Académique Documents
Professionnel Documents
Culture Documents
Diffie - Hellman: Cryptography and Protocols Andrei Bulatov
Transféré par
BehzadDescription originale:
Titre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Diffie - Hellman: Cryptography and Protocols Andrei Bulatov
Transféré par
BehzadDroits d'auteur :
Formats disponibles
Diffie Introduction Hellman
Cryptography and Protocols Andrei Bulatov
Cryptography and Protocols Diffie Hellman
15-2
Key Exchange
Using public key cryptography is expensive. A better way is to use in limited amount to generate a key for a private key cryptosystem If p is prime then there is a primitive root modulo p, that is a p 1 2 3 number g such that {1,2,K, p 1} = {g , g , g ,K, g } Diffie Hellman protocol: - Alice chooses a prime q and finds a primitive root g - Alice chooses a random X from {1, , q 2} and sends X p, q and X g (mod q) to Bob - Bob chooses random Y from {1, , q 2} and sends Y g Y (mod q) to Alice - Alice and Bob compute k g XY (mod q) (by computing Y X and X Y respectively. They use k as a private key
Cryptography and Protocols Diffie Hellman
15-3
Diffie Hellman Protocol
gX
Alice
X Z* p k = (gY ) X gY
Bob
Y Z* p k = ( g X )Y
Cryptography and Protocols Diffie Hellman
15-4
Diffie Hellman Protocol
If Eve can compute discrete logarithm, that is find X and Y, then the protocol is insecure. However, this is not enough Decisional Diffie Hellman (DDH) Assumption. For every prime p and a primitive root g modulo p the following two distributions over triplets are computationally indistinguishable: < g X , g Y , g XY > X, Y are random it is not true !! < g X , gY , Z > X, Y, Z are random
Cryptography and Protocols Diffie Hellman
15-5
Man in the Middle
gX
Alice
X Z* p g
W
Eve
V Z* p W Z* p k = ( g X )W k ' = ( g Y )V
gV
Bob
Y Z* p
gY
Eve masquerades as Bob for Alice and as Alice for Bob. So she can read all messages they send
Cryptography and Protocols Diffie Hellman
15-6
Other Problems
How do we know that p is prime and g is a primitive root? What if Eve replace g X with 1? What if Eve replace g X with an element of small order Safe primes: p=2q+1 where q is a prime.
Digital Signatures Introduction
Cryptography and Protocols Andrei Bulatov
Cryptography and Protocols Digital Signatures
16-8
Definition
Similar to symmetric case we need to care about data integrity A triple (Gen, Sign, Ver) is called a (T,)-secure signature scheme if validity for any pair (s,v) generated by Gen and every P {0,1}n we have Verv ( P, Signs ( P )) = 1 security for any Eve with time complexity at most T in the following game: - Alice chooses (s,v) - Eve gets black box access to Sign s (she has access to Verv ) - Eve wins if in the end she produces a pair (P,) such that (a) M was not queried (b) Verv ( P, ) = 1
Cryptography and Protocols Digital Signatures
16-9
Definition (cntd)
The probability Eve wins Pr[Eve wins ] < A scheme is secure if it is (T,)-secure for a superpolynomial pair (T,)
Cryptography and Protocols Digital Signatures
16-10
One-Time Signature Scheme
Eve is allowed to make only one query and we certify only one bit Thus Eves task is: Given (b, Sign s (b)) find (b , ) such that Verv (b , ) = 1 We use a one-way permutation f : {0,1}n {0,1}n with Pr n [Eve( f ( x)) = x] < for any polynomial time Eve and some superpolynomial Key generation: Gen chooses x 0 , x1 {0,1}n and computes y 0 = f ( x 0 ), y1 = f ( x1 ). Then set s = ( x 0 , x1 ) and v = ( y 0 , y1 ) Signing: Sign s (b) = x b Verification: Verv (b, x) = 1 f ( x) = y b
