Académique Documents
Professionnel Documents
Culture Documents
Amazon Mws Integration
Transféré par
ManojBhangale0 évaluation0% ont trouvé ce document utile (0 vote)
18 vues10 pagesAmazon Mws Integration
Copyright
© © All Rights Reserved
Formats disponibles
PPTX, PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentAmazon Mws Integration
Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PPTX, PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
18 vues10 pagesAmazon Mws Integration
Transféré par
ManojBhangaleAmazon Mws Integration
Droits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PPTX, PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 10
Identity and Access
Policy Distribution &
Transformation
Identity Services
Proxy/
Intermediary
Authentication
Services
Security Policy
Monitoring &
Reporting
Policy Decision
Firewall
Firewall
Policy Administration
Client System
(browser,
rich client)
Business Security Services
Web Application
Server/Portal
Server
Infrastructure
Existing
Application
IT Security
Services
Policy Enforcement
Vous aimerez peut-être aussi
- Gann - Enthios CalculatorDocument7 pagesGann - Enthios CalculatorSangheetha BPas encore d'évaluation
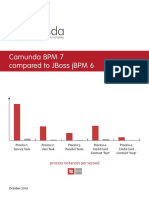
- 477 - Camunda BPM 7 Com Pared To JBossDocument17 pages477 - Camunda BPM 7 Com Pared To JBossManojBhangalePas encore d'évaluation
- State-wise List of Book Suppliers in IndiaDocument44 pagesState-wise List of Book Suppliers in IndiaManojBhangalePas encore d'évaluation
- Introduction To Networking, Part 1: Physical MediaDocument5 pagesIntroduction To Networking, Part 1: Physical MediaManojBhangalePas encore d'évaluation
- TD GEN Web2.0 SecurityDocument44 pagesTD GEN Web2.0 SecurityManojBhangalePas encore d'évaluation
- UML NotationDocument60 pagesUML NotationManojBhangalePas encore d'évaluation
- The Seven Famous Unsolved Math PuzzlesDocument6 pagesThe Seven Famous Unsolved Math PuzzlesManuel F. Presnilla100% (1)
- Power Drills and Drill BitsDocument10 pagesPower Drills and Drill Bitsmbhangale100% (1)
- Business PortalsDocument17 pagesBusiness PortalsManojBhangalePas encore d'évaluation
- Enterprise Service BusDocument15 pagesEnterprise Service BusManojBhangalePas encore d'évaluation
- Party Games For ChildrenDocument52 pagesParty Games For Childrenlili_mro100% (4)
- IT Enterprise Architecture Provides Strategic GuidanceDocument18 pagesIT Enterprise Architecture Provides Strategic Guidanceskumar1965Pas encore d'évaluation
- Cognos Product Line OverviewDocument7 pagesCognos Product Line OverviewManojBhangalePas encore d'évaluation
- Books List PDFDocument4 pagesBooks List PDFRohit Kumar100% (2)
- KVPYDocument12 pagesKVPYManojBhangalePas encore d'évaluation
- Shoe Dog: A Memoir by the Creator of NikeD'EverandShoe Dog: A Memoir by the Creator of NikeÉvaluation : 4.5 sur 5 étoiles4.5/5 (537)
- Never Split the Difference: Negotiating As If Your Life Depended On ItD'EverandNever Split the Difference: Negotiating As If Your Life Depended On ItÉvaluation : 4.5 sur 5 étoiles4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureD'EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureÉvaluation : 4.5 sur 5 étoiles4.5/5 (474)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeD'EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeÉvaluation : 4 sur 5 étoiles4/5 (5782)
- Grit: The Power of Passion and PerseveranceD'EverandGrit: The Power of Passion and PerseveranceÉvaluation : 4 sur 5 étoiles4/5 (587)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceD'EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceÉvaluation : 4 sur 5 étoiles4/5 (890)
- The Yellow House: A Memoir (2019 National Book Award Winner)D'EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Évaluation : 4 sur 5 étoiles4/5 (98)
- On Fire: The (Burning) Case for a Green New DealD'EverandOn Fire: The (Burning) Case for a Green New DealÉvaluation : 4 sur 5 étoiles4/5 (72)
- The Little Book of Hygge: Danish Secrets to Happy LivingD'EverandThe Little Book of Hygge: Danish Secrets to Happy LivingÉvaluation : 3.5 sur 5 étoiles3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryD'EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryÉvaluation : 3.5 sur 5 étoiles3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnD'EverandTeam of Rivals: The Political Genius of Abraham LincolnÉvaluation : 4.5 sur 5 étoiles4.5/5 (234)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaD'EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaÉvaluation : 4.5 sur 5 étoiles4.5/5 (265)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersD'EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersÉvaluation : 4.5 sur 5 étoiles4.5/5 (344)
- The Emperor of All Maladies: A Biography of CancerD'EverandThe Emperor of All Maladies: A Biography of CancerÉvaluation : 4.5 sur 5 étoiles4.5/5 (271)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyD'EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyÉvaluation : 3.5 sur 5 étoiles3.5/5 (2219)
- The Unwinding: An Inner History of the New AmericaD'EverandThe Unwinding: An Inner History of the New AmericaÉvaluation : 4 sur 5 étoiles4/5 (45)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreD'EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreÉvaluation : 4 sur 5 étoiles4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)D'EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Évaluation : 4.5 sur 5 étoiles4.5/5 (119)
- Her Body and Other Parties: StoriesD'EverandHer Body and Other Parties: StoriesÉvaluation : 4 sur 5 étoiles4/5 (821)