
4. Under Organizational Unit, you can join the computer to an OU in
the domain by selecting OU Path and then typing a path in the OU
Path box.
Copyright © 2007 Likewise Software. All rights reserved. 27
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Or, to join the computer to the Computers container, select Default
to "Computers" container.
5. Click Next.
6. Enter the user name and password of an Active Directory user with
the right to join a machine to the Active Directory domain, and then
click OK.
Note: If you do not use an Active Directory Domain Administrator
account, you might not have sufficient privileges to change an
existing machine object in Active Directory.
Join a Mac Computer to Active Directory
To join a computer running Mac OS X 10.4 or later to an Active Directory
domain, you must have administrative privileges on the Mac and
privileges on the Active Directory domain that allow you to join a
computer.
1. In Finder, click Applications. In the list of applications, double-click
Utilities, and then double-click Directory Access.
2. On the Services tab, click the lock and enter an administrator
name and password to unlock it.
3. In the list click Likewise, make sure the Enable check box for
Likewise is selected, and then click Configure.
4. Enter a name and password of a local machine account with
administrative privileges.
5. On the menu bar at the top of the screen, click the Likewise
Domain Join Tool menu, and then click Join or Leave Domain.
6. In the Computer name box, type the name of the local hostname of
the Mac without the .local extension. Because of a limitation with
Active Directory, the local hostname cannot be more than 16
characters. Also: localhost is not a valid name.
Tip: To find the local hostname of a Mac, on the Apple menu ,
click System Preferences, and then click Sharing. Under the
Computer Name box, click Edit. Your Mac's local hostname is
displayed.
Copyright © 2007 Likewise Software. All rights reserved. 28
Product Documentation 9
Likewise 4.0: Administrator’s Guide
7. In the Domain to join box, type the fully qualified domain name of
the Active Directory domain that you want to join.
8. Under Organizational Unit, you can join the computer to an OU in
the domain by selecting OU Path and then typing a path in the OU
Path box.
Note: To join the computer to an OU, you must be a member of the
Domain Administrator security group.
Or, to join the computer to the Computers container, select Default
to "Computers" container.
9. Click Join.
10. After you are joined to the domain, you can set the display login
window preference on the Mac: On the Apple menu , click
System Preferences, and then under System, click Accounts.
11. Click the lock and enter an administrator name and password to
unlock it.
12. Click Login Options, and then under Display login window as,
select Name and password.
Join Active Directory Without Changing /etc/hosts
When you join a computer to a domain by using the Likewise Domain
Join Tool, Likewise uses the hostname of the computer to derive a fully
qualified domain name (FQDN) and then automatically sets the
computer’s FQDN in the /etc/hosts file.
You can set the computer's FQDN without changing the /etc/hosts
file by using the shell prompt.
To join a Linux computer to the domain and set the computer's FQDN
without changing the /etc/hosts file, execute the following command
at the shell prompt, replacing domainName with the FQDN of the domain
that you want to join and joinAccount with the user name of an
account that has privileges to join computers to the domain:
/usr/centeris/bin/domainjoin-cli join --nohosts
domainName joinAccount
Copyright © 2007 Likewise Software. All rights reserved. 29
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Example: /usr/centeris/bin/domainjoin-cli join --
nohosts centerisdemo.com Administrator
If the Computer Fails to Join the Domain
Make sure the computer's FQDN is correct in /etc/hosts.
You can determine the fully qualified domain name of a computer
running Linux, Unix, or Mac OS X by executing the following command:
ping -c 1 `hostname`
When you execute this command, the computer looks up the primary
host entry for its hostname. In most cases, this means that it looks for its
hostname in /etc/hosts, returning the first FQDN name on the same
line. So, for the hostname qaserver, here's an example of a correct
entry in /etc/hosts:
10.100.10.10 qaserver.corpqa.centeris.com qaserver
If, however, the entry in /etc/hosts incorrectly lists the hostname (or
anything else) before the FQDN, the computer's FQDN becomes, using
the malformed example below, qaserver:
10.100.10.10 qaserver qaserver.corpqa.centeris.com
If the host entry cannot be found in /etc/hosts, the computer looks for
the results in DNS instead. This means that the computer must have a
correct A record in DNS. If the DNS information is wrong and you cannot
correct it, add an entry to /etc/hosts.
Join Active Directory with the Command Line
When you join a domain by using the command-line utility, Likewise uses
the hostname of the computer to derive a fully qualified domain name
(FQDN) and then automatically sets the computer’s FQDN in the
/etc/hosts file.
You can also join a domain without changing the /etc/hosts file; see
Join Active Directory Without Changing /etc/hosts.
On Linux computers, the domain join command-line utility is in
/usr/centeris/bin. On Unix and Mac OS X computers, it is in
/opt/centeris/bin.
Copyright © 2007 Likewise Software. All rights reserved. 30
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Important: To join a computer to a domain, you must have the user
name and password of an account that has privileges to join computers
to the domain and the full name of the domain that you want to join.
Join a Linux Computer to Active Directory
• Execute the following command, replacing domainName with the
FQDN of the domain that you want to join and joinAccount with the
user name of an account that has privileges to join computers to the
domain:
/usr/centeris/bin/domainjoin-cli join domainName
joinAccount
Example: /usr/centeris/bin/domainjoin-cli join
centerisdemo.com Administrator
Join a Unix Computer to Active Directory
• Execute the following command, replacing domainName with the
FQDN of the domain that you want to join and joinAccount with the
user name of an account that has privileges to join computers to the
domain:
/opt/centeris/bin/domainjoin-cli join domainName
joinAccount
Example: /opt/centeris/bin/domainjoin-cli join
centerisdemo.com Administrator
Join a Mac Computer to Active Directory
• Using sudo, execute the following command in the Terminal,
replacing domainName with the FQDN of the domain that you want to
join and joinAccount with the user name of an account that has
privileges to join computers to the domain:
sudo /opt/centeris/bin/domainjoin-cli join
domainName joinAccount
Example: sudo /opt/centeris/bin/domainjoin-cli join
centerisdemo.com Administrator
The terminal prompts you for two passwords: The first is for a user
account on the Mac that has admin privileges; the second is for the
Copyright © 2007 Likewise Software. All rights reserved. 31
Product Documentation 9
Likewise 4.0: Administrator’s Guide
user account in Active Directory that you specified in the join
command.
Options and Commands
The domainjoin-cli command-line interface includes the following
options:
Option Description Example
--help Displays the command-line domainjoin-cli --help
arguments.
--log {.| path} Generates a log file or prints domainjoin-cli --log
the log to the console. /var/log/domainjoin.log
join centerisdemo.com
Administrator
domainjoin-cli --log .
join centerisdemo.com
Administrator
The domainjoin-cli command-line interface includes the following
commands:
Command Description Example
query Displays the hostname and domainjoin-cli query
current domain. If the
computer is not joined to a
domain, it displays only the
hostname.
setname computerName Renames the computer and domainjoin-cli setname
modifies the /etc/hosts file RHEL44ID
with the name that you
specify.
join [--ou Joins the computer to the domainjoin-cli join --
organizationalUnit] [- domain that you specify by ou Engineering
-nohosts] domainName using the user account that centerisdemo.com
userName you specify. Administrator
You can use the --ou option
Copyright © 2007 Likewise Software. All rights reserved. 32
Product Documentation 9
Likewise 4.0: Administrator’s Guide
to join the computer to an OU
within the domain by
specifying the path to the OU
and the OU's name. When
you use this option, you must
also use an account that has
membership in the Domain
Administrators security group.
The --nohosts option joins
the computer to the domain
without modifying the
/etc/hosts file.
leave Removes the computer from domainjoin-cli leave
the Active Directory domain.
Rename a Joined Computer
To rename a computer that has been joined to Active Directory, you
must first leave the domain. You can then rename the computer by using
either the Likewise Domain Join Tool or the shell prompt. After you
rename the computer, you must rejoin it to the domain.
Important: To rename a computer and then rejoin it to a domain, you
must have the user name and password of a user with privileges to join a
computer to a domain.
Rename a Computer by Using the Domain Join Tool
1. From the desktop with root privileges, double-click the Likewise
Domain Join Tool, or at the shell prompt of a Linux computer, type
the following command:
/usr/centeris/bin/domainjoin-gui
2. Click Leave, and then click OK.
3. Start the Domain Join Tool again by double-clicking the Likewise
Domain Join Tool on the desktop, or by typing the following
command at the shell prompt of a Linux computer:
Copyright © 2007 Likewise Software. All rights reserved. 33
Product Documentation 9
Likewise 4.0: Administrator’s Guide
/usr/centeris/bin/domainjoin-gui
4. Click Next.
5. In the Computer Name box, rename the computer by typing a new
name.
6. In the Domain to join box, enter the Fully Qualified Domain Name
(FQDN) of the Active Directory domain.
7. Under Organizational Unit, you can join the computer to an OU in
the domain by selecting OU Path and then typing a path in the OU
Path box.
Or, to join the computer to the Computers container, select Default
to "Computers" container.
8. Click Next.
9. Enter the user name and password of an Active Directory user with
the right to join a machine to the Active Directory domain, and then
click OK.
Copyright © 2007 Likewise Software. All rights reserved. 34
Product Documentation 9
Likewise 4.0: Administrator’s Guide
The computer's name has been changed to the name that you specified
and the computer has been joined to the Active Directory domain with
the new name.
Rename a Computer by Using the Command-Line Tool
The following precedure removes a Unix computer from the domain,
renames the computer, and then rejoins it to the domain. You can also
use the command-line tool on a Linux computer; on a Linux computer,
the path to the tool is /usr/centeris/bin/.
1. With root privileges, at the shell prompt of a Unix computer, execute
the following command:
/opt/centeris/bin/domainjoin-cli leave
2. To rename the computer, execute the following command at the
shell prompt, replacing computerName with the new name of the
computer:
/opt/centeris/bin/domainjoin-cli setname
computerName
Example: /opt/centeris/bin/domainjoin-cli setname
RHEL44ID
3. To rejoin the renamed computer to the domain, execute the
following command at the shell prompt, replacing DomainName with
the name of the domain that you want to join and UserName with
the user name of a user who has privileges to join a domain:
/opt/centeris/bin/domainjoin-cli join DomainName
UserName
Example: /opt/centeris/bin/domainjoin-cli join
centerisdemo.com Administrator
It may take a few moments before the computer is joined to the
domain.
Copyright © 2007 Likewise Software. All rights reserved. 35
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Interactive Linux Sign-On
After the Likewise Agent has been installed and the Linux computer has
been joined to a domain, users can log on interactively by using their
Active Directory credentials. For example, a user can log on by using the
form DOMAIN\username.
1. On a Linux computer, log out of the current session.
2. Log on the system console by using an Active Directory user
account in the form of DOMAIN\username, where DOMAIN is the
Active Directory short name.
Note: You can control which users and groups can interactively sign on.
For more information, see Help for MMC extensions and About Group
Policies.
Leave a Domain
Remove a Linux Computer from a Domain
1. On the Linux computer that you want to remove from the Active
Directory domain, use a root account to run the following command
at the shell prompt:
/usr/centeris/bin/domainjoin-gui
2. Click Leave.
Remove a Unix Computer from a Domain
• On the Unix computer that you want to remove from the Active
Directory domain, execute the following command at the shell prompt:
/opt/centeris/bin/domainjoin-cli leave
Remove a Mac from a Domain
To leave a domain on a Mac OS X computer, you must have
administrative privileges on the Mac.
1. In Finder, click Applications.
2. In the list of applications, double-click Utilities, and then double-
click Directory Access.
Copyright © 2007 Likewise Software. All rights reserved. 36
Product Documentation 9
Likewise 4.0: Administrator’s Guide
3. On the Services tab, click the lock and enter an administrator
name and password to unlock it.
4. In the list, click Likewise, and then click Configure.
5. Enter a name and password of a local machine account with
administrative privileges.
6. On the menu bar at the top of the screen, click the Likewise
Domain Join Tool menu, and then click Join or Leave Domain.
7. Click Leave.
Copyright © 2007 Likewise Software. All rights reserved. 37
Product Documentation
Likewise 4.0: Administrator’s Guide
Using the Likewise Console
The Likewise Console lets you manage Linux, Unix, and Mac OS X
computers within Active Directory. The console, which runs on a
Windows administrative workstation that connects to an Active Directory
domain controller, includes tools that are integrated into Active Directory
Users and Computers, the Group Policy Management Console, and the
Group Policy Object Editor.
You can use the console to perform the following tasks:
• Import and assign Likewise licenses.
• Obtain status information about your Active Directory forests and
domains.
• Generate reports about users, groups, and computers.
• Migrate Unix and Linux users and groups by importing passwd and
group files and mapping the information to users and groups in Active
Directory.
• Set the default home directory and default login shell for all the
domains in a forest.
• Remove orphaned objects.
• Run multiple instances of the console and point them at different
domains.
• Run the console with a different user account.
• Connect to a different domain.
After you install the console, you can use Active Directory Users and
Computers to manage Unix and Linux users and groups. You can also
use the the Group Policy Object Editor to create or edit Linux- and Unix-
specific group policies, and you can use the Group Policy Management
Console to view information about group policies.
Start the Likewise Console
To start the Likewise Console, it must first be installed on your
administrative desktop.
Copyright © 2007 Likewise Software. All rights reserved. 38
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Depending on the options choosen during installation, you can start the
Likewise Console in the following ways:
• Click Start, point to All Programs, click Likewise, and then click
Likewise Console.
• Double-click on the Likewise desktop shortcut.
• At the command prompt, execute the following commands:
cd %ProgramFiles%\Centeris\LikewiseIdentity
iConsole.exe
The console starts and defaults to the forest that the desktop is joined to
using the signed on domain credentials.
Tip: You can run multiple instances of the Likewise Console and point
them at different domains.
About the Welcome Page
The Welcome page is the first screen that is displayed after you start the
Likewise Console. From the Welcome page, you can navigate to all other
console pages. You can also start Active Directory Users and Computers
(ADUC) as well as Cell Manager.
Connect to a Domain
If Likewise detects more than one Active Directory forest, it displays
them on the Likewise Console's Status page. You can connect to a forest
by double-clicking the forest name.
You can connect to another domain as follows:
1. On the File menu, click Connect.
2. In the Domain Name or Server box, type the name of the domain
or server that you want.
3. If your default credentials permit you to connect to the domain or
server, select Use default (logon) credentials. Otherwise, select
Use alternate credentials, and then in the Username and
Password boxes, type credentials that permit you to connect to the
domain or server.
Copyright © 2007 Likewise Software. All rights reserved. 39
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Run the Console with a Different Account
You can run the Likewise Console by using a different user account.
Note: Your domain policy might restrict your ability to use this option.
1. On your Windows administrative desktop, click Start, point to All
Programs, click Likewise, right-click Likewise Console, and then
click Run as.
2. Select The following user, and then in the User name box, enter
the name of the user account that you want to use.
3. In the Password box, type the password for the user account.
About Users and Computers Extensions
Likewise provides extension tabs to the property sheet of the following
Active Directory objects in the Microsoft Active Directory Users and
Computers MMC snap-in:
• Users: Likewise Settings
• Groups: Likewise Settings
• Organizational Units:
• Likewise Settings (for the associated cell)
• Group Policy
Copyright © 2007 Likewise Software. All rights reserved. 40
Product Documentation
Likewise 4.0: Administrator’s Guide
Working with Cells
Active Directory uses Organizational Units to group related objects in a
common container so that you can manage the objects in a uniform and
consistent way. To map Active Directory users to Linux and Unix user
identifiers (UIDs) and group identifiers (GIDs), you associate Likewise
cells with Organizational Units. When you associate a cell with an
Organizational Unit (OU), the cell becomes a custom mapping of Active
Directory users to UIDs and GIDs.
Cells can map a user to different UIDs and GIDs for different computers.
Linux and Unix computers that are in the OU (or an OU nested in it) use
the cell to map AD users to UIDs and GIDs. In the following screen shot,
the example user, Clark Kent, is allowed to access the Linux and Unix
computers that are in the selected Likewise cells:
Copyright © 2007 Likewise Software. All rights reserved. 41
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Creating Cells
Likewise modifies the Active Directory User and Computers MMC snap-
in so that you can create an associated cell for an OU and then use the
cell to manage UID-GID numbers. To create a cell, use Active Directory
Users and Computers to select the OU you want, view the Likewise
Settings property sheet, and then select the check box to associate a cell
with the OU. You can then assign UID-GID numbers manually or allow
Likewise to do it automatically. For more information, see Create a Cell.
When a Unix or Linux computer connects to Active Directory, it
determines the OU of which it is a member and checks whether a
Likewise cell is associated with it. If a cell is not associated with the OU,
the Likewise Agent on the Unix computer searches the parent and
grandparent OUs until it finds an OU that has a cell associated with it. If
an OU with an associated cell is not found, the agent uses the default
cell to map its username to UID and GID information.
Important: Before you associate a cell with an Organizational Unit,
make sure you have chosen the schema mode that you want. You
cannot change the schema mode after you create a cell, including a
default cell.
The Default Cell
Likewise lets you define a default cell. It handles mapping for computers
that are not in an OU with an associated cell. The default cell can contain
the mapping information for all your Linux and Unix computers.
A Linux or Unix computer can be a member of an OU that does not have
a cell associated with it. In such a case, the group polices associated
with the OU apply to the Linux and Unix computer, but user UID-GID
mappings follow the policy of the nearest parent cell, or the default cell.
Likewise does not require you to have a default cell.
Linking Cells
To provide a mechanism for inheritance and to ease system
management, Likewise can link cells. Linking specifies that users and
groups in a linked cell can access resources in the target cell. For
example, if your default cell contains 100 system administrators and you
want those administrators to have access to another cell, called
Engineering, you do not need to provision those users in the Engineering
cell. You can simply link the Engineering cell to the default cell, and then
the Engineering cell inherits the settings of the default cell. Then, to
Copyright © 2007 Likewise Software. All rights reserved. 42
Product Documentation 9
Likewise 4.0: Administrator’s Guide
make management easier, in the Engineering cell you can just specify
the mapping information that deviates from the default cell.
Although you can use linking to in effect set up a hierarchy of cells,
linking is not transitive. If, for example, a cell called Civil is linked to the
Engineering cell and the Engineering cell is linked to the default cell, the
Civil cell does not inherit the settings of the default cell.
When you link to multiple cells, the order that you set is important
because it controls the search order. Suppose that Steve, a system
administrator, has a UID of 1000,000 set in the default cell and a UID of
150,000 set in the Engineering cell. In the Civil cell, however, he must
use his UID from the Engineering cell to log on Civil computers. If the
Civil cell is linked to both the default cell and Engineering cell, the order
becomes important. If Engineering does not precede the default cell in
the search order, Steve will be assigned the wrong UID and will not be
able to log on computers in the Civil cell.
For instructions on how to link cells, see Link Cells.
Cell Manager
The Likewise Cell Manager is an MMC snap-in that you can use to
manage the cells that you associate with Active Directory Organizational
Units. With Cell Manager, you can view all your cells in one place. Cell
Manager complements Active Directory Users and Computers by letting
you delegate management of a cell -- that is, give others -- either a user
or a group -- the ability to add users and groups to a cell. Cell Manager
is automatically installed when you install the Likewise Console. For
more information, see Manage Cells.
Migrating NIS Domains
If use Likewise to migrate all your Unix and Linux users to Active
Directory, in most cases you will assign these users a UID and GID that
is consistent across all the Unix and Linux computers that are joined to
Active Directory -- a simple approach that reduces administrative
overhead.
In cases when multiple NIS domains are in use and you want to
eliminate these domains over time and migrate all users and computers
to Active Directory, mapping an Active Directory user to a single UID and
GID might be too difficult. When multiple NIS domains are in place, a
user typically has different UID-GID maps in each NIS domain. With
Likewise, you can eliminate these NIS domains but retain the different
Copyright © 2007 Likewise Software. All rights reserved. 43
Product Documentation 9
Likewise 4.0: Administrator’s Guide
NIS mapping information in Active Directory because Likewise lets you
use a cell to map a user to different UIDs and GIDs depending on the
Unix or Linux computer that they are accessing.
To move to Active Directory when you have multiple NIS servers, you
can create an OU (or choose an existing OU) and join to the OU all the
Unix computers that are connected to the NIS server. You can then use
cells to represent users' UID-GID mapping from the previous identity
management system.
Using Multiple Cells
If you have multiple Unix and Linux hosts but are not using a centralized
scheme to manage UIDs and GIDs, it is likely that each host has unique
UID-GID mappings. You may also have more than one centralized IMS,
such as multiple NIS domains. You can use multiple cells to represent
the UID-GID associations that the NIS domain provided, allowing those
Unix and Linux users to continue to use their existing UID-GID
information while using Active Directory credentials, as the following
diagram illustrates:
When using multiple cells, it is useful to identify what Unix and Linux
objects the cell will represent, such as the following:
• Individual Unix, Linux, or Mac OS X computers
Copyright © 2007 Likewise Software. All rights reserved. 44
Product Documentation 9
Likewise 4.0: Administrator’s Guide
• A single NIS domain
• Multiple NIS domains (which requires multiple cells)
Migration Tool
The Likewise Console provides a migration tool to import Linux, Unix,
and Mac OS X passwd and group files -- typically /etc/passwd and
/etc/group -- and automatically map their UIDs and GIDs to users and
groups defined in Active Directory. The migration tool can also generate
a Windows automation script to associate the Unix and Linux UIDs and
GIDs with Active Directory users and groups. For more information, see
Migrate Users to Active Directory.
