Académique Documents
Professionnel Documents
Culture Documents
Presentation On Cryptograph Y: Submitted by
Transféré par
Bidya dhar pandey0 évaluation0% ont trouvé ce document utile (0 vote)
17 vues13 pagesTitre original
Cryptography
Copyright
© © All Rights Reserved
Formats disponibles
PPTX, PDF, TXT ou lisez en ligne sur Scribd
Partager ce document
Partager ou intégrer le document
Avez-vous trouvé ce document utile ?
Ce contenu est-il inapproprié ?
Signaler ce documentDroits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PPTX, PDF, TXT ou lisez en ligne sur Scribd
0 évaluation0% ont trouvé ce document utile (0 vote)
17 vues13 pagesPresentation On Cryptograph Y: Submitted by
Transféré par
Bidya dhar pandeyDroits d'auteur :
© All Rights Reserved
Formats disponibles
Téléchargez comme PPTX, PDF, TXT ou lisez en ligne sur Scribd
Vous êtes sur la page 1sur 13
Presentation
on
CRYPTOGRAPH
Y
Submitted By:
Amartya Bhushan Pandey
Index
Introduction
What is Cryptography?
Purpose Of cryptography
Architecture of cryptography
Types of Cryptography
Types Of cryptography Algorithms
Conclusion
INTRODUCTION
The Internet or the global Internet is the internationally
connected network of computer networks with addresses that are
administrated by IANA (Internet address and Naming Authority).
There are many aspects to security and many applications,
ranging from secure commerce and payments to private
communications and protecting passwords. One essential aspect
for secure communications is that of cryptography.
Cryptography
derived its name from a Greek word called
What is Cryptography?
“krypto’s” which means “Hidden Secrets”.
Cryptography is the practice and study of hiding information. It
convert a plain intelligible data into an unintelligible data and
again retransforming that message into its original form.
Authentication: The process of proving one's identity. (The
PURPOSE OF CRYPTOGRAPHY
primary forms of host-to-host authentication on the Internet.)
Privacy : Ensuring that no one can read the message except
the intended receiver.
Integrity: Assuring the receiver that the received message has
not been altered in any way from the original.
Architecture of cryptography
Types of Cryptography
Secret Key Cryptography
• Single key used to encrypt and decrypt.
• Key must be known by both parties.
• Assuming we live in a hostile environment it may be hard to
share a secret key.
One
Public Keyof the keys
allocated to each person is called the "public
Cryptography
key", and is published in an open directory somewhere where
anyone can easily look it up, for example by email address.
Each entity has 2 keys:
Private Key (a secret)
Public key (well known).
Using Keys
Private keys are used for decrypting.
Public keys are used for encrypting.
TYPES OF CRYPTOGRAPHIC ALGORITHMS
Hash functions
Is a type of one-way function this are fundamental for much of
cryptography.
A one way function - is a function that is easy to calculate but
hard to invert.
It is difficult to calculate the input to the function given its
output.
CONCLUSION
We use either private key cryptography or public key
cryptography according to requirement.
If we want to send message quickly we use private key
algorithm and if we want to send messages secretly we use
public key algorithm.
Thanks…!!!
Any Query
Vous aimerez peut-être aussi
- CryptographyDocument14 pagesCryptographyPankaj AggarwalPas encore d'évaluation
- Cse CryptographyDocument18 pagesCse CryptographysavisuPas encore d'évaluation
- Cryptography Seminar - Types, Algorithms & AttacksDocument18 pagesCryptography Seminar - Types, Algorithms & AttacksHari HaranPas encore d'évaluation
- Presentation On Cryptograph Y: Submitted byDocument18 pagesPresentation On Cryptograph Y: Submitted bysadhana mmPas encore d'évaluation
- Cryptography: P.Nikhila N.Vishnu PriyaDocument13 pagesCryptography: P.Nikhila N.Vishnu PriyaNIkhila ReddyPas encore d'évaluation
- Cse CryptographyDocument18 pagesCse Cryptographyholyshit453Pas encore d'évaluation
