Académique Documents
Professionnel Documents
Culture Documents
AoIS CFP
Transféré par
Meraj AhmadDescription originale:
Titre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
AoIS CFP
Transféré par
Meraj AhmadDroits d'auteur :
Formats disponibles
Call for Papers Annals of Information Systems Special Volume in Security Informatics
Guest Editors: Christopher C. Yang (The Chinese University of Hong Kong, Hong Kong), Michael Chau (The University of Hong Kong, Hong Kong), Jau-Hwang Wang (Central Police University, Taiwan), and Hsinchun Chen (University of Arizona, USA)
Introduction
Intelligence and Security Informatics (ISI) is the study of the development and use of advanced information systems and technologies for national, international, and societal security-related applications. ISI topics include ISI data management, data and text mining for ISI applications, terrorism informatics, deception and intent detection, terrorist and criminal social network analysis, public health and bio-security, crime analysis, cyber-infrastructure protection, transportation infrastructure security, policy studies and evaluation, information assurance, among others. Due to the advent of terrorism attacks in recent years, ISI has gained increasingly more interest and attention from academic researchers, law enforcement and intelligence experts, information technology consultant and practitioners. The first IEEE International Conference on ISI was held in 2003 and subsequent meetings were held annually. Starting from 2006, the Workshops on ISI (PAISI) were also held annually in Pacific Asia, with large numbers of contributors and participants from the region. A European Workshop on ISI will also be started in Denmark in 2008. Given the importance of ISI, we are editing a volume of Annals of Information Systems on this topic. Annals of Information Systems is a journal series, consisting of volumes that address a specialized topic or a theme. AoIS publishes peer reviewed works in the analytical, technical as well as the organizational side of information systems. This journal series is part of a larger book series program run by Springer called Integrated Series in Information Systems, which comprises handbooks, monographs and other compiled collections of refereed research papers.
Scope
We solicit papers in four major subject areas in ISI, namely, (I) Information and Systems Security, (II) Information Sharing and Analysis in Security Informatics, (III) Infrastructure Protection and Emergency Responses, and (IV) National Security and Terrorism Informatics. Tentative subtopics under each topic are listed as follows:
I. Information and Systems Security Information assurance System security Internet security Corporate security policy and governance Identify fraud detection Biometrics and web signatures Social computing Secured access Privacy and security Cyber warfare Trust and security Civil liberties II. Information Sharing and Analysis in Security Informatics Intelligence-related knowledge discovery Criminal data mining and network analysis Criminal/intelligence info. sharing and visualization Web-based intelligence monitoring and analysis Spatio-temporal data analysis/GIS for crime analysis and security informatics Deception and intent detection Cyber-crime detection and analysis Authorship analysis and identification Applications of digital library technologies in intelligence data processing, preservation, sharing, and analysis Agents/collaborative systems for intelligence sharing HCI and UI of relevance to intelligence and security Information sharing policy and governance Privacy, security, and civil liberties issues III. Infrastructure Protection and Emergency Responses Public/animal health and bioterrorism info. infrastructure Transportation and communication infrastructure protection Cyber-infrastructure design and protection Intrusion detection Border/transportation safety Emergency response and management Disaster prevention, detection, & management Communication and decision support for search and rescue Assisting citizens' responses to terrorism and catastrophic events IV. National Security and Terrorism Informatics Terrorism related analytical methodologies and software tools Terrorism knowledge portals and databases Terrorist incident chronology databases Terrorism root cause analysis Social network analysis (radicalization, recruitment, conducting operations), visualization, and simulation Forecasting terrorism Countering terrorism Measuring the impact of terrorism on society
Submission
Authors are requested to present their manuscripts in a manner understandable to general professionals in English, following the Springer LNCS paper template. The instruction and template are available at http://www.se.cuhk.edu.hk/~yang/sv_contrib_11e.zip. Each manuscript should have 5000 to 8000 words and should follow a uniform structure as described below: Title: no longer than 10 words Affiliation: complete affiliation, position, postal, and email addresses Abstract: no more than 250 words Introduction: introduce the significance of the manuscript Literature Review of the field: a coherent and systematic review of related works in the topic area suitable for non-experts. Case studies/examples: One or two detailed case studies or examples of the presenting techniques, systems, implementations, and evaluation. Discussions and Conclusions References: 10 30 references Online resources (if available): a list of online resources that are relevant to the topic, e.g. Web sites, open source software, datasets, testbeds, demos, ontologies, benchmark results, golden standards, online publications, and reports, etc. Papers should be submitted to yang@se.cuhk.edu.hk by email. Submission is due on July 14, 2008.