Orphaned Objects Tool
The Likewise console provides a tool for finding and removing orphaned
objects. An orphaned object is a linked object, such as a Unix or Linux
user ID or group ID, that remain in a Likewise cell after you delete a
group or user's security identifier, or SID, from an Active Directory
domain. Removing orphaned objects from Active Directory can clean up
manually assigned user IDs and improve search speed. For more
information, see Find Orphaned Objects.
Create a Cell
To create a Likewise cell, you must first create an organizational unit, or
OU, in Active Directory. You can associate a cell with an existing OU.
Associating a Likewise cell with an OU requires Active Directory
administrative privileges that are sufficient to modify OU objects.
Important: Before you associate a cell with an organizational unit, make
sure you have chosen the schema mode that you want. You cannot
change the schema mode after you create a cell, including a default cell.
1. On your Windows administrative workstation, start Active Directory
Users and Computers.
2. In the console tree, right-click the name of the domain for which you
want to create an OU, point to New, and then click Organizational
Unit.
3. In the Name box, type a name for the OU, and then click OK.
4. In the console tree, right-click the OU that you just created -- or click
an existing OU -- click Properties, and then click the Likewise
Copyright © 2007 Likewise Software. All rights reserved. 45
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Settings tab.
5. Under Likewise Cell Information, select the Create Associated
Likewise Cell check box, and then click OK.
A cell is created, and you can now associate users with it.
Create a User
To create a Unix or Linux user account in Active Directory, you must
have sufficient administrative privileges -- for example, as a member of
the Enterprise Administrators group, the Domain Administrators group, or
as a delegate.
1. On your Windows administrative workstation, start Active Directory
Users and Computers.
2. In the console tree, right-click Users, point to New, and then click
User.
3. Enter the name and logon name information for the user, and then
click Next.
Copyright © 2007 Likewise Software. All rights reserved. 46
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Tip: For more information, see Create a New User Account in Active
Directory Users and Computers Help.
4. In the Password box and the Confirm password box, type a
password for the user, select the password options that you want,
and then click Next.
5. Click Finish.
6. In the console tree, right-click the user that you just created, and
then click Properties.
7. Click the Likewise Settings tab.
8. Under Likewise Cells, select the check box for the cell that you
want to associate the user with.
Under User info for cell, a default value, typically 100000, is
automatically populated in the GID box.
Copyright © 2007 Likewise Software. All rights reserved. 47
Product Documentation 9
Likewise 4.0: Administrator’s Guide
9. To set the UID, click Suggest, or type a value in the UID box.
10. To override the default home directory and login shell settings, in the
Home Directory box, type the directory that you want to set for the
user, and then in Login Shell box, type the login shell that you want.
11. Optionally, you can set a login name for the user in the Login Name
box and add a comment in the Comment box.
You use the Login Name box to set a login name for the user that is
different from the user's Active Directory login name. If you leave the
Login Name box empty, the user logs on Linux and Unix computers
by using his or her Active Directory login name.
Associate a User with One or More Cells
Within Active Directory Users and Computers, you can associate a user
with one or more Likewise cells to give the user access to the Linux,
Unix, and Mac OS X computers that are members of each cell.
Note: To associate a user with a cell, you must log on with sufficient
administrative privileges -- for example, as a member of the Domain
Administrators group.
1. Start Active Directory Users and Computers.
2. In the console tree, click Users.
3. In the details pane, right-click the user that you want, and then click
Properties.
4. Click the Likewise Settings tab.
5. Under Likewise Cells, select the check box for the cell that you
want to associate the user with. You can associate the user with
multiple cells by selecting the check boxes for the cells that you
want.
Under User info for cell, a default GID value, typically 100000, is
automatically populated in the GID box.
6. To set the UID, click Suggest, or type a value in the UID box.
Manage Cells
Copyright © 2007 Likewise Software. All rights reserved. 48
Product Documentation 9
Likewise 4.0: Administrator’s Guide
The Likewise Cell Manager is an MMC snap-in that you can use to
manage the cells that you associate with Active Directory Organizational
Units.
You can use Cell Manager to delegate management, change
permissions for a cell, add cells, view cells, and associate cells with OUs
to enable users and groups for Linux and Unix access. Cell Manager
also lets you filter cells to reduce clutter and connect to another domain.
Cell Manager is automatically installed when you install the Likewise
Console.
Start Cell Manager
1. In the Likewise Console, click the Welcome tab.
2. Under Tasks, click Launch Cell Manager.
Tip: To start Cell Manager from the Start menu, click Start, point to All
Programs, click Likewise, and then click Likewise Cell Manager.
Delegate Management
You can use Cell Manager to create an access control list (ACL) that
allows users or groups without administrative privileges to perform the
administrative operations that you specify. For example, you can
delegate management for the cell manager node to allow other users to
Copyright © 2007 Likewise Software. All rights reserved. 49
Product Documentation 9
Likewise 4.0: Administrator’s Guide
create and delete cells. You can delegate management of a cell, a
group, or a user.
1. In the Cell Manager console tree, right-click the folder of the cell that
you want to delegate management for, and then click Delegate
Control.
2. Follow the instructions in the Delegate Control Wizard.
Change Permissions of a Cell, Group, or User
1. In the Cell Manager console tree or in the details pane, right-click
the object that you want to change permissions for, and then click
Properties.
Tip: To select multiple users or groups, in the details pane, hold
down CTRL and click the users or groups that you want to change.
2. Click Permissions.
3. Make the changes that you want.
Add a Cell
When you add a cell, you must attach it to an Organizational Unit in
Active Directory.
1. In the Cell Manager console tree, right-click the top-level Cell
Manager domain node, point to New, and then click Cell.
2. In the list of OUs, expand the tree and then click the OU to which
you want to attach the cell.
Note: You cannot attach a cell to the top-level node (the domain).
3. In the First available user ID box, enter the number that you want.
Keep in mind that the user ID range cannot overlap with the ID
range of another cell.
4. In the First available group ID box, enter the number that you
want. Keep in mind that the user ID range cannot overlap with the ID
range of another cell.
5. In the Home directory template box, type the path for the home
directory that you want to set for users in the cell -- for example,
/home/%D/%U.
Copyright © 2007 Likewise Software. All rights reserved. 50
Product Documentation 9
Likewise 4.0: Administrator’s Guide
Important: When you set the home directory, you must use the
default user name variable (%U). You may specify the default domain
name by using the domain name variable (%D) but, unlike the user
name variable, it is not required.
6. In the Default login shell box, type the path to the default shell that
you want to use -- for example, /bin/sh.
Give a User Access to a Cell
When you give a user access to a cell by using Cell Manager, you can
add the new user to the cell only with default attributes. You can change
the attributes later by using in Active Directory Users and Computers;
see Specify a User's ID and Unix or Linux Settings.
1. In the Cell Manager console tree, right-click the cell that you want to
give a user access to, point to New, and then click User.
2. Find and select the user that you want to add, and then click OK.
Give a Group Access to a Cell
When you give a group access to a cell by using Cell Manager, you can
add the new group to the cell only with default attributes. You can
change the attributes later by using Active Directory Users and
Computers.
1. In the Cell Manager console tree, right-click the cell that you want to
give a user access to, point to New, and then click Group.
2. Find and select the group that you want to add, and then click OK.
Filter Cells
You can use filtering to set the maximum number of cells to display and
show only the cells that match a pattern.
1. In the Cell Manager console tree, right-click the top-level Cell
Manager domain node, and then click Filter.
2. Set the filtering values that you want to use.
Connect to a Different Domain
1. In the Cell Manager console tree, right-click the top-level Cell
Manager domain node, and then click Connect To Domain.
Copyright © 2007 Likewise Software. All rights reserved. 51
Product Documentation 9
Likewise 4.0: Administrator’s Guide
2. In the Domain box, type the domain that you want, or click Browse,
and then locate the domain that you want.
Assign a Group ID
You can assign a group identifier (GID) to an Active Directory group by
associating the group object with a cell and specifying a GID value for
the group object.
The GID information that you enter is applied to all objects within the
group. However, subgroups nested within the settings do not carry down;
you must apply the GID information to subgroups individually.
Note: To assign a group ID, you must log on with privileges sufficient to
modify the object.
1. On your Windows administrative workstation, Start Active Directory
Users and Computers.
2. In the console tree, click Users.
3. In the details pane, right-click a group object or any container object,
and then click Properties.
4. Click the Likewise Settings tab.
5. Under Cells, select the check box for the cell that you want to
associate with the group object.
6. To assign a GID, click Suggest, or in the GID box type the group
identifier that you want to assign to the group.
Tip: To generate a report that shows duplicate GIDs, see Show
Duplicate UIDs, GIDs, Login Names, and Group Aliases.
7. In the Group Alias box, you may type an alias for the group, but it is
not required.
8. In the Description text box, you may enter a description, but it is not
required.
Set a Group Alias
You can create an alias for a group that is part of a Likewise cell,
including the default cell. The group can use the alias within the cell.
Copyright © 2007 Likewise Software. All rights reserved. 52
Product Documentation 9
Likewise 4.0: Administrator’s Guide
1. On your Windows administrative workstation, start Active Directory
Users and Computers.
2. In the console tree, click Users.
3. In the list of users, right-click the group that you want, click
Properties, and then click the Likewise Settings tab.
4. Under Cells, select the check box for the cell that you want to set a
group alias for, and then in the Group Alias box, type an alias for
the group.
Tip: To generate a report that shows duplicate group aliases, see
Show Duplicate UIDs, GIDs, Login Names, and Group Aliases.
Specify a User's ID and Unix or Linux Settings
You can set a user's identifier (UID) and specify the user's Unix, Linux, or
Mac OS X settings.
Note: To provide a user with a UID and Unix or Linux settings, you must
have sufficient administrative privileges -- for example, as a domain
administrator or as a delegate. To delegate administrative privileges to
another user, see Delegate Management.
1. On your administrative workstation, start Active Directory Users and
Computers.
2. In the console tree, click Users.
3. In the details pane, right-click the user that you want, and then click
Properties.
Copyright © 2007 Likewise Software. All rights reserved. 53
Product Documentation 9
Likewise 4.0: Administrator’s Guide
4. Click the Likewise Settings tab.
5. Under Likewise Cells, select the check box for the cell that you
want to associate the user with.
Under User info for cell, a default value, typically 100000, is
automatically populated in the GID box.
6. To set the UID, click Suggest, or type a value in the UID box.
Tip: To generate a report that shows duplicate UIDs, see Show
Duplicate UIDs, GIDs, Login Names, and Group Aliases.
7. To override the default home directory and login shell settings, in the
Home Directory box, type the directory that you want to set for the
user, and then in Login Shell box, type the login shell that you want.
8. Optionally, you can set a login name for the user in the Login Name
box and add a comment in the Comment box.
You use the Login Name box to set a login name for the user that is
Copyright © 2007 Likewise Software. All rights reserved. 54
Product Documentation 9
Likewise 4.0: Administrator’s Guide
different from the user's Active Directory login name. If you leave the
Login Name box empty, the user logs on Linux and Unix computers
by using his or her Active Directory login name.
Apply Unix or Linux Settings to Multiple Users
Likewise lets you apply Unix, Linux, and Mac OS X settings to multiple
users at the same time. For example, you can assign multiple users to a
cell and then set their home directory.
The users must be members of a group that is associated with a cell and
each user must have a UID-GID mapping.
Note: To change users' settings, you must be logged on as a member of
the Domain Administrators security group or the Enterprise
Administrators security group. Or, you must have been delegated
privileges to modify the settings of the user objects that you want to
change; for more information, see Delegate Management.
1. On your Windows administrative workstation, start Active Directory
Users and Computers.
2. In the console tree, click Users, or expand the container that holds
the users that you want.
3. In the details pane, hold down CTRL and click the users that you
want.
4. Right-click the selected range of users, click Properties, and then
click the Likewise Settings tab.
5. Under UNIX/Linux User Information, select the check box for the
cell to which you want to assign the users.
By assigning the users to a cell, you are enabling them for access to
the Unix, Linux, and Mac OS computers that are in the cell.
6. Under User Info, make the changes that you want.
You can specify a GID for the users, and you can set their login shell
and home directory.
Copyright © 2007 Likewise Software. All rights reserved. 55
Product Documentation
Likewise 4.0: Administrator’s Guide
Disable a User
To disable a user, you must log on as a domain administrator or as a
member of another group that gives you privileges sufficient to modify
Active Directory user objects.
1. On your Windows administrative workstation, start Active Directory
Users and Computers.
2. In the tree, click Users.
3. In the details pane, right-click the user that you want to disable, and
then click Properties.
4. Click the Likewise Settings tab.
5. Under Likewise Cells, clear the check boxes for the cells in which
you want to disable the user.
To disable the user's access to all Linux, Unix, and Mac OS X
computers, in the list of cells under Likewise Cells, clear all the
check boxes.
Set the Default Home Directory
There are three ways that you can set the default home directory for
Linux, Unix, and Mac OS X users:
• Set a cell's default home directory by using the Likewise Settings tab
for an organizational unit's properties in Active Directory Users and
Computers.
• Select multiple users in Active Directory Users and Computers and
then set their default home directory.
• Set an individual user's default home directory by using the Likewise
Settings tab for the user's properties in Active Directory Users and
Computers.
Important: When you set the default home directory, you must use the
default user name variable (%U). You may specify the default domain
Copyright © 2007 Likewise Software. All rights reserved. 56
Product Documentation
Likewise 4.0: Administrator’s Guide
name by using the domain name variable (%D) but, unlike the user name
variable, it is not required.
Set the Home Directory for a Cell
Note: To set a default home directory for a cell, you must have Active
Directory administrative privileges to modify OU objects.
1. On your Windows administrative workstation, start Active Directory
Users and Computers.
2. In the console tree, right-click the OU for which you want to set a
home directory, click Properties, and then click the Likewise
Settings tab.
3. Under Likewise Cell Information, in the Default Home Directory
box, type the home directory that you want to set for the groups and
users in the cell.
Set the Home Directory for Multiple Users
Note: To change users' settings, you must log on as a member of the
Domain Administrators security group or the Enterprise Administrators
security group. Or, you must have been delegated privileges to modify
user settings; see Delegate Management.
1. On your administrative workstation, start Active Directory Users and
Computers.
2. In the console tree, expand Users, or expand the container that
holds the users that you want.
3. In the details pane, hold down CTRL and click the users that you
want.
4. Right-click on the selected range of users, click Properties, and
then click the Likewise Settings tab.
5. Under UNIX/Linux User Information, select the check box for the
cell that contains the users whose home directory you want to set.
Note: Selecting a check box for a cell assigns the selected users to
the cell and gives them access to the Unix, Linux, and Mac OS
computers that are in the cell.
If the check box for the cell that you want is already selected, click
the name of the cell.
Copyright © 2007 Likewise Software. All rights reserved. 57
Product Documentation
Likewise 4.0: Administrator’s Guide
6. In the Home Directory box, type the path for the home directory
that you want to set -- for example, /home/%D/%U.
Set the Home Directory for a Single User
Note: To change a user's settings, you must log on as a member of the
Domain Administrators security group or the Enterprise Administrators
security group. Or, you must have been delegated privileges to modify
user settings; see Delegate Management.
1. On your administrative workstation, start Active Directory Users and
Computers.
2. In the console tree, expand Users.
3. Right-click the user that you want, click Properties, and then click
the Likewise Settings tab.
4. In the list under Likewise Cells, click the cell for which you want to
set the user's home directory.
5. In the Home Directory box, type the path for the home directory
that you want to set -- for example, /home/%D/%U.
Set the Default Login Shell
By using Likewise, there are two ways that you can set the default login
shell for Linux, Unix, and Mac OS X users:
• Set a cell's default login shell by using the Likewise Settings tab for an
organizational unit's properties in Active Directory Users and
Computers.
• Select multiple users in Active Directory Users and Computers and
then set their default login shell.
• Set an individual user's default login shell by using the Likewise
Settings tab in Active Directory Users and Computers.
Set the Login Shell for a Cell
Note: To set a default login shell for a cell, you must have Active
Directory administrative privileges to modify OU objects.
1. On your Windows administrative workstation, start Active Directory
Users and Computers.
Copyright © 2007 Likewise Software. All rights reserved. 58
Product Documentation
Likewise 4.0: Administrator’s Guide
2. In the console tree, right-click the OU for which you want to set a
login shell, click Properties, and then click the Likewise Settings
tab.
3. Under Likewise Cell Information, in the Default Login Shell box,
type the login shell that you want to set for the users and groups in
the cell.
Set the Login Shell for Multiple Users
Note: To change users' settings, you must log on as a member of the
Domain Administrators security group or the Enterprise Administrators
security group. Or, you must have been delegated privileges to modify
user settings; see Delegate Management.
1. On your administrator workstation, start Active Directory Users and
Computers.
2. In the console tree, expand Users, or expand the container that
holds the users that you want.
3. In the details pane, hold down CTRL and click the users that you
want.
4. Right-click on the selected range of users, click Properties, and
then click the Likewise Settings tab.
5. Under UNIX/Linux User Information, select the check box for the
cell that contains the users whose home directory you want to set.
Note: Selecting a check box for a cell assigns the selected users to
the cell and gives them access to the Unix, Linux, and Mac OS
computers that are in the cell.
If the check box for the cell that you want is already selected, click
the name of the cell.
6. In the Login Shell box, type the login shell that you want to set -- for
example, /bin/sh.
Set the Login Shell for a Single User
Note: To change a user's settings, you must log on as a member of the
Domain Administrators security group or the Enterprise Administrators
security group. Or, you must have been delegated privileges to modify
user settings; see Delegate Management.
Copyright © 2007 Likewise Software. All rights reserved. 59
Product Documentation
Likewise 4.0: Administrator’s Guide
1. On your administrator workstation, start Active Directory Users and
Computers.
2. In the console tree, expand Users.
3. Right-click the user that you want, click Properties, and then click
the Likewise Settings tab.
4. In the list under Likewise Cells, click the cell for which you want to
set the user's home directory.
5. In the Login Shell box, type the login shell that you want to set -- for
example, /bin/bash.
Copyright © 2007 Likewise Software. All rights reserved. 60
Product Documentation
Likewise 4.0: Administrator’s Guide
Migrating Users and Finding Orphaned Objects
The Likewise Diagnostics and Migration page provides two tools to help
you manage your mixed network:
• Find Orphaned Objects
• Run Migration Tool
An orphaned object is a linked object, such as a Unix user ID or group
ID, that remains in a cell after you delete a group or user's security
identifier, or SID, from an Active Directory domain. You can use the Find
Orphaned Objects tool to clean up manually assigned user IDs and
improve search speed.
The migration tool imports Linux and Unix passwd files and group files
and maps them to the users and groups defined in Active Directory. The
tool lets you resolve conflicts and ambiguous user names before you
commit the changes.
Migrate Users to Active Directory
You can use the Likewise migration tool to import Linux, Unix, and Mac
OS X passwd and group files -- typically /etc/passwd and
/etc/group -- and automatically map their UIDs and GIDs to users and
groups defined in Active Directory. Or, you can choose to generate a
Windows automation script to associate the Unix and Linux UIDs and
GIDs with Active Directory users and groups. Before you commit the
changes, you can resolve ambiguous user names and other conflicts.
Important: Before you migrate users to a domain that operates in non-
schema mode, it is recommended that you find and remove orphaned
objects. The IDs associated with orphaned objects are reserved until you
remove the orphaned objects. See Find Orphaned Objects.
What You Need Before You Begin
Before running the migration tool, you should have the following
information ready:
• The name of the domain to which you want to migrate the account
information.
• Credentials that allow you to modify the domain.
Copyright © 2007 Likewise Software. All rights reserved. 61
Product Documentation
Likewise 4.0: Administrator’s Guide
• The Unix or Linux passwd file and corresponding group file that you
want to add to Active Directory and manage with Likewise. The
password and group files can be from a computer or an NIS server.
Run the Migration Tool
1. In the Likewise Console, click the Diagnostics & Migration tab.
2. Under Tasks, click Run Migration Tool.
3. Click Next.
4. In the Domain box, type the domain name that you want to migrate
the account information to.
5. If your logon credentials allow you to modify the domain, under
Credentials, select Use logon credentials .
Or, if your logon credentials are not allowed to modify the domain,
select Use alternate credentials, and then enter credentials that
have the appropriate privileges.
6. Click Next.
7. Click Import, and then in the Map name box, type a name that
corresponds to the computer that the passwd and group files are
from.
The migration tool imports the passwd file and group file into the
map file, which is then matched to existing Active Directory user and
group names.
8. In the Passwd file box, type the path and name of the file that you
want to import, or click Browse and then find the file that you want.
9. In the Group file box, type the path and name of the passwd file's
corresponding group file, or click Browse and then find the file.
10. To import default Unix or Linux user accounts such as root and
public, clear the Omit standard Linux/UNIX user accounts
check box.
