Académique Documents
Professionnel Documents
Culture Documents
BF ch02
Transféré par
Rawan Z NemerTitre original
Copyright
Formats disponibles
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
Formats disponibles
BF ch02
Transféré par
Rawan Z NemerDroits d'auteur :
Formats disponibles
2.
1
Chapter 2
Network Models
Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
2.2
2-1 LAYERED TASKS
We use the concept of layers in our daily life. As an
example, let us consider two friends who communicate
through postal mail. The process of sending a letter to a
friend would be complex if there were no services
available from the post office.
Sender, Receiver, and Carrier
Hierarchy
Topics discussed in this section:
2.3
Figure 2.1 Tasks involved in sending a letter
2.4
2-2 THE OSI MODEL
Established in 1947, the I nternational Standards
Organization (I SO) is a multinational body dedicated to
worldwide agreement on international standards. An I SO
standard that covers all aspects of network
communications is the Open Systems I nterconnection
(OSI ) model. I t was first introduced in the late 1970s.
Layered Architecture
Peer-to-Peer Processes
Encapsulation
Topics discussed in this section:
2.5
ISO is the organization.
OSI is the model.
Note
2.6
Figure 2.2 Seven layers of the OSI model
2.7
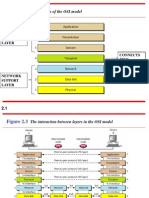
Figure 2.3 The interaction between layers in the OSI model
2.8
Figure 2.4 An exchange using the OSI model
2.9
2-3 LAYERS IN THE OSI MODEL
I n this section we briefly describe the functions of each
layer in the OSI model.
Physical Layer
Data Link Layer
Network Layer
Transport Layer
Session Layer
Presentation Layer
Application Layer
Topics discussed in this section:
2.10
Figure 2.5 Physical layer
2.11
The physical layer is responsible for movements of
individual bits from one hop (node) to the next.
Note
2.12
Figure 2.6 Data link layer
2.13
The data link layer is responsible for moving
frames from one hop (node) to the next.
Note
2.14
Figure 2.7 Hop-to-hop delivery
2.15
Figure 2.8 Network layer
2.16
The network layer is responsible for the
delivery of individual packets from
the source host to the destination host.
Note
2.17
Figure 2.9 Source-to-destination delivery
2.18
Figure 2.10 Transport layer
2.19
The transport layer is responsible for the delivery
of a message from one process to another.
Note
Also responsible for
Service point addressing ( to specific process running program)
Segmentation and reassembly
Connection control (connectionless and connectionoriented)
Flow control
Error control
2.20
Figure 2.11 Reliable process-to-process delivery of a message
2.21
Figure 2.12 Session layer
2.22
The session layer is responsible for dialog
control and synchronization.
Note
Dialog control ( half duplex or full duplex mode)
Synchronization checkpoint or synchronization
point
2.23
Figure 2.13 Presentation layer
2.24
The presentation layer is responsible for translation,
compression, and encryption.
Note
Translation : change the information to bit streams (encoding)
At the sender translate it to common format and at the receiver
machine changes the common format into its receiver dependent
format
Encryption: transforms the original information to another form.
Decryption( the reverse)
Compression: reduces the number of bits contained in the
information
2.25
Figure 2.14 Application layer
2.26
The application layer is responsible for
providing services to the user.
Note
Like:
Network virtual terminal: your account in BU
File transfer, access, and management: your account at computer lab.
Mail services.
Directory services.
2.27
Figure 2.15 Summary of layers
2.28
2-4 TCP/IP PROTOCOL SUITE
The layers in the TCP/I P protocol suite do not exactly
match those in the OSI model. The original TCP/I P
protocol suite was defined as having four layers: host-to-
network, internet, transport, and application. However,
when TCP/I P is compared to OSI , we can say that the
TCP/I P protocol suite is made of five layers: physical,
data link, network, transport, and application.
Physical and Data Link Layers
Network Layer
Transport Layer
Application Layer
Topics discussed in this section:
2.29
Figure 2.16 TCP/I P and OSI model
Transmission
Control Protocol
Stream Control
Transmission Protocol
User Datagram Protocol
2.30
IP Internet protocol :
provides no error checking or tracking
ARP Address Resolution Protocol :
used to associate a logical address with a physical address. To
find the physical address of the node when its internet address
known.