Vous aimerez peut-être aussi
- 20bce7201-Cs Final Lab ReportDocument20 pages20bce7201-Cs Final Lab ReportCHAVA VEDHA SAMHITHA 20BCE7201Pas encore d'évaluation
- The Synergy of Scientometric Analysis and Knowledge Mapping With Topic Models Modelling The Development Trajectories of Information Security and Cyber Security ResearchDocument34 pagesThe Synergy of Scientometric Analysis and Knowledge Mapping With Topic Models Modelling The Development Trajectories of Information Security and Cyber Security ResearchnaelyPas encore d'évaluation
- Research Proposal Handout 2Document3 pagesResearch Proposal Handout 2Grosir Tas KenKanPas encore d'évaluation
- Keynote Lecture 1 Dark Web: Exploring and Mining The Dark Side of The WebDocument2 pagesKeynote Lecture 1 Dark Web: Exploring and Mining The Dark Side of The WebPrajwal PatilPas encore d'évaluation
- Weis2015 CFPDocument2 pagesWeis2015 CFPpankajpandeylkoPas encore d'évaluation
- Cyber Crime Investigation Syllabus - Dr. Jayakumar .VDocument1 pageCyber Crime Investigation Syllabus - Dr. Jayakumar .VPrasoonPas encore d'évaluation
- Data Science JournalDocument2 pagesData Science JournalMukesh NalekarPas encore d'évaluation
- Internet Security and PrivacyDocument9 pagesInternet Security and PrivacykolawolePas encore d'évaluation
- Symmetry: Artificial Intelligence in The Cyber Domain: Offense and DefenseDocument24 pagesSymmetry: Artificial Intelligence in The Cyber Domain: Offense and Defensechow sajPas encore d'évaluation
- Electronics: A Comparative Analysis of Cyber-Threat Intelligence Sources, Formats and LanguagesDocument22 pagesElectronics: A Comparative Analysis of Cyber-Threat Intelligence Sources, Formats and LanguagesstPas encore d'évaluation
- Tacd PresentationDocument9 pagesTacd PresentationParth PawarPas encore d'évaluation
- Ucl Secret Open Evening 2020Document51 pagesUcl Secret Open Evening 2020Manoj Shahu (Lecturer)Pas encore d'évaluation
- Dark Web Terrorism Research - Research - Artificial Intelligence Laboratory - Eller College of Management - The University of ArizonaDocument9 pagesDark Web Terrorism Research - Research - Artificial Intelligence Laboratory - Eller College of Management - The University of ArizonaHutch Rev OliverPas encore d'évaluation
- ICDARDocument5 pagesICDARcloudserviceuitPas encore d'évaluation
- Overview OSINTv1Document39 pagesOverview OSINTv1ridwanfachruPas encore d'évaluation
- Research Paper - A Synopsis On Cyber Terrorism and Warfare by Shreedeep RayamajhiDocument27 pagesResearch Paper - A Synopsis On Cyber Terrorism and Warfare by Shreedeep RayamajhiShreedeepRayamajhi100% (5)
- Task 4Document2 pagesTask 4TessaPas encore d'évaluation
- ICDP11CFPDocument1 pageICDP11CFPYounghyunLeePas encore d'évaluation
- Digital Privacy Theory Policies and TechnologiesDocument3 pagesDigital Privacy Theory Policies and TechnologiesfloraagathaaPas encore d'évaluation
- Deviance in Social Media and Social Cyber Forensics Uncovering Hidden Relations Using Open Source Information (OSINF)Document116 pagesDeviance in Social Media and Social Cyber Forensics Uncovering Hidden Relations Using Open Source Information (OSINF)Ari El VoyagerPas encore d'évaluation
- Critical Information Infrastructures Security: Erich Rome Marianthi Theocharidou Stephen WolthusenDocument269 pagesCritical Information Infrastructures Security: Erich Rome Marianthi Theocharidou Stephen WolthusenVikasPas encore d'évaluation
- Advancing Information Systems Theories Rationale and Processes 1St Edition Nik Rushdi Hassan Full ChapterDocument51 pagesAdvancing Information Systems Theories Rationale and Processes 1St Edition Nik Rushdi Hassan Full Chapterlakisha.province164100% (16)
- Call For Book ChaptersDocument4 pagesCall For Book ChaptersCIO White PapersPas encore d'évaluation
- A FrontDocument40 pagesA Frontrhemacs3Pas encore d'évaluation