11. Click Import.
Copyright © 2007 Likewise Software. All rights reserved. 62
Product Documentation
Likewise 4.0: Administrator’s Guide
12. In the list under Users, clear the Import check box for any user that
you do not want to import, and then click Next.
13. Select the organizational unit to which you want to migrate the Linux
or Unix account information.
If you select the top of your domain, the information is migrated to
the default Likewise cell of your Active Directory forest and UID
numbers are automatically assigned within the domain's range.
If you select an organizational unit, Likewise creates a cell for the
organizational unit and migrates the account information to it,
maintaining your UIDs and GIDs if the passwd and group files agree
and if the UIDs and GIDs do not conflict with existing users or
groups. The migrated account information applies only to computers
that are members of the organizational unit.
14. Click Next.
15. Under Migration Options, do any of the following:
To Do This
Create groups in Active Directory that match Select the Create groups in Active
your Linux or Unix groups Directory to match Linux/UNIX groups
check box.
Create all groups in Active Directory -- not Select the Create all groups in AD (not just
just the references ones. To select this referenced ones) check box.
option, you must first you must first select the
Create groups in Active Directory to
match Linux/UNIX groups check box.
Generate script that can repair ownership Select the Generate scripts to repair file
and group settings ownership and group settings check box.
Change the GID of imported users to Select the Change GID of imported users
"Domain Users" to "Domain Users" check box.
Set the alias even if it is the same as Select the Always set Login Name (alias),
sAMAccountName even when same as sAMAccountName
check box.
Generate a Visual Basic script to perform Select the Generated VBScript to perform
migration migration check box, and then in the Script
name box, type a name for the script. In the
Folder for generated scripts box, enter the
directory that you want.
Copyright © 2007 Likewise Software. All rights reserved. 63
Product Documentation
Likewise 4.0: Administrator’s Guide
16. Click Next.
17. Click the Users tab and verify that the information is correct.
18. Click the Groups tab and verify that the information is correct.
19. To import the passwd and group files after you verify that the
information is correct, click Next.
Find Orphaned Objects
You can use Likewise to find and remove orphaned objects. An
orphaned object is a linked object, such as a Unix or Linux user ID or
group ID, that remains in a cell after you delete a group or user's security
identifier, or SID, from an Active Directory domain.
Removing orphaned objects from Active Directory can clean up manually
assigned user IDs and improve search speed. It is recommended that
you remove orphaned objects before you use the migration tool with a
domain that operates in non-schema mode.
1. In the Likewise Console, click the Diagnostics & Migration tab.
2. Under Tasks, click Find Orphaned Objects.
3. Click Select Domains, select the domains that you want to scan,
and then click OK.
4. Click Begin Scan.
5. To remove the objects that appear in the Orphaned objects to
delete box, click Delete Objects.
Copyright © 2007 Likewise Software. All rights reserved. 64
Product Documentation
Likewise 4.0: Administrator’s Guide
Generating Reports
Likewise empowers you to create custom reports about Linux and Unix
users, groups, computers, forests, and domains within Active Directory.
From the Reports tab in the Likewise Console, you can generate the
following reports:
Report Description
Forest Users and Groups Displays all Unix- and Linux-
enabled users and groups in an
Active Directory forest. This
report can also display duplicate
UIDs, GIDs, login names, and
group aliases.
User Access Shows the Unix and Linux
machines that each Active
Directory user can access.
Group Access Lists the Unix and Linux
machines that each Active
Directory group can access.
Group Membership Shows the members of each
Unix- and Linux-enabled Active
Directory group.
Computer Access Lists the users who can access
each Unix and Linux computer.
You can choose the information that you want to include in a report by
selecting from a variety of report columns. Depending on the type of
report, you can select different columns for users, groups, computers,
and cells. When you generate a User Access report, for example, you
can select from such report columns as Login Name, Unix Login Name,
User Status, UID, Primary GID, Gecos, Login Shell, and Home Directory.
Each type of report includes filters and options. All the reports let you
filter by domain. Depending on the type of report that you create, you can
choose whether to show disabled users or disabled computers. For
some reports you can limit the number of objects by specifying a
Copyright © 2007 Likewise Software. All rights reserved. 65
Product Documentation
Likewise 4.0: Administrator’s Guide
maximum. For example, the Group Access report gives you a report
option to set the maximum number o computers per group.
After you generate a report, you can view, save, preview, and print it.
Likewise outputs the report data in XML but displays it in HTML. After
you generate a report, you can save it in XML, HTML, or CSV by clicking
Save As, and then in the Save as type box, clicking the format that you
want.
Create a Computer Access Report
A Computer Access report shows the Active Directory users who can
access each Unix and Linux computer in the scope that you specify. You
can customize the report by selecting the user details, computers, and
domains that the report displays.
1. In the Likewise Console, click the Reports tab.
2. Under Report Name, click Computer Access.
3. In the filters and options panel, click the Report Columns tab.
4. In the tree, expand Users, and then select the information that you
want to include in the report.
The Sample Report gives you a preview of the Report Columns that
you choose.
5. In the tree, expand Computers, and then select the columns that
you want.
6. In the tree, expand Cells, and then select the columns that you
want.
Tip: To reset the selections in the tree under Users, Computers,
and Cells, click Default.
7. Click the Domains tab, and then select the domains that you want
to include in the report.
8. Click the Report Options tab and make the changes that you want.
To limit the number of users that the report shows for each
Copyright © 2007 Likewise Software. All rights reserved. 66
Product Documentation
Likewise 4.0: Administrator’s Guide
computer, in the Maximum users per computer box, type a
number.
9. Click the Computers tab, and then select Show all.
Or, select Show listed, and then click Add.
o In the Select Computers dialog box, click Locations, select the
location you want to search, and then click OK.
o In the Enter the object names to select box, type the name of
one or more computers -- for example, AppSrvSea-1. Separate
multiple entries with semicolons. For a list of examples, click
examples.
o Click Check Names, and then click OK.
Tip: To use additional criteria to search for and select computers,
click Advanced. Then, to show more information about a
computer in the Search results box, click Columns, and add or
remove columns.
10. In the Report Name panel, click Run Report.
Create a Forest Users and Groups Report
A Forest Users and Groups report lists all the Unix- and Linux-enabled
users and groups in an Active Directory forest. You can customize the
report by selecting the user details, group details, domains, and cells that
the report displays.
1. In the Likewise Console, click the Reports tab.
2. Under Report Name, click Forest Users and Groups.
3. In the filters and options panel, click the Report Columns tab.
4. In the tree, expand Users, and then select the information that you
want to include in the report.
The Sample Report gives you a preview of the Report Columns that
you choose.
5. In the tree, expand Groups, and then select the columns that you
want.
Copyright © 2007 Likewise Software. All rights reserved. 67
Product Documentation
Likewise 4.0: Administrator’s Guide
6. In the tree, expand Computers, and then select the columns that
you want.
Tip: To reset the selections under Users, Groups, and Computers,
click Default.
7. Click the Domains tab, and then select the domains that you want
the report to include.
8. Click the Report Options tab and make the changes that you want.
9. Click the Cells tab, and then select Show all.
Or, select Show listed, click Add, and then select the cells that you
want.
10. In the Report Name panel, click Run Report.
Create a Group Access Report
A Group Access report shows the Unix and Linux computers that each
Active Directory group can access. You can customize the report by
selecting the group details, computer information, domains, and groups
that the report displays.
1. In the Likewise Console, click the Reports tab.
2. Under Report Name, click Group Access.
3. In the filters and options panel, click the Report Columns tab.
4. In the tree, expand Groups, and then select the information that you
want to include in the report.
The Sample Report gives you a preview of the Report Columns that
you choose.
5. In the tree, expand Computers, and then select the columns that
you want.
Tip: To reset the selections under Groups and Computers, click
Default.
6. Click the Domains tab, and then select the domains that you want.
Copyright © 2007 Likewise Software. All rights reserved. 68
Product Documentation
Likewise 4.0: Administrator’s Guide
7. Click the Report Options tab, and then make the changes that you
want.
To limit the number of computers that the report will show for each
group, in the Maximum computers per group box, type a number.
8. Click the Groups tab, and then select Show all.
Or, select Show listed, and then click Add.
o In the Select Groups dialog box, click Locations, select the
location you want to search, and then click OK.
o In the Enter the object names to select box, type the name of
one or more groups -- for example, Group Policy Creator
Owners. Separate multiple entries with semicolons. For a list of
examples, click examples.
o Click Check Names, and then click OK.
Tip: To use additional criteria to search for and select groups,
click Advanced. Then, to show more information about a group
in the Search results box, click Columns, and add or remove
columns.
9. In the Report Name panel, click Run Report.
Create a Group Membership Report
A Group Membership report shows the members of your Unix and Linux
Active Directory groups. You can customize the report by selecting the
user details, group details, domains, and groups that the report displays.
1. In the Likewise Console, click the Reports tab.
2. Under Report Name, click Group Membership.
3. In the filters and options panel, click the Report Columns tab.
4. In the tree, expand Users, and then select the information that you
want to include in the report.
The Sample Report gives you a preview of the Report Columns that
you choose.
Copyright © 2007 Likewise Software. All rights reserved. 69
Product Documentation
Likewise 4.0: Administrator’s Guide
5. In the tree, expand Groups, and then select the columns that you
want.
Tip: To reset the selections under Users and Groups, click Default.
6. Click the Domains tab, and then select the domains that you want.
7. Click the Report Options tab, and then make the changes that you
want.
8. Click the Groups tab, and then select Show all.
Or, select Show listed, and then click Add.
o In the Select Groups dialog box, click Locations, select the
location you want to search, and then click OK.
o In the Enter the object names to select box, type the name of
one or more groups -- for example, Group Policy Creator
Owners. Separate multiple entries with semicolons. For a list of
examples, click examples.
o Click Check Names, and then click OK.
Tip: To use additional criteria to search for and select groups,
click Advanced. Then, to show more information about a group
in the Search results box, click Columns, and add or remove
columns.
9. In the Report Name panel, click Run Report.
Create a User Access Report
A User Access report shows the Unix and Linux computers that each
Active Directory user can access. You can customize the report by
selecting the user details, computer information, domains, and users that
the report displays.
1. In the Likewise Console, click the Reports tab.
2. Under Report Name, click User Access.
3. In the filters and options panel, click the Report Columns tab.
Copyright © 2007 Likewise Software. All rights reserved. 70
Product Documentation
Likewise 4.0: Administrator’s Guide
4. In the tree, expand Users, and then select the information that you
want to include in the report.
The Sample Report gives you a preview of the Report Columns that
you choose.
5. In the tree, expand Computers, and then select the columns that
you want.
Tip: To reset the selections under Users and Computers, click
Default.
6. Click the Domains tab, and then select the domains that you want.
7. Click the Report Options tab, and then make the changes that you
want.
To limit the number of computers that the report will show for each
user, in the Maximum computers per user box, type a number.
8. Click the Users tab, and then select Show all.
Or, select Show listed, and then click Add.
o In the Select Users dialog box, click Locations, select the
location you want to search, and then click OK.
o In the Enter the object names to select box, type the name of
one or more of the following object types, separated by
semicolons: DisplayName; ObjectName; UserName;
ObjectName@DomainName; DomainName\ObjectName. For a
list of examples, click examples.
o Click Check Names, and then click OK.
Tip: To use additional criteria to search for and select users, click
Advanced. Then, to show more information about a user in the
Search results box, click Columns, and add or remove
columns.
9. In the Report Name panel, click Run Report.
Show Computer Access by Cell
You can generate a Computer Access report to show the users who
have access to the Linux and Unix computers in each Likewise cell
Copyright © 2007 Likewise Software. All rights reserved. 71
Product Documentation
Likewise 4.0: Administrator’s Guide
within the scope that you specify. You can customize the report by
selecting the user details, computers, and domains that the report
displays.
1. In the Likewise Console, click the Reports tab.
2. Under Report Name, click Computer Access.
3. In the filters and options panel, click the Report Columns tab.
4. In the tree, expand Users, and then select the information that you
want to include in the report.
The Sample Report gives you a preview of the Report Columns that
you choose.
5. In the tree, expand Computers, and then select the columns that
you want.
Tip: To reset the selections in the tree under Users, Computers,
and Cells, click Default.
6. In the tree, select Cells, and then expand Cells and select Cell
Name:
Copyright © 2007 Likewise Software. All rights reserved. 72
Product Documentation
Likewise 4.0: Administrator’s Guide
7. Click the Domains tab, and then select the domains that you want
to include in the report.
8. Click the Report Options tab and make the changes that you want.
To limit the number of users that the report shows for each
computer, in the Maximum users per computer box, type a
number.
9. Click the Computers tab, and then select Show all.
Or, select Show listed, and then click Add.
o In the Select Computers dialog box, click Locations, select the
location you want to search, and then click OK.
o In the Enter the object names to select box, type the name of
one or more computers -- for example, AppSrvSea-1. Separate
multiple entries with semicolons. For a list of examples, click
examples.
o Click Check Names, and then click OK.
Tip: To use additional criteria to search for and select computers,
click Advanced. Then, to show more information about a
computer in the Search results box, click Columns, and add or
remove columns.
10. In the Report Name panel, click Run Report.
Show Duplicate UIDs, GIDs, Login Names, and Group Aliases
A Forest Users and Groups report can list all the duplicate UIDs, GIDs,
Login Names, and Group Aliases in an Active Directory forest. You can
customize the report by selecting the user details, group details,
domains, and cells that the report displays.
Generating a report that shows duplicate UIDs, GIDs, Login Names, and
Group Aliases can help you troubleshoot and resolve conflicts within
your Active Directory forest.
1. In the Likewise Console, click the Reports tab.
2. Under Report Name, click Group Membership.
Copyright © 2007 Likewise Software. All rights reserved. 73
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the filters and options panel, click the Report Columns tab.
4. In the tree, expand Users, and then select the information that you
want to include in the report. To show duplicates, select UID,
Primary GID, and Login Name.
The Sample Report gives you a preview of the Report Columns that
you choose.
5. In the tree, expand Groups, and then select or clear the columns
that you want. To show duplicates, select Group Alias and GID.
6. In the tree, expand Computers, and then select or clear the
columns that you want.
7. In the tree, expand Duplicates, and then select or clear the columns
that you want:
8. Click the Domains tab, and then select the domains that you want
the report to include.
Copyright © 2007 Likewise Software. All rights reserved. 74
Product Documentation
Likewise 4.0: Administrator’s Guide
9. Click the Report Options tab and make the changes that you want.
10. Click the Cells tab, and then select Show all.
Or, select Show listed, click Add, and then select the cells that you
want.
11. In the Report Name panel, click Run Report.
Copyright © 2007 Likewise Software. All rights reserved. 75
Product Documentation
Likewise 4.0: Administrator’s Guide
Working with Group Policies
Likewise empowers you to define group policies for computers running
Linux, Unix, and Mac OS X. Likewise includes more than 100 policies
that are custom made for non-Windows computers. All the policies are
integrated into the Microsoft Group Policy Object Editor.
For example, you can use a group policy to control who can use sudo for
access to root-level privileges by specifying a common sudoers file for
target computers. You could, for instance, create an Active Directory
group called SudoUsers, add Active Directory users to the group, and
then apply the sudo group policy to the container, giving those users
sudo access on their Linux and Unix computers. In the sudoers file, you
can specify Windows-style user names and identities. Using a group
policy for sudo gives you a powerful method to remotely and uniformly
audit and control access to Unix and Linux resources.
Likewise stores its Unix and Linux group policies in the same locations
and in the same format as the default Windows group policies -- in the
system volume (sysvol) shared directory. Unix and Linux computers
that are joined to an Active Directory domain receive their group policies
in the same way that a Windows system does:
To create or change a group policy, you must be logged on as a member
of the Domain Administrators security group, the Enterprise
Administrators security group, or the Group Policy Creator Owners
security group. With the Microsoft Group Policy Management Console,
you can grant users permission to create Group Policy Objects (GPOs).
Likewise gives you the option of creating and editing group policies with
either the Group Policy Object Editor (GPOE) or the Group Policy
Copyright © 2007 Likewise Software. All rights reserved. 76
Product Documentation
Likewise 4.0: Administrator’s Guide
Management Console (GPMC). When you use the Group Policy
Management Console, you can view group policy settings.
In the Group Policy Object Editor, the Likewise group policies are in the
UNIX and Linux Settings folder in the console tree under Computer
Configuration; the Likewise user settings are under User Configuration:
User Settings
Likewise includes several hundred group policies for Linux user settings -
- policies that are based on the Gnome GConf project to define desktop
and application preferences such as the default web browser. You can
apply the group policies for user settings only to Linux computers that
are running the Gnome desktop.
For information about the group policies for user settings, see About
User Settings.
Copyright © 2007 Likewise Software. All rights reserved. 77
Product Documentation
Likewise 4.0: Administrator’s Guide
The Group Policy Agent
The Likewise Group Policy Agent is automatically installed when you
install the Likewise Agent on a Linux, Unix, or Mac OS X computer.
To apply group policies and enforce them on a computer, the Group
Policy Agent runs continuously as a daemon. It processes both user
policy and computer policy types. For computer policies, the agent
traverses the computer's distinguished name (DN) path in Active
Directory. For a user's policy processing, which occurs when a user logs
on, the agent traverses the user's DN path in Active Directory. The
Group Policy Agent uses the computer’s machine account credentials to
securely retrieve policy template files over the network from the domain’s
protected system volume shared directory. The Likewise Group Policy
Agent, however, does not apply Windows policies.
The Group Policy Agent connects to Active Directory, retrieves changes,
and applies them once every 30 minutes, when a computer boots or
restarts, or when requested by the GPO refresh tool.
The GPO Refresh Tool
To force a Unix, Linux, or Mac OS X computer to pull the latest version of
its group policies, you can run the GPO refresh tool at any time on the
computer that you want to update. To run the GPO refresh tool on a
Linux computer, execute the following command at the shell prompt:
/usr/centeris/bin/gporefresh
On a Unix or Mac OS X computer, the command is slightly different:
/opt/centeris/bin/gporefresh
The command should return a result that looks like this:
20070731100621:0xb7f046c0:INFO:GPO Refresh succeeded
On target computers, Likewise stores its group policies in
/var/cache/centeris/grouppolicy.
Inheritance
The Likewise group policies are of two general types: file based or
property based. Most policies are property based. Property-based
policies are inherited, meaning that the location of a GPO within the
Copyright © 2007 Likewise Software. All rights reserved. 78
Product Documentation
Likewise 4.0: Administrator’s Guide
Active Directory hierarchy can affect its application. Property-based
policies do not replace local policies -- they merge with them.
File-based policies -- such as sudo and automount -- typically replace the
local file. File-based policies are not inherited and do not merge with the
local file.
Filtering by Target Platform
You can set group policies to target all versions of the following
platforms. Some group policies, however, apply only to specific
platforms. For instance, some group polices apply only to Linux. For
more information, see the Help topic for the group policy that you want to
use.
• Apple Mac OS X
• CentOS Linux
• Debian Linux
• Fedora Linux
• Hewlett-Packard HP-UX
• IBM AIX
• OpenSUSE Linux
• Red Hat Linux
• Red Hat Enterprise Linux (ES and AS)
• Sun Solaris
• SUSE Linux
• SUSE Linux Enterprise Desktop
• SUSE Linux Enterprise Server
• Ubuntu Linux
To target a group policy at a platform, see Set Target Platforms.
Copyright © 2007 Likewise Software. All rights reserved. 79
Product Documentation
Likewise 4.0: Administrator’s Guide
Create or Edit a Group Policy
You can create or edit a group policy for computers running Linux, Unix,
and Mac OS X by using either the Group Policy Object Editor (GPOE) or
the Group Policy Management Console (GPMC).
Important: To create or edit a group policy, you must log on as a
member of the Domain Administrators security group, the Enterprise
Administrators security group, or the Group Policy Creator Owners
security group.
1. On your administrator workstation, start Active Directory Users and
Computers.
2. In the tree, right-click the organizational unit that you want, and then
click Properties.
Note: Make sure the organizational unit is associated with a
Likewise cell. For more information, see Create a Cell.
3. Click the Group Policy tab. How you proceed depends on whether
you have the Microsoft Group Policy Management Console (GPMC)
installed:
If you do not have GPMC If you have GPMC installed,
installed, do this: do this:
1. Click New. 1. Click Open.
2. Type a name for your group 2. In the Group Policy
policy object -- for example, Management Console, right-
message of the day. click the organizational unit that
you want, and then click Create
and Link a GPO Here.
3. Click the group policy object 3. In the Name box, type a
that you created and then click name for your group policy
Edit. object.
4. Click the group policy object
that you created, and then on
the Action menu, click Edit.
Copyright © 2007 Likewise Software. All rights reserved. 80
Product Documentation
Likewise 4.0: Administrator’s Guide
4. In the Group Policy Object Editor, in the console tree under
Computer Configuration or User Configuration, find the group
policy category that you want, and then in the details pane, double-
click the policy that you want to set.
In the console tree, the Likewise group policies are under Unix and
Linux Settings. For instructions on how to configure a Likewise
group policy, see the Help topic for the policy that you want to use.
Tip: You can download the Microsoft Group Policy Management
Console at http://www.microsoft.com/downloads/.
Apply a Group Policy to a Cell
To apply a group policy to a cell, you must first associate the cell with an
organizational unit. For more information, see Create a Cell.