x{0,1}
Vous aimerez peut-être aussi
- Elliptic Curve Cryptography (ECC) : Mustafa Demirhan Bhaskar Anepu Ajit KunjalDocument18 pagesElliptic Curve Cryptography (ECC) : Mustafa Demirhan Bhaskar Anepu Ajit KunjalAtanu SarkarPas encore d'évaluation
- Chapter 7-2: Signature SchemesDocument37 pagesChapter 7-2: Signature SchemesMARIA AL-ABBADIPas encore d'évaluation
- Dttf/Nb479: Dszquphsbqiz Day 25: FT Latedaysle AvgDocument8 pagesDttf/Nb479: Dszquphsbqiz Day 25: FT Latedaysle AvgMaulik DantaraPas encore d'évaluation
- Crypto Assignment 4Document9 pagesCrypto Assignment 4Goutham SidarthPas encore d'évaluation
- Student Solution Chap 10Document6 pagesStudent Solution Chap 10priyapati21Pas encore d'évaluation
- Exop 1Document4 pagesExop 1Samiksha IyengarPas encore d'évaluation
- Harvard Algorithms cs124 NotesDocument6 pagesHarvard Algorithms cs124 NotesYamini DasguptaPas encore d'évaluation
- Lecture 15 - Elliptic Curves IIDocument23 pagesLecture 15 - Elliptic Curves IIaditiPas encore d'évaluation
- Asymmetric or Public Key CryptographyDocument55 pagesAsymmetric or Public Key CryptographySriharshitha DeepalaPas encore d'évaluation
- Overview of Public-Key Cryptography: Vitaly ShmatikovDocument24 pagesOverview of Public-Key Cryptography: Vitaly ShmatikovUmesh ThoriyaPas encore d'évaluation
- FALLSEM2019-20 CSE1011 ETH VL2019201001850 Reference Material I 14-Aug-2019 Module-3Document56 pagesFALLSEM2019-20 CSE1011 ETH VL2019201001850 Reference Material I 14-Aug-2019 Module-3gokulPas encore d'évaluation
- Diffie-Hellman Key ExchangeDocument5 pagesDiffie-Hellman Key ExchangeNikitaPas encore d'évaluation
- Group Theory in CS: Cryptography, Diffie-Hellman, and Elliptic CurvesDocument5 pagesGroup Theory in CS: Cryptography, Diffie-Hellman, and Elliptic CurvesMihir VahanwalaPas encore d'évaluation
- CryptographyDocument26 pagesCryptographySamin Hossain UtshoPas encore d'évaluation
- Module 4Document30 pagesModule 4Prakash SaubhariPas encore d'évaluation
- Cryptography and Network SecurityDocument25 pagesCryptography and Network SecurityViraj KumarPas encore d'évaluation
- Diffie-Hellman Key ExchangeDocument20 pagesDiffie-Hellman Key ExchangecezilcPas encore d'évaluation
- Diffie HellmanDocument2 pagesDiffie Hellmanapi-3737802Pas encore d'évaluation
- The Discrete Logarithm ProblemDocument5 pagesThe Discrete Logarithm ProblemSushil AzadPas encore d'évaluation
- Crypto 3Document9 pagesCrypto 3sauravkgupta5077Pas encore d'évaluation
- 18 Rsa 26 09 2023Document15 pages18 Rsa 26 09 2023corote1026Pas encore d'évaluation
- Chapter 7-1: Signature SchemesDocument37 pagesChapter 7-1: Signature SchemesMARIA AL-ABBADIPas encore d'évaluation
- Lecture 09Document5 pagesLecture 099192AltonDsilvaPas encore d'évaluation
- Crypto Slides 14 PK Tutor.1x1Document22 pagesCrypto Slides 14 PK Tutor.1x1Janhavi VishwanathPas encore d'évaluation
- 07 Shortest Path AlgorithmsDocument18 pages07 Shortest Path AlgorithmsahmPas encore d'évaluation
- HW 6Document4 pagesHW 6Kiên TrungPas encore d'évaluation
- HW 4Document4 pagesHW 4Happy manPas encore d'évaluation
