Académique Documents
Professionnel Documents
Culture Documents
Network Security - A Layered Approach: H. I. M. T. Greater Noida, D. N. College, Hisar, G. P. Hisar
Transféré par
srs0507Description originale:
Titre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Network Security - A Layered Approach: H. I. M. T. Greater Noida, D. N. College, Hisar, G. P. Hisar
Transféré par
srs0507Droits d'auteur :
Formats disponibles
Network Security A Layered Approach
Kanchan Bala1, Barjeena Lucky2, Surinder Pal Garg3 H. I. M. T. Greater Noida, 2D. N. College, Hisar, 3G. P. Hisar.
Abstract
Security issues are critical for the success of pervasive computing. Because pervasive computing and ebusiness may provide millions of people with the power to move trillions of dollars in goods or money by a few mouse clicks, the security of e-business transaction is a top priority. With the number of security threats on the rise, network security has become an essential part of maintaining the privacy and integrity of an enterprise. Network security provider has the technology to help you define your network against attacks by implementing preventative security solutions. Cryptography is a minor tool to obtain Network Security. Our layered approach to network security was designed with the knowledge that no single tool can protect every segment of network from harming. In reality, the surge of blended threats has resulted in the need for integration between individual security products in order to reduce possible gaps in protection.
methodical approach to network security. In many industries enhanced security is not an option-its mandatory federal regulation such as sarbnessoxelyGLBA and other require organizations such as financial institutions, health care providers and federal agencies to implement stringent security programs to protect digital assets. Now we are introducing you to a layered approach for securing your network. This layered approach is both a technical strategy, espousing adequate measures be put in place at different levels within your network infrastructures. The layered approach centers on maintaining appropriate security measures and procedures at five different levels within IT department. 1. Perimeter 2. Network 3. Host 4. Application 5. Data
1. Introduction
Network layer security is a key aspect of the internet based security mechanism. Originally; people were concentrating only on application level security. However, new security requirements demand that even the lower level data units should be protected. With the view in mind, network security mechanism has emerged and is being used extensively in real life.
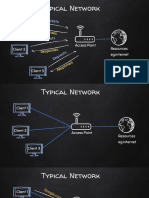
Figure 2. The security level in the layered approach and the technologies that function on each.
Figure 1. Network security A Layered Approach Network security is a mission-critical concern for enterprises, government agencies, and organizations of all sizes. Todays advanced threats demand a
2. Perimeter Security (Level 1)
The perimeter is the first line of defense from outside, un-trusted networks. The perimeter acts as the first and last point of contact for security defenses protecting the network. It is the area where your network ends and the Internet begins. The perimeter consists of one or more firewalls and a set of strictly controlled servers located in a portion of the perimeter referred to as the DMZ (demilitarized zone). A DMZ typically contains the Web Servers, email gateway, network antivirus and DNS servers that must be exposed to the internet. A compromised network perimeter can cripple your ability to conduct business. For Example, if your organization relies on your Web servers for revenue generation, and those servers have been hacked and are off-line, you lose money for every minute they are down. The following technologies provide security at the network perimeter.
2.2 Network Based Anti - Virus
Installed in the DMZ, network based anti -virus software compares incoming and outgoing email message content to a database known virus profiles. Network based anti-virus products block infected email traffic by quarantining suspicious and infected e-mail messages and then notifying recipients and administrators. This prevents email infected with a virus from entering and spreading across your network, and it prevents your network from spreading virus infected email. To work effectively, the database of known viruses must be kept up to date.
2.3 VPN
A VPN is a mechanism of employing encryption, authentication and integrity protection so that we can use a public network (Such as the Internet) as if it is a private network. A VPN is a mechanism to simulate a private network over a public network. It essentially creates an encrypted tunnel across the Internet, approximating the security and confidentiality of a private network. A VPN tunnel can terminate on a VPN- enabled router, firewall or server within the DMZ. Enforcing VPN connections for all remote and wireless network segments is an important bestpractice that is relatively easy and inexpensive to implement.