- CF Lecture 02-Digital Forensics and Cyber CrimesDocument43 pagesCF Lecture 02-Digital Forensics and Cyber CrimesFaisal ShahzadPas encore d'évaluation
- CSLeichter Interpol 11.09.2017Document47 pagesCSLeichter Interpol 11.09.2017drcarlleichterPas encore d'évaluation
- (OSINT) Open Source Intelligence Investigation - From Strategy To Implementation (2016)Document302 pages(OSINT) Open Source Intelligence Investigation - From Strategy To Implementation (2016)dogeveneziano63% (8)
- Combatting Cybercrime and Cyberterrorism - Challenges, Trends and Priorities (PDFDrive)Document321 pagesCombatting Cybercrime and Cyberterrorism - Challenges, Trends and Priorities (PDFDrive)John Kissel ComboPas encore d'évaluation
- Detecting Cyber Security Threats in WeblogsDocument12 pagesDetecting Cyber Security Threats in Weblogsayoub_itPas encore d'évaluation
- 10.1007@978 3 030 27615 7Document458 pages10.1007@978 3 030 27615 7Abdillah AzulPas encore d'évaluation
- Third IFIP WGDocument172 pagesThird IFIP WGGábor GrünhutPas encore d'évaluation
- CSLeichter 15.09.2017 NISLabC1 As IntendedDocument49 pagesCSLeichter 15.09.2017 NISLabC1 As IntendeddrcarlleichterPas encore d'évaluation
- IntroductionDocument4 pagesIntroductionmndungu225Pas encore d'évaluation
- A Review of Motivations of Illegal Cyber ActivitieDocument18 pagesA Review of Motivations of Illegal Cyber ActivitieAdhi Indra HermanuPas encore d'évaluation
- Designing A Data Warehouse For Cyber Crimes: Il-Yeol Song John D. MaguireDocument18 pagesDesigning A Data Warehouse For Cyber Crimes: Il-Yeol Song John D. MaguireMohammad Faried RahmatPas encore d'évaluation
- Slowik-Resume LongDocument3 pagesSlowik-Resume Longramesh krPas encore d'évaluation
- Framework For The Cultivation of A Military Cybersecurity CultureDocument11 pagesFramework For The Cultivation of A Military Cybersecurity CultureClaudia EnescuPas encore d'évaluation
- Aderibigbe Ayomide CSC 439 AssignmentDocument12 pagesAderibigbe Ayomide CSC 439 AssignmentuniwylimpPas encore d'évaluation
- Case Study of Storm WormDocument4 pagesCase Study of Storm WormReynhel MabungaPas encore d'évaluation
- Research Questions Research Design DataDocument68 pagesResearch Questions Research Design Datajhay thegreatPas encore d'évaluation
- Literature ReviewDocument6 pagesLiterature ReviewDilshan ChristopherPas encore d'évaluation
- A Review of Trends and Issues of Cybersecurity inDocument21 pagesA Review of Trends and Issues of Cybersecurity inMisheck MarengaPas encore d'évaluation
- Cyber Security - International Relations - Oxford BibliographiesDocument28 pagesCyber Security - International Relations - Oxford Bibliographiesmaccio malloPas encore d'évaluation
- Researching Cybercrimes Methodologies, Ethics, and Critical ApproachesDocument548 pagesResearching Cybercrimes Methodologies, Ethics, and Critical ApproachesBrigada Osint50% (2)
- 9781643683096Document348 pages9781643683096haroonPas encore d'évaluation
- Hcii2013 - V11 - LNCS8014 - 978 3 642 39237 5Document636 pagesHcii2013 - V11 - LNCS8014 - 978 3 642 39237 5Jorge DávilaPas encore d'évaluation
- Canvas Chapter 8Document22 pagesCanvas Chapter 8Andrei Neagoe FILMSPas encore d'évaluation
- Data Mining: Chapter XLIDocument8 pagesData Mining: Chapter XLIJonathan Rodriguez PerezPas encore d'évaluation
- Eighth International Conference On Network & Communications Security (NCS 2016)Document2 pagesEighth International Conference On Network & Communications Security (NCS 2016)CS & ITPas encore d'évaluation
- Citizen Lab Booklet P EDocument20 pagesCitizen Lab Booklet P Epasqual32Pas encore d'évaluation
- Cyberloafing Research 1997-2019: A Citation-Based Literature ReviewDocument14 pagesCyberloafing Research 1997-2019: A Citation-Based Literature ReviewsharventhiriPas encore d'évaluation
- 10.1007/978 3 319 10377 8Document351 pages10.1007/978 3 319 10377 8josé rengifo delgadoPas encore d'évaluation