RARP- Reverse Address Resolution Protocol:
allows a host to discover its Internet address when it knows only
its physical address.
ICMP Internet Control Message Protocol:
sends a query and error reporting messages, used by hosts and
gateways to send back to the sender.
IGMP- Internet Group Message Protocol:
used to transmission of message to a group of recipients
simultaneous.
Network layer Protocol
2.31
TCP and UDP (host to host protocol)
Delivery the message from one process to another process
UDP User Datagram Protocol :
Add port address, checksum error control and length information
to the data from the upper layer.
TCP Transmission Control Protocol :
Connection-oriented , the connection between two ends must be
established before either can transmit data.
Divides the data into segments. With a sequence number
SCTP- Stream Control Transmission Protocol:
For new application like VOIP.
Transport layer Protocol
2.32
2-5 ADDRESSING
Four levels of addresses are used in an internet employing
the TCP/I P protocols: physical, logical, port, and specific.
Physical Addresses
Logical Addresses
Port Addresses
Specific Addresses
Topics discussed in this section:
2.33
Figure 2.17 Addresses in TCP/I P
2.34
Figure 2.18 Relationship of layers and addresses in TCP/I P
2.35
I n Figure 2.19 a node with physical address 10 sends a
frame to a node with physical address 87. The two nodes
are connected by a link (bus topology LAN). As the
figure shows, the computer with physical address 10 is
the sender, and the computer with physical address 87 is
the receiver.
Example 2.1
2.36
Figure 2.19 Physical addresses
2.37
As we will see in Chapter 13, most local-area networks
use a 48-bit (6-byte) physical address written as 12
hexadecimal digits; every byte (2 hexadecimal digits) is
separated by a colon, as shown below:
Example 2.2
07:01:02:01:2C:4B
A 6-byte (12 hexadecimal digits) physical address.
2.38
Figure 2.20 shows a part of an internet with two routers
connecting three LANs. Each device (computer or
router) has a pair of addresses (logical and physical) for
each connection. I n this case, each computer is
connected to only one link and therefore has only one
pair of addresses. Each router, however, is connected to
three networks (only two are shown in the figure). So
each router has three pairs of addresses, one for each
connection.
Example 2.3
2.39
Figure 2.20 I P addresses
2.40
Figure 2.21 shows two computers communicating via the
I nternet. The sending computer is running three
processes at this time with port addresses a, b, and c. The
receiving computer is running two processes at this time
with port addresses j and k. Process a in the sending
computer needs to communicate with process j in the
receiving computer. Note that although physical
addresses change from hop to hop, logical and port
addresses remain the same from the source to
destination.
Example 2.4
2.41
Figure 2.21 Port addresses
2.42
The physical addresses will change from hop to hop,
but the logical addresses usually remain the same.
Note
2.43
Example 2.5
As we will see in Chapter 23, a port address is a 16-bit
address represented by one decimal number as shown.
753
A 16-bit port address represented
as one single number.
Vous aimerez peut-être aussi
- Internet of Things: Architectures, Protocols and StandardsD'EverandInternet of Things: Architectures, Protocols and StandardsPas encore d'évaluation
- Exploring BeagleBone: Tools and Techniques for Building with Embedded LinuxD'EverandExploring BeagleBone: Tools and Techniques for Building with Embedded LinuxÉvaluation : 4 sur 5 étoiles4/5 (1)
