Académique Documents
Professionnel Documents
Culture Documents
Assign3 Solution
Transféré par
Bintang Mandala PutraDescription originale:
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
Assign3 Solution
Transféré par
Bintang Mandala PutraDroits d'auteur :
Formats disponibles
1. (15 points) Mobile IP. a.
Discuss the performance inefficiency of mobile IP regarding data forwarding from a correspondent node to a mobile node. Answer: Triangular routing causes mobile IP inefficient. It is made of the three segments, CN to HA, HA to COA/MN, and MN back to CN. With the basic mobile IP protocol all packets to the MN have to go through the HA. This can cause unnecessary overheads for the network between CN and HA, but also between HA and COA, depending on the current location of the MN. As the example shown in the textbook, latency can increase dramatically. This is particularly unfortunate if the MNs and has are separated by, e.g. transatlantic links. (7 points ) b. Discuss an optimization to improve the performance of mobile IP as well any problem(s) brought in by the optimization. Answer: One way to optimize the route is to inform the CN of the current location of the MN. The CN can learn the location by caching it in a binding cache which is a part of the local routing table for the CN. The appropriate entity to inform the CN of the location is the HA. The detail process is: CN can request the current location from the HA. If allowed by the MN, the HA returns the COA of the MN via an update message. The CN can send its data directly to the cur rent FA, FA forwards the packets to the MN. This scenario shows a COA located at an FA. Encapsulation of data for tunneling to the COA is now done by the CN, not the HA. (4 points) This optimization of mobile IP causes several security problems. Not all users of mobile communication systems want to reveal their current location( in the sense of an IP subnet ) to a communication partner. (4 points) 2. (15 points) DHCP and its uses to support mobility. a. What is the basic purpose of DHCP? Names the entities of DHCP. Answer: DHCP is a mechanism for configuring nodes. It is mainly used to simplify the installation and maintenance of networked computers. (4 points) The entities acquired via DHCP are, e.g., DHCP relay, DHCP server etc. (4 points) b. How can DHCP be used for mobility and support of mobile IP? Answer: DHCP is a good candidate for support the acquisition of COA for mobile nodes. The same holds for all other parameters needed, such as address of the default router, DNS servers etc. A DHCP server should be located in the subnet of the access point of the mobile node, or at least a DHCP relay should provide forwarding of the messages. (7 points) 3. (20 points) Transmission loss in wired and wireless networks.
a. State and compare different types of transmission l ss in TCP that can o occur in wired and wireless networks. Answer: Packet loss due to congestion: Congestion may appear from time to time even in carefully designed networks. The packets buffers of a router are filled and the router can not forward the packets fast enough because the sum of the input rates of packets destined for one output link is higher than the capacity of the output link. The only thing a router can do in this situation is to drop packets. This kind of packet loss can occur in both wireless and wired networks. Packet loss due to random loss The random loss is due to bit corruption and link errors. In wired network, the transmission error rate (10-10-10-12) is generally very low so that it can be neglected. However it is not true for the wireless network (10-2 -10-4 ). Packet loss due to burst loss The burst loss may be initiated by signal fading. Prolonged uncontrolled channel interference can lead to correlated packet losses. Yet it generally occurs over a very short duration, leading a loss of several consecutive segments at a time. In an infrastructure network, when a mobile host is moved from the coverage of a base station to another, all subsequent communications are routed via the new base station and the handoff process is completed. However the packet may be lost as they are routed to the old station during the process of the handoff. Therefore a handoff event can initiate a burst loss event. In ad hoc network, same situation can happen. During to the mobility of the mobile host, the network connectivity and the network topology can change. The transmission path for a traffic flow may be affected. Some time is necessary to complete the rerouting process for the traffic flow. Thus some packet belong to the same traffic flow may be lost during the process. As a result, a burst loss event occurs in this case. (6 points) b. What is the reaction of TCP Reno in case of segment loss? Answer: When sender receives three duplicate ACKs, fast retransmit is triggered such that inferred loss segment is retransmitted immediately. Fast recovery is also combined with fast retransmit. A fast retransmit suggests the presence of mild congestion. The slow start threshold is set to half of the amount of outstanding data sent to the network. Since the reception of a duplicate ACK indicates the departure of a segment from the network, congestion window is set to the sum of the slow start threshold and the number of the duplicate ACK received.