1. In Active Directory Users and Computers, right-click the
organizational unit that you want to apply a group policy to, and then
click Properties.
2. Click the Group Policy tab, and then click New.
3. Enter a name for the group policy object.
4. In the list, click the GPO, and then click Edit.
5. In the Group Policy Object Editor, in the console tree under
Computer Configuration, find the group policy category that you
want, and then in the details pane, double-click the policy that you
want to set.
In the console tree, the Likewise group policies are under UNIX and
Linux Settings. For instructions on how to configure a Likewise
group policy, see the Help topic for the policy that you want to use.
Set Target Platforms
By using Likewise, you can set the target platforms for a group policy.
The policy's settings are applied only to the platforms that you choose.
You can set the target platforms by operating system, distribution, and
version. For example, you can create a group policy and then target it
only at computers running SUSE Linux Enterprise Server. Or, you can
target the policy at a mixture of operating systems and distributions, such
as Red Hat Linux, Sun Solaris, Ubuntu Desktop, and HP-UX. In addition,
you can target some policies at computers running Mac OS X.
Copyright © 2007 Likewise Software. All rights reserved. 81
Product Documentation
Likewise 4.0: Administrator’s Guide
Note: Some group policies do not apply to all platforms or versions. For
more information, see the Help topic for the group policy that you are
configuring.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration or under User Configuration, expand
Unix and Linux Settings, and then click Target Platform Filter:
3. In the details pane, double-click Target platforms.
4. To target all the platforms in the list, select All.
Or, to choose the platforms that you want to target, click Select
from the List, and then in the list, select the platforms that you
want.
Copyright © 2007 Likewise Software. All rights reserved. 82
Product Documentation
Likewise 4.0: Administrator’s Guide
Create and Test a Sudo Group Policy
By using either the Group Policy Object Editor (GPOE) or the Group
Policy Management Console (GPMC), you can define a group policy to
specify a sudo configuration file for target computers running Linux, Unix,
and Mac OS X.
Sudo, or superuser do, allows a user to run a command as root or as
another user. The sudo configuration file is copied to the local machine
and replaces the local sudoers file. A sudo file can reference local
users and groups or Active Directory users and groups. For more
information about sudo, see the man pages for your system.
When you define the policy, you can also set its target platforms. The
policy's settings are applied only to the operating systems, distributions,
and versions that you choose. For example, you can target the policy
only at computers running SUSE Linux Enterprise Server. Or, you can
target the policy at a mixture of operating systems and distributions, such
as Mac OS X, Red Hat Linux, Sun Solaris, Ubuntu Desktop, and HP-UX.
Important: To create a group policy, you must log on your Windows
administrative workstation as a member of the Domain Administrators
security group, the Enterprise Administrators security group, or the
Group Policy Creator Owners security group.
Create a Sudo Group Policy
1. On your Windows administrator workstation, start Active Directory
Users and Computers.
2. In the tree, right-click the organizational unit that you want, and then
click Properties.
Note: Make sure the organizational unit is associated with a
Likewise cell. For more information, see Create a Cell.
3. Click the Group Policy tab. How you proceed depends on whether
you have the Microsoft Group Policy Management Console (GPMC)
installed:
If you do not have GPMC If you have GPMC installed, do
installed, do this: this:
1. Click New. 1. Click Open.
2. Type a name for your group 2. In the Group Policy Management
Copyright © 2007 Likewise Software. All rights reserved. 83
Product Documentation
Likewise 4.0: Administrator’s Guide
policy object -- for example, Console, right-click the
message of the day. organizational unit that you want,
and then click Create and Link a
GPO Here.
3. Click the group policy object that 3. In the Name box, type a name
you created and then click Edit. for your group policy object.
4. Click the group policy object that
you created, and then on the
Action menu, click Edit.
4. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Security Settings, and then click SUDO command:
5. In the details pane, double-click Define Sudoer file, select the
Define this Policy Setting check box, and then in the Current file
content box, type your commands.
Or, to import a sudo configuration file, click Import, and then find the
file that you want.
Copyright © 2007 Likewise Software. All rights reserved. 84
Product Documentation
Likewise 4.0: Administrator’s Guide
6. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings, and
then click Target Platform Filter.
Copyright © 2007 Likewise Software. All rights reserved. 85
Product Documentation
Likewise 4.0: Administrator’s Guide
7. In the details pane, double-click Target platforms.
8. To target all the platforms in the list, select All.
Or, to choose the platforms that you want to target, click Select
from the List, and then in the list, select the platforms that you
want.
Tip: You can download the Microsoft Group Policy Management
Console at http://www.microsoft.com/downloads/.
Test the Sudo Group Policy
After you set the sudo group policy, you can test it on a target computer.
The target computer must be in a cell associated with the organizational
unit that you set the sudoers policy for.
1. On a target Linux computer, log on as an administrator and execute
the following command to force group policies to refresh:
/usr/centeris/bin/gporefresh
Copyright © 2007 Likewise Software. All rights reserved. 86
Product Documentation
Likewise 4.0: Administrator’s Guide
On a Unix computer, the command is slightly different:
/opt/centeris/bin/gporefresh
2. Check whether your sudoers file is on the computer:
cat /etc/sudoers
3. Log on the Unix or Linux computer as a regular user who has sudo
privileges as specified in the sudoers configuration file.
4. Try to access a system resource that requires root access using
sudo. When prompted, use the password of the user you are logged
on as, unless targetpw is set in the sudoers file.
Verify that the user was authenticated and that the user can access
the system resource.
Test Sudo Security
1. Log on as a user who is not enabled with sudo in the sudoers file
that you used to set the group policy.
2. Verify that the user cannot perform root functions using sudo with
his or her Active Directory credentials.
View a Report on a Group Policy's Settings
If you have the Group Policy Management Console installed on your
administrative workstation, you can view a report that shows the settings
for a Likewise group policy. The Microsoft Group Policy Management
Console can be downloaded for free at
http://www.microsoft.com/downloads/.
1. In the Microsoft Group Policy Management Console, in the console
tree, expand the domain that you want, expand Group Policy
Objects, and then click the group policy object for which you want to
view a report.
2. In the details pane, click the Settings tab. The console generates
and displays the report. Here's an example:
Copyright © 2007 Likewise Software. All rights reserved. 87
Product Documentation
Likewise 4.0: Administrator’s Guide
Tip: To view other information about the group policy, click one of the
other tabs -- for example, Scope.
About User Settings
Likewise lets you set group policies for Linux user settings -- policies
based on the Gnome GConf project to define desktop and application
preferences such as the default web browser.
Important: You can apply group policies for user settings only to Linux
computers that are running the Gnome desktop.
To set the policies, use the Group Policy Object Editor. After you add the
Gnome schemas for your Linux platform, the policies appear in the Unix
and Linux User Settings folder under User Configuration:
Copyright © 2007 Likewise Software. All rights reserved. 88
Product Documentation
Likewise 4.0: Administrator’s Guide
There are several thousand Gnome-based group policies. They include
user settings for applications like the browser, help viewer, and main
menu. They also include settings for tailoring the keyboard for
accessibility, specifying URL handlers, and configuring volume manager.
For example, you can set a user policy to define whether the Gnome
volume manager automatically mounts removable storage drives when
they are inserted into a computer.
Note: Different Linux distributions with the same Gnome desktop version
may contain different Gnome-based user settings. The Gnome-based
group policies that are available for Red Hat, for example, might differ
from those that are available for SUSE.
Because there are so many group policies for user settings, there are
only two Help topics for them:
• Example: Set the Default Web Browser for a Gnome Desktop
• Example: Set a Firefox Home Page URL
These two topics show you how to define a Gnome-based group policy.
The procedure for defining the other policies is the same as or similar to
Copyright © 2007 Likewise Software. All rights reserved. 89
Product Documentation
Likewise 4.0: Administrator’s Guide
that of the two example topics -- it's just a matter of finding the policy that
you want in the Group Policy Object Editor's console tree.
Storing Gnome GConf Preferences
GConf is a system for storing user preferences for applications that
makes managing preferences easier for system administrators. On target
computers with desktops running Gnome, the preferences that you set in
the group policies are stored in a series of storage locations called
configuration sources. The addresses of the sources are specified in a
file called /etc/gconf/<version>/path -- for example,
/etc/gconf/2/path. (The location of the sources can vary by
platform.) Each configuration source has an XML backend that stores
data in XML files.
Likewise uses GConf version 2. For more information, see the Gnome
GConf project at http://www.gnome.org/projects/gconf/.
GConf Per-User Daemon
The GConf implementation runs a daemon for each user: gconfd. The
daemon notifies applications when a configuration value has changed. It
also caches values so that each application doesn't have to parse XML
files. The daemon typically quits a few minutes after the last application
using it has stopped running.
You can force the GConf daemon to reload its cache by executing the
following command at the shell prompt on a target Linux computer:
killall -HUP gconfd-2
GConf Tool
GConf includes a command-line tool, gconftool-2. You can use it to
display some of the Gnome desktop settings:
gconftool-2 -R /desktop/gnome
Because Likewise provides group policies to manage Gnome desktop
settings, you typically do not need to use the GConf command-line tool.
Schema Files
A schema is a set of metainformation that describes a configuration
setting. The metainformation includes the type of value, documentation
on the setting, and the factory default for the value. On target computers
running the Gnome desktop, the schema files are stored in
Copyright © 2007 Likewise Software. All rights reserved. 90
Product Documentation
Likewise 4.0: Administrator’s Guide
/etc/gconf/schemas. When you define or change a user-setting
group policy, the Likewise software on the target computer pulls the
change and modifies the schema accordingly.
To use a schema, however, you must first load it. Likewise includes
schemas in ZIP file format for a number of common platforms, including
Fedora, Open SuSE, and Red Hat. If the schemas for your target
platform are not included with Likewise, you must copy them from your
Linux platform to a location that you can access from a Windows
administrative desktop that runs the Likewise Console. For instructions
on how to load Gnome schemas, see Add Gnome Schemas.
Add Gnome Schemas
Before you can apply group policies for Gnome-based user settings, you
must add the schemas to the Gnome Configuration Settings folder in the
Group Policy Object Editor (GPOE). You can obtain the schemas in two
ways:
• Extract the schemas from the ZIP files that Likewise includes for a
number of common platforms. Likewise comes with ZIP files
containing schemas for Fedora, Red Hat, Debian, CentOS, Ubuntu,
and several versions of SUSE.
• Copy the Gnome schemas from a Linux computer to a directory that
you can access from a Windows administrative workstation that is
running the Likewise Console. The schema files are typically stored in
/etc/gconf/schemas.
Likewise uses GConf version 2. For more information, see the Gnome
GConf project at http://www.gnome.org/projects/gconf/.
Important: To use the Gnome-based user settings, the target Linux
computer must be running the Gnome desktop.
1. On your Windows administrative workstation, in the Group Policy
Object Editor, expand User Configuration, and then expand Unix
and Linux User Settings.
2. Right-click Gnome Configuration Settings, and then click
Add/Remove Gnome schemas:
Copyright © 2007 Likewise Software. All rights reserved. 91
Product Documentation
Likewise 4.0: Administrator’s Guide
3. Click Add, right-click the ZIP file for your platform, click Extract All,
and then follow the instructions in the Extraction Wizard.
Or, if the schema files for your target platform are not included with
Likewise, use SCP or FTP to copy the Gnome schemas from
/etc/gconf/schemas on the target Linux system to a directory,
drive, or server that you can access from a Windows administrative
workstation that is running the Likewise Console and that you use to
apply group policies.
Note: The schema directory varies by platform; the path might be
different on your system.
4. Locate the directory containing the schemas that you want to load,
select the schemas you want, click Open, and then click OK:
Copyright © 2007 Likewise Software. All rights reserved. 92
Product Documentation
Likewise 4.0: Administrator’s Guide
5. In the GPOE console tree, right-click Gnome Configuration
Settings, and then click Refresh.
The policies appear under Gnome Configuration Settings:
Copyright © 2007 Likewise Software. All rights reserved. 93
Product Documentation
Likewise 4.0: Administrator’s Guide
Tip: Different Linux distributions with the same Gnome desktop
version may contain different Gnome schema-based user settings.
The Gnome group policies that are available for OpenSUSE, for
example, are differ from those that are available for SLED.
Because the user settings can be different for each platform, you
must manage your Gnome group policies so that you can distinguish
the platform to which the policy is applied. For example, you might
want to set different group policy objects for each platform and
include the name of the platform in the name of the GPO, like this:
RHEL_url-handler_mailto.
Example: Set a Firefox Home Page URL
You can use a group policy based on a Gnome GConf schema to set a
home page URL for Firefox on target Linux computers running the
Gnome desktop.
The procedure for setting other GConf schema-based group policies are
similar to the following steps. In the console tree of the Group Policy
Object Editor, all the GConf group policies are in the Unix and Linux
Settings folder under User Configuration.
Important: You can apply group policies for user settings only to Linux
computers that are running the Gnome desktop.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under User
Configuration, expand Unix and Linux Settings, expand Gnome
Configuration Settings, expand Apps, expand Firefox, and then
click General.
Copyright © 2007 Likewise Software. All rights reserved. 94
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click homepage_url, and then select the
Define this policy setting check box.
4. In the String Value box, enter the URL for home page that you want
to set -- for example, www.likewisesoftware.com.
Copyright © 2007 Likewise Software. All rights reserved. 95
Product Documentation
Likewise 4.0: Administrator’s Guide
Example: Set the Default Web Browser for a Gnome Desktop
You can use a group policy to set the default Web browser on target
Gnome desktop-compatible Linux computers. The user policy is based
on a Gnome GConf schema.
The procedure for setting other GConf schema-based group policies are
similar to the following steps. In the console tree of the Group Policy
Object Editor, all the GConf group policies are in the Unix and Linux
Settings folder under User Configuration.
Important: You can apply group policies for user settings only to Linux
computers that are running the Gnome desktop.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under User
Configuration, expand Unix and Linux Settings, expand Gnome
Configuration Settings, expand Desktop, expand Gnome, expand
Applications, and then click Browser.
Copyright © 2007 Likewise Software. All rights reserved. 96
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click exec, and then select the Define
this policy setting check box.
4. In the String Value box, enter the name of the application for the
browser that you want to set -- for example, firefox.
Display Settings
Change the Screen Saver Theme Interval
Likewise lets you define a group policy on target Unix and Linux
computers that sets the interval when the screen saver's theme changes.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the theme interval to the Gnome configuration registry, overriding
the user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Display Settings, and then click Gnome Settings:
Copyright © 2007 Likewise Software. All rights reserved. 97
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Change the screensaver theme
interval, and then select the Define this Policy Setting check box.
4. In the Change after box, enter the number of minutes to display a
theme before changing it.
Display a Keyboard in the Screen Saver
Likewise lets you define a group policy on target Linux and Unix
computers that displays a virtual keyboard in the screen saver so that a
user with limited dexterity can unlock the computer. You can also use
this policy for kiosk installations that have a touch screen and no
keyboard.
This policy works on computers running a version of Linux or Unix that
includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the setting to the Gnome configuration registry, overriding the
user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the tree under Computer
Configuration, expand Unix and Linux Settings, expand Display
Settings, and then click Gnome Settings.
3. In the details pane, double-click Show keyboard in Screen Saver,
and then select the Define this Policy Setting check box.
4. Click Enabled or Disabled.
Display a Screen Saver Logout Option
Likewise lets you define a group policy on target Unix and Linux
computers to show a logout option in the screen saver's unlock dialog.
Copyright © 2007 Likewise Software. All rights reserved. 98
Product Documentation
Likewise 4.0: Administrator’s Guide
You can also set a delay before the logout option becomes available in
the unlock dialog. To set a delay, see Set the Time till Logout Option Is
Available.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the logout option to the Gnome configuration registry, overriding the
user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the tree under Computer
Configuration, expand Unix and Linux Settings, expand Display
Settings, and then click Gnome Settings.
3. In the details pane, double-click Show screensaver logout option,
and then select the Define this Policy Setting check box.
4. Select Enabled or Disabled.
Display a Switch User Option with the Screen Saver
Likewise lets you define a group policy on target Unix and Linux
computers to display an option to switch user in the screen saver's
unlock dialog.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the switch user option to the Gnome configuration registry,
overriding the user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the tree under Computer
Configuration, expand Unix and Linux Settings, expand Display
Settings, and then click Gnome Settings.
3. In the details pane, double-click Show screensaver switch user
option, and then select the Define this Policy Setting check box.
Copyright © 2007 Likewise Software. All rights reserved. 99
Product Documentation
Likewise 4.0: Administrator’s Guide
4. Select Enabled or Disabled.
Display Screen Saver When a Session Is Idle
By using Likewise, you can define a group policy that displays the screen
saver on target Unix and Linux computers after a session becomes idle.
To set the idle delay, see Set the Screen Saver Idle Delay.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the settings that you define to the Gnome registry, overriding the
user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the tree under Computer
Configuration, expand Unix and Linux Settings, expand Display
Settings, and then click Gnome Settings.
3. In the details pane, double-click Screensaver Idle Activation, and
then select the Define this Policy Setting check box.
4. Select Enabled or Disabled.
Embed a Keyboard Command in the Screen Saver
Likewise lets you define a group policy on target Linux and Unix
computers that embeds a keyboard command in the screen saver. You
can use the embedded keyboard command for kiosk installations that
have a touch screen and no keyboard.
The command that you associate with this policy must implement an
XEmbed plug interface and output a window XID on the standard output.
XEmbed is a protocol that uses basic X mechanisms, such as client
messages and reparenting windows, to embed a control from one
application in another.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the setting to the Gnome configuration registry, overriding the
user's local settings.
Copyright © 2007 Likewise Software. All rights reserved. 100
Product Documentation
Likewise 4.0: Administrator’s Guide
Important: To embed a keyboard command in the screen saver, you
must define and enable the Show Keyboard in the Screen Saver group
policy.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the tree under Computer
Configuration, expand Unix and Linux Settings, expand Display
Settings, and then click Gnome Settings.
3. In the details pane, double-click Screensaver embedded keyboard
command, and then select the Define this Policy Setting check
box.
4. In the Command to run box, type a command that implements an
XEmbed plug interface and outputs a window XID on the standard
output.
For example, if the Matchbox Keyboard application is installed on
the target computer and you want to run it, you can type the
following command in the Command to run box:
matchbox-keyboard --xid
Lock the Screen with the Screen Saver
By using Likewise, you can define a group policy on target Unix and
Linux computers that locks the screen when the screen saver comes on.
This policy can help prevent unauthorized access to idle machines.
To set the interval between the time that the screen saver comes on and
the time that the screen is locked, see Set the Screen Lockout Interval. If
you do not specify the lockout interval, this policy locks the screen when
screen saver becomes active.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the setting to the Gnome configuration registry, overriding the
user's local settings.
Copyright © 2007 Likewise Software. All rights reserved. 101
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the tree under Computer
Configuration, expand Unix and Linux Settings, expand Display
Settings, and then click Gnome Settings.
3. In the details pane, double-click Screensaver to lock system, and
then select the Define this Policy Setting check box.
4. Select Enabled or Disabled.
Run a Logout Command from the Screen Saver Dialog
Likewise lets you define a group policy on target Unix and Linux
computers to run a command when a user logs out from the screen
saver's dialog. It is recommended that you use this command only to log
the user out without any other interaction.
For this policy to work, you must define and enable the group policy to
show the screensaver logout option; see Display a Screen Saver Logout
Option.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the logout command to the Gnome configuration registry, overriding
the user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Display Settings, and then click Gnome Settings.
3. In the details pane, double-click Screensaver logout command,
and then select the Define this Policy Setting check box.
4. In the Command to run box, type the command that you want to
run.
Copyright © 2007 Likewise Software. All rights reserved. 102
Product Documentation
Likewise 4.0: Administrator’s Guide
Set the Screen Lockout Interval
With Likewise, you can define a group policy on target Unix and Linux
computers that sets the lockout interval for the Lock the Screen with the
Screen Saver policy.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the setting to the Gnome configuration registry, overriding the
user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Display Settings, and then click Gnome Settings.
3. In the details pane, double-click Screensaver time till lockout is
enforced, and then select the Define this Policy Setting check
box.
4. In the Lock after box, enter the number of minutes that you want
between the time that the screen saver becomes active and the time
that lockout occurs.
Set the Screen Saver Idle Delay
With Likewise, you can define a group policy that specifies the minutes of
inactivity before the screen saver is displayed on target Unix and Linux
computers.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the idle delay setting to the Gnome configuration registry,
overriding the user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
Copyright © 2007 Likewise Software. All rights reserved. 103
Product Documentation
Likewise 4.0: Administrator’s Guide
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Display Settings, and then click Gnome Settings.
3. In the details pane, double-click Screensaver Idle Delay, and then
select the Define this Policy Setting check box.
4. In the Activate screensaver after box, enter the minutes of
inactivity that are allowed before the session is considered idle and
the screen saver is displayed.
Set the Time till the Logout Option Is Available
You can define a group policy on target Unix and Linux computers to set
a delay before the logout option becomes available in the unlock dialog.
For this policy to work, you must define the group policy that displays the
logout option; see Display a Screen Saver Logout Option.