- Mcgraw-Hill ©the Mcgraw-Hill Companies, Inc., 2000Document42 pagesMcgraw-Hill ©the Mcgraw-Hill Companies, Inc., 2000Maham uroojPas encore d'évaluation
- Chapter 2 - Network Models - Computer - NetworkDocument47 pagesChapter 2 - Network Models - Computer - Networkdhairyajoshi94Pas encore d'évaluation
- Network ModelsDocument42 pagesNetwork Modelsmh9273702Pas encore d'évaluation
- YsakDocument41 pagesYsakSreekanth ParameswaranPas encore d'évaluation
- CH 02Document49 pagesCH 02Rohith RevindranPas encore d'évaluation
- Network ModelsDocument40 pagesNetwork ModelsR!0Pas encore d'évaluation
- Ccnet 10f Lec02 ch2Document42 pagesCcnet 10f Lec02 ch2Ehsan ElahiPas encore d'évaluation
- Dcom Lecture 2Document41 pagesDcom Lecture 2Jonathan MainaPas encore d'évaluation
- Network ModelsDocument44 pagesNetwork ModelsShafiq ImtiazPas encore d'évaluation
- Network ModelsDocument42 pagesNetwork Models209X1A2855 MEKALA VARUN YADAVPas encore d'évaluation
- Chapter 2Document46 pagesChapter 2arrgantenPas encore d'évaluation
- Network Models: College of Computer Science & Engineering University of HailDocument41 pagesNetwork Models: College of Computer Science & Engineering University of HailkusumPas encore d'évaluation
- CH 02Document40 pagesCH 02as5239903Pas encore d'évaluation
- Lecture 3 Osi and TCPDocument41 pagesLecture 3 Osi and TCPRishita MaheshwariPas encore d'évaluation
- CH 02Document42 pagesCH 02Pallavi YadavPas encore d'évaluation
- Osi TCP IpDocument53 pagesOsi TCP IpSarah GazanPas encore d'évaluation
- Frozen ch02Document42 pagesFrozen ch02Shashank AgarwalPas encore d'évaluation
- Network ModelsDocument48 pagesNetwork Modelsvishakha singhPas encore d'évaluation
- Seven Layers of The OSI Model: User Support LayerDocument44 pagesSeven Layers of The OSI Model: User Support LayerRaj DesaiPas encore d'évaluation
- Chapter 2Document36 pagesChapter 2Raza ShahPas encore d'évaluation
- Computer Networks Network ModelsDocument41 pagesComputer Networks Network Models12user123Pas encore d'évaluation
- ch02 PDFDocument44 pagesch02 PDFTriệu Hồng BiênPas encore d'évaluation
- WINSEM2021-22 ITA1006 TH VL2021220504451 Reference Material I 23-02-2022 Module 1 Network ModelDocument48 pagesWINSEM2021-22 ITA1006 TH VL2021220504451 Reference Material I 23-02-2022 Module 1 Network ModelRiyanshi Kedia 21BCA0022Pas encore d'évaluation
- Layering, TCP/IP and OSI Model, Addressing: Reference - Kurose and ForuzanDocument52 pagesLayering, TCP/IP and OSI Model, Addressing: Reference - Kurose and ForuzanAmrutha VellankiPas encore d'évaluation
- NetworkDocument49 pagesNetworkVIDYAPas encore d'évaluation
- Lec # 02 - BF - CH # 02 - Network ModelsDocument57 pagesLec # 02 - BF - CH # 02 - Network ModelsJaveria AmjadPas encore d'évaluation
- About LayersDocument43 pagesAbout Layers219x1a05e7Pas encore d'évaluation
- DCCN Minor 1Document196 pagesDCCN Minor 1khushbooPas encore d'évaluation
- The OSI Model and The TCP/IP Protocol SuiteDocument40 pagesThe OSI Model and The TCP/IP Protocol SuiteAlfred Richie BennettPas encore d'évaluation
- Network Models: 2-1 Layered TasksDocument22 pagesNetwork Models: 2-1 Layered Tasksabbasmiry83Pas encore d'évaluation
- The OSI Model and The TCP/IP Protocol Suite: ObjectivesDocument39 pagesThe OSI Model and The TCP/IP Protocol Suite: ObjectivesAli AhmadPas encore d'évaluation
- Network ModelsDocument38 pagesNetwork ModelsdeardestinyPas encore d'évaluation
- The OSI Model and The TCP/IP Protocol SuiteDocument39 pagesThe OSI Model and The TCP/IP Protocol SuiteSafwan ShaikhPas encore d'évaluation
- CH 02Document53 pagesCH 02Nceba Perseverance MbewePas encore d'évaluation
- Network Models: Lecture # 3 - 4Document35 pagesNetwork Models: Lecture # 3 - 4Dr-Muhammad RizwanPas encore d'évaluation