- Cryptography: Joemari Saysay Sabao, MitDocument17 pagesCryptography: Joemari Saysay Sabao, Mitpia espanilloPas encore d'évaluation
- Cse CryptographyDocument15 pagesCse CryptographyPrasannaPas encore d'évaluation
- CryptographyDocument13 pagesCryptographyShrutiPas encore d'évaluation
- Cloud Cryptography SeminarDocument19 pagesCloud Cryptography Seminartejas it do d he got f foods manchiPas encore d'évaluation
- 18bcon020 Vatsal PDFDocument16 pages18bcon020 Vatsal PDFVatsal GuptaPas encore d'évaluation
- Cryptography: The Art and Science of Hiding InformationDocument20 pagesCryptography: The Art and Science of Hiding InformationMohammed Arbaz Salim KhanPas encore d'évaluation
- Cryptography: An Introduction to Cryptographic TechniquesDocument16 pagesCryptography: An Introduction to Cryptographic TechniquesGRACEPas encore d'évaluation
- Cse CryptographyDocument19 pagesCse CryptographyunknownPas encore d'évaluation
- Designing E-Commerce Security SolutionsDocument18 pagesDesigning E-Commerce Security SolutionsMukund HindujaPas encore d'évaluation
- UntitledDocument154 pagesUntitledJuanca100% (1)
- Adem Seminar PPT Final ReportsssDocument16 pagesAdem Seminar PPT Final ReportsssSimon YohannesPas encore d'évaluation
- Chapter1 Crypto B (1) - 1Document26 pagesChapter1 Crypto B (1) - 1Naazir jemaPas encore d'évaluation
- Major Doc Fine1Document75 pagesMajor Doc Fine1Anil SagarPas encore d'évaluation
- Index: 3.1 Private Key Algorithm 3.2 Public Key Algorithm 3.3 Hash FunctionsDocument11 pagesIndex: 3.1 Private Key Algorithm 3.2 Public Key Algorithm 3.3 Hash FunctionsYogesh YadavPas encore d'évaluation
- CryptographywordDocument3 pagesCryptographywordRUBENPas encore d'évaluation
- CRYPTOGRAPHYDocument7 pagesCRYPTOGRAPHYsaeed BarzaghlyPas encore d'évaluation
- SohaiDocument16 pagesSohaiJHON ANDREI SEMAPas encore d'évaluation
- Chapter 5 Authentication and Encryption TechnologyDocument34 pagesChapter 5 Authentication and Encryption TechnologyHasniza HarunPas encore d'évaluation
- CSE Cryptography ReportDocument21 pagesCSE Cryptography ReportOtunuya Chukwudi Henry EngrPas encore d'évaluation
- Ghaffa Ndaru Sandyeta Bin Marsudi - (32DDT20F2034) Muhammad Azeem Amirul Bin Mohd Zulkeflee - (32DDT20F2031)Document18 pagesGhaffa Ndaru Sandyeta Bin Marsudi - (32DDT20F2034) Muhammad Azeem Amirul Bin Mohd Zulkeflee - (32DDT20F2031)Triple DDDPas encore d'évaluation
- Lecture 1.1 Introduction Cryptography-UpdatedDocument7 pagesLecture 1.1 Introduction Cryptography-UpdatedNurdin YussufPas encore d'évaluation
- E - Commerce: Submitted To Anshita RajDocument11 pagesE - Commerce: Submitted To Anshita Rajabhhi yadavPas encore d'évaluation
- Cryptography Full ReportDocument9 pagesCryptography Full ReportSushant SharmaPas encore d'évaluation
- BUBUNDocument17 pagesBUBUNluckypapiPas encore d'évaluation
- Cryptography: Latika Arora, IT/06/321Document5 pagesCryptography: Latika Arora, IT/06/321Yatish TagraPas encore d'évaluation
- CryptographyDocument27 pagesCryptographyganesh_ecb123Pas encore d'évaluation
- The Basics of Cryptography: Encryption and DecryptionDocument5 pagesThe Basics of Cryptography: Encryption and DecryptionAngelyn BlanquiscoPas encore d'évaluation
- 3.5.1 Asymmetric Keys and Encryption MethodsDocument5 pages3.5.1 Asymmetric Keys and Encryption MethodsNashit BudhwaniPas encore d'évaluation
- Public Key Encryption: By, Arya Santhosh Reshma Elsa RejiDocument11 pagesPublic Key Encryption: By, Arya Santhosh Reshma Elsa RejiARYA SANTHOSH MBA 2017Pas encore d'évaluation
- What Is Cryptography?: U-I Foundations of CryptographyDocument63 pagesWhat Is Cryptography?: U-I Foundations of CryptographyAman RoyPas encore d'évaluation
- Index 2. Cryptography-Purpose 3. Types of Cryptographic AlgorithmsDocument12 pagesIndex 2. Cryptography-Purpose 3. Types of Cryptographic Algorithmstimothyosaigbovo3466Pas encore d'évaluation
- ReportDocument60 pagesReportHema SudhakarPas encore d'évaluation