- EllipticCurveCryptography HandoutDocument34 pagesEllipticCurveCryptography HandoutShobhit UmraoPas encore d'évaluation
- Homework 2 AIDocument14 pagesHomework 2 AImwroulimou67% (6)
- Q. No. 1 - 25 Carry One Mark EachDocument29 pagesQ. No. 1 - 25 Carry One Mark Eachamrendra7Pas encore d'évaluation
- 1.1 Pseudorandom GeneratorsDocument7 pages1.1 Pseudorandom GeneratorsMuhammad Al KahfiPas encore d'évaluation
- Chip-Firing Games On Graphs: A. BJ OrnerDocument17 pagesChip-Firing Games On Graphs: A. BJ OrnerMark Edward GonzalesPas encore d'évaluation
- ZKP Session 1Document26 pagesZKP Session 1Hridam BasuPas encore d'évaluation
- CHAPTER 09 - Digital SignaturesDocument37 pagesCHAPTER 09 - Digital SignaturesbukanDiaPas encore d'évaluation
- CSCE 465 Computer & Network Security: Public Key Public Key Cryptogrophy CryptogrophyDocument33 pagesCSCE 465 Computer & Network Security: Public Key Public Key Cryptogrophy CryptogrophyJohn KenPas encore d'évaluation
- Comp3355 L4a (PKC)Document53 pagesComp3355 L4a (PKC)Wai Kin TsuiPas encore d'évaluation
- TTDT - 05 EPayment Security IIDocument13 pagesTTDT - 05 EPayment Security IIPhương Trần Thị AnhPas encore d'évaluation
- Elgamal Public Key Cryptography: Cs 303 Alg. Number Theory & Cryptography Jeremy JohnsonDocument12 pagesElgamal Public Key Cryptography: Cs 303 Alg. Number Theory & Cryptography Jeremy JohnsonKishan Singh Vishen100% (1)
- 02 Stream AnnotatedDocument79 pages02 Stream Annotatedripperjack999Pas encore d'évaluation
- Kanp-Sack LectureDocument28 pagesKanp-Sack LectureSaikarPas encore d'évaluation
- Asymmetric Key CryptographyDocument27 pagesAsymmetric Key CryptographyAyush Agrawal 19110143Pas encore d'évaluation
- Plain Text (P) "Attack Postponed" C E (K, P) (P + K) Mod 26 Key 5 C (P + 5) Mod 26Document5 pagesPlain Text (P) "Attack Postponed" C E (K, P) (P + K) Mod 26 Key 5 C (P + 5) Mod 26Gnana SekharPas encore d'évaluation
- 15-853:algorithms in The Real World: Cryptography 3 and 4Document43 pages15-853:algorithms in The Real World: Cryptography 3 and 4NagarajuRaginaboyinaPas encore d'évaluation
- Systems and Network Security (NETW-1002) : Dr. Mohamed Abdelwahab Saleh IET-Networks, GUC Spring 2017 Exercise 6Document2 pagesSystems and Network Security (NETW-1002) : Dr. Mohamed Abdelwahab Saleh IET-Networks, GUC Spring 2017 Exercise 6SridharPas encore d'évaluation
- CHAPTER 05 - Public-Key CryptographyDocument29 pagesCHAPTER 05 - Public-Key CryptographyPPas encore d'évaluation
- Problem 3Document7 pagesProblem 3Vivek PatelPas encore d'évaluation
- Diffie Hellman PDFDocument6 pagesDiffie Hellman PDFsushmaPas encore d'évaluation
- Chapter-3 Computer SecurityDocument67 pagesChapter-3 Computer SecurityKetoran OliPas encore d'évaluation
- DDJ Elliptic - Curves.and - CryptographyDocument14 pagesDDJ Elliptic - Curves.and - CryptographyRaul Eduardo Garcia GarciaPas encore d'évaluation
- Cryptography and Network Security: Fifth Edition by William StallingsDocument41 pagesCryptography and Network Security: Fifth Edition by William StallingsDineshkumar SPas encore d'évaluation
- 5 Key Exchange Ver2Document27 pages5 Key Exchange Ver2Andi Soelkifly MelbaPas encore d'évaluation
- Crypto3 4Document43 pagesCrypto3 4SRC ExamPas encore d'évaluation
- RSA Cryptanalysis: 3 Class 22 4 2018Document17 pagesRSA Cryptanalysis: 3 Class 22 4 2018Zain Alabeeden AlarejiPas encore d'évaluation