When an ACK for a new segment arrives, congestion window is reset to the slow start threshold and congestion avoidance is triggered. When the retransmission timer expires, the inferred loss segment is retransmitted. At the same the slow start is triggered. The slow start is performed starting with congestion window equal to one until it approaches to a predefined threshold. The congestion avoidance phase is then carried out where congestion window is increased by one for each RTT. ( 6 points ) c. In what situation does this reaction make sense and why it is quite often problematic in the case of wireless networks? Answer: The reaction makes sense if the packet loss is due to network congestion. However in wireless network, non-congestive segment loss becomes nonnegligible because of the following problems as below: Channel contention: In wireless network, signals are broadcast and interfere with each others. A collision will be sensed and transmission may fail when there exists concurrent transmission within the interference range of either sender. This problem can be exacerbated in TDMA based multi- hop wireless networks. The number of segment that can be in flight concurrently is limited from a source to a destination, thereby constraining the achievable throughput for a TCP connection. Furthermore the correlated arrivals of data segments and their ACKs lead to contention for the wireless channel, causing excessive collisions and packet losses. Signal Fading: Signal transmitted over the wireless medium may be distorted or weakened because they are propagated over an open unprotected and ever changing medium with irregular boundary. Besides the same signal may disperse and travel on different paths may take different times to reach the destination. Thus the resultant signal after summing up all dispersed signals may have been significantly distorted and attenuated when compared with the transmitted signal. The receiver may not recognize the signal and hence the transmitted data can not be received. Mobility: In infrastructure network, a handoff occurs when a mobile host moved from the coverage of a base station to another. In some occasions, the packets are lost during the handoff. In ad hoc network, the network topology changes when a mobile host moves. The same situation will happens in this case as the infrastructure network. Limited Power and Energy: A mobile host is generally handy, small size and dedicated to perform a certain set of functions. So the power source is limited for mobile host. To conserve the energy, it should be able to transmit an d receive in an intelligent manner so as to minimize the number of the retransmissions and receptions for certain communication operation. (8 points ) 4. (25 points) Compare and contrast ATCP, Freeze -TCP, TCP-Casablanca, TCPDOOR, and TCP-Peach in terms of their solution approaches, devices involved,
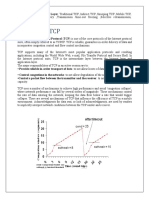
control information needed, and merits and drawbacks. Answer: Solution approach: ( 5 points ) In TCP-Peach, dummy segment, which are low-priority segments with a copy of the recently transmitted data, is employed to probe network. A successfully delivered dummy segment indicates that unused network resources exist and the transmission rate can then be increased accordingly. In TCP-Casablanca, a biased queue management scheme is applied to discriminate congestion losses from random losses. Congestion losses are de-randomized so that the distribution of congestive losses differs from that of random wireless losses. Such information is then used to determine whether congestion occurs. So these two solutio ns are congestion detection approaches. In Freeze-TCP, the receiver continuously monitors the signal strength and detects any impending handoffs. ZWA is sent to force the sender into the persist mode. Then all retransmission timers and the size of congestion windows are frozen until the advertised window is opened in the receiver. In TCP-DOOR, the receiver detects the out-of-order and then notifies the sender. The sender can either temporally disable congestion control or perform recovery during congestion avoidance. During disabling congestion control, the sender will keep it state unchanged for a time period. By instant recovery during congestion avoidance, the source recovers immediately to the state before the congestion response. The signal strength in Freeze-TCP and the out of order information in TCP-DOOR are used to decide the communication activity of a TCP connection may/may not be readjusted based on the network conditions after the suspension. So these two methods can be considered as the state suspension approach. In ATCP, the problem in ad hoc network is revolved by a sender-side, all-in-one solution. The key idea of ATCP is to introduce an ATCP layer between TCP and IP at the sender protocol stack. The current TCP state can be monitored and ECN/ICMP s can be employed to sense the onset of the network congestion. Based on the above information, the network can go to one of the four different states. The 4 states includes disconnect state, congestion control state, loss state and normal state. Different mechanisms can be triggered in the different states. So this method can be considered as the hybrid approach. Device involved and Control Information: ( 10 points ) ATCP : ATCP layer is introduced between IP and TCP at the sender protocol stack. s When network congestion is experienced, a router sets the ECN flag when it processes a packet. Moreover an ICMP source quench message is sent to the sender directly by the router when the transmission path is unstable or/and the network is partitioned. So the sender and router are involved. Freeze-TCP: Freeze-TCP is devised as a receiver-side solution to improve the TCP performance. The receiver continuously monitors the signal strengths of its wireless antenna. When the impending handoff is experienced, the receiver can detect it. The