2.1 Firewall
A firewall is typically installed on a server connected to the inside and the outside of the network perimeter. A firewall performs three general functions: 1. Traffic Control 2. Address Translations 3. VPN terminations A firewall acts like a sentry. If implemented, it guards a corporate network by standing between the network and the outside world. All the traffic between the network and the internet in either direction must pass through the firewall. The firewall decides if the traffic can be allowed to flow or whether it must be stopped from proceeding further. It ensures that only permissible requests are allowed through. Additionally, firewalls help secure the network by translating internal IP addresses to IP addresses that are visible to the internet. This prevents the disclosure of critical information about the structure of the network inside the firewall. A firewall can also terminate VPN tunnels.
3. Network Security (Level 2)
The network level of the layered security model refers to your internal LAN and WAN. The following technologies provide security at network level:
3.1 Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)
IDS and IPS technologies analyze traffic moving across your network in much greater detail than your firewall. Similar to antivirus systems, IPS and IDS devices analyze traffic and compare each packet to a database of known attack profiles. The difference is that anti- virus inspects files on the system, whereas IDS and IPS inspects packets within network traffic. When attacks are detected, IDS/IPS technologies take action. IDS alert and IPS block the harmful traffic. In fact, most IPSs have an IDS at their core. The key difference between the technologies is implied by their names. IDS products only detect malicious traffic, while IPS products prevent such traffic from entering your network.
Figure 3. Firewall Installation
3.2 Vulnerability Management
Vulnerability management system performs two related function. They scan the network for source addresses, TCP state verification, and rouge services running on the network. They manage the process of
3.3 Network access control
Network access control solutions protect the network by ensuring that endpoints meet defined security standard before they are allowed to access the network. Endpoints security solutions allow or deny access based on tests run against a device when it attempts to connect. They typically test for (1) required software, such as service packs, up to date antivirus definitions, etc. and (2) prohibited applications, such as file sharing and spyware.
3.4 Access Control and User Authentication
Access control entails authenticating users who access your network. Authentication is typically performed against the user information in a RADIUS, LDAP or Window ACTIVE directory.
Figure 4. Intrusion Detection System
4. Host Security (Level 3)
In the layered security model, the host level pertains to the individual devices, Such as servers, switches, routers etc on the network. Each device has a number of configurable parameters that, when set inappropriately, can creater exploitable security holes. These parameters include registry settings, services operating on the device, or patches to the operating system or important applications. The following technologies provide security at host level.
Figure 5. Intrusion prevention system (out-of-band configuration)
4.1 Host based Intrusion Detection System
Host based IDs perform similarly to network IDsthe key difference being that they monitor traffic on a single network device. Host based IDs are fine tuned to the specific operational characteristics of the host device and therefore provide a high degree of protection when properly administered.
4.2 Host Based Vulnerability Assessment
Figure 6. Intrusion prevention system (In-Line Configuration) repairing the vulnerabilities found. Vulnerability managers scan devices on a network for flaws and vulnerabilities that could be exploited by hackers or harmful traffic. They typically maintain a database of rules that identify known vulnerabilities for a range of network devices and applications. Host base VA tool scan a single network device for security vulnerabilities. Host based VA tools are fine tuned to the device they are monitor. They are extremely accurate and make minimal demands on the hosts resources. Because they are configured specifically for the host device, they provide an excellent level of coverage when properly administered.
4.3 Network Access Control
Network access control solutions do double duty, protecting both the network and individual hosts. These solutions continually check the host for harmful applications and infection and also verify that required security measures, such as anti-virus and personal firewalls are installed and up to date.
6.1 Encryption
Data encryption schemes are commonly implemented at the data, the application, and the operating systems levels. Common encryption strategies include PKI, PGP and RSA.
6.2 Access Control / User Authentication
Like network, and host and application level authentication, only authorized users are given to access data.