- Shannon's Theory of Secure Communication: CSG 252 Fall 2006 Riccardo PucellaDocument23 pagesShannon's Theory of Secure Communication: CSG 252 Fall 2006 Riccardo PucellaG NAVEEN KUMARPas encore d'évaluation
- RSADocument11 pagesRSAZaryab ArifPas encore d'évaluation
- Public Key Cryptography-2Document27 pagesPublic Key Cryptography-2Restu Elisya SriandhaPas encore d'évaluation
- Encryption AlgorithmsDocument15 pagesEncryption AlgorithmssumipriyaaPas encore d'évaluation
- Cryptology April 2021 NEWESTDocument8 pagesCryptology April 2021 NEWESTYANYANPas encore d'évaluation
- R6512 eDocument176 pagesR6512 ePithoon UngnaparatPas encore d'évaluation
- R6510C - IEC 870 Interface GuideDocument12 pagesR6510C - IEC 870 Interface GuideBehzadPas encore d'évaluation
- R6511 BDocument45 pagesR6511 BPithoon UngnaparatPas encore d'évaluation
- Erl Scada BrochureDocument12 pagesErl Scada BrochureBehzadPas encore d'évaluation
- A Decision-Making Model On Stage Financing For Smart Transmission Grid Investment Based On Technology ReadinessDocument8 pagesA Decision-Making Model On Stage Financing For Smart Transmission Grid Investment Based On Technology ReadinessBehzadPas encore d'évaluation
- Vaigai ScheduleDocument67 pagesVaigai ScheduleMalti BansalPas encore d'évaluation
- Confidence Intervals For Kendall's Tau-B CorrelationDocument6 pagesConfidence Intervals For Kendall's Tau-B CorrelationscjofyWFawlroa2r06YFVabfbajPas encore d'évaluation
- Introduction To ControlDocument507 pagesIntroduction To Controlnaderjsa100% (2)
- DOQ117A - Quick Kaizen ModelDocument12 pagesDOQ117A - Quick Kaizen ModelShaimae ABOULMAJDPas encore d'évaluation
- AI ML Subject NamesDocument21 pagesAI ML Subject NamesDIVYANSH PANDEYPas encore d'évaluation
- Ordinary Differential EquationsDocument51 pagesOrdinary Differential EquationsG MahendraPas encore d'évaluation
- Schaum or - Branch & Bound AlgorithmsDocument16 pagesSchaum or - Branch & Bound Algorithms5678totodilePas encore d'évaluation
- 329 Lect 07Document10 pages329 Lect 07des tosPas encore d'évaluation
- CSC583 Final Aug2021 - QuestionDocument6 pagesCSC583 Final Aug2021 - QuestionMUHAMMAD DANIEL AIMAN BIN MD AMANPas encore d'évaluation
- D. Factorising Linear and Quadratic ExpressionsDocument13 pagesD. Factorising Linear and Quadratic ExpressionsRaihan RafaPas encore d'évaluation
- PricingCMSSpreadOptionsAndDigitalCMSSpreadOptionsWithSmile Berrahoui PDFDocument7 pagesPricingCMSSpreadOptionsAndDigitalCMSSpreadOptionsWithSmile Berrahoui PDFshih_kaichihPas encore d'évaluation
- Lectura 1 Artificial - Intelligence - Enabled - Project - ManagementDocument23 pagesLectura 1 Artificial - Intelligence - Enabled - Project - ManagementliberatahilarioPas encore d'évaluation
- Applied Machine Learning Course Schedule: TopicDocument29 pagesApplied Machine Learning Course Schedule: TopicAmarjeet KrishhnanPas encore d'évaluation
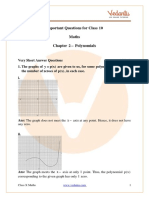
- CBSE Class 10 Maths Chapter 2 Polynomials Important Questions 2022-23 PDFDocument42 pagesCBSE Class 10 Maths Chapter 2 Polynomials Important Questions 2022-23 PDFShaunak BasuPas encore d'évaluation
- A X AX X: SMA3013 Linear AlgebraDocument11 pagesA X AX X: SMA3013 Linear AlgebraArvind RaveePas encore d'évaluation
- Theory of Computation MCQsDocument40 pagesTheory of Computation MCQsJitender Sharma85% (27)