- Osi ModelDocument44 pagesOsi Modelhenreke-1Pas encore d'évaluation
- Chapter 2 - Network Model - Part BDocument16 pagesChapter 2 - Network Model - Part BGolam MuktadirPas encore d'évaluation
- TCP IP Protocol Suite Chap-02 OSI ModelDocument39 pagesTCP IP Protocol Suite Chap-02 OSI ModelRahul RajPas encore d'évaluation
- The OSI Model and The TCP/IP Protocol SuiteDocument39 pagesThe OSI Model and The TCP/IP Protocol SuiteS JPas encore d'évaluation
- The OSI Model and The TCP/IP Protocol Suite: ObjectivesDocument39 pagesThe OSI Model and The TCP/IP Protocol Suite: ObjectivesShaik RasoolPas encore d'évaluation
- Chapter - 1: Miss Usha Padma Assistant Professor Department of ETE R V College of EngineeringDocument130 pagesChapter - 1: Miss Usha Padma Assistant Professor Department of ETE R V College of EngineeringSHANTANU B SPas encore d'évaluation
- Slide 1Document14 pagesSlide 1Durba Binte KalamPas encore d'évaluation
- Advanced CN Lecture 1Document34 pagesAdvanced CN Lecture 1Amir ButtPas encore d'évaluation
- Layers: Sender, Receiver, and Carrier HierarchyDocument36 pagesLayers: Sender, Receiver, and Carrier HierarchyP NischalaPas encore d'évaluation
- Network ModelsDocument47 pagesNetwork Modelsvai123adrPas encore d'évaluation
- CH 02Document27 pagesCH 02Petter PPas encore d'évaluation
- Data and Computer Communications: - Protocol Architecture, TCP/IP, and Internet-Based ApplicationsDocument25 pagesData and Computer Communications: - Protocol Architecture, TCP/IP, and Internet-Based ApplicationsHamza HasnynePas encore d'évaluation
- Network Models Tcp/IpDocument23 pagesNetwork Models Tcp/IpYawar ArslanPas encore d'évaluation
- Cnns 1Document58 pagesCnns 1Hrithik JaiswalPas encore d'évaluation
- Layering9 9 19Document69 pagesLayering9 9 19MonicaPas encore d'évaluation
- ch-2 DCCNDocument53 pagesch-2 DCCNMuntarin RahmanPas encore d'évaluation
- Ch02 OBE-Network ModelDocument26 pagesCh02 OBE-Network ModelNooraFukuzawa NorPas encore d'évaluation
- ECIE 3313 - 1 - 2017-18 CH - 02Document59 pagesECIE 3313 - 1 - 2017-18 CH - 02Syahmi SafwanPas encore d'évaluation
- CH 02Document42 pagesCH 02Tanvi SharmaPas encore d'évaluation
- CCNA Interview Questions You'll Most Likely Be AskedD'EverandCCNA Interview Questions You'll Most Likely Be AskedPas encore d'évaluation
- CCST Cisco Certified Support Technician Study Guide: Networking ExamD'EverandCCST Cisco Certified Support Technician Study Guide: Networking ExamPas encore d'évaluation
- Chapter 4 & 5: Digital & Analog TransmissionDocument21 pagesChapter 4 & 5: Digital & Analog TransmissionRawan Z NemerPas encore d'évaluation
- Determining System Requirements: CAIS233Document24 pagesDetermining System Requirements: CAIS233Rawan Z NemerPas encore d'évaluation
- Determining System Requirements: CAIS233Document16 pagesDetermining System Requirements: CAIS233Rawan Z NemerPas encore d'évaluation
- General Physics 1 Mechanics Hazeem Sake EkDocument319 pagesGeneral Physics 1 Mechanics Hazeem Sake EkRawan Z Nemer67% (3)
- General Physics 2 Electrostatics Hazeem SakeekDocument288 pagesGeneral Physics 2 Electrostatics Hazeem SakeekRawan Z NemerPas encore d'évaluation
- General Physics 2 Electrostatics Hazeem SakeekDocument288 pagesGeneral Physics 2 Electrostatics Hazeem SakeekRawan Z NemerPas encore d'évaluation
- Chapter 25Document57 pagesChapter 25Rawan Z NemerPas encore d'évaluation
- Chapter 24Document41 pagesChapter 24Rawan Z NemerPas encore d'évaluation
- Capacitance and DielectricsDocument55 pagesCapacitance and DielectricsRawan Z NemerPas encore d'évaluation