4.4 Anti Virus
Device-specific anti-virus applications provide an additional layer of protection when used in conjunction with network based anti-virus tools.
7. Conclusion
Hackers and cyber terrorist are launching network attack combines with increasing frequency and sophistication. The traditional approach to securitynamely a firewall combined with an anti-virus in incapable of protecting. However, erect a formidable defense by implementing network security using a layered approach.
5. Application Security (Level 4)
Application level security is currently receiving a great deal of attention. Poorly protected applications can provide easy access to confidential data and records. The hard truth is that most programmers dont code with security in mind. Applications are being placed on the web for access by customers, partners or even remote employees with increasing frequency. The following technologies provide security at the application level:
8. References
[1] R.T. Morris, 1985, A Weakness in the 4.2BSD Unix TCP/IP Software, Computing Science Technical Report No. 117, AT&T Bell Laboratories, Murray Hill, New Jersey. [2] S.M. Bellovin, Security Problems in the TCP/IP Protocol Suite, Computer Communication Review, Vol. 19, No. 2, pp. 32-48, April 1989. [3] Y. Rekhter, R. Moskowitz, D. Karrenberg, G. de Groot, E. Lear, ``Address Allocation for Private Internets.'' RFC 1918. [4] J.P. Holbrook, J.K. Reynolds. ``Site Security Handbook.'' RFC 1244. [5] M. Curtin, ``Snake Oil Warning Signs: Encryption Software to Avoid.'' USENET <sci.crypt> Frequently Asked Questions File.
5.1 Application Shield
An application shield is frequently referred to as an application-level firewall. In ensures that incoming and outgoing requests are permissible for the given application. Commonly installed on web servers, email servers, database servers and similar machines, an application shield is transparent to the user but highly integrated with the device on the backend.
6. Data Security (Level 5)
Data level security entails a blend of policy and encryption. Encryption data where it resides and as it travels across your network is a recommended best practice because, if all other security measures fail, a strong encryption scheme protects your proprietary data. Data security is highly dependent on organization wide policies that govern who have access to data, what authorized users can do with it, and who has ultimately responsibility for its integrity and safe keeping. The following technologies provide security at data level:
Vous aimerez peut-être aussi
- Topic 2. Network SecurityDocument5 pagesTopic 2. Network SecurityRosetephanie ZalunPas encore d'évaluation
- Network Security Pros and ClassificationsDocument8 pagesNetwork Security Pros and ClassificationsAdam CooperPas encore d'évaluation
- Pp-I Com N SecDocument11 pagesPp-I Com N SecGawrav BaishyaPas encore d'évaluation
- 1.1. Firewall.: 1.2.1. Network PolicyDocument7 pages1.1. Firewall.: 1.2.1. Network PolicyPhát TrầnPas encore d'évaluation
- Data Security in Local Network Using Distributed FirewallDocument10 pagesData Security in Local Network Using Distributed FirewallAnonymous oQ82DcZnPas encore d'évaluation
- Module 3 Computer Network SecurityDocument5 pagesModule 3 Computer Network SecurityMac John Teves PobletePas encore d'évaluation
- NetworkSecurityFinalDocument7 pagesNetworkSecurityFinalMd. Ziaul Haque ShiponPas encore d'évaluation