- Chapter Seven Data Security and Integrity Under This Chapter We Will Discuss Fundamentals of Secure NetworksDocument23 pagesChapter Seven Data Security and Integrity Under This Chapter We Will Discuss Fundamentals of Secure NetworksGetnete degemuPas encore d'évaluation
- Encryption and Authentication Interview QuestionsDocument19 pagesEncryption and Authentication Interview QuestionsSam RogerPas encore d'évaluation
- Types of CryptographyDocument11 pagesTypes of CryptographyBridget Smith92% (12)
- Week 1Document37 pagesWeek 1Nina SyPas encore d'évaluation
- Cryptography: Presented By: Tanu Singh Shubham Pratap Vipul Tomar Class: It-6B Roll NoDocument17 pagesCryptography: Presented By: Tanu Singh Shubham Pratap Vipul Tomar Class: It-6B Roll NoMohit TiwariPas encore d'évaluation
- Explain Basic Objectives of CryptographyDocument62 pagesExplain Basic Objectives of Cryptographyrojemav574Pas encore d'évaluation
- Cryptography - Encryption/DecryptionDocument16 pagesCryptography - Encryption/DecryptionLakshya MahaniPas encore d'évaluation
- Lecture-1 - Intro To CryptographyDocument19 pagesLecture-1 - Intro To CryptographymarkburgPas encore d'évaluation
- 01-Introduction To CryptographyDocument107 pages01-Introduction To CryptographyHggPas encore d'évaluation
- Easychair Preprint: Esha Rawat, Anuska Singh, Alap Mahar and Amit AgarwalDocument7 pagesEasychair Preprint: Esha Rawat, Anuska Singh, Alap Mahar and Amit AgarwalStubborn BloodPas encore d'évaluation
- Public Key Infrastructure by Muhedin Abdullahi MohammedDocument123 pagesPublic Key Infrastructure by Muhedin Abdullahi Mohammedshabir AhmadPas encore d'évaluation
- Cryptography & Network SecurityDocument5 pagesCryptography & Network SecurityAlok ShuklaPas encore d'évaluation
- Introduction Graphic in PCDocument43 pagesIntroduction Graphic in PChahajsPas encore d'évaluation
- Security and CryptographyDocument9 pagesSecurity and CryptographyRavi Kumar KPas encore d'évaluation
- Assignment 2 - Part 2 - CryptographyDocument11 pagesAssignment 2 - Part 2 - CryptographyPJ1988Pas encore d'évaluation
- CryptographyDocument19 pagesCryptographySrilekha RajakumaranPas encore d'évaluation
- امنيه الفصل الاولDocument41 pagesامنيه الفصل الاولرسول ابراهيم عبد علي رويعيPas encore d'évaluation
- Chapter 2Document91 pagesChapter 2Destaye Sole WonidePas encore d'évaluation
- Introduction To Cryptography: Marcus K. G. AdomeyDocument52 pagesIntroduction To Cryptography: Marcus K. G. Adomeysaurabh sirohiPas encore d'évaluation
- Topic: Cryptology: History of CryptographyDocument24 pagesTopic: Cryptology: History of CryptographyAziz Ur RehmanPas encore d'évaluation
- BlockChain Technology & Blueprint Ultimate Guide: Learn Everything You Need To Know For Beginners & ExperiencedD'EverandBlockChain Technology & Blueprint Ultimate Guide: Learn Everything You Need To Know For Beginners & ExperiencedPas encore d'évaluation
- Nomenclatura - Encyclopedia of modern Cryptography and Internet Security: From AutoCrypt and Exponential Encryption to Zero-Knowledge-Proof Keys [Paperback]D'EverandNomenclatura - Encyclopedia of modern Cryptography and Internet Security: From AutoCrypt and Exponential Encryption to Zero-Knowledge-Proof Keys [Paperback]Pas encore d'évaluation
- ICMR Website Update 25march 10AM IST PDFDocument1 pageICMR Website Update 25march 10AM IST PDFBidya dhar pandeyPas encore d'évaluation
- Ismr Full2011Document226 pagesIsmr Full2011Shafi KhanPas encore d'évaluation
- Basics of Stock MarketDocument338 pagesBasics of Stock Marketsarthak1826Pas encore d'évaluation
- Basics of Stock MarketDocument338 pagesBasics of Stock Marketsarthak1826Pas encore d'évaluation
- OSPF Neighborship TroubleshootingDocument40 pagesOSPF Neighborship TroubleshootingJay MPas encore d'évaluation
- Competitive Profile Matrix (CPM) SampleDocument2 pagesCompetitive Profile Matrix (CPM) SampleApril DeePas encore d'évaluation
- Metallic Bonding ExplainedDocument3 pagesMetallic Bonding ExplainedNajam Us SamadPas encore d'évaluation