You can use this policy on computers running a version of Linux or Unix
that includes Gnome desktop 2.12 or later. The policy, which is inherited,
adds the logout option interval to the Gnome configuration registry,
overriding the user's local settings.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Display Settings, and then click Gnome Settings.
3. In the details pane, double-click Screensaver time till logout
option is offered, and then select the Define this Policy Setting
check box.
4. In the Show logout option after box, enter the minutes that you
want the screen saver to wait until it displays the logout option in the
unlock dialog.
Copyright © 2007 Likewise Software. All rights reserved. 104
Product Documentation
Likewise 4.0: Administrator’s Guide
File System Settings
Automount a File System
By using Likewise, you can create a group policy to start a daemon that
automatically mounts a file system on target Unix and Linux computers.
When a user attempts to access an unmounted file system, the file that
you associate with this policy automatically mounts it.
This policy, which can be especially helpful in large networks, has
several uses:
• Automount NFS, Samba, and boot mounts or partitions.
• Cross-mount file systems between a few machines, especially
machines that are not always online.
• Switch between a forced-on ASCII conversion mount of a DOS file
system and a forced-off ASCII conversion mount of the same DOS file
system.
• Automount removable devices.
You can use this policy on computers running Linux, Unix, or Mac OS X.
This policy replaces the local file. It is not inherited and does not merge
with the local file. For more information, see About Group Policies.
Automount a File System
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand File System Settings, and then click AutoMount:
Copyright © 2007 Likewise Software. All rights reserved. 105
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click AutoMount, and then select the
Define this Policy Setting check box.
4. Click Add, type the name of the file you want, or click Browse and
then find the file you want.
5. If the file is executable, select the File is executable check box.
6. Click OK.
Create Directories, Files, and Links
By using Likewise, you can define a group policy to create directories,
files, and symbolic links on target Unix and Linux computers.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is not inherited, does not concatenate a series of
settings across multiple group policy objects in different locations within
the Active Directory hierarchy. Instead, the closest local policy object is
applied.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand File System Settings, and then click Files, Directories
and Links.
3. In the details pane, double-click Create Directories, Install Files,
Configure Links, and then select the Define this Policy Setting
check box.
4. Click Add, click the type of object that you want, and then click OK.
5. Use the Object Editor that appears to set the object's paths and
other file system properties.
Tip: To change an object's properties later, click the object in the
list, and then click Edit.
Copyright © 2007 Likewise Software. All rights reserved. 106
Product Documentation
Likewise 4.0: Administrator’s Guide
Specify the File System Mounts (fstab)
With Likewise, you can create a group policy for the file systems table, or
fstab, on target Unix and Linux computers and add mount entries to it by
using a graphical user interface. Fstab, typically located in /etc/fstab,
is a configuration file that specifies how a computer is to mount partitions
and storage devices.
This policy can add the following kinds of file systems to fstab:
• Common Internet File System (cifs)
• Linux Native File System (ext2)
• New Linux Native File System (ext3)
• ISO9660 CD-ROM (iso9660)
• Network File System (NFS)
• Network File System version 4 (NFS4)
Important: For cifs and iso9660 file systems, make sure the owner and
group objects in Active Directory are enabled in a Likewise cell. Doing so
defines UID and GID values for the objects on the systems where the
policy setting is to take effect.
You can use this policy with computers running Linux or Unix; the policy,
however, does not work with Mac OS X.
This policy replaces the local policies. It is not inherited and does not
merge with the local settings. For more information, see About Group
Policies.
Specify File System Mounts
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand File System Settings, and then click File System Mounts
(fstab).
Copyright © 2007 Likewise Software. All rights reserved. 107
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click File System Mount, and then
select the Define this Policy Setting check box.
4. Click Add, click the type of file system that you want to mount, and
then click OK.
5. Use the Add New Mount Wizard to specify the mount details for the
type of file system that you want to mount.
After you use the wizard to add a file system, you can edit the mount
details and options by clicking the mount entry in the list and then
clicking Edit.
6. To disable the mount, in the list of mount entries, under Status,
double-click Enabled.
Likewise Settings
Acquire Kerberos Tickets on Logon
Likewise lets you define a group policy to set target Linux and Unix
computers to obtain a Kerberos ticket when they log on the Windows NT
domain using the Kerberos authentication protocol.
This policy works with computers running Linux, Unix, or Mac OS X. The
policy, which is inherited, does not replace local policies; it merges with
them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon:
Copyright © 2007 Likewise Software. All rights reserved. 108
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Acquire Kerberos tickets on
logon (krb5_ccache_type), and then select the Define this Policy
Setting check box.
4. In the String value box, do one of the following:
To Do this
Store the Kerberos ticket in a Kerberos Type FILE
5 credentials cache
Authenticate using Kerberos without Leave the String value
keeping a ticket cache box empty.
Tip: On the target computer, you can see a list of tickets by
executing the Kerberos klist command at the shell prompt. The
command lists the location of the credentials cache, the expiration
time of each ticket, and the flags that apply to the tickets.
Allow Access to Samba Server Null-Password Accounts
You can create a group policy to allow clients to gain access to Samba
server accounts with null passwords. This policy modifies the following
file on target Samba servers: /etc/samba/smb.conf.
Warning: Enabling this policy poses significant security risks.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Allow access to Samba server
null-password accounts (null passwords), and then select the
Define this policy setting check box.
4. Select Enabled or Disabled.
Allow Cached Logons
You can create a group policy to allow target Unix and Linux computers
to use cached credentials when they cannot connect to the network or
the domain controller for authentication.
Copyright © 2007 Likewise Software. All rights reserved. 109
Product Documentation
Likewise 4.0: Administrator’s Guide
Important: If you enable this group policy, you must also enable the
group policy for Allow Offline Logon Support, which is in the
Authorization and Identification folder in the Group Policy Object Editor
console tree.
You can use this policy on computers running Unix, Linux, and Mac OS
X. The policy, which is inherited, does not replace local policies; it
merges with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon.
3. In the details pane, double-click Allow cached logons
(cached_login), and then select the Define this Policy Setting
check box.
4. Select Enabled or Disabled.
Allow Logon Rights
By using Likewise, you can create a group policy to specify the Active
Directory users and groups allowed to log onto target Unix and Linux
computers. Users and groups who have logon rights can log on the
target computers either locally or remotely. You can also use this policy
to enforce logon rules for local users and groups.
To use this policy, you must grant the users and groups access to the
Likewise cell that contains the target computer object. By default, all Unix
and Linux computers are joined to the default cell, and all members of
the Domain Users group are allowed to access the default cell.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
Copyright © 2007 Likewise Software. All rights reserved. 110
Product Documentation
Likewise 4.0: Administrator’s Guide
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon.
3. In the details pane, double-click Allow logon rights
(require_membership_of), and then select the Define this Policy
Setting check box.
4. Click and then locate the users or groups that you want to grant
logon rights.
Or, in the Users and/or Groups box, type a comma-separated list
of the users and groups that you want. In the list, you can use short
domain names with Active Directory account names and group
names. You can also use local account names and local user
groups as well as security identifiers (SIDs) in string format.
For example, you could enter the following comma-separated list:
CORP\\johndoe, root, janedoe@corp.mycorp.com,
CORP\\domain^users, S-1-1-0
In the example, the entry s-1-1-0 is a SID in string format.
5. Grant the users and groups access to the Likewise cell that contains
the target computer object.
Allow Offline Logon Support
By using Likewise, you can create a group policy to allow target Unix and
Linux computers to log onto domain accounts when the network or the
domain controller is unavailable. This setting caches logon credentials
and account information in lwiauthd.
Important: If you enable this group policy, you must also enable the
group policy for Allow Cached Logons, which is in the Logon folder in the
Group Policy Object Editor console tree.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, edit or create a group policy for the
Copyright © 2007 Likewise Software. All rights reserved. 111
Product Documentation
Likewise 4.0: Administrator’s Guide
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the tree under Computer
Configuration, expand Unix and Linux Settings, expand Likewise
Settings, and then click Authorization and Identification.
3. In the details pane, double-click Allow offline logon support
(winbind offline logon), and then select the Define this Policy
Setting check box.
4. Select Enabled or Disabled.
Copy Template Files When Creating a Home Directory
Likewise can add the contents of skel to the home directory created for
a user account on target Linux and Unix computers. Using the skel
directory ensures that all users begin with the same settings or
environment.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon.
3. In the details pane, double-click Copy template files when
creating home directory (skel), and then select the Define this
Policy Setting check box.
4. In the Path to skeleton template directory box, type the path that
you want -- for example, /etc/skel.
Create a .k5login File in a User's Home Directory
Likewise lets you define a group policy to create a .k5login file in the
home directory of a user account on target Linux and Unix computers
that log onto the Windows NT domain using the Kerberos authentication
protocol.
Copyright © 2007 Likewise Software. All rights reserved. 112
Product Documentation
Likewise 4.0: Administrator’s Guide
The .k5login file contains the user's Kerberos principal, which uniquely
identifies the user within the Kerberos authentication protocol. Kerberos
can use the .k5login file to check whether a principal is allowed to log on
as a user. A .k5login file is useful when your computers and your users
are in different Kerberos realms or different Active Directory domains,
which can occur when you use Active Directory trusts.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon.
3. In the details pane, double-click Create a .k5login file in user
home directory (create_k5login), and then select the Define this
Policy Setting check box.
4. Select Enabled or Disabled.
When enabled, Kerberos is allowed to create a .k5login file in the
home directory of a given user account. When disabled, Kerberos is
not allowed to create a .k5login file.
Create a Home Directory for a User Account at Logon
By using Likewise, you can automatically create a home directory for a
user account on target Linux and Unix computers. When the user logs on
the computer, the home directory is created if it does not exist. The
location of the home directory is specified in the Likewise settings of the
user account.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
Copyright © 2007 Likewise Software. All rights reserved. 113
Product Documentation
Likewise 4.0: Administrator’s Guide
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon.
3. In the details pane, double-click Create home directory for user
account at logon (create_homedir), and then select the Define
this Policy Setting check box.
4. Select Enabled or Disabled.
Digitally Sign Client Communications
You can create a group policy to enable, disable, or require SMB signing
when a client communicates with a server.
To help prevent session-hijacking attacks, the Server Message Block
(SMB) protocol supports mutual authentication by placing a digital
signature into each Server Message Block. The signature is then verified
by both the client and the server.
To use SMB signing, you must either offer it or require it on both the
SMB client and the SMB server. If SMB signing is offered on a server,
clients that are also enabled for SMB signing use the packet signing
protocol during all subsequent sessions. If SMB signing is required on a
server, a client cannot establish a session unless it is at least enabled for
SMB signing. To set a server to use SMB signing, see Digitally Sign
Server Communications.
This group policy adds the value that you specify to
lwiauthd_policy.conf. When this policy is undefined or disabled,
client signing is set to auto -- signing is turned on but not required,
and the client does what the server supports.
Digitally Sign Client Communications
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
Copyright © 2007 Likewise Software. All rights reserved. 114
Product Documentation
Likewise 4.0: Administrator’s Guide
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Digitally sign client
communications (client signing), and then select the Define this
policy setting check box.
4. In the drop-down list, click the option that you want. For example, to
enable signing and to make it mandatory, click signing is
mandatory.
Digitally Sign Server Communications
You can create a group policy to control whether a server offers or
requires SMB signing. This policy modifies the following file on target
Linux, Unix, and Mac OS X servers: /etc/samba/smb.conf.
To help prevent message attacks, the Server Message Block (SMB)
protocol supports mutual authentication by placing a digital signature into
each Server Message Block. The digital signature is then verified by both
the client and the server.
To use SMB signing, you must either offer it or require it on both the
SMB client and the SMB server. If SMB signing is offered on a server,
clients that are also enabled for SMB signing use the packet signing
protocol during all subsequent sessions. If SMB signing is required on a
server, a client cannot establish a session unless it is at least enabled for
SMB signing. To set clients to use SMB signing, see Digitally Sign Client
Communications.
If this policy is disabled, the server does not require the SMB client to
sign packets. The default is disabled.
Digitally Sign Server Communications
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
Copyright © 2007 Likewise Software. All rights reserved. 115
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Digitally sign server
communications (server signing), and then select the Define this
policy setting check box.
4. In the drop-down list, click the option that you want. For example, to
offer signing and to make it mandatory, click signing is required.
Log on using Kerberos Authentication
Likewise lets you define a group policy to grant target Linux and Unix
computers access to a Windows NT domain using the Kerberos
authentication protocol.
After defining this policy, you can either enable or disable it. When
enabled, users log on the Windows NT domain using Kerberos. When
disabled, NT LAN Manager (NTLM) is used instead. NTLM is a Microsoft
authentication protocol used with the SMB protocol. NTLM is also used if
Kerberos is unavailable from the domain controller.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon.
3. In the details pane, double-click Log on using Kerberos
authentication (krb5_auth), and then select the Define this Policy
Setting check box.
4. Select Enabled or Disabled.
Log Winbind Debugging Information
To monitor and troubleshoot the winbind PAM module, you can define a
Likewise group policy that logs winbind debugging information for
lwiauthd on target computers running Linux, Unix, or Mac OS X.
lwiauthd is the Likewise winbind daemon.
Copyright © 2007 Likewise Software. All rights reserved. 116
Product Documentation
Likewise 4.0: Administrator’s Guide
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon.
3. In the details pane, double-click Log debugging information
(debug), and then select the Define this Policy Setting check box.
4. Select either Enabled or Disabled.
Refresh Kerberos Tickets
By using Likewise, you can use a group policy to automatically refresh
Kerberos tickets on target Linux and Unix computers. The Kerberos
authentication protocol grants tickets to prove the identity of users in a
secure way. By automatically refreshing tickets, you can maintain a
user's domain access.
After defining this policy, you can either enable or disable it. When
enabled, lwiauthd, the Likewise winbind daemon, automatically
refreshes Kerberos tickets that are retrieved using the pam_win bind
module. When disabled, tickets are not automatically refreshed. It is
recommended that you set the policy to enabled.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
Copyright © 2007 Likewise Software. All rights reserved. 117
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Automatically refresh Kerberos
tickets (winbind refresh tickets), and then select the Define this
Policy Setting check box.
4. Select Enabled or Disabled.
Replace Spaces in Names with a Character
Likewise lets you define a group policy on target Unix and Linux
computers to replace spaces in Active Directory user and group names
with a character that you choose.
For example, when you set the replacement character to ^, the group
DOMAIN\Domain Users in Active Directory appears as
DOMAIN\domain^users on target Linux and Unix computers.
Note: The Likewise winbind daemon, lwiauthd, renders all names of
Active Directory users and groups lowercase.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
Replace Spaces in Names with a Character
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Replacement character for names
with spaces (winbind replacement character), and then select the
Define this Policy Setting check box.
4. In the Character to replace spaces in names with box, type the
character that you want -- for example, ^.
Copyright © 2007 Likewise Software. All rights reserved. 118
Product Documentation
Likewise 4.0: Administrator’s Guide
Send Encrypted Passwords to Third-Party SMB Servers
You can create a group policy to require a client to send encrypted
passwords to a third-party SMB server when the server does not accept
plain text passwords.
Important: Defining and then disabling this group policy requires the
client to send an encrypted password to the SMB server. Defining and
enabling this group policy allows the client to send a plain text password
to the SMB server -- the default setting that is in effect before you define
the group policy.
The setting that you specify is added to lwiauthd_policy.conf on
target Unix, Linux, and Mac OS X computers.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Send encrypted password to
third-party SMB servers (client plaintext auth), and then select
the Define this policy setting check box.
4. Select Enabled or Disabled.
Tip: To require the client to send an encrypted password, select
Disabled.
Set Permissions with a File Creation Mask
Likewise can set permissions for the home directory that is created when
a user logs on target Linux and Unix computers. The home directory and
all the files in the directory are preset with the ownership settings of the
file creation mask, or umask.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
Copyright © 2007 Likewise Software. All rights reserved. 119
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon.
3. In the details pane, double-click File creation mask for the
contents of the home directory (umask), and then select the
Define this Policy Setting check box.
4. Under Default File Permissions and under Default Directory
Permissions, select the options that you want.
Or, in the Umask value box, type a umask value for the permission
level that you want, and then click Set.
For example, if you specify an umask value of 022, the file
permissions are set as follows: File Owner Read and Write, Others
Read Only; Directory Owner Read and Write and Execute, others
Read and Execute.
Set the Depth of Nested Group Expansion
By using Likewise, you can define a group policy to set the level of
nested group expansion on target Unix and Linux computers. The level
of nested group expansion specifies how deep the Likewise winbind
daemon, lwiauthd, traverses the tree when it expands nested groups
into a membership list.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, edit or create a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
Copyright © 2007 Likewise Software. All rights reserved. 120
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Depth of nested group expansion
(winbind expand groups), and then select the Define this Policy
Setting check box.
4. In the Depth of group expansion box, type a number to specify
how many levels you want winbind to process when it expands
nested groups into a membership list.
For example, if you set the depth of group expansion to 0, group
expansion is in effect disabled. If you set the depth of group
expansion to 7 -- a typical setting -- winbind processes nested
groups as deep as 7 levels.
Set the ID Mapping Cache Expiration Time
Likewise lets you define a group policy to set the expiration time for the
ID mapping cache on target Linux and Unix computers. After a user or
group is mapped to its security identifier (SID) in Active Directory, the
Likewise winbind daemon, lwiauthd, caches the entry for the time that
you specify.
This policy can improve the performance of your system if, for example,
you are making a lot of changes to your ID mapping.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the tree under Computer
Configuration, expand Unix and Linux Settings, expand Likewise
Settings, and then click Authorization and Identification.
3. In the details pane, double-click ID mapping cache expiration time
(idmap expire time), and then select the Define this Policy
Setting check box.
4. In the Expiration time box, enter the time, in minutes, that you
want.
Copyright © 2007 Likewise Software. All rights reserved. 121
Product Documentation
Likewise 4.0: Administrator’s Guide
Set the ID Mapping Negative Cache Expiration Time
Likewise lets you define a group policy to specify how long the Likewise
winbind daemon, lwiauthd, caches the unmapped state for an
unsuccessful security identifier (SID) mapping of an Active Directory user
or group. This policy prevents repeated lookup requests that might
degrade the performance of your system.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click ID mapping negative cache
expiration time (idmap negative time), and then select the Define
this Policy Setting check box.
4. In the Negative cache time box, enter the time, in minutes, that you
want.
Set the Machine Account Password Expiration Time
By using Likewise, you can define a group policy to set the machine
account password's expiration time on target Unix and Linux computers.
The expiration time specifies when machine account passwords are
reset in Active Directory.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
Copyright © 2007 Likewise Software. All rights reserved. 122
Product Documentation
Likewise 4.0: Administrator’s Guide
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Machine account password
expiration time (machine password timeout), and then select the
Define this Policy Setting check box.
4. In the Expiration Time box, enter the time, in days, that you want.
Set the Maximum Tolerance for Kerberos Clock Skew
You can create a group policy to set the maximum amount of time that
the clock of the Kerberos Distribution Center (KDC) can deviate from the
clock of target hosts. For security, a host rejects responses from any
KDC whose clock is not within the maximum clock skew, as set in the
host's krb5.conf file.
The default clock skew is 300 seconds, or 5 minutes. This policy
changes the clock skew value in the krb5.conf file of target Linux,
Unix, and Mac OS X hosts.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Set the Maximum Tolerance for
Kerberos Clock Skew (clockskew), and then select the Define
this policy setting check box.
4. In the Maximum tolerance box, enter the maximum amount of time,
in minutes, to allow for the clock skew.
Set the Minimum UID-GID Value
You can define a group policy to specify the minimum UID-GID value for
target Linux, Unix, and Mac OS X computers. The lowest minimum value
that you can set is 50; the highest minimum is 9999.
Copyright © 2007 Likewise Software. All rights reserved. 123
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Minimum UID-GID Value
(lwidentity:min_id_value), and then select the Define this policy
setting check box.
4. In the Minimum Value box, enter the number that you want.
Set the Samba Hostname Resolver Cache Timeout
You can create a group policy to set Samba's hostname cache resolver
timeout on target Linux, Unix, and Mac OS X servers. The policy
specifies the number of minutes before entries in Samba's hostname
resolver cache expire. If you define the policy and set the timeout to 0,
caching is disabled.
The policy sets the time period you specify in
lwiauthd_policy.conf.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Samba server hostname resolver
cache timeout (name cache timeout), and then select the Define
this policy setting check box.
4. In the name cache timeout box, enter the minutes that you want to
set for the cache timeout.
Copyright © 2007 Likewise Software. All rights reserved. 124
Product Documentation
Likewise 4.0: Administrator’s Guide
Tip: To disable caching, enter 0.
Set the Samba Server LDAP Connection Timeout
You can create a group policy to set the time, in seconds, that a Samba
server is to wait to connect to an LDAP server before the connection
fails. This policy sets the time period in lwiauthd_policy.conf on
target Linux, Unix, and Mac OS X computers.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Samba server LDAP connection
failure timeout (ldap timeout), and then select the Define this
policy setting check box.
4. In the LDAP Timeout box, enter the seconds that you want to set
for the LDAP timeout.