- Network Security DesignDocument5 pagesNetwork Security DesignMahbubur RahmanPas encore d'évaluation
- Wireless Network Security Vulnerabilities Threats and CountermeasuresDocument6 pagesWireless Network Security Vulnerabilities Threats and CountermeasuresMaria BatoolPas encore d'évaluation
- Work SecurityDocument6 pagesWork Securitypardeep bainsPas encore d'évaluation
- Configure Firewall SettingsDocument4 pagesConfigure Firewall SettingsOliver C Silvano100% (1)
- Need For Network SecurityDocument8 pagesNeed For Network SecurityRyan CooperPas encore d'évaluation
- Unit - 2: Infrastructure of Network Security: StructureDocument44 pagesUnit - 2: Infrastructure of Network Security: StructureSreeprada VPas encore d'évaluation
- DSDocument14 pagesDSapi-26172869Pas encore d'évaluation
- Valnurabiloity AssessmentDocument5 pagesValnurabiloity AssessmentBlessing ShenjePas encore d'évaluation
- Network Security ReportDocument19 pagesNetwork Security ReportTushar ChandhokPas encore d'évaluation
- Dimaano, Zareena A. (IT 112 REPORT NOTES)Document7 pagesDimaano, Zareena A. (IT 112 REPORT NOTES)Zareena AgapanPas encore d'évaluation
- Intrusion Detection TechniquesDocument5 pagesIntrusion Detection TechniquesJoshua AyoolaPas encore d'évaluation
- Firewalls: Paper Presentation OnDocument10 pagesFirewalls: Paper Presentation OnKalyan DasariPas encore d'évaluation
- Lesson 1 Network SecurityDocument3 pagesLesson 1 Network SecurityBelle SebullenPas encore d'évaluation
- Firewall: What Is A Firewall?Document4 pagesFirewall: What Is A Firewall?Naveen AdaikkalamPas encore d'évaluation
- Firewalls For Network SecDocument48 pagesFirewalls For Network Sectarnedo1Pas encore d'évaluation
- Network Security Devices You Need To Know AboutDocument30 pagesNetwork Security Devices You Need To Know Aboutramya.gPas encore d'évaluation
- A Literature Survey On Network Attacks and Prevention: AbstractDocument7 pagesA Literature Survey On Network Attacks and Prevention: Abstractmani DILLSPas encore d'évaluation
- Basic Concepts of Network SecurityDocument16 pagesBasic Concepts of Network SecurityRajkumar DharmarajPas encore d'évaluation
- System For IntrusionDocument8 pagesSystem For IntrusionVictoria OdemakinPas encore d'évaluation
- Network SecurityDocument13 pagesNetwork SecurityGra VaqueroPas encore d'évaluation
- Design and Implementation of A Network Security Model For Cooperative NetworkDocument11 pagesDesign and Implementation of A Network Security Model For Cooperative NetworkJitendra Yadav100% (1)
- Research ProjectDocument8 pagesResearch ProjectAlvin ChiengPas encore d'évaluation
- Welcome To International Journal of Engineering Research and Development (IJERD)Document7 pagesWelcome To International Journal of Engineering Research and Development (IJERD)IJERDPas encore d'évaluation
- Network security and defending against common attacksDocument7 pagesNetwork security and defending against common attackskainat KhalidPas encore d'évaluation
- Internet Firewalls: BY T. Naveen KumarDocument11 pagesInternet Firewalls: BY T. Naveen KumarDarsh AntaniPas encore d'évaluation
- Chapter Goals: Security TechnologiesDocument12 pagesChapter Goals: Security TechnologiesDheeraj MishraPas encore d'évaluation
- Unit 6Document7 pagesUnit 6ayushmakhijani382Pas encore d'évaluation
- Security IssuesDocument9 pagesSecurity IssuesYogesh DeoPas encore d'évaluation
- Unit Iv Network Security and FirewallDocument22 pagesUnit Iv Network Security and FirewallUjwal KoiralaPas encore d'évaluation