ZWA can be sent to se nder. As a result, the sender is forced i to persist mode, n whenever possible about one RTT before a handoff is expected to occur. In this case, the receiver is involved. TCP-Casablanca: TCP-Casablanca applies a simple biased queue management scheme to discriminate congestion losses from random loss. The data segments are marked either or in outby sender by the specific marking pattern. Moreover the retransmitted segments are always marked . When network congestion is in experienced, a router will drop the p ackets labeled out before packets. By in doing so, the dropping sequence will show correlated losses. Such correlation can be detected in receiver by computing a discriminator function. When the transmission path is unstable, the receiver can also find by computing the discriminator function. The reason is there is no correlation between the loss type of a segment and the dropping probability. In this case, the sender, receiver and router are involved. TCP-DOOR: TCP-DOOR is developed with detection of OOO and response for adhoc network. The OOO event is deemed to imply routing changes in the network. The TCP packet sequence number and ACK duplication sequence number, or current timestamps are inserted into each data and ACK segments. The sender/receiver based OOO detection can be employed OOO events. If the receiver detects the OOO event, it should notify the sender. So the sender and receiver are involved. TCP-Peach: TCP-Peach is developed to deal with the adverse effect with long propagation delays and high link error rates. The dummy segments and their ACKs are used to probe the available network resources. In the beginning, Sudden Start is done by the sender sends (rwnd-1) dummy segments after the first data segment. The receiver sends their ACKs back to sender. When a segment loss is detected through duplicate ACKs, the Fast retransmit is done and then Rapid Recovery is applied until the ACK for the lost data segment is received. Moreover when the network congestion is experienced, the Dummy segments and their ACKs are of lower priority than regular segments and should be dropped first. So router receiver and sender will be involved. Merits: ( 5 points ) ATCP is only an existing proposal that attempt to handle most of the problems relating to wireless networks. Since ATCP take over the control for segment retransmission whenever three duplicate ACKs are received or a retransmission timeout is going to occur, it successfully avoids taking any spurious congestion control measures which shrink the congestion window size unnecessarily. Freeze-TCP: The sender is frozen until a non-zero window size is advertised by receiver. The burst loss can be resolved and no modification is necessary for the intermediate nodes. TCP-Casablanca: It can give a highly congestion prediction accuracy.
TCP-DOOR: This approach can avoid invoking unnecessary congestion control by detecting and responding to OOO packet delivery events. TCP-Peach: This approach can maintain ACK-clocking when cwnd is smaller than the number of unacknowledged data segments, and more segment data can be sent during the certain duration after cwnd is halved. Drawback: ( 5 point s ) ATCP: First, ATCP is inefficient in using the ava ilable bandwidth for data transmission in high-speed wireless networks with the presence of frequent route changes and network partition. Second ATCP requires the mobile hosts to be aware of and be implemented with ECN. The destination also needs to interp ret and forward ECN information. Third, ATCP do not allow a sender to send new data when it is in the loss state. The loss state can be frequent for the sender. Hence ACK-clocking can not be maintained. This substantially degrades the TCP performance running in an error-prone wireless network. Freeze-TCP: First, Freeze-TCP needs some cross-layer information so that the network stack of a mobile host must be aware of mobility; second, prediction must be done on when the disconnection occurs; third, the sche me fails to predict an upcoming disconnection even if it happens at a wireless link along the transmission path, where the end -points of the link are neither sender nor receiver; Fourth, the resumed transmission rate may be set inappropriately; Fifth, the scheme can only avoid the performance degradations due to disconnections. TCP-Casablanca: The TCP-Casablanca requires participating routers to have a differentia l packet dropping policy; besides it can not perform well in the presence of other TCP-friend ly flows when the congestive losses are dominant. TCP-DOOR: TCP-DOOR may set the sending rate of a connection inappropriately after a route change; besides it does not perform well in a congested network environment with substantial persistent packet reordering. TCP-Peach: Since the dummy segments are sent at a rate doubled that before a loss event is conjectured, they may be dropped at the routers since such an increase can lead to congestion. Besides, there would be wastage of network resource since the delivery of dummy segments does not result in any gain. Furthermore, all routers have to be configured to implement priority-based scheduling.