Set the Winbind Cache Expiration Time
By using Likewise, you can specify how long the Likewise winbind
daemon, lwiauthd, caches information about a user's home directory,
logon shell, and the mapping between the user or group and the security
identifier (SID) on target Unix and Linux computers. Winbind features
that are using offline cached credentials reattempt to log onto the Active
Directory domain controller at the interval that you set. When online,
lwiauthd also caches the information for the specified time period.
You can use this policy to improve the performance of your system by
increasing the expiration time of the cache.
This policy works on computers running Linux, Unix, or Mac OS X. The
policy, which is inherited, does not replace local policies; it merges with
them. For more information, see About Group Policies.
Copyright © 2007 Likewise Software. All rights reserved. 125
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Winbind cache expiration time
(winbind cache time), and then select the Define this Policy
Setting check box.
4. In the Cache timeout box, enter the time, in minutes, that you want.
Show a Denied Logon Rights Message
This group policy displays a message when an Active Directory user
cannot log on a target computer because the user is not in the list of the
users or groups defined in the Allow Logon Rights
(require_membership_of) group policy.
When you set the policy, you specify the message that is displayed for
the not_a_member_error. This policy applies to computers running
Linux, Unix, and Mac OS X.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon:
Copyright © 2007 Likewise Software. All rights reserved. 126
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Denied logon rights message
(not_a_member_error), and then select the Define this policy
setting check box.
4. In the Logon error message box, type the text that you want to
display.
Show a Password Expiration Warning
This group policy sets the number of days to display a warning before a
password expires on target Linux computers. Setting the number of days
to 0 disables the warning. Without setting this policy, the default warning
time is 5 days.
This policy is only for computers running Linux.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Logon:
3. In the details pane, double-click Password expiration warning
(warn_pwd_expire), and then select the Define this policy setting
check box.
4. In the Password expiration warning box, enter the number of days
that you want.
Tip: To turn off the warning on target Linux computers, enter 0.
Turn Off Client LANMAN Authentication
You can create a group policy to disable LANMAN authentication by an
SMB client. LANMAN is an obsolete Windows authentication protocol
that was replaced by NTLM. By default, LANMAN authentication is
Copyright © 2007 Likewise Software. All rights reserved. 127
Product Documentation
Likewise 4.0: Administrator’s Guide
enabled, which might pose a security threat because of LANMAN's weak
encryption.
This policy modifies lwiauthd_policy.conf on target Linux, Unix,
and Mac OS X clients.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Turn off client LANMAN
authentication (client lanman auth), and then select the Define
this policy setting check box.
4. Select Enabled or Disabled.
Note: If you disable LANMAN authentication, only servers that
support NT password hashes will accept an SMB client's
connection. For example, if the client's LANMAN authentication is
disabled, the client cannot connect to Windows 95 or Windows 98
servers.
Turn On Client NTLMv2 Authentication
You can create a group policy to enable client NTLMv2 authentication.
NTLM is a Microsoft challenge-response authentication protocol that is
used with the SMB protocol. NTLMv2 is cryptographically stronger than
NTLMv1. Without setting this group policy, the default is to not use
NTLMv2.
This policy modifies lwiauthd_policy.conf on target Linux, Unix,
and Mac OS X clients.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
Copyright © 2007 Likewise Software. All rights reserved. 128
Product Documentation
Likewise 4.0: Administrator’s Guide
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Likewise Settings, and then click Authorization and
Identification.
3. In the details pane, double-click Turn on client NTLMv2
authentication (client ntlmv2 auth), and then select the Define
this policy setting check box.
4. Select either Enabled or Disabled, with the following results:
Policy Setting Authentication Authentication
Used Disabled
Enabled NTLMv2 or LMv2 NTLMv1,
LANMAN, plain
text (share-level
authentication is
disabled)
Disabled NTLMv1 or NTLMv2, LMv2
LANMAN
Note: Some servers might allow only an NTLMv2 response, not an
LMv2 response.
Logging and Auditing Settings
Create a SysLog Policy
By using Likewise, you can create a syslog group policy for target Unix
and Linux computers. A syslog policy can help you manage,
troubleshoot, and audit your systems.
Likewise provides a graphical user interface to configure and customize
your syslog policies. You can log different facilities, such as cron,
daemon, and auth, and you can use priority levels and filters to collect
messages.
This policy works with computers running Linux, Unix, or Mac OS X. The
policy replaces the local policies. It is not inherited and does not merge
with the local settings. For more information, see About Group Policies.
Copyright © 2007 Likewise Software. All rights reserved. 129
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Logging and Audit Settings, and then click SysLog:
3. In the details pane, double-click SysLog, and then select the Define
this Policy Setting check box.
4. Click Add.
5. In the Syslog Policy Editor, in the Destination Type list, click the
destination for the syslog.
6. The box below the Destination Type list changes depending on the
destination type that you select:
For a Destination Type of Do this
File Enter the path to the file.
Named Pipe Enter the path and name of the
pipe file.
Remote Host Enter the IP address or the
server name of the remote host.
Local Users Enter a comma-separated list of
email addresses.
All Users The box is unavailable.
Copyright © 2007 Likewise Software. All rights reserved. 130
Product Documentation
Likewise 4.0: Administrator’s Guide
7. Click in the Facilities box and then click to select the facilities
that you want to log.
8. Select the facilities that you want. You can select All, or you can
select Selected Items, and then select the check boxes for the
facilities that you want in the list.
To enter a custom list of facilities, select Custom Entry, and then
type a comma-separated list of the facilities that you want to use --
for example: cron, daemon, auth, kern
9. In the list under Priorities, click the priority level for which you want
to log events.
10. In the list under Filter, click the filter that you want to apply to the
priority level, and then click OK.
Tip: To change a log's options later, click a log in the list, and then
click Edit.
Rotate Logs
To help you manage, troubleshoot, and archive your system's log files,
you can create a group policy to configure and customize your log-
rotation daemon. For example, you can choose to use either a
logrotate or logrotate.d file, specify the maximum size before
rotation, compress old log files, and set an address for emailing log files
and error messages. You can also enter commands to run before and
after rotation.
This policy works with computers running Linux, Unix, or Mac OS X. The
policy replaces the local policies. It is not inherited and does not merge
with the local settings. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Logging and Audit Settings, and then click LogRotate.
Copyright © 2007 Likewise Software. All rights reserved. 131
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Rotate logs, and then select the
Define this Policy Setting check box.
4. Click Add.
5. In the Log Rotate Policy Editor, under the General Options tab, set
the options that you want.
6. Click the Log Options tab, and then set the options that you want.
7. Click the Mail/Script Options tab, and then set the options that you
want.
Secure Computers with an AppArmor Policy
By using Likewise, you can create an AppArmor group policy to help
secure target computers that are running SUSE Linux Enterprise.
AppArmor is a Linux Security Module implementation of name-based
access controls. To help protect your operating system and applications
from threats, AppArmor uses security policies, called profiles, that define
the system resources and privileges that an application can use.
Copyright © 2007 Likewise Software. All rights reserved. 132
Product Documentation
Likewise 4.0: Administrator’s Guide
AppArmor is included with all SUSE distributions from SUSE Linux
Enterprise Server 9, Service Pack 3 (SLES9 SP3) and later, including
SLES10, SLED10, and openSUSE 10.0, 10.1, and 10.2.
Note: To configure this policy, you must have a file containing an
AppArmor security profile. The SUSE Linux distribution contains default
profiles that you can use. It also contains tools to build your own profiles.
For information on how to obtain or create a security profile, see the
AppArmor documentation.
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
Secure Computers with an AppArmor Policy
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Logging and Audit Settings, and then click AppArmor.
3. In the details pane, double-click AppArmor, and then select the
Define this Policy Setting check box.
4. Click Add, find the security profile that you want to use, and then
click Open.
5. In the list under Profile Mode, do one of the following:
To Click
Log events that would have been complain
denied if the profile were set to
enforce
Enforce the polices defined by enforce
the security profile
Secure Computers with an SELinux Policy
With Likewise, you can create a Security-Enhanced Linux group policy to
help secure target computers running Red Hat Enterprise Linux.
Copyright © 2007 Likewise Software. All rights reserved. 133
Product Documentation
Likewise 4.0: Administrator’s Guide
Security-Enhanced Linux, or SELinux, puts in place mandatory access
control by using the Linux Security Modules, or LSM, in the Linux kernel.
The security architecture, which is based on the principle of least
privilege, provides fine-grained control over the users and processes that
are allowed to access a system or execute commands on it.
SELinux can secure processes from each other. For example, if you
have a public web server that is also acting as a DNS server, SELinux
can isolate the two processes so that a vulnerability in the web server
process does not expose access to the DNS server.
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
Note: This policy applies the settings that you define in the procedure
below to the /etc/sysconfig/selinux file on target computers
running Red Hat Enterprise Linux. The /etc/sysconfig/selinux file
is the primary configuration file for enabling or disabling SELinux and for
setting which policy to enforce on the system and how to enforce it.
Secure Computers with an SELinux Policy
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Logging and Audit Settings, and then click SELinux.
3. In the details pane, double-click SELinux, and then select the
Define this policy setting check box.
4. In the SE Linux list, do one of the following:
To define the top-level state of Click
SELinux on the target
computers as
enforcing mode -- meaning that enforcing
the SELinux security policy is
enforced
permissive mode -- meaning that permissive
SELinux prints warnings but
Copyright © 2007 Likewise Software. All rights reserved. 134
Product Documentation
Likewise 4.0: Administrator’s Guide
does not enforce policy. You can
use this setting for debugging
and troubleshooting.
In permissive mode, more
denials are logged, as subjects
can continue to execute actions
that are denied in enforcing
mode.
For example, traversing a
directory tree generates multiple
avc: denied messages for
every directory level read. In
enforcing mode, a kernel would
have stopped the initial traversal
and not generated further denial
messages.
disabled mode -- meaning that disabled
SELinux is fully disabled.
SELinux hooks are disengaged
from the kernel and the pseudo-
file system is unregistered.
5. In the SE Linux Type list, click either targeted or strict.
Selecting targeted protects only targeted network daemons. The
default targeted policy protects the following daemons on Red Hat
Enterprise Linux 4: dhcpd, httpd (apache.te), named, nscd,
ntpd, portmap, snmpd, squid, and syslogd. The rest of the
system runs in the unconfined_t domain. The policy files for
these daemons are in
/etc/selinux/targeted/src/policy/domains/program
and might vary depending on the version of Red Hat Enterprise
Linux that you are using.
Selecting strict provides full SELinux protection for all daemons.
The system defines security contexts for all objects and subjects,
and the policy enforcement server processes every action.
Copyright © 2007 Likewise Software. All rights reserved. 135
Product Documentation
Likewise 4.0: Administrator’s Guide
Message Settings
Display a Message of the Day
By using Likewise, you can use a group policy to set a message of the
day in the /etc/motd file on target Linux and Unix computers.
The message of the day, which appears after a user logs in but before
the logon script executes, can give users information about a computer.
For example, the message can remind users of the next scheduled
maintenance window.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy replaces the motd file on the target computer.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Message Settings, and then click Message of the Day:
3. In the details pane, double-click Message of the day (/etc/motd),
select the Define this Policy Setting check box, and then in the
Text Value box, type your message.
Tip: Limit the size of your message to one screen.
Display a Message with a Login Prompt Policy
By using Likewise, you can use a group policy to set a message in the
/etc/issue file on target Linux and Unix computers. The message,
which appears before the login prompt, can display the name of the
operating system, the kernel version, and other information that identifies
the system.
Copyright © 2007 Likewise Software. All rights reserved. 136
Product Documentation
Likewise 4.0: Administrator’s Guide
In the message text, you can use characters, numbers, and special
characters; there is no limit to the length of the message.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy replaces the /etc/issue file on target computers.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Message Settings, and then click Login Prompt.
3. In the details pane, double-click Login Prompt (/etc/issue), select
the Define this Policy Setting check box, and then in the Text
Value box, type your message.
In your message, you can use escape codes that getty (on Unix) or
agetty (on Linux) recognizes. For example, if you write Welcome to
\s \r \l, on a Linux computer, agetty replaces \s with the name
of the operating system, \r with the kernel version, and \l with the
name of the terminal device. For a list of escape codes, see the
getty or agetty man pages for your system.
Message Settings
Display a Message of the Day
By using Likewise, you can use a group policy to set a message of the
day in the /etc/motd file on target Linux and Unix computers.
The message of the day, which appears after a user logs in but before
the logon script executes, can give users information about a computer.
For example, the message can remind users of the next scheduled
maintenance window.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy replaces the motd file on the target computer.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
Copyright © 2007 Likewise Software. All rights reserved. 137
Product Documentation
Likewise 4.0: Administrator’s Guide
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Message Settings, and then click Message of the Day:
3. In the details pane, double-click Message of the day (/etc/motd),
select the Define this Policy Setting check box, and then in the
Text Value box, type your message.
Tip: Limit the size of your message to one screen.
Display a Message with a Login Prompt Policy
By using Likewise, you can use a group policy to set a message in the
/etc/issue file on target Linux and Unix computers. The message,
which appears before the login prompt, can display the name of the
operating system, the kernel version, and other information that identifies
the system.
In the message text, you can use characters, numbers, and special
characters; there is no limit to the length of the message.
You can use this policy on computers running Linux, Unix, or Mac OS X.
The policy replaces the /etc/issue file on target computers.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Message Settings, and then click Login Prompt.
3. In the details pane, double-click Login Prompt (/etc/issue), select
the Define this Policy Setting check box, and then in the Text
Value box, type your message.
Copyright © 2007 Likewise Software. All rights reserved. 138
Product Documentation
Likewise 4.0: Administrator’s Guide
In your message, you can use escape codes that getty (on Unix) or
agetty (on Linux) recognizes. For example, if you write Welcome to
\s \r \l, on a Linux computer, agetty replaces \s with the name
of the operating system, \r with the kernel version, and \l with the
name of the terminal device. For a list of escape codes, see the
getty or agetty man pages for your system.
Security Settings
Define a Sudo Policy
By using Likewise, you can use a group policy to specify a sudo
configuration file for target computer running Linux, Unix, and Mac OS X.
The sudo configuration file is copied to the local machine and replaces
the local sudoers file. A sudo file can reference local users and groups
or Active Directory users and groups.
Sudo, or superuser do, allows a user to run a command as root or as
another user. For more information about sudo, see the man pages for
your system.
This policy is not inherited and does not merge with the local file. For
more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Security Settings, and then click SUDO command:
Copyright © 2007 Likewise Software. All rights reserved. 139
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Define Sudoer file, select the
Define this Policy Setting check box, and then in the Current file
content box, type your commands.
Or, to import a sudo configuration file, click Import, and then find the
file that you want.
Note: The sudoers file must follow the format described in the
sudoers man page and it must have Unix-style line endings. If the
line endings are DOS-style, use dos2unix to convert them.
Require Complex Passwords
By using Likewise, you can define a group policy on target Linux
computers that requires user account passwords to meet complexity
requirements. This policy can help improve the security of your
computers.
When enabled, passwords must meet the following minimum
requirements:
• Not contain the user's account name or parts of the user's full name
that exceed two consecutive characters.
• Be at least six characters in length.
• Contain characters from three of these four categories:
• English uppercase characters (A through Z)
• English lowercase characters (a through z)
• Base 10 digits (0 through 9)
• Non-alphabetic characters (for example, !, $, #, %)
Complexity requirements are enforced when passwords are created or
changed.
You can use this policy only on computers running Linux. The policy,
which is inherited, does not replace local policies; it merges with them.
For more information, see About Group Policies.
Require Complex Passwords
Copyright © 2007 Likewise Software. All rights reserved. 140
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Security Settings, and then click Password Policy.
3. In the details pane, double-click Password must meet complexity
requirements, and then select the Define this Policy Setting
check box.
4. Select Enabled or Disabled.
Set the Maximum Password Age
By using Likewise, you can define a group policy for target local system
accounts on Linux computers to set the maximum number of days that a
password can be used before it must be changed.
You can set passwords to expire after 1 to 999 days, or you can specify
that passwords never expire by setting the number of days to 0.
If the maximum password age is between 1 and 999 days, the minimum
password age, as set in the minimum password age group policy, must
be less than the maximum password age. If the maximum password age
is set to 0, the minimum password age can be any value between 0 and
998 days.
You can use this policy only on computers running Linux. The policy,
which is inherited, does not replace local policies; it merges with them.
For more information, see About Group Policies.
Set the Maximum Password Age
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Security Settings, and then click Password Policy.
Copyright © 2007 Likewise Software. All rights reserved. 141
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Maximum password age, and then
select the Define this Policy Setting check box.
4. In the Expires after box, enter the number of days that you want.
Set the Minimum Password Age
By using Likewise, you can define a group policy for target local system
accounts on Linux computers to set the minimum number of days that a
password can be used before it must be changed.
You can set a value between 1 and 998 days, or you can allow users to
change their passwords immediately by setting the number of days to 0.
The minimum password age must be less than the maximum password
age, as specified in the maximum password age group policy, unless the
maximum password age is set to 0. If the maximum password age is set
to 0, the minimum password age can be set to any value between 0 and
998.
You can use this policy only on computers running Linux. The policy,
which is inherited, does not replace local policies; it merges with them.
For more information, see About Group Policies.
Set the Minimum Password Age
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Security Settings, and then click Password Policy.
3. In the details pane, double-click Minimum password age, and then
select the Define this Policy Setting check box.
4. In the Can change after box, enter the number of days that you
want.
Set the Minimum Password Length
By using Likewise, you can define a group policy that specifies the
minimum number of characters for a user account password on target
Copyright © 2007 Likewise Software. All rights reserved. 142
Product Documentation
Likewise 4.0: Administrator’s Guide
Linux computers. This policy can help improve security on your
computers.
You can set a value of between 1 and 14 characters. If you set the
number of characters to 0, a password is not required.
Linux distributions that require a 5-character password will continue to
enforce this minimum length. The enforcement of this policy might
depend on the Linux distribution that you are using.
You can use this policy only on computers running Linux. The policy,
which is inherited, does not replace local policies; it merges with them.
For more information, see About Group Policies.
Set the Minimum Password Length
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Security Settings, and then click Password Policy.
3. In the details pane, double-click Minimum password length, and
then select the Define this Policy Setting check box.
4. In the Minimum length box, enter a number from 0 to 14.
Task Settings
Run a Script File
Likewise lets you use a group policy to execute a text-based script file on
target Linux and Unix computers.
The script file runs under the root account when the target computer first
receives the group policy object or when the policy object's version
changes. When a target system is rebooted, the script runs again.
This policy replaces the local file. It is not inherited and does not merge
with the local file. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
Copyright © 2007 Likewise Software. All rights reserved. 143
Product Documentation
Likewise 4.0: Administrator’s Guide
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Task Settings, and then click Run Script:
3. In the details pane, double-click Script file, and then select the
Define this Policy Setting check box.
4. In the Current file content box, type your script. Example:
#!/bin/bash
echo "`date` Running AD Script 1 ($0)" >> /tmp/AD_GPO.log
Or, click Import, find the file that contains your script, and then
click Open.
Schedule Cron Jobs with a crontab or cron.d Policy
By using Likewise, you can use a group policy to schedule commands,
or cron jobs, that are executed at a set time on target Linux and Unix
computers.
When you set this policy, you must select a file type of /etc/cron.d or
crontab. You can use cron.d only on Linux computers; crontab
works on computers running Linux or Unix, including Mac OS X.
Using crontab overwrites the crontab file on target computers. Using
cron.d adds your file to the /etc/cron.d directory on target Linux
computers.
Copyright © 2007 Likewise Software. All rights reserved. 144
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Task Settings, and then click Crontab/Cron.d.
3. In the details pane, double-click Crontab Settings, and then select
the Define this Policy Setting check box.
4. To specify the crontab file type, click Change Type, select either
/etc/cron.d or crontab, and then click OK.
Selecting /etc/cron.d -- which is not supported by the Sun Solaris,
Mac OS X, or IBM AIX operating systems -- adds the file to the
/etc/cron.d directory while preserving existing files and other
files inherited from policy objects.
Selecting crontab -- which works with most systems, including
Solaris, AIX, and Mac OS X -- uses the crontab utility to install the
file in the root account, overriding the account's existing crontab
settings and any files inherited from policy objects.
5. In the Current file content box, type your command. Example:
* * * * * echo "`date` Running Cronjob 1 ($0) " >>
/tmp/AD_GPO.log
Or, click Import, find the file that contains your commands, and
then click Open.
Copyright © 2007 Likewise Software. All rights reserved. 145
Product Documentation
Likewise 4.0: Administrator’s Guide
Mac System Preferences
Allow Bluetooth Devices to Find the Computer
You can create a group policy to make target Mac OS X computers
discoverable by Bluetooth devices.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences:
3. In the details pane, double-click Allow other Bluetooth devices to
discover the computer, and then select the Define this policy
setting check box.
4. Select Enabled or Disabled. When Enabled is selected, Bluetooth
is discoverable; when Disabled is selected, Bluetooth is not
discoverable.
Note: If you disable this policy, Bluetooth devices can still connect to
target computers.
Allow Bluetooth Devices to Wake the Computer
You can create a group policy to set the system preferences to allow
Bluetooth devices to wake target Mac OS X computers. This policy
allows a user who has a Bluetooth keyboard or mouse to press a key or
click the mouse to wake a sleeping computer.