- TTDS Assignment 1 Fall 2023Document1 pageTTDS Assignment 1 Fall 2023hsaleemPas encore d'évaluation
- A Deep Learning Model Based On Concatenation Approach For The Diagnosis of Brain TumorDocument10 pagesA Deep Learning Model Based On Concatenation Approach For The Diagnosis of Brain Tumorhamed razaPas encore d'évaluation
- Deep Learning With PyTorch PDFDocument255 pagesDeep Learning With PyTorch PDFSofyanArdiantoPas encore d'évaluation
- Table (With Non Integer Solution) Given BelowDocument2 pagesTable (With Non Integer Solution) Given BelowJaleel ChennaiPas encore d'évaluation
- Caesar Cipher Tutorial: EncryptionDocument2 pagesCaesar Cipher Tutorial: EncryptionUdaay SikderPas encore d'évaluation
- Third NoDocument6 pagesThird Nofikadu walkaPas encore d'évaluation
- 72552Document8 pages72552Andres GuevaraPas encore d'évaluation
- CHAPTER1 Signals and SpectraDocument38 pagesCHAPTER1 Signals and SpectraGita Eka RamadhaPas encore d'évaluation
- Control 7Document30 pagesControl 7harshaPas encore d'évaluation
- Lab Task - 2: Control Statement Related ProblemsDocument3 pagesLab Task - 2: Control Statement Related ProblemsTANZIN TANZINAPas encore d'évaluation
- Differential Geometry and Mechanics Applications To Chaotic Dynamical SystemsDocument24 pagesDifferential Geometry and Mechanics Applications To Chaotic Dynamical SystemsGINOUX Jean-MarcPas encore d'évaluation
- Data Structure - IDocument39 pagesData Structure - INamanPas encore d'évaluation
- 030 Ice 01 Result Dec10 InsDocument41 pages030 Ice 01 Result Dec10 InsDevanshu AnandPas encore d'évaluation
- DSP Lab SyllabusDocument3 pagesDSP Lab SyllabusKiranKumarPas encore d'évaluation
- Facing Cyber Threats Head On: Protecting Yourself and Your BusinessD'EverandFacing Cyber Threats Head On: Protecting Yourself and Your BusinessÉvaluation : 4.5 sur 5 étoiles4.5/5 (27)
- The Internet Con: How to Seize the Means of ComputationD'EverandThe Internet Con: How to Seize the Means of ComputationÉvaluation : 5 sur 5 étoiles5/5 (6)
- OSCP Offensive Security Certified Professional Practice Tests With Answers To Pass the OSCP Ethical Hacking Certification ExamD'EverandOSCP Offensive Security Certified Professional Practice Tests With Answers To Pass the OSCP Ethical Hacking Certification ExamPas encore d'évaluation
- Tor Darknet Bundle (5 in 1): Master the Art of InvisibilityD'EverandTor Darknet Bundle (5 in 1): Master the Art of InvisibilityÉvaluation : 4.5 sur 5 étoiles4.5/5 (5)
- Practical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTD'EverandPractical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTPas encore d'évaluation
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPND'EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNÉvaluation : 5 sur 5 étoiles5/5 (1)
- Coding Democracy: How a Growing Hacking Movement is Disrupting Concentrations of Power, Mass Surveillance, and Authoritarianism in the Digital AgeD'EverandCoding Democracy: How a Growing Hacking Movement is Disrupting Concentrations of Power, Mass Surveillance, and Authoritarianism in the Digital AgeÉvaluation : 4.5 sur 5 étoiles4.5/5 (3)
- Anonymize Yourself: The Art of Anonymity to Achieve Your Ambition in the Shadows and Protect Your Identity, Privacy and ReputationD'EverandAnonymize Yourself: The Art of Anonymity to Achieve Your Ambition in the Shadows and Protect Your Identity, Privacy and ReputationÉvaluation : 4 sur 5 étoiles4/5 (23)