5. (25 points) Mobility issues in file systems. a. Why is the strong consistency of file systems problematic in a wireless and mobile environment? Answer:
It is simply too expensive to maintain strong consistency. Continuous updates require permanent connectivity, without connectivity all access must be blocked. (5 points) b. Discuss in detail the alternatives in place of the strong consistency of file systems to support client mobility. Answer: There are several alternatives in places of the strong consistency of file systems to support client mobility such as caching, prefetching, hoarding, automatic reintegration, manual reintegration etc. Caching: Caching means to save a copy of a file when it is downloaded from a server as requested by a client. The operating system on each client intercepts open and close file system calls and forwards them to a cache- management process called Venus in AFS as an example. After a file is opened, read and write operations on its bypass Venus. Venus contacts a server only on a cache miss on open, or on a close after modification. In both cases, the file is transferred in its entity. Cache coherence is maintained by a callback mechanism, whereby servers notify workstations of changes to cached files. Client dynamically determines the location of tiles on servers and cache s this information. Prefetching: Prefetching means fetch files from a server in advance the client makes a request for these files. To improve the caching performance, it is better to put the most important files into the cache. Different strategies are developed to do it. As an example in Coda, the files currently used can be prefetched when the client is strongly connected to the server. The importance of the file is also pre-defined by user. Coda can use such information to explicitly pre- fetch it. Hoarding: To provide all the necessary files for disconnected work, hoarding is employed to offer extensive mechanisms for pre-fetching of files while connected. If the client is connected to the server with a strong connection, hoarding transparently pre- fetches files currently used. This automatic data collection is necessary for it is impossible for a standard user to know all the files currently used. A user can pre-determine a list of files, which Coda should explicitly pre-fetch. Additionally a user can assign priorities to certain programs. Coda now decides on the current cache content using the list and a LRU strategy. Automatic reintegration: When the client is disconnected, the system keeps a record of changed files, but does not maintain a history of changes for each file. The cache always has only one replicate. After reconnection, the system executes a sequence of update operations to make the replicates on the server identical to the cached copy.
Manual reintegration: There are also some conflicts that can not been resolved automatically. As an example i Coda, automatic reintegration can not work n when two users have changed the same file. In this case the systems can saves the changed files as copy on the server to allow for manual reintegration. (20 points)
Vous aimerez peut-être aussi
- Part 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersDocument6 pagesPart 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersKani MozhiPas encore d'évaluation
- A Throughput Analysis of TCP in ADHOC NetworksDocument8 pagesA Throughput Analysis of TCP in ADHOC NetworksCS & ITPas encore d'évaluation
- TCP Over Wireless: Dr. RitikaDocument53 pagesTCP Over Wireless: Dr. RitikamonumunduriPas encore d'évaluation
- Unit 5 Final NotesDocument20 pagesUnit 5 Final Notesappsectesting3Pas encore d'évaluation
- Chapte Rwise Content DocxDocument18 pagesChapte Rwise Content DocxwexidaPas encore d'évaluation