Copyright © 2007 Likewise Software. All rights reserved. 146
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Allow Bluetooth devices to wake
the computer, and then select the Define this policy setting check
box.
4. Select Enabled or Disabled. When Enabled is selected, a
Bluetooth device is allowed to wake the computer.
Block UDP Traffic on a Mac
By using Likewise, you can create a group policy to set the built-in
firewall on target computers running Mac OS X to block UDP traffic.
Blocking User Datagram Protocol traffic can help secure target
computers.
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Block UDP traffic usage, and then
select the Define this Policy Setting check box.
4. Select Enabled or Disabled.
Copyright © 2007 Likewise Software. All rights reserved. 147
Product Documentation
Likewise 4.0: Administrator’s Guide
Disable Automatic User Login on a Mac
By using Likewise, you can create a group policy to disable automatic
login on target computers running Mac OS X. This policy requires a user
to log on every time the computer is turned on or restarted.
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Disable automatic user login, and
then select the Define this Policy Setting check box.
4. Select Enabled or Disabled.
Log Firewall Activity on a Mac
By using Likewise, you can create a group policy to log firewall activity
on target computers running Mac OS X Tiger or later.
To help you monitor and audit Mac computers for security issues, this
policy turns on firewall logging, which keeps a log of such events as
blocked attempts, blocked sources, and blocked destinations.
The log is at /var/log/ipfw.log. Mac OS X resets and archives the
log file every 7 days. An archived log file is deleted after about 30 days.
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
Copyright © 2007 Likewise Software. All rights reserved. 148
Product Documentation
Likewise 4.0: Administrator’s Guide
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Turn on firewall logging, and then
select the Define this Policy Setting check box.
4. Select Enabled or Disabled.
Secure System Preferences on a Mac
By using Likewise, you can create a group policy to lock system
preferences on target computers running Mac OS X so that only
administrators with the password can change the preferences.
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Secure system preferences with
password, and then select the Define this Policy Setting check
box.
4. Select Enabled or Disabled.
Set DNS Servers and Search Domains on a Mac
You can create a group policy to specify the DNS servers and search
domains on target Mac OS X computers.
The search domains are automatically appended to names that are
typed in Internet applications. For example, if you set
campus.college.edu as a search domain, a user can type server1 in
the Finder’s Connect To Server dialog to connect to
server1.campus.college.edu.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
Copyright © 2007 Likewise Software. All rights reserved. 149
Product Documentation
Likewise 4.0: Administrator’s Guide
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click DNS Settings, and then select the
Define this policy setting check box.
4. In the DNS Servers box, type the DNS address that you want to
use. To enter more than one address, you must put each additional
address on a new line.
5. In the Search Domains box, optionally type the search domain that
you want.
To enter multiple search domains, separate each by a comma.
Domains are searched in the order you list them. To include local
as one of the search domains, the target computers must be running
OS X 10.4 or later and local must be first. Example:
local, likewisesoftware.com, campus.college.edu
Tip: To stop a local user from changing a Mac OS X computer's network
settings, see Secure System Preferences on a Mac.
Show Bluetooth Status in the Menu Bar
You can create a group policy to set the system preferences to show the
Bluetooth status in the menu bar of a target Mac OS X computer. When
enabled, the policy displays a Bluetooth status icon in the menu bar. The
icon shows one of the following Bluetooth statuses:
Icon Description
Bluetooth is turned on but no devices are communicating
with it.
A Bluetooth adapter is connected to the computer but
turned off.
Copyright © 2007 Likewise Software. All rights reserved. 150
Product Documentation
Likewise 4.0: Administrator’s Guide
Bluetooth is turned on and a Bluetooth device is
communicating with the computer.
No Bluetooth device is connected to the computer.
The battery on a connected Bluetooth device is low.
Show Bluetooth Status in the Menu Bar
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Show Bluetooth status in the
menu bar, and then select the Define this policy setting check
box.
4. Select Enabled or Disabled.
Turn Bluetooth On or Off
You can create a group policy to turn on or turn off Bluetooth power on
target Mac OS X computers. When Bluetooth power is turned off, other
Bluetooth devices, such as wireless keyboards and mobile phones,
cannot connect to the computer.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
Copyright © 2007 Likewise Software. All rights reserved. 151
Product Documentation
Likewise 4.0: Administrator’s Guide
3. In the details pane, double-click Turn Bluetooth on or off, and then
select the Define this policy setting check box.
4. Select Enabled or Disabled. When Enabled is selected, Bluetooth
is on; when Disabled is selected, Bluetooth is off.
Turn On AppleTalk
You can create a group policy to make AppleTalk active on target Mac
OS X computers. You can also use this policy to make AppleTalk
inactive.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organizational unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Make AppleTalk active, and then
select the Define this policy setting check box.
4. In the list under Configure, click the option that you want. When
Automatically is selected, AppleTalk is active. When Manually is
selected, you must enter the Node ID and the Network ID.
Tip: To stop a local user from changing a Mac OS X computer's
AppleTalk settings, see Secure System Preferences on a Mac.
Use Firewall Stealth Mode on a Mac
By using Likewise, you can create a group policy to set the built-in
firewall on target computers running Mac OS X to operate in stealth
mode.
Stealth mode cloaks the target computer behind its firewall: Uninvited
traffic gets no response, and other computers that send traffic to the
target computer get no information about it. Stealth mode can help
protect the target computer's security.
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
Copyright © 2007 Likewise Software. All rights reserved. 152
Product Documentation
Likewise 4.0: Administrator’s Guide
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Use firewall stealth mode, and
then select the Define this Policy Setting check box.
4. Select Enabled or Disabled.
Use Secure Virtual Memory on a Mac
By using Likewise, you can create a group policy to configure target
computers running Mac OS X to store application data in secure virtual
memory.
In case the computer's hard drive is accessed without authorization, this
policy sets the target Mac to encrypt the data that it stores in virtual
memory.
This policy, which is inherited, does not replace local policies; it merges
with them. For more information, see About Group Policies.
1. In Active Directory Users and Computers or in the Group Policy
Management Console, create or edit a group policy for the
organization unit that you want, and then open it with the Group
Policy Object Editor.
2. In the Group Policy Object Editor, in the console tree under
Computer Configuration, expand Unix and Linux Settings,
expand Macintosh Settings, and then click Macintosh System
Preferences.
3. In the details pane, double-click Use secure virtual memory, and
then select the Define this Policy Setting check box.
4. Select Enabled or Disabled.
Copyright © 2007 Likewise Software. All rights reserved. 153
Product Documentation
Likewise 4.0: Administrator’s Guide
Single Sign-On
Single Sign On
About Single Sign-On
Likewise provides more than just system access. It provides network-
wide single sign-on.
In addition to authenticating and authorizing users for system access,
Likewise initializes and maintains Kerberos ticket granting for all Active
Directory user sessions on a Linux or Unix system. Once initialized, a
user can perform AD-authenticated single sign-on activities, including the
following:
• SSH, rlogin, rsh, telnet, and FTP
• Firefox browsing of intranet sites
• LDAP queries against Active Directory
With a valid user Kerberos Ticket Granting Ticket (TGT), the underlying
Generic Security Services (GSS) system will request a Kerberos service
ticket for Kerberos-enabled service.
FTP
You will need both a GSS-enabled FTP daemon and client. This is part
of the krb5-workstation package. Once installed, you can enable the
daemon by editing the disable line in /etc/xinet.d/gssftp to no
and enabling the xinetd super server service:
Example from Red Hat or Fedora Core:
# default: off
# description: The kerberized FTP server accepts FTP
connections \
# that can be authenticated with Kerberos 5.
service ftp
Copyright © 2007 Likewise Software. All rights reserved. 154
Product Documentation
Likewise 4.0: Administrator’s Guide
flags = REUSE
socket_type = stream
wait = no
user = root
server = /usr/kerberos/sbin/ftpd
server_args = -l -a
log_on_failure += USERID
disable = no
Example of an FTP single sign-on:
[johnyu@juser-linux ~]$ ftp juser-linux.corp.company.com
Connected to juser-linux.corp.company.com.
220 juserr-linux FTP server (Version 5.60) ready.
334 Using authentication type GSSAPI; ADAT must follow
GSSAPI accepted as authentication type
GSSAPI authentication succeeded
Copyright © 2007 Likewise Software. All rights reserved. 155
Product Documentation
Likewise 4.0: Administrator’s Guide
Name (juser-linux.corp.compay.com:johnyu):
232 GSSAPI user jgeer@CORP.COMPANY.COM is authorized
as johnyu
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
Logging In and Verifying Kerberos Tickets
To obtain a valid ticket through Likewise, log on through a PAM entry
point such as a non-single sign-on SSH (secure shell) login, the Unix
console, or the X11 display manager (XDM).
Example from Red Hat or Fedora Core:
login as: juser@corp.company.com
juser@corp.company.com@jgeer-linux.corp.centeris.com's
password:
Last login: Mon Jul 2 13:22:25 2007 from localhost.localdomain
$ klist
Ticket cache: FILE:/tmp/krb5cc_100013
Default principal: juser@CORP.COMPANY.COM
Copyright © 2007 Likewise Software. All rights reserved. 156
Product Documentation
Likewise 4.0: Administrator’s Guide
Valid starting Expires Service principal
07/02/07 13:26:24 07/02/07 23:26:44
krbtgt/CORP.COMPANY.COM@CORP.COMPANY.COM
renew until 07/09/07 13:26:24
07/02/07 13:26:44 07/02/07 23:26:44 JUSER-
LINUX$@CORP.COMPANY.COM
renew until 07/09/07 13:26:24
Perform an Authenticated LDAP Search
Example from Red Hat or Fedora Core system:
$ klist
$ ldapsearch -H ldap://corp.centeris.com -Y GSSAPI -b
"OU=PM,OU=Bellevue,DC=corp,DC=centeris,DC=com"
"givenName=John"
SASL/GSSAPI authentication started
SASL username: juser@CORP.COMPANY.COM
SASL SSF: 56
SASL installing layers
# extended LDIF
# LDAPv3
# base <OU=PM,OU=Bellevue,DC=corp,DC=company,DC=com>
with scope subtree
# filter: givenName=John
# requesting: ALL
Copyright © 2007 Likewise Software. All rights reserved. 157
Product Documentation
Likewise 4.0: Administrator’s Guide
# John Y. User, PM, Bellevue, corp.company.com
dn: CN=John Y.
User,OU=PM,OU=Bellevue,DC=corp,DC=company,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: John Y. User
sn: User
givenName: John
initials: Y
distinguishedName: CN=John Y.
User,OU=PM,OU=Bellevue,DC=corp,DC=company,DC=co
instanceType: 4
whenCreated: 20050518173419.0Z
whenChanged: 20070701110111.0Z
displayName: John Y. User
uSNCreated: 2573986
memberOf:
CN=VMAdmins,OU=Engineering,DC=corp,DC=company,DC=com
uSNChanged: 6052558
name: John Y. User
Copyright © 2007 Likewise Software. All rights reserved. 158
Product Documentation
Likewise 4.0: Administrator’s Guide
objectGUID:: 7OcUg0HERUusL/Idoy8ucQ==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 128276130965468750
lastLogoff: 0
lastLogon: 128278818847812500
pwdLastSet: 127610791087187500
primaryGroupID: 513
userParameters::
bTogICAgICAgICAgICAgICAgICAgIGQJICAgICAgICAgICAgICAgIC
AgICAgI
CAg
objectSid:: AQUAAAAAAAUVAAAABmrrGFq7/kaof0eDlgUAAA==
adminCount: 1
accountExpires: 9223372036854775807
logonCount: 14398
sAMAccountName: JUser
sAMAccountType: 805306368
userPrincipalName: JUser@corp.company.com
objectCategory:
CN=Person,CN=Schema,CN=Configuration,DC=corp,DC=company
,DC=co
Copyright © 2007 Likewise Software. All rights reserved. 159
Product Documentation
Likewise 4.0: Administrator’s Guide
mSMQSignCertificates::
AgAAABHOOeQnCg3L80Fg7RL8GRRpRZm2oF8nSZGxsDEjgMFm
vQEAADC
CAbkwggFjoAMCAQICBKqlWlUwDAYIKoZIhvcNAgUFADBkMREw
DwYDVQQHHggATQBTAE0AUTELMAkG
A1UECh4CAC0xCzAJBgNVBAseAgAtMTUwMwYDVQQDHiwAQw
BPAFIAUABcAEoARwBlAGUAcgAsACAAa
gBnAGUAZQByAC0AdgBhAGkAbzAeFw0wNTA3MDEyMTAwNTR
aFw0xMzA3MDEyMTAwNTRaMGQxETAPBg
NVBAceCABNAFMATQBRMQswCQYDVQQKHgIALTELMAkGA1U
ECx4CAC0xNTAzBgNVBAMeLABDAE8AUgB
QAFwASgBHAGUAZQByACwAIABqAGcAZQBlAHIALQB2AGEAa
QBvMFwwDQYJKoZIhvcNAQEBBQADSwAw
SAJBALj8sXCwD6vuPTc8A1sY+tFyGL7JF3iNb85wnEENElgNHHr
cvbjYGRF4sPoALHK/HScf7z6a8
WABkMeRidMeJ7UCAwEAATANBgkqhkiG9w0BAQQFAANBAIvb
TV516CP9gRVp6HnSh6httGO14HXNJL
IVi3NiaZ/GFVppqzVSBxcFvmGHaVz9BkBOOfjUscK7s92zuUjBQH
TlqiFDUhLcZ5VxWB0zIZB6hFr
j2RU7J0GcBdShUuCbLrUBAAAwggGxMIIBW6ADAgECAgSqpVp
VMAwGCCqGSIb3DQIFBQAwYDERMA8G
A1UEBx4IAE0AUwBNAFExCzAJBgNVBAoeAgAtMQswCQYDVQQ
LHgIALTExMC8GA1UEAx4oAEMATwBSA
FAAXABKAEcAZQBlAHIALAAgAGoAZwBlAGUAcgAtAGgAcDAe
Fw0wNTA4MTgxODEzMjlaFw0xMzA4MT
gxODEzMjlaMGAxETAPBgNVBAceCABNAFMATQBRMQswCQYD
VQQKHgIALTELMAkGA1UECx4CAC0xMTA
vBgNVBAMeKABDAE8AUgBQAFwASgBHAGUAZQByACwAIABq
Copyright © 2007 Likewise Software. All rights reserved. 160
Product Documentation
Likewise 4.0: Administrator’s Guide
AGcAZQBlAHIALQBoAHAwXDANBgkqhkiG
9w0BAQEFAANLADBIAkEAsU+XJ59U0CwIaRUJGCsntjM+vaqr7J/
e5zcbTL4EscZug5NlnA7LouRvm
ZmqXc+EWb9MjISnmvsj4m4tX0QIFQIDAQABMA0GCSqGSIb3DQ
EBBAUAA0EAfFhp9jo8hGw3aQAccT
1KwqPa6VWDNrLUJIBYNn2fQWKLmNDb/N74/bpHbYNVGn0WXst
o0IJ8b8KHNAK4RvM4yQ==
mSMQDigests:: 5aohQ1IS3GeVcVgdMyGQeg==
mSMQDigests:: Ec455CcKDcvzQWDtEvwZFA==
msNPAllowDialin: TRUE
lastLogonTimestamp: 128277612716718750
# search result
search: 4
result: 0 Success
# numResponses: 2
# numEntries: 1
rlogin
You will need both a GSS-enabled telnet daemon and client. This is part
of the krb5-workstation package. Once installed, you can enable the
daemon by editing the “disable” line in /etc/xinet.d/krb5-telnet
to no and enabling the xinetd super server service:
Example from Red Hat or Fedora Core:
# default: off
# description: The kerberized rlogin server accepts BSD-style
rlogin sessions, \
Copyright © 2007 Likewise Software. All rights reserved. 161
Product Documentation
Likewise 4.0: Administrator’s Guide
# but uses Kerberos 5 authentication.
service klogin
flags = REUSE
socket_type = stream
wait = no
user = root
server = /usr/kerberos/sbin/klogind
server_args = -5
disable = no
Example of rlogin single sign-on:
[johnyu@juser-linux ~]$ rlogin juser-linux.corp.company.com
Last login: Mon Jul 2 19:00:59 from juser-linux
[johnyu@juser-linux ~]$
rsh
You will need both a GSS-enabled rsh daemon and client. This is part of
the krb5-workstation package. Once installed, you can enable the
daemon by editing the disable line in /etc/xinet.d/kshell to no
and enabling the xinetd super server service:
Example from Red Hat or Fedora Core:
# default: off
# description: The kerberized rshell server accepts rshell
Copyright © 2007 Likewise Software. All rights reserved. 162
Product Documentation
Likewise 4.0: Administrator’s Guide
commands \
# authenticated and encrypted with Kerberos 5.
service kshell
flags = REUSE
socket_type = stream
wait = no
user = root
server = /usr/kerberos/sbin/kshd
server_args = -e -5
disable = no
Example of rsh single sign-on:
[johnyu@juser-linux ~]$ rsh juser-linux.corp.company.com
Last login: Mon Jul 2 18:53:21 from juser-linux
[johnyu@juser-linux ~]$ id
Telnet
You will need both a GSS-enabled telnet daemon and client. This is part
of the krb5-workstation package. Once installed, you can enable the
daemon by editing the disable line in /etc/xinet.d/krb5-telnet
to no and enabling the xinetd super server service:
Example from Red Hat or Fedora Core:
# default: off
# description: The kerberized FTP server accepts FTP
Copyright © 2007 Likewise Software. All rights reserved. 163
Product Documentation
Likewise 4.0: Administrator’s Guide
connections \
# that can be authenticated with Kerberos 5.
service ftp
flags = REUSE
socket_type = stream
wait = no
user = root
server = /usr/kerberos/sbin/ftpd
server_args = -l -a
log_on_failure += USERID
disable = no
Example of telnet sngle sign-on:
[johnyu@juser-linux ~]$ telnet -a juser-linux.corp.company.com
Trying 127.0.0.2...
Connected to juser-linux.corp.company.com (127.0.0.2).
Escape character is '^]'.
[ Kerberos V5 accepts you as ``juser@CORP.COMPANY.COM'' ]
Last login: Mon Jul 2 18:36:39 from localhost.localdomain
[johnyu@juser-linux ~]$ id
uid=100013(johnyu) gid=100000(CORP\domain^users)
Copyright © 2007 Likewise Software. All rights reserved. 164
Product Documentation
Likewise 4.0: Administrator’s Guide
groups=10(wheel),100000(CORP\domain^users),100005(CORP\vm
admins) context=system_u:system_r:unconfined_t
[johnyu@juser-linux ~]$
Use Firefox to Single Sign-On to Intranet Sites
When logged on an X11 desktop, you have access to GSS-aware
applications such as Mozilla Firefox. Firefox is configured by default to
not attempt a negotiation with any website. To override this behavior,
change network.negotiate-auth.delegation-uris and
network.negotiate-auth.trusted-uris to include a filter white
list of URIs that the browser will attempt to negotiate a single sign-on
with. Among the broadest may be Error! Hyperlink reference not valid
and Error! Hyperlink reference not valid, which includes all standard web
URIs.
Then, restart the web browser and point to a Windows authenticated web
site, such as Sharepoint.
Copyright © 2007 Likewise Software. All rights reserved. 165
Product Documentation
Likewise 4.0: Administrator’s Guide
Troubleshooting the Agent
Check Authentication
On the Unix or Linux computer that is joined to the Active Directory
domain, you can check the domain user's information by executing the
following command at the shell prompt. Replace username with the
name of the user that you want to check.
/usr/centeris/bin/lwiinfo –i username
If Do this
The wrong information is Check Active Directory to make
returned sure the user has an account.
The user is not found Check the status of the
authentication daemon.
The user is found Check whether the same user is
in the /etc/passwd file. If
necessary, migrate the user.
Check the Status of the Authentication Daemon
You can check the status of the authentication daemon on a Unix or
Linux computer running the Likewise Agent by executing the following
command at the shell prompt as the root user:
/sbin/service centeris.com-lwiauthd status
If the authentication daemon is running, the result should look like this:
lwiauthd (pid 18258 18257 18012 17912 17911) is running...
If the service is not running, execute the following command:
/sbin/service centeris.com-lwiauthd start
Next, as the root user, check whether the authentication daemon is
communicating with the windbind daemon by executing the following
command:
/usr/centeris/bin/lwiinfo -p
Copyright © 2007 Likewise Software. All rights reserved. 166
Product Documentation
Likewise 4.0: Administrator’s Guide
If all is well, the result should look like this:
Ping to winbindd succeeded on fd 4
Check the Status of the Group Policy Daemon
You can check the status of the group policy daemon on a Unix or Linux
computer running the Likewise Agent by executing the following
command at the shell prompt as the root user:
/sbin/service centeris.com-gpagentd status
If all is well, the result should look like this:
centeris-gpagentd (pid 17946) is running...
Check the Version and Build Number
Check the Version Number of the Agent
To check the version number of the Likewise Agent, execute one of the
following commands at the shell prompt:
Operating System Command
Linux /usr/centeris/bin/lwiinfo
--version
or
/usr/centeris/bin/lwiinfo
-V
Unix and Mac OS X /opt/centeris/bin/lwiinfo
--version
or
/opt/centeris/bin/lwiinfo
–V
Note: In the shorthand version, the -V must be an uppercase letter.