- Secuity SystemDocument13 pagesSecuity SystemNur WidiyasonoPas encore d'évaluation
- Track: Decision Analytics, Mobile Services and Service ScienceDocument2 pagesTrack: Decision Analytics, Mobile Services and Service Sciencebozzaitabob4493Pas encore d'évaluation
- Keyword Indexing and Searching Tool KIST A Tool ToDocument8 pagesKeyword Indexing and Searching Tool KIST A Tool ToFaimina RiyazPas encore d'évaluation
- E680 Instruction Manual EN V1.30Document40 pagesE680 Instruction Manual EN V1.30Роман НазаренкоPas encore d'évaluation
- ModlistDocument11 pagesModlistМиколаКомпанієцьPas encore d'évaluation
- DVLSI Expt 1Document3 pagesDVLSI Expt 1vickyPas encore d'évaluation
- Shihab Saadi ResumeDocument1 pageShihab Saadi ResumeMd. Nazmus ShakibPas encore d'évaluation
- Business Communication TodayDocument39 pagesBusiness Communication TodaymzPas encore d'évaluation
- Tele-Graffiti: By: Nagendra K. (4BW07EC410)Document26 pagesTele-Graffiti: By: Nagendra K. (4BW07EC410)nagendra_ec105393100% (1)
- Questions and Key Answer A. Multiple Choice Put The Cross (O) On The Letter A, B, or C For The Correct Answer!Document2 pagesQuestions and Key Answer A. Multiple Choice Put The Cross (O) On The Letter A, B, or C For The Correct Answer!FATHNISAH NURSAHBAN HZPas encore d'évaluation
- chp1 Logic CircuitDocument3 pageschp1 Logic Circuitheyfiez12Pas encore d'évaluation
- Robowars: Important Notes and GuidelinesDocument5 pagesRobowars: Important Notes and GuidelinesAkash KumarPas encore d'évaluation
- Rudrabhisheka-Stotram Telugu PDF File2009Document3 pagesRudrabhisheka-Stotram Telugu PDF File2009Sreenivas GPas encore d'évaluation
- 03 Activity 3 - ARGDocument4 pages03 Activity 3 - ARGstapaPas encore d'évaluation
- Micro MarkDocument116 pagesMicro MarkCem AvciPas encore d'évaluation
- 339ref AjDocument344 pages339ref AjEdwin Yachachin MarceloPas encore d'évaluation
- Darji Yashvi New ResumeDocument2 pagesDarji Yashvi New ResumePatel ManavPas encore d'évaluation
- Create A Variety of Assessments Using Pathways 2E Examview ContentDocument3 pagesCreate A Variety of Assessments Using Pathways 2E Examview ContentMaha Al AmadPas encore d'évaluation
- WP8 Enterprise Device Management ProtocolDocument96 pagesWP8 Enterprise Device Management ProtocolredinezPas encore d'évaluation
- Transistor Bias CircuitsDocument29 pagesTransistor Bias CircuitsbruhPas encore d'évaluation
- KanchanDocument84 pagesKanchanJyoti KumariPas encore d'évaluation
- ANSYS Mechanical APDL Advanced Tutorials PDFDocument380 pagesANSYS Mechanical APDL Advanced Tutorials PDFNam Vo50% (2)
- Barnagay Inventory Form 1Document2 pagesBarnagay Inventory Form 1Barangay San Jose Csfp100% (2)
- Circus ThesisDocument6 pagesCircus ThesisSomeoneWriteMyPaperSingapore100% (2)
- Digital Forensics ToolsDocument15 pagesDigital Forensics ToolsChartered AccountantPas encore d'évaluation
- DevOps Glossary - The DevOps Engineer's HandbookDocument17 pagesDevOps Glossary - The DevOps Engineer's HandbookvcmsrinivasPas encore d'évaluation
- 2 - Git Checklist (Light Theme)Document7 pages2 - Git Checklist (Light Theme)dymbv gPas encore d'évaluation
- Configuring A JOB in T24Document2 pagesConfiguring A JOB in T24Jagadeesh JPas encore d'évaluation
- DsPIC33F Family Reference Manual AllDocument4 pagesDsPIC33F Family Reference Manual AllVlad MizeffPas encore d'évaluation
- Soal B. Inggris Ke Bab 3Document5 pagesSoal B. Inggris Ke Bab 3atok ftcpPas encore d'évaluation
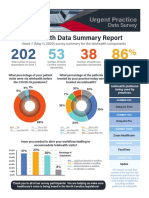
- UPDS Telehealth Data ReportDocument3 pagesUPDS Telehealth Data ReportCorey LarkinsPas encore d'évaluation
- GROWINGDocument269 pagesGROWINGRavinder SutariPas encore d'évaluation
- Media and Inofrmation Literarcy Quarter 2 - Module 3: People and Media Modules 3-4Document22 pagesMedia and Inofrmation Literarcy Quarter 2 - Module 3: People and Media Modules 3-4Rodge Cancino100% (1)