- Cs601 Unit VDocument20 pagesCs601 Unit VRekha RahangdalePas encore d'évaluation
- Transport Layer Protocols For Ad-Hoc NetworksDocument29 pagesTransport Layer Protocols For Ad-Hoc NetworksShachi P GowdaPas encore d'évaluation
- 4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDocument16 pages4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDr. Sashi Kanth Reddy APas encore d'évaluation
- 1 Compare I-TCP, S-TCP and M-TCP 2 Understand CO3: Assignment # 2Document8 pages1 Compare I-TCP, S-TCP and M-TCP 2 Understand CO3: Assignment # 2wexidaPas encore d'évaluation
- Computer Networks Assignment QuestionsDocument8 pagesComputer Networks Assignment Questionsmayank27jaitly100% (1)
- Transport Layer: Fig. 6-4 Nesting of TPDU's, Packets, and FramesDocument22 pagesTransport Layer: Fig. 6-4 Nesting of TPDU's, Packets, and FramesAnantharaj ManojPas encore d'évaluation
- Unit 4 NotesDocument20 pagesUnit 4 NotesUmapathi Pawar SPas encore d'évaluation
- A Comparison of Techniques For Improving TCP Performance Over Wireless LinksDocument4 pagesA Comparison of Techniques For Improving TCP Performance Over Wireless LinksMuthu Vijay DeepakPas encore d'évaluation
- Wireless Transmission Control Protocol For: of AsDocument5 pagesWireless Transmission Control Protocol For: of AsKrishna DeshpandePas encore d'évaluation
- Priority TX in 802 - 11Document19 pagesPriority TX in 802 - 11Manuel ChawPas encore d'évaluation
- TCP For Wireless NetworksDocument16 pagesTCP For Wireless NetworksAnbarasan TRPas encore d'évaluation
- VJJVJVJDocument7 pagesVJJVJVJAnirudh KawPas encore d'évaluation
- Mobile Communications Chapter 9: Mobile Transport Layer: Motivation TCP-mechanisms Classical ApproachesDocument18 pagesMobile Communications Chapter 9: Mobile Transport Layer: Motivation TCP-mechanisms Classical Approacheschandra100% (1)
- Turning Hidden Nodes Into Helper Nodes in IEEE 802.11 Wireless LAN NetworksDocument12 pagesTurning Hidden Nodes Into Helper Nodes in IEEE 802.11 Wireless LAN NetworksphdmadhuPas encore d'évaluation
- Mobile Transport LayerDocument43 pagesMobile Transport LayerPoli Markova0% (1)
- Transport Layer ProtocolDocument28 pagesTransport Layer ProtocolShivanisAccountPas encore d'évaluation
- TCP Westwood: End-to-End Congestion Control For Wired/Wireless NetworksDocument13 pagesTCP Westwood: End-to-End Congestion Control For Wired/Wireless NetworksReetika AroraPas encore d'évaluation
- Mobile Communications Chapter 9: Mobile Transport Layer: Motivation TCP-mechanisms Classical ApproachesDocument18 pagesMobile Communications Chapter 9: Mobile Transport Layer: Motivation TCP-mechanisms Classical ApproachesArulPas encore d'évaluation
- A Solution For Improving TCP Performance Over Wireless LinksDocument12 pagesA Solution For Improving TCP Performance Over Wireless LinksBirsh EndawkiePas encore d'évaluation
- Directorate of Technical Education, Tamilnadu: Thanthai Periyar Government Institute of Technology, Vellore-632002Document22 pagesDirectorate of Technical Education, Tamilnadu: Thanthai Periyar Government Institute of Technology, Vellore-632002Karthick RaajPas encore d'évaluation
- Unit 4Document18 pagesUnit 4Manasa PPas encore d'évaluation
- Mobile TCPDocument7 pagesMobile TCPTUSHARPas encore d'évaluation
- Mobile Transport ProtocolsDocument15 pagesMobile Transport ProtocolsAditya SinghPas encore d'évaluation
- MC Unit 4Document28 pagesMC Unit 4Naveenkumar TariPas encore d'évaluation
- TCP Performance Enhancement Over UMTS Network With RNC FeedbackDocument6 pagesTCP Performance Enhancement Over UMTS Network With RNC FeedbackumtsrfPas encore d'évaluation