- 09 - Network SecurityDocument1 page09 - Network SecurityWorldPas encore d'évaluation
- Cis300 Assignment1 09 Ajay Balami C30105210041Document9 pagesCis300 Assignment1 09 Ajay Balami C30105210041Sulav BalamiPas encore d'évaluation
- The Current Situation of The Existing SystemDocument4 pagesThe Current Situation of The Existing SystemSithmaPas encore d'évaluation
- Network SecuurityDocument25 pagesNetwork SecuurityDebopriyo SarkarPas encore d'évaluation
- Network Security: Compiled: Engineer M. Mago, Mba, MSC (Electronics & Automation Engineering, Telecoms)Document16 pagesNetwork Security: Compiled: Engineer M. Mago, Mba, MSC (Electronics & Automation Engineering, Telecoms)prosper mukaroPas encore d'évaluation
- Network Firewall 4Document8 pagesNetwork Firewall 4earl bagainPas encore d'évaluation
- Network Security - Attacks and Defense Mechanism by Designing An Intelligent Firewall AgentDocument14 pagesNetwork Security - Attacks and Defense Mechanism by Designing An Intelligent Firewall AgentAdekogbe damilarePas encore d'évaluation
- "Firewall": A Written Report in Network ManagementDocument16 pages"Firewall": A Written Report in Network ManagementLeah Ann DiazPas encore d'évaluation
- Banking System Have ApplicationsDocument6 pagesBanking System Have ApplicationsRahul SurapaneniPas encore d'évaluation
- Design and Implementation of A Network Security Model For Cooperative Network PDFDocument11 pagesDesign and Implementation of A Network Security Model For Cooperative Network PDFSpad ParnianPas encore d'évaluation
- Design and Implementation of A Network Security Model For Cooperative Network PDFDocument11 pagesDesign and Implementation of A Network Security Model For Cooperative Network PDFyassin alkulaiPas encore d'évaluation
- Unit 5Document27 pagesUnit 519wj-1236 tejaswiPas encore d'évaluation
- On Firewall ReportDocument12 pagesOn Firewall ReportPrincess Yashika0% (1)
- Network Security FrameworkDocument7 pagesNetwork Security FrameworkStevePas encore d'évaluation
- NETB238 Test2Document7 pagesNETB238 Test2Hose ezeldinPas encore d'évaluation
- "Role of Firewalls in Internet Security": Harshali R.JoshiDocument5 pages"Role of Firewalls in Internet Security": Harshali R.Joshi111jalwa_1111jalwaPas encore d'évaluation
- Introduction To Networks - Network SecurityDocument5 pagesIntroduction To Networks - Network SecurityFaical BitamPas encore d'évaluation
- Firewalls: Paper Presentation OnDocument10 pagesFirewalls: Paper Presentation OnSonu SinghPas encore d'évaluation
- NETWORKSECURITYDocument4 pagesNETWORKSECURITYytbarekukPas encore d'évaluation
- Submitted By: B.S.S Monica B.Sarath Chaitanya Iii/Ivcse Iii/IvcseDocument10 pagesSubmitted By: B.S.S Monica B.Sarath Chaitanya Iii/Ivcse Iii/IvcseSarathchaitanya BeharaPas encore d'évaluation
- CSS10-1ST Quarter - Week 5Document21 pagesCSS10-1ST Quarter - Week 5George Mar Bien AriolaPas encore d'évaluation
- Configuration of Firewall-Om ChauhanDocument6 pagesConfiguration of Firewall-Om Chauhan2203031240954Pas encore d'évaluation
- CYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookD'EverandCYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookPas encore d'évaluation
- CEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021D'EverandCEH: Certified Ethical Hacker v11 : Exam Cram Notes - First Edition - 2021Pas encore d'évaluation
- Networks+ +Pre+Connection+AttacksDocument15 pagesNetworks+ +Pre+Connection+AttacksUDIT RAYPas encore d'évaluation