- Bucket Elevator CatalogDocument43 pagesBucket Elevator CatalogErsin Sucu100% (1)
- Opnet Env VariablesDocument1 pageOpnet Env VariablesRizwan KhanPas encore d'évaluation
- Logical Thinking: Hsem1Btechfastrack0719Document4 pagesLogical Thinking: Hsem1Btechfastrack0719Vikas MishraPas encore d'évaluation
- M. Mohamed Musthafa - T. Ashok Kumar - T. Mohanraj - R. Chandramouli 2018Document6 pagesM. Mohamed Musthafa - T. Ashok Kumar - T. Mohanraj - R. Chandramouli 2018Steve CardenasPas encore d'évaluation
- Electronics: Quarter II - Module 3Document18 pagesElectronics: Quarter II - Module 3Eden BayaniPas encore d'évaluation
- 2.zener Diode As Voltage RegulatorDocument2 pages2.zener Diode As Voltage RegulatorLaxmikant DigraskarPas encore d'évaluation
- 1990 - CameronDocument8 pages1990 - CameronChiara GastaldiPas encore d'évaluation
- Exercise Chapter 2: PDT SESI 2018/2019Document4 pagesExercise Chapter 2: PDT SESI 2018/2019EizaNizamPas encore d'évaluation
- Anomaly Detection in Surveillance VideoDocument59 pagesAnomaly Detection in Surveillance VideoNikhil MarkanPas encore d'évaluation
- I/O System, Device Drivers and Virtualization ChapterDocument89 pagesI/O System, Device Drivers and Virtualization ChapterKanishk GoelPas encore d'évaluation
- Inductive Sensor NI20-CP40-Y1X: Type CodeDocument4 pagesInductive Sensor NI20-CP40-Y1X: Type CodeCristiano FariasPas encore d'évaluation
- BIT Pilani Quantum Chemistry Course OverviewDocument6 pagesBIT Pilani Quantum Chemistry Course OverviewUtkarsh BansalPas encore d'évaluation
- BB TNS Up 4Document10 pagesBB TNS Up 4Haphaell ResplandesPas encore d'évaluation
- BASIC CYCLE DEVELOPMENT TECHNIQUESDocument7 pagesBASIC CYCLE DEVELOPMENT TECHNIQUEShasan_j688675Pas encore d'évaluation
- Retrieving and Reading - A Comprehensive Survey On Open-Domain Question AnsweringDocument21 pagesRetrieving and Reading - A Comprehensive Survey On Open-Domain Question AnsweringEap ChenPas encore d'évaluation
- Unit 6 S2Phy Thermal Transfer PracticeDocument8 pagesUnit 6 S2Phy Thermal Transfer PracticeWilly TanPas encore d'évaluation
- Computer Anatomy ExplainedDocument9 pagesComputer Anatomy ExplainedAnjuman AraaPas encore d'évaluation
- 2008 ATRA Seminar Manual PDFDocument277 pages2008 ATRA Seminar Manual PDFdaswine100% (3)
- AOCS CC 3 25 2009 Melting Point PDFDocument2 pagesAOCS CC 3 25 2009 Melting Point PDFpiagiopersempre0% (1)
- DLL 9th WeekDocument6 pagesDLL 9th WeekBea ParkPas encore d'évaluation
- DTN - Overview v2Document20 pagesDTN - Overview v2Ernesto QuintanaPas encore d'évaluation
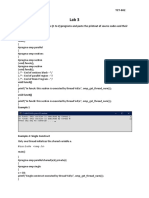
- Lab 3Document23 pagesLab 3RAMESH KUMARPas encore d'évaluation
- Technical Specification OF 11&33 KV Indoor Type Switchgear For Consumer SubstationDocument12 pagesTechnical Specification OF 11&33 KV Indoor Type Switchgear For Consumer SubstationAhmed JwdhariPas encore d'évaluation
- Theoretical Comparison of Direct-Sampling Versus Heterodyne RF Receivers - IEEE Journals & MagazineDocument2 pagesTheoretical Comparison of Direct-Sampling Versus Heterodyne RF Receivers - IEEE Journals & MagazineEnricoLia0% (1)
- Autodesk 3dconnexion Hotfix Readme PDFDocument3 pagesAutodesk 3dconnexion Hotfix Readme PDFjhuskanovicPas encore d'évaluation
- Table JigDocument11 pagesTable JigMd Aziq Md RaziPas encore d'évaluation
- Experimental Confirmation of Some Factors Influencing Dynamic Concrete Compressive Strengths in High-Speed Impact TestsDocument8 pagesExperimental Confirmation of Some Factors Influencing Dynamic Concrete Compressive Strengths in High-Speed Impact TestsMohamad AzharPas encore d'évaluation



























































![Nomenclatura - Encyclopedia of modern Cryptography and Internet Security: From AutoCrypt and Exponential Encryption to Zero-Knowledge-Proof Keys [Paperback]](https://imgv2-2-f.scribdassets.com/img/word_document/421844479/149x198/e9c664736d/1617232007?v=1)