- Tcp-Bus: Improving TCP Performance in Wireless Ad Hoc NetworksDocument12 pagesTcp-Bus: Improving TCP Performance in Wireless Ad Hoc NetworksHarish GokulPas encore d'évaluation
- TCP Tuning On Sender SideDocument6 pagesTCP Tuning On Sender SideAbi AnnunPas encore d'évaluation
- Routing For Vehicle Based DTNDocument5 pagesRouting For Vehicle Based DTNVaibhav GodsePas encore d'évaluation
- TCP Over 3G ProtocolDocument6 pagesTCP Over 3G ProtocolHitesh KumarPas encore d'évaluation
- Advantages of High Speed Wired Medium Over To Wireless MediumDocument5 pagesAdvantages of High Speed Wired Medium Over To Wireless MediumSara AliPas encore d'évaluation
- Datocom AnswersDocument11 pagesDatocom AnswersHalefom DestaPas encore d'évaluation
- Indirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerDocument12 pagesIndirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerMukesh91% (220)
- Opnetwork03 WanDocument7 pagesOpnetwork03 WanHán LaPas encore d'évaluation
- CN Ia-2Document14 pagesCN Ia-2Shivam NarkhedePas encore d'évaluation
- TCP Performance Over GPRS: Michael MeyerDocument5 pagesTCP Performance Over GPRS: Michael Meyerrkrishna44Pas encore d'évaluation
- Chapter 6 QuestionsDocument7 pagesChapter 6 Questionsahmed zuhdPas encore d'évaluation
- Tutorial 9 AnswersDocument3 pagesTutorial 9 AnswersMohd SaqibPas encore d'évaluation
- TCP Optimization Through FEC, ARQ and Transmission Power TradeoffsDocument12 pagesTCP Optimization Through FEC, ARQ and Transmission Power TradeoffshelbakouryPas encore d'évaluation
- Data Link QuestionDocument7 pagesData Link QuestionAhmed Aziz SultanPas encore d'évaluation
- SE150610 NWC203c PE 01Document4 pagesSE150610 NWC203c PE 01huybhxse150610Pas encore d'évaluation
- TCP in Wirless DomainDocument24 pagesTCP in Wirless Domainapi-19981733Pas encore d'évaluation
- NN - LAN Troubleshooting and Base LiningDocument20 pagesNN - LAN Troubleshooting and Base LiningJae Phoenix JohnsonPas encore d'évaluation
- Study of Transport LayerDocument14 pagesStudy of Transport LayerFebin KfPas encore d'évaluation
- Performance Evaluation of TCP Reno, SACK and FACK Over WimaxDocument5 pagesPerformance Evaluation of TCP Reno, SACK and FACK Over WimaxHarjinder191Pas encore d'évaluation
- CN - Unit4.1 PDFDocument40 pagesCN - Unit4.1 PDFKanika TyagiPas encore d'évaluation
- A Review On Snoop With Rerouting in Wired Cum Wireless NetworksDocument4 pagesA Review On Snoop With Rerouting in Wired Cum Wireless NetworksInternational Organization of Scientific Research (IOSR)Pas encore d'évaluation
- DCN Unit-3saqDocument6 pagesDCN Unit-3saqsravan kumarPas encore d'évaluation
- Rejinpaul MC UNIT4Document27 pagesRejinpaul MC UNIT4SENTHIL VPas encore d'évaluation
- Describe Switching Technique in Detail. Circuit SwitchingDocument5 pagesDescribe Switching Technique in Detail. Circuit SwitchingHrituja HedauPas encore d'évaluation
- DATA COMMS AND NETWORKS Assignment 1Document23 pagesDATA COMMS AND NETWORKS Assignment 1farai nyakudangaPas encore d'évaluation
- Kevin Brown and Suresh Singh Department of Computer Science University of South Carolina Columbia, SC 29205 July 29, 1997Document25 pagesKevin Brown and Suresh Singh Department of Computer Science University of South Carolina Columbia, SC 29205 July 29, 1997priya raiPas encore d'évaluation
- CCNA Interview Questions You'll Most Likely Be AskedD'EverandCCNA Interview Questions You'll Most Likely Be AskedPas encore d'évaluation
- Indoor Radio Planning: A Practical Guide for 2G, 3G and 4GD'EverandIndoor Radio Planning: A Practical Guide for 2G, 3G and 4GÉvaluation : 5 sur 5 étoiles5/5 (1)
- Concise Guide to OTN optical transport networksD'EverandConcise Guide to OTN optical transport networksÉvaluation : 4 sur 5 étoiles4/5 (2)