- Hacking With Kali Linux : A Comprehensive, Step-By-Step Beginner's Guide to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingD'EverandHacking With Kali Linux : A Comprehensive, Step-By-Step Beginner's Guide to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingÉvaluation : 4.5 sur 5 étoiles4.5/5 (9)
- An Ultimate Guide to Kali Linux for BeginnersD'EverandAn Ultimate Guide to Kali Linux for BeginnersÉvaluation : 3.5 sur 5 étoiles3.5/5 (4)
- Cybersecurity for Beginners : Learn the Fundamentals of Cybersecurity in an Easy, Step-by-Step Guide: 1D'EverandCybersecurity for Beginners : Learn the Fundamentals of Cybersecurity in an Easy, Step-by-Step Guide: 1Pas encore d'évaluation
- Transformational Security Awareness: What Neuroscientists, Storytellers, and Marketers Can Teach Us About Driving Secure BehaviorsD'EverandTransformational Security Awareness: What Neuroscientists, Storytellers, and Marketers Can Teach Us About Driving Secure BehaviorsÉvaluation : 5 sur 5 étoiles5/5 (2)
- Hands-On AWS Penetration Testing with Kali Linux: Set up a virtual lab and pentest major AWS services, including EC2, S3, Lambda, and CloudFormationD'EverandHands-On AWS Penetration Testing with Kali Linux: Set up a virtual lab and pentest major AWS services, including EC2, S3, Lambda, and CloudFormationPas encore d'évaluation
- Cyber Security: How to Protect Your Digital Life, Avoid Identity Theft, Prevent Extortion, and Secure Your Social Privacy in 2020 and beyondD'EverandCyber Security: How to Protect Your Digital Life, Avoid Identity Theft, Prevent Extortion, and Secure Your Social Privacy in 2020 and beyondÉvaluation : 4.5 sur 5 étoiles4.5/5 (14)
- 200+ Ways to Protect Your Privacy: Simple Ways to Prevent Hacks and Protect Your Privacy--On and OfflineD'Everand200+ Ways to Protect Your Privacy: Simple Ways to Prevent Hacks and Protect Your Privacy--On and OfflinePas encore d'évaluation
- Risk Management and Information Systems ControlD'EverandRisk Management and Information Systems ControlÉvaluation : 5 sur 5 étoiles5/5 (1)
- Digital Forensics and Incident Response - Second Edition: Incident response techniques and procedures to respond to modern cyber threats, 2nd EditionD'EverandDigital Forensics and Incident Response - Second Edition: Incident response techniques and procedures to respond to modern cyber threats, 2nd EditionPas encore d'évaluation
- CCSP Certified Cloud Security Professional A Step by Step Study Guide to Ace the ExamD'EverandCCSP Certified Cloud Security Professional A Step by Step Study Guide to Ace the ExamPas encore d'évaluation
- The Mediatrician's Guide: A Joyful Approach to Raising Healthy, Smart, Kind Kids in a Screen-Saturated WorldD'EverandThe Mediatrician's Guide: A Joyful Approach to Raising Healthy, Smart, Kind Kids in a Screen-Saturated WorldPas encore d'évaluation
- CYBERSECURITY FOR BEGINNERS: HOW TO DEFEND AGAINST HACKERS & MALWARED'EverandCYBERSECURITY FOR BEGINNERS: HOW TO DEFEND AGAINST HACKERS & MALWAREÉvaluation : 3.5 sur 5 étoiles3.5/5 (6)
- The Internet Con: How to Seize the Means of ComputationD'EverandThe Internet Con: How to Seize the Means of ComputationÉvaluation : 5 sur 5 étoiles5/5 (1)