Check the Build Number of the Agent
On Linux distributions that support RPM -- for example, Red Hat
Enterprise Linux, Fedora, SUSE Linux Enterprise, openSUSE, and
Copyright © 2007 Likewise Software. All rights reserved. 167
Product Documentation
Likewise 4.0: Administrator’s Guide
CentOS -- you can determine the build number of the agent (3.5.0.xxxx)
by executing the following command at the shell prompt:
rpm -qa | grep centeris
The result shows the build version after the version number:
centeris-openldap-2.3.27-3.15040.868
centeris-auth-3.1.0-1.15090.877
centeris-krb5-1.5.1-10.15040.868
centeris-grouppolicy-3.1.0-1.15097.878
centeris-auth-mono-1.2.2-0.15097.878
centeris-password-policy-3.1.0-1.15097.878
centeris-expat-2.0.0-2.15097.878
centeris-auth-gui-3.1.0-1.15097.878
On Unix computers and Linux distributions that do not support RPM, the
command to check the build number varies by platform:
Platform Command
Debian dpkg –S /usr/centeris/
Solaris pkgchk-l -p | grep
centeris
AIX lslpp –l | grep centeris
HP-UX swlist -l | grep centeris
Clear the Authentication Cache
There are certain conditions under which you might need to clear the
cache so that a user's ID is recognized on a target computer.
The user's ID is, by default, cached for 900 seconds (15 minutes). If you
change a user's UID for a Likewise cell, during the 900 seconds after you
change the UID you must clear the cache on a target computer in the cell
before the user can log on.
Or, if you set the Minimum UID-GID Value group policy to 99 for a OU
with an associated Likewise cell that contains a user with a UID lower
than 99, you must change the user's UID so that it is 99 or higher and
then you must clear the cache before the user can log on during the 15-
minute period after the change.
Copyright © 2007 Likewise Software. All rights reserved. 168
Product Documentation
Likewise 4.0: Administrator’s Guide
If you do not clear the cache after changing the UID, the computer will
not find the user until after the cache expires:
#id centerisdemo\\blugosi
id: centerisdemo\blugosi: No such user
There are three Likewise group policies that can affect the cache time:
• The Winbind Cache Expiration Time, which stores UID-SID mappings,
user/group enumeration lists, getgrnam() and getpwnam(), and so
forth. Its default expiration time is 900 seconds (15 minutes).
• The ID Mapping Cache Expiration Time, which caches the mapping
tables for SIDs, UIDs, and GIDs. Its default is 1 hour.
• The ID Mapping Negative Cache Expiration Time, which stores failed
SID-UID-GID lookups to prevent an overload of resolution requests.
Its default is 5 minutes.
Tip: While you are deploying and testing Likewise, set the cache
expiration times of the Winbind Cache Expiration Time and the ID
Mapping Cache Expiration Time policies to a short period of time.
Clear the Cache on a Linux Computer
1. Stop the Likewise authentication daemon by executing the following
command as root:
/etc/init.d/centeris.com-lwiauthd stop
2. Clear the cache:
rm -f /var/lib/lwidentity/*tdb
3. Start the Likewise authentication daemon:
/etc/init.d/centeris.com-lwiauthd start
After the clearing the cache, the user is recognized:
# id centerisdemo\\blugosi
uid=101(CENTERISDEMO\blugosi)
gid=100000(CENTERISDEMO\domain^users)
groups=100000(CENTERISDEMO\domain^users)
Copyright © 2007 Likewise Software. All rights reserved. 169
Product Documentation
Likewise 4.0: Administrator’s Guide
Determine a Computer's FQDN
You can determine the fully qualified domain name of a computer
running Linux, Unix, or Mac OS X by executing the following command at
the shell prompt:
ping -c 1 `hostname`
Force Group Policies to Refresh
The Group Policy Agent connects to Active Directory, retrieves changes
to policy objects, and applies the changes once every 30 minutes, when
a computer boots or restarts, or when requested by the GPO refresh
tool.
You can run the GPO refresh tool at any time on a Unix or Linux
computer within the Active Directory domain. To run the GPO refresh
tool on a Linux computer, execute the following command at the shell
prompt:
/usr/centeris/bin/gporefresh
On Unix computers, the command is slightly different:
/opt/centeris/bin/gporefresh
The command should return a result that looks like this:
20070731100621:0xb7f046c0:INFO:GPO Refresh succeeded
On target computers, Likewise stores its group policies in
/var/cache/centeris/grouppolicy.
Generate a Domain-Join Log
To help troubleshoot problems with joining a domain, you can use the
command-line utility's log option with the join command. The log
option captures information about the attempt to join the domain on the
screen or in a file.
• To display the information in the terminal, execute the following
command; the dot after --log specifies that the information is shown
in the console:
domainjoin-cli --log . join domainName userName
Copyright © 2007 Likewise Software. All rights reserved. 170
Product Documentation
Likewise 4.0: Administrator’s Guide
• To save the information in a log file, execute the following command:
domainjoin-cli --log path join domainName userName
Example:
domainjoin-cli --log /var/log/domainjoin.log join
centerisdemo.com Administrator
Generate a Group Policy Agent Debug Log
You can generate a group policy agent debug log on a Unix or Linux
computer running the Likewise Agent.
1. Log on as root user.
2. Stop the group policy daemon by executing the following command
at the shell prompt:
/sbin/service centeris.com-gpagentd stop
The command should return the following result:
Stopping gpagentd: [ OK ]
3. Start the group policy daemon in command-line debug mode and
capture the output in a file:
/usr/centeris/sbin/centeris-gpagentd --loglevel 4
> foo.log
4. From a separate root session, execute the following command to
force a GPO refresh:
/usr/centeris/bin/gporefresh
Generate a Network Trace
Execute the following command in a separate session to dump network
traffic as the root user and interrupt the trace with CTRL-C:
tcpdump –s 1500 –i eth0 –w trace.pcap
The result should look something like this:
Copyright © 2007 Likewise Software. All rights reserved. 171
Product Documentation
Likewise 4.0: Administrator’s Guide
tcpdump: listening on eth0
28 packets received by filter
0 packets dropped by kernel
Generate a PAM Debug Log
You can generate a debug log for PAM on a Unix or Linux computer
running the Likewise Agent. PAM stands for pluggable authentication
modules.
1. Log on as root user.
2. Edit /etc/security/pam_lwidentity.conf so that it includes
the following:
[global]
debug = yes
The data is sent to syslog.
3. After some activity, in /etc/security/pam_lwidentity.conf,
comment out the line with debug = yes.
By default, this information appears in /var/log/messages.
Generate an Authentication Agent Debug Log
1. Log in as root user.
2. Modify the file /etc/samba/lwiauthd.conf to include the
following:
[global]
log level = 10
3. Restart the Likewise authentication daemon by executing the
following command from the command line:
/sbin/service centeris.com-lwiauthd restart
The result should look like this:
Stopping lwiauthd: [ OK ]
Starting lwiauthd: [ OK ]
Copyright © 2007 Likewise Software. All rights reserved. 172
Product Documentation
Likewise 4.0: Administrator’s Guide
4. After some activity, comment out the log level line and restart
the daemon.
Important: If you do not comment out the log level and then restart
the daemon, you might run into disk space issues over time.
The log files will appear in /var/log/lwidentity.
Make Sure Outbound Ports Are Open
If you are using local firewall settings, such as iptables, on a computer
running the Likewise Agent, make sure the following ports are open for
outbound traffic.
Note: The Likewise Agent is a client only; it does not listen on any ports.
Port Protocol Use
53 UDP/TCP DNS
88 UDP/TCP Kerberos
123 UDP NTP
137 UDP NetBIOS Name
Service
139 TCP NetBIOS Session
(SMB)
389 UDP/TCP LDAP
445 TCP SMB over TCP
Restart the Authentication Daemon
You can restart the authentication daemon by executing the following
command at the shell prompt:
/etc/init.d/centeris.com-lwiauthd restart
To stop the daemon, enter the following command:
/etc/init.d/centeris.com-lwiauthd stop
To start the daemon, enter the following command:
/etc/init.d/centeris.com-lwiauthd start
Copyright © 2007 Likewise Software. All rights reserved. 173
Product Documentation
Likewise 4.0: Administrator’s Guide
Restart the Group Policy Daemon
You can restart the group policy daemon by executing the following
command from the command line:
/etc/init.d/centeris.com-gpagentd restart
To stop the daemon, enter the following command:
/etc/init.d/centeris.com-gpagentd stop
To start the daemon, enter the following command:
/etc/init.d/centeris.com-gpagentd start
Copyright © 2007 Likewise Software. All rights reserved. 174
Product Documentation
Likewise 4.0: Administrator’s Guide
Contact Technical Support
For either post-sales technical support or for free technical support
during an evaluation period, please visit the Likewise support Web page
at http://www.likewisesoftware.com/support/. You can use the support
page to register for support, submit incidents, and receive direct
technical assistance.
Technical support may ask for your Likewise version, Linux version, and
Microsoft Windows version. To find the Likewise product version, in the
Likewise Console, on the menu bar, click Help, and then click About.
Copyright © 2007 Likewise Software. All rights reserved. 175
Product Documentation
Likewise 4.0: Administrator’s Guide
Platform Support
Likewise supports a broad range of platforms. Likewise Software is constantly adding new vendors and
distributions to the following list. To get the latest list of supported platforms, go to
www.likewisesoftware.com.
Supported
Vendor Distribution
32-bit 64-bit
SuSE Linux Desktop 8.2 Yes -
SuSE Linux Desktop 9.0 Yes -
SuSE Linux Desktop 9.1 Yes Yes
SuSE Linux Desktop 9.2 Yes Yes
SuSE Linux Desktop 9.3 Yes Yes
SuSE SuSE Linux Enterprise Desktop 10.0 Yes Yes
OpenSuSE Linux 10.0 Yes Yes
OpenSuSE Linux 10.1 Yes Yes
OpenSuSE Linux 10.2 Yes Yes
SuSE Linux Enterprise Server 9.0 Yes Yes
SuSE Linux Enterprise Server 10.0 Yes Yes
Red Hat Red Hat Enterprise Linux AS 2.1 Yes -
Red Hat Enterprise Linux ES 2.1 Yes -
Red Hat Enterprise Linux WS 2.1 Yes -
Red Hat Enterprise Linux AS 3.0 Yes Yes
Red Hat Enterprise Linux ES 3.0 Yes Yes
Red Hat Enterprise Linux WS 3.0 Yes Yes
Red Hat Enterprise Linux AS 4.0 Yes Yes
Copyright © 2007 Likewise Software. All rights reserved. 176
Product Documentation
Likewise 4.0: Administrator’s Guide
Red Hat Enterprise Linux ES 4.0 Yes Yes
Red Hat Enterprise Linux WS 4.0 Yes Yes
Red Hat Enterprise Linux 5.0 Yes Yes
Red Hat Enterprise Linux 5.0 Desktop Yes Yes
Red Hat Enterprise Linux 5.0 Advanced Platform Yes Yes
Red Hat Enterprise Linux AS 7.2 Yes -
Red Hat Enterprise Linux ES 7.2 Yes -
Red Hat Enterprise Linux WS 7.2 Yes -
Red Hat Enterprise Linux AS 7.3 Yes -
Red Hat Enterprise Linux ES 7.3 Yes -
Red Hat Enterprise Linux WS 7.3 Yes -
Red Hat Enterprise Linux AS 8 Yes -
Red Hat Enterprise Linux ES 8 Yes -
Red Hat Enterprise Linux WS 8 Yes -
Red Hat Enterprise Linux AS 9 Yes -
Red Hat Enterprise Linux ES 9 Yes -
Red Hat Enterprise Linux WS 9 Yes -
Fedora Core 3 Yes Yes
Fedora Core 4 Yes Yes
Fedora Fedora Core 5 Yes Yes
Fedora Core 6 Yes Yes
Fedora Core 7 Yes Yes
Copyright © 2007 Likewise Software. All rights reserved. 177
Product Documentation
Likewise 4.0: Administrator’s Guide
CentOS 4.0 Yes Yes
CentOS 4.1 Yes Yes
CentOS 4.2 Yes Yes
CentOS
CentOS 4.3 Yes Yes
CentOS 4.4 Yes Yes
CentOS 5.0 Yes Yes
Debian Debian Linux 3.1 Yes Yes
Ubuntu Desktop 6.06 Yes Yes
Ubuntu Desktop 6.10 Yes Yes
Ubuntu Ubuntu Server 6.06 Yes Yes
Ubuntu Server 6.10 Yes Yes
Ubuntu Desktop 7.04 Yes Yes
Solaris 8 (SPARC) Yes Yes
Solaris 9 (SPARC) Yes Yes
Sun
Solaris 10 (SPARC) Yes Yes
Solaris 10 x86 Yes Yes
AIX 5L 5.2 Yes Yes
AIX
AIX 5L 5.3 Yes Yes
HP-UX 11.11 PA-RISC - Trusted Mode - Yes
HP-UX 11.11 PA-RISC - 64-bit - Yes
HP
HP-UX 11.23 Itanium - Trusted Mode - Yes
HP-UX 11.23 Itanium - 64-bit - Yes
Copyright © 2007 Likewise Software. All rights reserved. 178
Product Documentation
Likewise 4.0: Administrator’s Guide
OS X v10.4 PPC Yes Yes
OS X Server v10.4 PPC Yes Yes
Apple
OS X v10.4 x86 Yes Yes
VMWare ESX Server 3.0.1 Yes -
Copyright © 2007 Likewise Software. All rights reserved. 179
Product Documentation
Likewise 4.0: Administrator’s Guide
ABOUT LIKEWISE
Likewise® Software solutions improve management and interoperability of Windows,
Linux, and UNIX systems with easy to use software for Linux administration and
cross-platform identity management.
Likewise provides familiar Windows-based tools for system administrators
to seamlessly integrate Linux and UNIX systems with Microsoft Active Directory.
This enables companies running mixed networks to utilize existing Windows skills
and resources, maximize the value of their Active Directory investment, strengthen
the security of their network and lower the total cost of ownership of Linux servers.
Likewise Software is a Bellevue, WA-based software company funded by leading
venture capital firms Ignition Partners, Intel Capital, and Trinity Ventures. Likewise
has experienced management and engineering teams in place and is led by senior
executives from leading technology companies such as Microsoft, F5 Networks,
EMC and Mercury.
Copyright © 2007 Likewise Software. All rights reserved. 180
Vous aimerez peut-être aussi
- Likewise Samba Guide For Likewise Enterprise 4.1 or EarlierDocument9 pagesLikewise Samba Guide For Likewise Enterprise 4.1 or EarlierLikewise Software100% (3)
- Likewise Samba Guide 5Document9 pagesLikewise Samba Guide 5Likewise Software100% (3)
- Likewise Samba Guide 5Document9 pagesLikewise Samba Guide 5Likewise Software100% (3)
- Boost Compliance With Sarbanes-OxleyDocument19 pagesBoost Compliance With Sarbanes-OxleyLikewise Software100% (1)
- Likewise Whitepaper HIPAA ComplianceDocument17 pagesLikewise Whitepaper HIPAA ComplianceLikewise Software100% (2)
- How To Create and Test A Sudo Group Policy For Linux and UnixDocument9 pagesHow To Create and Test A Sudo Group Policy For Linux and UnixLikewise Software100% (2)
- Group Policies For Mac OS XDocument11 pagesGroup Policies For Mac OS XLikewise Software100% (1)
- Likewise Open 5.0 Installation and Administration GuideDocument86 pagesLikewise Open 5.0 Installation and Administration GuideLikewise Software100% (2)
- Using Likewise Cell Technology To Manage Users and ComputersDocument12 pagesUsing Likewise Cell Technology To Manage Users and ComputersLikewise Software100% (1)
- Using Likewise For Single Sign-OnWith Kerberos and Active DirectoryDocument7 pagesUsing Likewise For Single Sign-OnWith Kerberos and Active DirectoryLikewise Software100% (7)
- Likewise Open Version 5.0 Quick Install Guide For Mac OSDocument4 pagesLikewise Open Version 5.0 Quick Install Guide For Mac OSLikewise SoftwarePas encore d'évaluation
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (400)
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (588)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (895)
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (266)
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (74)
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (345)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (121)
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)
- Ansys Mechanical APDL FeaturesDocument298 pagesAnsys Mechanical APDL Featureschetan_thakur4278Pas encore d'évaluation
- Manual Service Brother 7065Document337 pagesManual Service Brother 7065pheniel1100% (2)
- Hamilton v. HernandezDocument29 pagesHamilton v. HernandezBillboardPas encore d'évaluation
- As204-80, As204-80Lf: Gaas Ic Sp4T Nonreflective Switch With Driver 300 Khz-3.5 GHZDocument4 pagesAs204-80, As204-80Lf: Gaas Ic Sp4T Nonreflective Switch With Driver 300 Khz-3.5 GHZnjesraPas encore d'évaluation
- Winpenpack Flash Expert: Applications ListDocument4 pagesWinpenpack Flash Expert: Applications Listrobi cahyadiPas encore d'évaluation
- Maintenance Costs and Life Cycle Cost AnalysisDocument24 pagesMaintenance Costs and Life Cycle Cost AnalysisHugoCabanillasPas encore d'évaluation
- Radiologic Science For Technologists Physics Biology and Protection 10th Edition Bushong Test BankDocument36 pagesRadiologic Science For Technologists Physics Biology and Protection 10th Edition Bushong Test Bankcostardrivel.4vwhu100% (13)
- M2000 HA System Administrator Guide (Sun, S10)Document498 pagesM2000 HA System Administrator Guide (Sun, S10)dattabhPas encore d'évaluation
- Image Studio Lite TutorialDocument40 pagesImage Studio Lite TutorialorutraodnamraPas encore d'évaluation
- Oracle Fusion Applications Administrator's Guide For Analytics and ReportsDocument48 pagesOracle Fusion Applications Administrator's Guide For Analytics and ReportsNitaiChand DasPas encore d'évaluation
- B737 QRH New Format HandoutDocument15 pagesB737 QRH New Format HandoutDiana Bi100% (4)
- Calculus Early Transcendentals 8th Edition Stewart Solutions ManualDocument26 pagesCalculus Early Transcendentals 8th Edition Stewart Solutions Manualflotegiantizelpjwy96% (23)
- Summary of The Case: FactsDocument17 pagesSummary of The Case: FactsRicha KesarwaniPas encore d'évaluation
- 7XV5655-0BA00-Hub Manual A4 PDFDocument51 pages7XV5655-0BA00-Hub Manual A4 PDFAldo Bona HasudunganPas encore d'évaluation
- Live Hard.... : ISSUE #12Document8 pagesLive Hard.... : ISSUE #12hsp32756Pas encore d'évaluation
- Full Download Introduction To Managerial Accounting 7th Edition Brewer Solutions ManualDocument22 pagesFull Download Introduction To Managerial Accounting 7th Edition Brewer Solutions Manualstulhokyb100% (32)
- Embedded Customization Course 10.0.700Document70 pagesEmbedded Customization Course 10.0.700nerz8830Pas encore d'évaluation
- Clicker 2 Pic32mx Manual v102Document33 pagesClicker 2 Pic32mx Manual v102yohiliPas encore d'évaluation
- Application Deployment Guide - Demand Planning 2016.2Document148 pagesApplication Deployment Guide - Demand Planning 2016.2Kothasudarshan KumarPas encore d'évaluation
- I T H ' M: N HE ON Ble High Court of AdrasDocument15 pagesI T H ' M: N HE ON Ble High Court of Adrasbhavna khatwaniPas encore d'évaluation
- Wealth of Knowledge Converting Intellectual ProperDocument51 pagesWealth of Knowledge Converting Intellectual ProperKonda LohithPas encore d'évaluation
- QN 1 Which of The Following Is NOT An Example of Literary Work?Document51 pagesQN 1 Which of The Following Is NOT An Example of Literary Work?Nguyễn Phước Định KiênPas encore d'évaluation
- OpenScape Voice Server V9R4.48.2 Release Notes V1.0 InternalDocument39 pagesOpenScape Voice Server V9R4.48.2 Release Notes V1.0 Internaldinesh SangamPas encore d'évaluation
- Developer License Agreement 30mar17 - Final v2Document18 pagesDeveloper License Agreement 30mar17 - Final v2Andy DaviesPas encore d'évaluation
- Illustrator Scripting GuideDocument57 pagesIllustrator Scripting GuideSravanKumarPas encore d'évaluation
- 1xze GAkobBnb9fsIDThYq35MbELg3o6eDocument9 pages1xze GAkobBnb9fsIDThYq35MbELg3o6elukas bentesPas encore d'évaluation
- CP Chemical Industry Pallets Edition Nr7 July 2017Document44 pagesCP Chemical Industry Pallets Edition Nr7 July 2017rafeik.isePas encore d'évaluation
- WBP Ten081110Document32 pagesWBP Ten081110njsmith5Pas encore d'évaluation
- Third Party Notices For UIIDocument2 pagesThird Party Notices For UIIsarathPas encore d'évaluation
- DMR Conventional Radio - BT - User Manual - R8.5Document42 pagesDMR Conventional Radio - BT - User Manual - R8.5Alex GomezPas encore d'évaluation