- General Physics 1 Mechanics Hazeem Sake EkDocument319 pagesGeneral Physics 1 Mechanics Hazeem Sake EkRawan Z Nemer67% (3)
- Standards For Multimedia CommunicationsDocument50 pagesStandards For Multimedia Communicationsoureducation.inPas encore d'évaluation
- DVG CH 01-2005Document22 pagesDVG CH 01-2005Vlase CiprianPas encore d'évaluation
- Dsat1000s SeriesDocument27 pagesDsat1000s SeriesElkaPas encore d'évaluation
- Windows XP Unattended InstallationDocument43 pagesWindows XP Unattended InstallationMarcos SantosPas encore d'évaluation
- Presentation State of Cyber Security in MyanmarDocument36 pagesPresentation State of Cyber Security in MyanmarDark WebPas encore d'évaluation
- User Guide: VelopDocument1 225 pagesUser Guide: VelopArturito NotificaPas encore d'évaluation
- S7-1200 1500 Webserver DOC v3 enDocument34 pagesS7-1200 1500 Webserver DOC v3 enAym BrPas encore d'évaluation
- NetNumenU31 GPON NBI Manual For TL1Document499 pagesNetNumenU31 GPON NBI Manual For TL1Gabriela Cintia Reyna GonzalezPas encore d'évaluation
- Cafezee PDFDocument121 pagesCafezee PDFSai Pyae Sone ThuPas encore d'évaluation
- A Step-By-Step Guide To Cyber Risk AssessmentDocument13 pagesA Step-By-Step Guide To Cyber Risk AssessmentEagle StrikePas encore d'évaluation
- COGNEX Is5000instDocument64 pagesCOGNEX Is5000instClaudemir SantosPas encore d'évaluation
- Computer Networks Networking - HardwareDocument21 pagesComputer Networks Networking - HardwareShujaat YousufPas encore d'évaluation
- ControlCenter InstallGuideDocument104 pagesControlCenter InstallGuideRahul SushruthPas encore d'évaluation
- AttckwioDocument7 pagesAttckwioGaneshPas encore d'évaluation
- CIPer Model 30 Product Data 31-00236Document7 pagesCIPer Model 30 Product Data 31-00236Min Jiat PANGPas encore d'évaluation
- UMTS Material (LT)Document215 pagesUMTS Material (LT)Matthew JejeloyePas encore d'évaluation
- ProMA Series A&EDocument10 pagesProMA Series A&EAbdullah AlhfetiPas encore d'évaluation
- ClassificationDocument34 pagesClassificationKarthikeyan SnPas encore d'évaluation
- Congestion Control For Wireless Cellular Systems With Applications To UMTSDocument2 pagesCongestion Control For Wireless Cellular Systems With Applications To UMTSChristopher AiyapiPas encore d'évaluation
- VP Product Management Chief Technology Officer in Seattle WA Resume Scott ToborgDocument9 pagesVP Product Management Chief Technology Officer in Seattle WA Resume Scott ToborgScottToborgPas encore d'évaluation
- SEEDS: Airport Management Database SystemDocument8 pagesSEEDS: Airport Management Database Systemgovindaraj_scholesPas encore d'évaluation
- Linksys Unmanaged Switches: Key Features and BenefitsDocument2 pagesLinksys Unmanaged Switches: Key Features and BenefitsChrisGiovanniCaroLlanquimanPas encore d'évaluation
- Internet of ThingsDocument15 pagesInternet of ThingsAishwarya Aishu33% (3)
- DWR-961 REVD DATASHEET v1.00 VERIZONDocument2 pagesDWR-961 REVD DATASHEET v1.00 VERIZONJohnPas encore d'évaluation
- Termsconditions of JionetDocument3 pagesTermsconditions of JionetskPas encore d'évaluation
- Jonyl Abang - FINAL EXAM IN CISDocument25 pagesJonyl Abang - FINAL EXAM IN CISLynoj AbangPas encore d'évaluation
- Sunny Tripower CORE1 (STP 50-40) : Operating ManualDocument114 pagesSunny Tripower CORE1 (STP 50-40) : Operating ManualMonster LifePas encore d'évaluation
- White Paper Voice Services With IP-MSANDocument16 pagesWhite Paper Voice Services With IP-MSANAnouar AleyaPas encore d'évaluation
- XWEB300D/500D/500 EVO: Installation ManualDocument22 pagesXWEB300D/500D/500 EVO: Installation ManualHoàngViệtAnhPas encore d'évaluation
- GRS MasterRev6.1Document571 pagesGRS MasterRev6.1Jorge MezaPas encore d'évaluation