- Introduction to Internet & Web Technology: Internet & Web TechnologyD'EverandIntroduction to Internet & Web Technology: Internet & Web TechnologyPas encore d'évaluation
- Windows Administrator Interview Questions and AnswersDocument7 pagesWindows Administrator Interview Questions and AnswersZerin CltPas encore d'évaluation
- Db7012 User ManualDocument63 pagesDb7012 User ManualRaul Angel Perez AbadPas encore d'évaluation
- Synology High Availability White Paper: Based OnDocument17 pagesSynology High Availability White Paper: Based OnDhani Aristyawan SimangunsongPas encore d'évaluation
- ExtremeWare 7.8.1b1 Release NotesDocument66 pagesExtremeWare 7.8.1b1 Release Notespbartlett1977Pas encore d'évaluation
- HUB, Switch, Router PDFDocument11 pagesHUB, Switch, Router PDFDiana Larisa ArdeleanuPas encore d'évaluation
- Oms Catalog PDFDocument5 pagesOms Catalog PDFAL AnbarasuPas encore d'évaluation
- AIX Hardening GuideDocument5 pagesAIX Hardening GuideMAPG100% (7)
- Address Mapping in Data CommunicationDocument16 pagesAddress Mapping in Data CommunicationYELCHURI VENKATA NAGASAI RAVI TEJAPas encore d'évaluation
- High Availability With SynologyDocument3 pagesHigh Availability With SynologyDhani Aristyawan SimangunsongPas encore d'évaluation
- IE Operating Instruction Manual NewDocument27 pagesIE Operating Instruction Manual Newvalentin bajinaruPas encore d'évaluation
- Documents Manual 443479 WinBook Security 8CH4CAM Manual R2 PDFDocument81 pagesDocuments Manual 443479 WinBook Security 8CH4CAM Manual R2 PDFMIGUEL ANGEL GARCIAPas encore d'évaluation
- 1 - Router-Modem OptimizationDocument5 pages1 - Router-Modem OptimizationLucas MeirelesPas encore d'évaluation
- EasyClocking Xenio I1000 User Manual 2Document32 pagesEasyClocking Xenio I1000 User Manual 2Mario Javier PradaPas encore d'évaluation
- VMG1312-B10A CLI Reference ManualDocument124 pagesVMG1312-B10A CLI Reference ManualTefy GiqueauxPas encore d'évaluation
- XH9948 ManualDocument42 pagesXH9948 ManualfostechPas encore d'évaluation
- WIZ-iRadio User Manual V1.0Document28 pagesWIZ-iRadio User Manual V1.0Claudio Mauricio Letzkus AlmendaresPas encore d'évaluation
- USR TCP232 302 User Manual - V1.0.3.01 PDFDocument22 pagesUSR TCP232 302 User Manual - V1.0.3.01 PDFmcgeezer1Pas encore d'évaluation
- ICSI - CNSS Certified Network Security SpecialistDocument262 pagesICSI - CNSS Certified Network Security Specialistnahid01Pas encore d'évaluation
- Network Security With PfsenseDocument178 pagesNetwork Security With PfsenseSoporte BarbatPas encore d'évaluation
- Chapter 4 V7.01 AgprepararDocument76 pagesChapter 4 V7.01 AgprepararCarlos Eduardo GarciaPas encore d'évaluation
- HCIA-WLAN V3.0 Training Material-2Document100 pagesHCIA-WLAN V3.0 Training Material-2RIVERA SANCHEZ JOHN ALEXPas encore d'évaluation
- ZD SNMP Reference Guide - 20120928Document126 pagesZD SNMP Reference Guide - 20120928primodopretoPas encore d'évaluation
- MCSA 70-340 NotesDocument34 pagesMCSA 70-340 NotesbekPas encore d'évaluation
- All Command Huawei OLT (MA56xx)Document35 pagesAll Command Huawei OLT (MA56xx)Hamyx LimaPas encore d'évaluation
- Nma Gtu Question-BankDocument24 pagesNma Gtu Question-BankBurhanuddin UdaipurwalaPas encore d'évaluation
- MCSA - Windows Server 2008Document9 pagesMCSA - Windows Server 2008Michael RandolphPas encore d'évaluation
- Rescued DocumentDocument121 pagesRescued DocumentsrivardanPas encore d'évaluation
- HUAWEI S5720-SI Switch DatasheetDocument12 pagesHUAWEI S5720-SI Switch DatasheetcesarPas encore d'évaluation
- HCIA Cheat Sheet CLI Commands - Miftah Rahman (Go) - BlogDocument10 pagesHCIA Cheat Sheet CLI Commands - Miftah Rahman (Go) - Blogسودان نولوجيPas encore d'évaluation
- 2 2 1 1 5b Equipmend Data Sheets CommDocument40 pages2 2 1 1 5b Equipmend Data Sheets CommMilic MilicevicPas encore d'évaluation