- 8.1.4.7 Packet Tracer - Subnetting Scenario 1 PDFDocument4 pages8.1.4.7 Packet Tracer - Subnetting Scenario 1 PDFSyammirul RashidPas encore d'évaluation
- Lte Drive Test ConceptDocument8 pagesLte Drive Test ConceptDineshRamaPas encore d'évaluation
- 4.3.1.6 Lab - Troubleshoot PPoE PDFDocument7 pages4.3.1.6 Lab - Troubleshoot PPoE PDFcesarinj20% (5)
- Computer Network Case StudyDocument20 pagesComputer Network Case StudyFatima Chariwala100% (1)
- Flexi Hopper XC: DatasheetDocument4 pagesFlexi Hopper XC: DatasheetFllu124Pas encore d'évaluation
- Moxa Eds P506e Series Datasheet v1.0Document6 pagesMoxa Eds P506e Series Datasheet v1.0Carlos Garcia Jacome DarkerPas encore d'évaluation
- Lab 1Document2 pagesLab 1flickishdesirePas encore d'évaluation
- Network Topology ICF 8Document9 pagesNetwork Topology ICF 8Gianan JPPas encore d'évaluation
- Huawei B315s-22 Manual Product Description PDFDocument21 pagesHuawei B315s-22 Manual Product Description PDFgitsPas encore d'évaluation
- Computer Networks: Application LayerDocument64 pagesComputer Networks: Application LayerkratiPas encore d'évaluation
- AVIAT TRANSMISSION CONFIGURATION GUIDEDocument13 pagesAVIAT TRANSMISSION CONFIGURATION GUIDEDickson Ndambuki Mang’uuPas encore d'évaluation
- 3hh 03573 Aaaa Tqzza 01 Isam r2 5 System DescriptionDocument196 pages3hh 03573 Aaaa Tqzza 01 Isam r2 5 System DescriptionStavros SotiriadisPas encore d'évaluation
- DEF CON China 1.0 - Sergey-Puzankov-Attacks-you-can't-combat-vulnerabilities-of-most-robust-mobile-operators PDFDocument51 pagesDEF CON China 1.0 - Sergey-Puzankov-Attacks-you-can't-combat-vulnerabilities-of-most-robust-mobile-operators PDFJohn ZhouPas encore d'évaluation
- Configuring IPsec VPN With A FortiGate and A Cisco ASADocument6 pagesConfiguring IPsec VPN With A FortiGate and A Cisco ASAAshokPas encore d'évaluation
- Air Interface: 5G YjsDocument38 pagesAir Interface: 5G YjsRoei ZoharPas encore d'évaluation
- Drive Test QuestionsDocument9 pagesDrive Test Questionsmoses50% (2)
- Is Called A Protocol.: Protocol Is A Standard Procedure and Format That Two Data Communication DevicesDocument7 pagesIs Called A Protocol.: Protocol Is A Standard Procedure and Format That Two Data Communication DevicesHeta DesaiPas encore d'évaluation
- Data Sheet 6GK5213-3BB00-2TB2: Transfer RateDocument6 pagesData Sheet 6GK5213-3BB00-2TB2: Transfer RateClaudiu VlasceanuPas encore d'évaluation
- 4G TrainingDocument31 pages4G TrainingFahim Sayed100% (1)
- Cisco CCNA SyllabusDocument2 pagesCisco CCNA Syllabusnidheesh1001Pas encore d'évaluation
- week13-FIREWALL IPTABLESDocument54 pagesweek13-FIREWALL IPTABLESПашаPas encore d'évaluation
- TL-MR6400 (UN V1 Datasheet PDFDocument7 pagesTL-MR6400 (UN V1 Datasheet PDFJuan Dela CruzPas encore d'évaluation
- Huawei Wifi Ax3Document356 pagesHuawei Wifi Ax3camilo0699Pas encore d'évaluation
- BRKDCT 2378Document104 pagesBRKDCT 2378Ken YuPas encore d'évaluation
- Ieee 802Document1 pageIeee 802api-3835728Pas encore d'évaluation
- Skillsheet-15A - Cambridge VCE Further MathematicsDocument2 pagesSkillsheet-15A - Cambridge VCE Further MathematicsPPas encore d'évaluation
- WiMAX Modeling Techniques and Applications PDFDocument133 pagesWiMAX Modeling Techniques and Applications PDFคนชายแดน ฝั่งตะวันตกPas encore d'évaluation
- SOP For PTCL White Leble Telephone ComplaintsDocument2 pagesSOP For PTCL White Leble Telephone ComplaintsKashifntcPas encore d'évaluation
- Packet FilteringDocument29 pagesPacket Filteringvijit13100% (1)